Maybe you were once advised to “look for the padlock” as a means of telling legitimate e-commerce sites from phishing or malware traps. Unfortunately, this has never been more useless advice. New research indicates that half of all phishing scams are now hosted on Web sites whose Internet address includes the padlock and begins with “https://”.
Recent data from anti-phishing company PhishLabs shows that 49 percent of all phishing sites in the third quarter of 2018 bore the padlock security icon next to the phishing site domain name as displayed in a browser address bar. That’s up from 25 percent just one year ago, and from 35 percent in the second quarter of 2018.
This alarming shift is notable because a majority of Internet users have taken the age-old “look for the lock” advice to heart, and still associate the lock icon with legitimate sites. A PhishLabs survey conducted last year found more than 80% of respondents believed the green lock indicated a website was either legitimate and/or safe.
In reality, the https:// part of the address (also called “Secure Sockets Layer” or SSL) merely signifies the data being transmitted back and forth between your browser and the site is encrypted and can’t be read by third parties. The presence of the padlock does not mean the site is legitimate, nor is it any proof the site has been security-hardened against intrusion from hackers.
Most of the battle to combat cybercrime involves defenders responding to offensive moves made by attackers. But the rapidly increasing adoption of SSL by phishers is a good example in which fraudsters are taking their cue from legitimate sites.
“PhishLabs believes that this can be attributed to both the continued use of SSL certificates by phishers who register their own domain names and create certificates for them, as well as a general increase in SSL due to the Google Chrome browser now displaying ‘Not secure’ for web sites that do not use SSL,” said John LaCour, chief technology officer for the company. “The bottom line is that the presence or lack of SSL doesn’t tell you anything about a site’s legitimacy.”
The major Web browser makers work with a number of security organizations to index and block new phishing sites, often serving bright red warning pages that flag the page of a phishing scam and seek to discourage people from visiting the sites. But not all phishing scams get flagged so quickly.
I spent a few minutes browsing phishtank.com for phishing sites that use SSL, and found this cleverly crafted page that attempts to phish credentials from users of Bibox, a cryptocurrency exchange. Click the image below and see if you can spot what’s going on with this Web address:
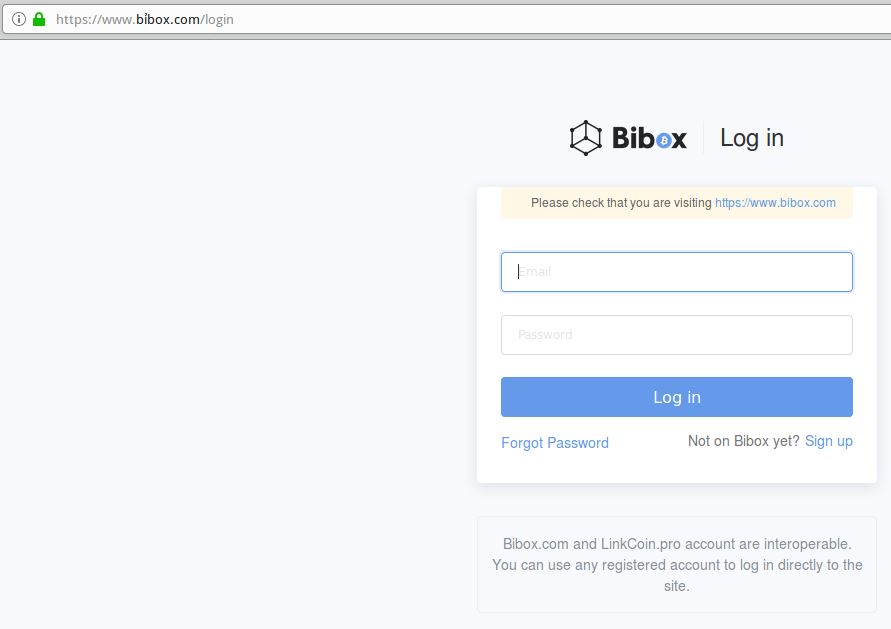
This live phish targets users of cryptocurrency exchange Bibox. Look carefully at the URL in the address bar, and you’ll notice a squiggly mark over the “i” in Bibox. This is an internationalized domain name, and the real address is https://www.xn--bbox-vw5a[.]com/login
Load the live phishing page at https://www.xn--bbox-vw5a[.]com/login (that link has been hobbled on purpose) in Google Chrome and you’ll get a red “Deceptive Site Ahead” warning. Load the address above — known as “punycode” — in Mozilla Firefox and the page renders just fine, at least as of this writing.
This phishing site takes advantage of internationalized domain names (IDNs) to introduce visual confusion. In this case, the “i” in Bibox.com is rendered as the Vietnamese character “ỉ,” which is extremely difficult to distinguish in a URL address bar.
As KrebsOnSecurity noted in March, while Chrome, Safari and recent versions of Microsoft’s Internet Explorer and Edge browsers all render IDNs in their clunky punycode state, Firefox will happily convert the code to the look-alike domain as displayed in the address bar.
If you’re a Firefox (or Tor) user and would like Firefox to always render IDNs as their punycode equivalent when displayed in the browser address bar, type “about:config” without the quotes into a Firefox address bar.
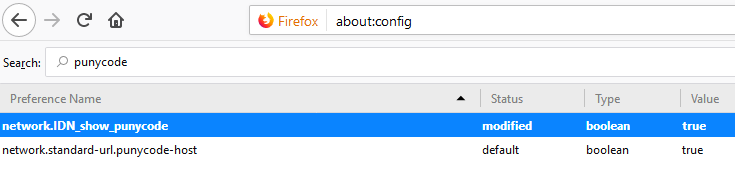
Then in the “search:” box type “punycode,” and you should see one or two options there. The one you want is called “network.IDN_show_punycode.” By default, it is set to “false”; double-clicking that entry should change that setting to “true.”



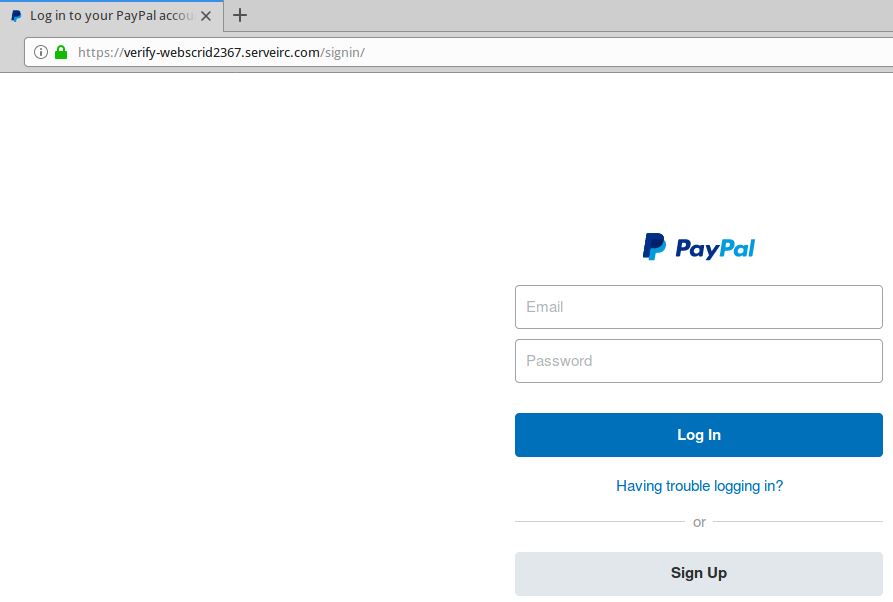
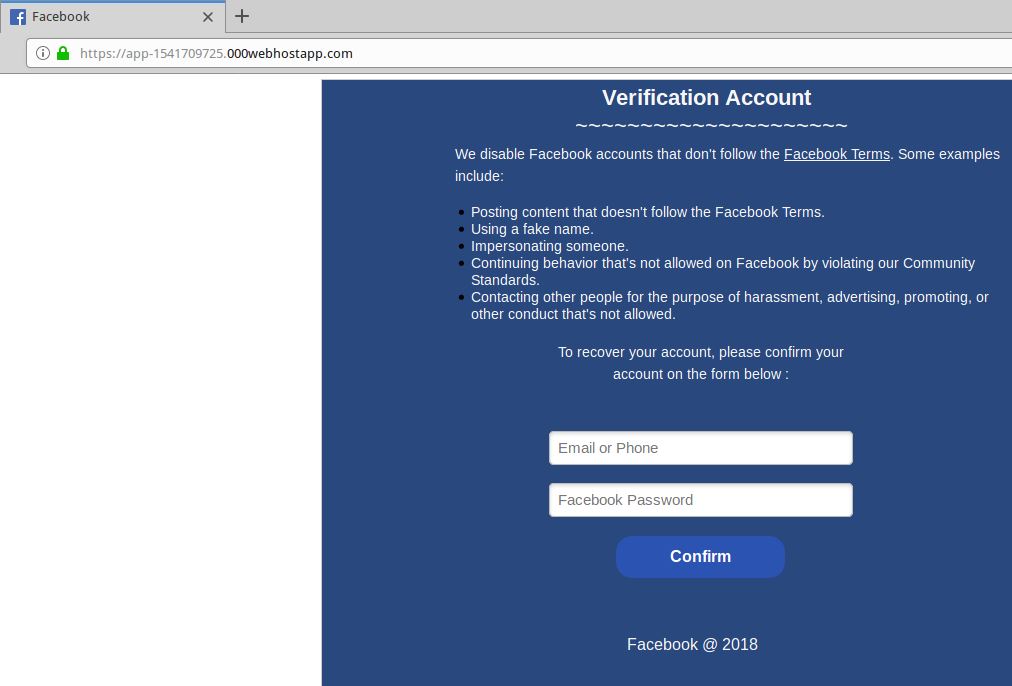

FWIW, when I tried to visit the “bibox” phish site using Firefox 63.0.3 on November 27, 2018, I got a “Deceptive site ahead” warning advisory “provided by Google Safe Browsing”.
What’s the point of a certificate authority if they pass out certs to phishers? There should be a big difference between how the lock is displayed depending on if the cert is chained to a trusted certificate authority or not.
The cert merely helps you determine if you’re connected securely to the site in question. Basic certs aren’t designed to tell you anything about the quality or intent of the site itself.
A phisher could buy a cert from *any* trusted certificate authority; they choose LE simply because there’s no cost involved.
“Chain of Trust” should mean something. LE is crapping on that trust.
(responding to VB’s assertion that “chain of trust” should mean something)
Misplaced trust is the root of the problem, because trust is not transitive.
LetsEncrypt is doing their job perfectly correct. They are validating that the site in question is in fact the site you see in the URL.
What is the alternative? Make the certificate authorities check every site every day to make sure that the contents of the website is not deceptive?
vb,
In an ideal world, certificates should reflect something about the trustworthiness of a site. A padlock should not only indicate that a browser has an encrypted connection to a website, but that it’s operated by someone good and decent.
Unfortunately, we don’t live in an ideal world.
Governments are not good, but it’s occasionally necessary to use their websites securely.
Banks and investment firms are a necessary evil, but their malevolence shouldn’t prevent a secure connection to view my accounts.
Facebook, Twitter, and Google are the very definition of bad corporatist oppressors who engage in pervasive tracking of everything and everyone, yet their idiot users expect secure account access.
Smaller websites might be owned creeps, bigots, extremists, or jerks.
-Does that mean they should all be ineligible to run HTTPS?
-Who’s to be the investigative authority checking into the lives of website owners?
-Where’s the due process for legitimate websites denied encryption certificate, because the owner has unpopular beliefs?
And that’s why the padlock is not a symbol of trustworthiness and decency. It only means the connection from the user to the website is secure. Nothing more, nothing less.
Well said.
People seem to place undue responsibility on a simple icon of a padlock. It cannot possibly convey all the information that might be useful for a consumer, even if they were so inclined to try a holistic profile of the website.
Browsers do have “more info” for those users who don’t understand what a padlock means. For Chrome it says,
“Your information (for example, passwords or credit card numbers) is private when sent to this site. Learn more”
For Firefox it says,
“The page you are viewing was encrypted before being transmitted over the Internet. Encryption makes it difficult for unauthorized people to view information traveling between computers. It is therefore unlikely that anyone read this page as it traveled across the network.”
If people don’t bother to even click to find out what the padlock means, they have little say.
+1
Thanks for the Firefox tip – dumb default these days for us ASCII-speakers.
Hi Brian:
Would like to catch up and talk to you about bringing you to Pittsburgh for an event next year
Let me know when we can talk or call 412-965-2502
Dave Hickton
Come on now Brian…if you aren’t using letsencrypt during your phishing campaigns, which is even automated in even the average deployment, than you’re really a total scrub at the game. Think about it; we need to get past an email filtering service, very likely a proxy or L7 firewall, so even with SSL intercept having a cert is basic, trivial and free. This really isn’t a great article from a content/usefulness standpoint to be honest. SSL is practically irrelevant and not something I’ve seen most of my user bases opt for in click-through rates.
I think the point he’s trying to make is that so much mainstream media tried to give people a “simple” method for determining if a website was trying to phish them, and now that’s backfired. It was a flawed plan in the first place, obviously.
First, let’s fix the article as FireFox actually uses G SafeBrowsing and puts up a big red warning, so commenters like James D. are not mislead.
Then, @LezBeHonest isn’t right, as Average Joe is not aware what LetsEncrypt is at all, not to mention the tech mumbo-jumbo mentioned; having a “grey padlock” is a problem and average people shall be made aware.
In Chrome/Chromium you need at least two well placed clicks to see the actual cert and it doesn’t help since you have to _understand_ what you’re seeing. And I do not expect EV certs just magically appear everywhere, which may (or likely may not) help the issue.
Even worse it’s not that simple as “do not sign non-ascii” since, let’s be honest, the educated part of the world 🙂 [which is everywhere outside the US] is writing in UTF-8 and it’s valid, most of the time. SafeBrowsing is a half-good solution, at least. Should be implemented in every browser.
Oh by the way Chromium [not Chrome, which I don’t use and don’t know about] renders the _translated_ URL as well instead of PunyCode by default.
Thank you Google for deflated the value of HTTPS by forcing everyone to use it.
Does anyone know how to find who the host for these two domains are?
forusajobs.net
forusajobs.com
The scammer’s information is not appearing on iCANN WHOIS.
John, It looks like the domains you just posted were created by someone that is trying to load up on google ad money. His site does not seem to be configured to steal identity like the other sites you have found in the past. Looks like he figured out how to hide his identity.
It takes about 30 seconds to find the company that’s hosting those two sites…
It takes evem less time to answer John Clark’s question and tell him how to do it himself.
That would encourage John to continue promoting his blog by posting similar comments on every new topic here.
If you look at his site it’s apparent he is not doing for the money. There is no advertising and it’s rather obvious he is using an fake name. “John Clark” is the name used in Tom Clancy books.
It looks like he just wants to get the word out so the scammers stop victimizing the people (much like Krebs is doing).
John,
Congratulations on updating your site and catching a few more scammers.
This site has a subscription option for delving into domain historical data, but also a WHOIS tool you can use a few times each day for free:
https://whois.domaintools.com/
The sites you inquired about were very recently re-registered. The free tool doesn’t indicate who previously registered those domains, but it shows the current registrant for one in Panama and the other in USA.
Good luck.
I think this is a clear effect of Google pushing for the encrypted web. With their funding of let’s encrypt, if is free for anyone to obtain a trusted cert for any domain. Browsers need to inform users that a green lock icon does not mean they are accessing the site they think they are.
Regarding Punycode display of IDN Domain names:
You can’t just forcefully show all websites as Punycode, as there are some legitimate sites which only have IDN names, such as flüge.de. The only alternative URL that’d be usable would be fluege.de, but that’s already in use by a competitor.
As result flüge.de has no alternative.
And if you’d force all URLs to show as punycode, users would soon get used to xn--bcher-kva.de or xn--flge-1ra.de, and would stop paying any attention whatsoever to URLs (and honestly, punycode URLs always look like phishing domains anyway).
God bless russia and putin.
God bless carders fraudsters, hustlers, moneymakers.
God bless africa
For Firefox in about:config I set property network.IDN_show_punycode to “true”. I think this keeps you from being deceived.
Firefox just posted an article titled “6 Essential Tips for Safe Online Shopping”. Tip no. 1 reads in part: …”a green lock at the top corner of the URL bar means the site is encrypted…”. As we know from this article, that’s absolutely untrue.
Brian, perhaps you can reach out to Mozilla/Firefox and let them know the truth about the green padlock, and suggest they issue a correction. I couldn’t find a good way to contact them.
URL: https://blog.mozilla.org/firefox/6-tips-for-safe-online-shopping/?utm_source=newsletter&utm_medium=email&utm_campaign=firefox-11-29-18&utm_content=text-link
Unfortunately, you’re making the same mistake that the article is warning you about: Confusing “encrypted” with “trustworthy”. The Firefox article is correct in saying that the site is encrypted. It then even goes on: “Either way, make sure the site you’re on is trustworthy.”
Wow, did you even read Brian’s article at all?
This is why DV SSL should be forbidden or at least that sites with DV should have a red padlock or something. Today a normal user can’t see the difference between an organization validated certificate and a DV issued one..
The article and comments provide good awareness that the green lock does not indicate that a website is safe and the punycode configuration is a good step. Does anyone have suggestions for verifying the trustworthiness of a site other than Google’s “Deceptive site ahead” or “the site ahead contains malware” warning? Is there a plugin that would help? Should the SSL cert be examined each time you visit a site and if so what are some red flags?
https://krebsonsecurity.com/2018/11/how-to-shop-online-like-a-security-pro/comment-page-1/#comment-476876
I don’t know much about certs. However, I upgrade to more recent encryption levels.
Thank you – very helpful.
Thank you – very helpful. I was hoping there would be a plugin or something that would handle most of the manual querying but I guess that’s where Google’s warnings come into play. I guess manual queries are fine because we all typically visit sites with which we’re already comfortable.
Right. And, antivirus products help some too. I don’t use AV; but on occassion do online lookups.
Might be worth outlining that EV certificates do provide some level of authenticity to the website.
Is the Brian Krebs who supposedly authored this page ( http://89.46.223.70 ), the same Brian Krebs that authored this one?
The address was included in some half-baked hacking attempt on my site and I arrived here during my investigations.