Easily the most sophisticated skimming devices made for hacking terminals at retail self-checkout lanes are a new breed of PIN pad overlay combined with a flexible, paper-thin device that fits inside the terminal’s chip reader slot. What enables these skimmers to be so slim? They draw their power from the low-voltage current that gets triggered when a chip-based card is inserted. As a result, they do not require external batteries, and can remain in operation indefinitely.
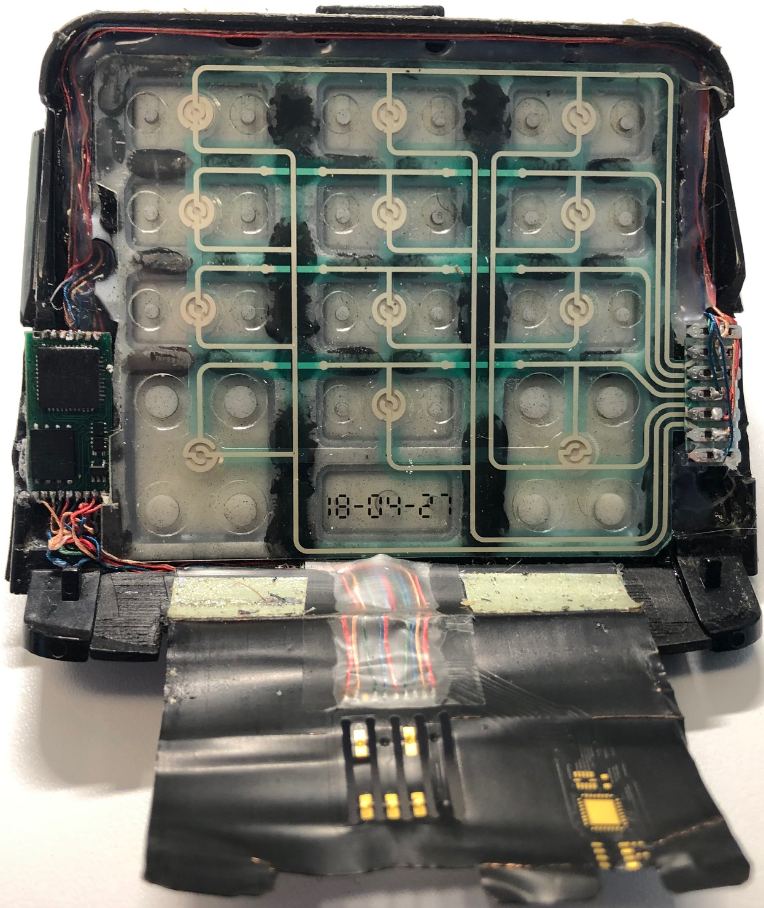
A point-of-sale skimming device that consists of a PIN pad overlay (top) and a smart card skimmer (a.k.a. “shimmer”). The entire device folds onto itself, with the bottom end of the flexible card shimmer fed into the mouth of the chip card acceptance slot.
The overlay skimming device pictured above consists of two main components. The one on top is a regular PIN pad overlay designed to record keypresses when a customer enters their debit card PIN. The overlay includes a microcontroller and a small data storage unit (bottom left).
The second component, which is wired to the overlay skimmer, is a flexible card skimmer (often called a “shimmer”) that gets fed into the mouth of the chip card acceptance slot. You’ll notice neither device contains a battery, because there simply isn’t enough space to accommodate one.
Virtually all payment card terminals at self-checkout lanes now accept (if not also require) cards with a chip to be inserted into the machine. When a chip card is inserted, the terminal reads the data stored on the smart card by sending an electric current through the chip.
Incredibly, this skimming apparatus is able to siphon a small amount of that power (a few milliamps) to record any data transmitted by the payment terminal transaction and PIN pad presses. When the terminal is no longer in use, the skimming device remains dormant.
The skimmer pictured above does not stick out of the payment terminal at all when it’s been seated properly inside the machine. Here’s what the fake PIN pad overlay and card skimmer looks like when fully inserted into the card acceptance slot and viewed head-on:

The insert skimmer fully ensconced inside the compromised payment terminal. Image: KrebsOnSecurity.com
Would you detect an overlay skimmer like this? Here’s what it looks like when attached to a customer-facing payment terminal:

The PIN pad overlay and skimmer, fully seated on a payment terminal.
REALLY SMART CARDS
The fraud investigators I spoke with about this device (who did so on condition of anonymity) said initially they couldn’t figure out how the thieves who plant these devices go about retrieving the stolen data from the skimmer. Normally, overlay skimmers relay this data wirelessly using a built-in Bluetooth circuit board. But that also requires the device to have a substantial internal power supply, such as a somewhat bulky cell phone battery.
The investigators surmised that the crooks would retrieve the stolen data by periodically revisiting the compromised terminals with a specialized smart card that — when inserted — instructs the skimmer to dump all of the saved information onto the card. And indeed, this is exactly what investigators ultimately found was the case.
“Originally it was just speculation,” the source told KrebsOnSecurity. “But a [compromised] merchant found a couple of ‘white’ smartcards with no markings on them [that] were left at one of their stores. They informed us that they had a lab validate that this is how it worked.”
Some readers might reasonably be asking why it would be the case that the card acceptance slot on any chip-based payment terminal would be tall enough to accommodate both a chip card and a flexible skimming device such as this.
The answer, as with many aspects of security systems that decrease in effectiveness over time, has to do with allowances made for purposes of backward compatibility. Most modern chip-based cards are significantly thinner than the average payment card was just a few years ago, but the design specifications for these terminals state that they must be able to allow the use of older, taller cards — such as those that still include embossing (raised numbers and letters). Embossing is a practically stone-age throwback to the way credit cards were originally read, through the use of manual “knuckle-buster” card imprint machines and carbon-copy paper.
“The bad guys are taking advantage of that, because most smart cards are way thinner than the specs for these machines require,” the source explained. “In fact, these slots are so tall that you could fit two cards in there.”
IT’S ALL BACKWARDS
Backward compatibility is a major theme in enabling many types of card skimming, including devices made to compromise automated teller machines (ATMs). Virtually all chip-based cards (at least those issued in the United States) still have much of the same data that’s stored in the chip encoded on a magnetic stripe on the back of the card. This dual functionality also allows cardholders to swipe the stripe if for some reason the card’s chip or a merchant’s smartcard-enabled terminal has malfunctioned.
Chip-based credit and debit cards are designed to make it infeasible for skimming devices or malware to clone your card when you pay for something by dipping the chip instead of swiping the stripe. But thieves are adept at exploiting weaknesses in how certain financial institutions have implemented the technology to sidestep key chip card security features and effectively create usable, counterfeit cards.
Many people believe that skimmers are mainly a problem in the United States, where some ATMs still do not require more secure chip-based cards that are far more expensive and difficult for thieves to clone. However, it’s precisely because some U.S. ATMs lack this security requirement that skimming remains so prevalent in other parts of the world.
Mainly for reasons of backward compatibility to accommodate American tourists, a great number of ATMs outside the U.S. allow non-chip-based cards to be inserted into the cash machine. What’s more, many chip-based cards issued by American and European banks alike still have cardholder data encoded on a magnetic stripe in addition to the chip.
When thieves skim non-U.S. ATMs, they generally sell the stolen card and PIN data to fraudsters in Asia and North America. Those fraudsters in turn will encode the card data onto counterfeit cards and withdraw cash at older ATMs here in the United States and elsewhere.
Interestingly, even after most U.S. banks put in place fully chip-capable ATMs, the magnetic stripe will still be needed because it’s an integral part of the way ATMs work: Most ATMs in use today require a magnetic stripe for the card to be accepted into the machine. The main reason for this is to ensure that customers are putting the card into the slot correctly, as embossed letters and numbers running across odd spots in the card reader can take their toll on the machines over time.
And there are the tens of thousands of fuel pumps here in the United States that still allow chip-based card accounts to be swiped. The fuel pump industry has for years won delay after delay in implementing more secure payment requirements for cards (primarily by flexing their ability to favor their own fuel-branded cards, which largely bypass the major credit card networks).
Unsurprisingly, the past two decades have seen the emergence of organized gas theft gangs that take full advantage of the single weakest area of card security in the United States. These thieves use cloned cards to steal hundreds of gallons of gas at multiple filling stations. The gas is pumped into hollowed-out trucks and vans, which ferry the fuel to a giant tanker truck. The criminals then sell and deliver the gas at cut rate prices to shady and complicit fuel station owners and truck stops.
A great many people use debit cards for everyday purchases, but I’ve never been interested in assuming the added risk and pay for everything with cash or a credit card. Armed with your PIN and debit card data, thieves can clone the card and pull money out of your account at an ATM. Having your checking account emptied of cash while your bank sorts out the situation can be a huge hassle and create secondary problems (bounced checks, for instance).
The next skimmer post here will examine an inexpensive and ingenious analog device that helps retail workers quickly check whether their payment terminals have been tampered with by bad guys.




My strategy is to have two credit cards and two debit cards. One of the credit and debit have very low daily and total max limits. I use those on suspect or smaller businesses (without money to spend on the best security). I only use the other credit card on major website orders. The other debit is my main checking and I hardly ever use it except to get cashback at big grocery stores or at the bank’s ATM. So far so good.
Why, indeed would you ever use a debit card? These days, you barely need cash, so ATMs are fairly useless. If you n need cash, go inside your bank and withdraw it. Not that hard.
Having to go into a bank branch, during working hours, is inconvenient.
Many people use banks that don’t have a lot of branches. Using the big banks that have lots of branches, also leads to more fees, because banks have to keep branches open.
ATMs are at least available everywhere, and work across banks.
I agree, that debit cards should be avoided. Although some shops don’t like paying the much larger transaction fees, so some just refuse to take some credit cards, leaving you with a need to use a debit card or cash.
Exactly, many gas stations tack an extra $.10 per gallon if you want to use a credit card versus debit cards or cash. Doesn’t seem like a lot but it adds up.
If you don’t want to go in and pay cash to use the pump, you are stuck paying the fee to use a credit card or accepting the possible risk and using a debit card. What needs to be done is stop the ability for these merchants to charge more for credit than for debit. Make it one price for any card based transaction and I think most people will stop using debit at the pump.
Your credit card usage costs merchants 2.5 – 3.2% in fees which go to your card issuer, the front/back end processor and their merchant services provider. Your debit card may only cost them 50cents if its from a big bank (credit unions and small banks fees for debit cards run closer to the credit card rates). When you consider the gross profit margin on what you’re purchasing may only be a single digit, taking 2-3% right off the top to feed the financial industry may mean a loss for the merchant by the time it becomes a net profit.
Small businesses are choked by a financial industry they have no influence and no control over & are forced to participate in if they want to stay in business.
Large businesses have some leverage. Your local gas station is probably a franchisee – in other words- a small business who pays large franchise fees to wear that big label.
This is exactly the problem.
A major local grocery chain tried to force VISA credit cards to charge a smaller fee… by refusing to accept those cards from customers… but it doesn’t work. They lost customers instead. So the card providers know they have all the leverage here. Free market economics break down when there the persons making a choice, aren’t the ones who pay.
My Credit Union doesn’t even have a branch in the state I live in now. I just get cash back from WalMart via my Discover card (no charge). $60 lasts a LONG time in a near-cashless society during a pandemic.
“Why would you ever use a debit card?” There are stores which do not accept credit cards. They save money that way by not paying the fees. I shop at a grocery store which only accepts cash, debit, checks and SNAP.
As far as Debit cards go and in answer to your question about why anyone would use one, I can tell you as an American who’s lived in Milano, Italy for decades, that in this country at least, just about everyone uses debit cards rather than credit cards. There are many valid reasons for this. A simple cash withdrawal from inside a bank can take up to a half hour. Also, the simple act of opening a bank account here, which is necessary in order to obtain a credit card of any kind, is a bureaucratic nightmare, whereas obtaining a Debit card usually takes about ten minutes. Add to all of this the fact that so many Italians are impoverished and would never come close to qualifying for a credit card, and you’ve got a Debit card heaven in this country. I’m sorry to have to end with the well known fact, at least well known here, that Italy has a HUGE number of scammers and criminals in its population and if credit cards were as readily available here as they are in the United States, the only thing that law enforcement would be working on, 24/7, would be credit card fraud.
Not all countries debit cards have the problems that the US has the UK for example.
I just don’t do online banking at all with my primary bank for OPSEC reasons which solves a lot of problems.
A lot depends on the bank. My debit card is a MasterCard… issued by my banked, and backed by my accounts. I get rewards, all the same security that you have on your CC, and no fees or interest.
So… Why wouldn’t I use it?
“all the same security” ?
So if someone empties your checking account with that debit card… the money is immediately returned if you file a fraud claim after a month?
I think not.
Credit vs. debit is fundamentally different. One is a direct link to your money. If stolen by fraud, it takes a lot of work to get it back, and the bank may never do it.
…my credit union offers what they call combo cards (debit and credit in one) and the money comes directly out of my account and yes, they put back immediately any fraud transactions…
…you obviously have chosen the wrong bank…
My credit union offers ATM-only cards that can’t be used for debit purchases. I have my notification set for any withdrawal whatsoever, and a daily limit of one transaction, maximum $250. Unless I’m really slow off the mark, my maximum downside is this figure.
Why not use Apple Pay or Google Pay or Samsung Pay. They are far more secure than using the card.
Excellent article
Can the skimmers be avoided by using the tap feature rather than inserting the card?
Great question Bob! Was just about to ask the same thing. Thanks!
Mitch
Not really.
“Tap” is similar to “Chip and PIN” or EMV
Instead of using metal contacts on the card, tapping just uses a “contactless” radio frequency (RF). The reader energizes the card (low power transfer over RF) similar to active RFID used in toll road access.
But the underlying data is the same.
Basically “tapping” still uses a “Chip and PIN”. The main difference is only the medium of data transfer.
“Chip-based credit and debit cards are designed to make it infeasible for skimming devices or malware to clone your card when you pay for something by dipping the chip instead of swiping the stripe. But thieves are adept at exploiting weaknesses in how certain financial institutions have implemented the technology to sidestep key chip card security features and effectively create usable, counterfeit cards.
Many people believe that skimmers are mainly a problem in the United States, where some ATMs still do not require more secure chip-based cards that are far more expensive and difficult for thieves to clone. However, it’s precisely because some U.S. ATMs lack this security requirement that skimming remains so prevalent in other parts of the world.
Mainly for reasons of backward compatibility to accommodate American tourists, a great number of ATMs outside the U.S. allow non-chip-based cards to be inserted into the cash machine. What’s more, many chip-based cards issued by American and European banks alike still have cardholder data encoded on a magnetic stripe in addition to the chip.
When thieves skim non-U.S. ATMs, they generally sell the stolen card and PIN data to fraudsters in Asia and North America. Those fraudsters in turn will encode the card data onto counterfeit cards and withdraw cash at older ATMs here in the United States and elsewhere.”
Interesting. So chip/swipe/and tap are no bueno.
What about using the Apple pay or other NFC transmission? It is my understanding actual PAN is not sent to the terminal, only a token key and the CVV into the secure element.
https://codeburst.io/how-does-apple-pay-actually-work-f52f7d9348b7
Probly get compromised by a NFC-enabled skimmer. Take a look at how to have more than one NFC scanner monitoring the same structural element. All it takes is for that mode to become more mainstream, and the hackers will start looking into it
Perhaps the question is more like, does the NFC data link have proper encryption put in place? Or is the industry doing it’s usual professional thing & assuming that it’s impossible to have an unofficial device physically touching the same structure? Does the tap area have a security focused standard to be signal isolated from any other part of a terminal & to allow registering a change in ‘sticker height’, should someone attempt to place an overlay on top of the tap area?
And why is it that terminals do not have a visual based object detection to observe if someone is placing anything other than a card anywhere near the reader slots? I won’t have a problem with the machine sounding an alert if my coat sleeve is blocking it’s view of my hands
And this is why I use crypto
I doubt it.
The 3 most common uses for crypto:
1) Criminal activity – the vast majority of legit commercial stores don’t accept it.
2) Speculation – people hoard crypto just to see it’s value rise as others hoard it too. They don’t spend it though, as actually buying things with crypto defeats the purpose.
3) Ideology – People who are suspicious of central banks or authority. There is a desire to see crypto replace other currencies, but of course commercial vendors don’t typically share this ideology.
Hmm, you mean, you’re pro-boil-the-oceans [1].
Glad to hear you care so much about your fellow residents of Terra.
[1] https://www.verdict.co.uk/bitcoin-cryptocurrency-sustainability/
There are some things missing from the article on how the criminals are replaying the compromised data. I would imagine that it would be a shimmer (not skimmer) inserted between the EMV IC and the POS to expel the PAN, and track data in clear text. Otherwise, they would need to use any actual chip data almost instantly before it becomes obsolete with the next attempt. I believe we still have an older version of this type of skimmer from 2-3 years ago pulled off a terminal in a popular grocery store chain. I believe it had GSM not BLE.
The article does explain how the data is used.
It usually exploits backward compatibility.
“Chip-based credit and debit cards are designed to make it infeasible for skimming devices or malware to clone your card when you pay for something by dipping the chip instead of swiping the stripe. But thieves are adept at exploiting weaknesses in how certain financial institutions have implemented the technology to sidestep key chip card security features and effectively create usable, counterfeit cards.
Many people believe that skimmers are mainly a problem in the United States, where some ATMs still do not require more secure chip-based cards that are far more expensive and difficult for thieves to clone. However, it’s precisely because some U.S. ATMs lack this security requirement that skimming remains so prevalent in other parts of the world.
Mainly for reasons of backward compatibility to accommodate American tourists, a great number of ATMs outside the U.S. allow non-chip-based cards to be inserted into the cash machine. What’s more, many chip-based cards issued by American and European banks alike still have cardholder data encoded on a magnetic stripe in addition to the chip.
When thieves skim non-U.S. ATMs, they generally sell the stolen card and PIN data to fraudsters in Asia and North America. Those fraudsters in turn will encode the card data onto counterfeit cards and withdraw cash at older ATMs here in the United States and elsewhere.”
thanks for quoting the article I just read
No problem. Now here’s a quote from the comment you totally read before you replied…
“some things missing from the article”
“There are some things missing from the article on how the criminals are replaying the compromised data. I would imagine that it would be a shimmer (not skimmer) inserted between the EMV IC and the POS to expel the PAN, and track data in clear text… -Oswald The Iron
I agree, some information is missing – Brian Krebs probably holds back some sensitive stuff for various reasons.
The idea of getting the PAN when the “shimmer” is energized extracting data is a possibility.
BK noted, “this skimming apparatus is able to siphon a small amount of that power (a few milliamps) to record any data transmitted by the payment terminal transaction and PIN pad presses”
When looking over BK’s posts and links in the posts there could be many mistakes with the Chip n Pin system and there are a number of possibilities:
“…Chips don’t really do much to help in real security… You can’t rely on sequential chip numbers because not every transaction will be done with a chip. You can’t use them on-line because you don’t have the support for on-line transactions or from the computers making the transaction. And it’s not really more secure in the POS either. The attack vector… against Target was reading in-memory data IIRC, and chips won’t solve that. – TemporalBeing
hxxps://krebsonsecurity[.]com/2015/08/chip-card-atm-shimmer-found-in-mexico/comment-page-1/#comment-390144
The problem of banks CC companies and CC processors taking short cuts:
“…I tested the cards of myself and colleagues with a magstripe reader and chip reader and found that many UK banks still did not implement iCVV despite the bank spokesperson saying that they do. See http://sec.cs.ucl.ac[.]uk/users/smurdoch/papers/ieeesp09tamper%5B.%5Dpdf…” -Steven Murdoch
Hxxps://krebsonsecurity [dot]com/2015/08/chip-card-atm-shimmer-found-in-mexico/comment-page-1/#comment-390321
Mismatch of Data:
“…this shimmer reads the track data from the chip which includes the iCVV/iCVC. The fraudsters then take this data and create a magstripe card? This should never work if the issuer is validating CVV/CVC on their card present magstripe transactions as the iCVV/iCVC that was stolen will never match the true magstripe CVV/CVC…” -Brown
Brian Krebs responds: You’re right. Hence the penultimate paragraph in the story: “Banks can run a simple check to see if any card inserted into an ATM is a counterfeit magnetic stripe card that is encoded with data stolen from a chip card. But there may be some instances in which banks are doing this checking incorrectly or not at all during some periods, and experts say the thieves have figured out which ATMs will accept magnetic stripe cards that are cloned from chip cards.” -BK
hxxps://krebsonsecurity[.]com/2015/08/chip-card-atm-shimmer-found-in-mexico/comment-page-1/#comment-390266
and
hxxps://krebsonsecurity[.]com/2015/08/chip-card-atm-shimmer-found-in-mexico/comment-page-1/#comments
From BK’s recent post “Mexican Politician Removed Over Alleged Ties to Romanian ATM Skimmer Gang” we get a better picture of the planting skimmer job.
The ATM skimmer gang were using inside information, bribing ATM technicians plant skimmers with support from the Attorney General’s office and a lot of manpower to skin tourists. That is real social engineering game to plant hidden skimmers in competitors ATMs and reap the ill gotten gains.
See: “Mexican Politician Removed Over Alleged Ties to Romanian ATM Skimmer Gang” it is self explanatory. A lot of things can be altered. Technology in the wrong hands can do wrong things.
https://krebsonsecurity[dot]com/2021/02/mexican-politician-removed-over-alleged-ties-to-romanian-atm-skimmer-gang/
Excuse all of the errors, I had to bang this out.
I recently changed my ‘usual’ gas station because a new one opened that allows touchless payments inside and at the pump. Unless these guys have found a way to mess with apple pay?
As far as I know… Apple Pay hasn’t been compromised yet. It acts a broker, so there is nothing of value to “skim” at all. Not even backward compatible data that could be used at swipe terminals.
But it does put Apple in between you and your bank. If they ever get compromised in a major hack… then that is a big deal. Also, privacy conscience people might not like Apple knowing about every transaction in the real world.
…i once forgot my wallet and was at some store and needed a printer – so i configured my phone to pay via “tap” and viola it worked fine…
…but here in alaska gas pumps that take the tap are few and far between…
…but the new safeways do…
Hell, finding pumps up here that take chip are few and far between. The Shell stations run by 3 Bears are the only ones I’ve encountered. Which pumps up here take tap? I’ve seen plenty with the reader, but its not enabled.
…the safeway gas stations here in fairbanks, both east and west, have the chip readers, but not the tap, you have to go in the store in the “new” self checkouts to see the tap readers…
You have some big misunderstandings about AP. It’s safer and more anonymous than you realize. Apple isn’t into Hoovering up your personal info; they leave that to the other guys.
Apple is not between you and your bank. When you set up AP, an VX alias card number is stored in your device’s Secure Enclave and is given to the merchant when you pay or debit.
Apple gets no info on what you buy. They do get a transaction amount so they can bill the card issuer for their fees.
The merchant gets no personal info on you because AP only transmits the alias card number and a single use PIN to the network to allow transaction authorization.
Google Pay does the same thing as well.
Brian,
Is it possible, and would you recommend, that we somehow scratch/disable the magnetic stripe in our credit cards?
And maybe keep just one card intact in the closet to be used whenever we travel abroad? (I guess it’s good to be able to get cash if needed)
The “shimmer” seems like it would be tricky to install correctly. Much more difficult to install than a swipe reader overlay that installs in a second or two. I suppose that a shimmer could be installed in a self-checkout lane during a period of low activity when there are few employees watching, but it seems high risk to me.
Where I work we have a tool the thickness of a standard credit card that gets inserted into all pinpads at the end of the day to check for skimmers. Curious if these new skimmers are detectable by said tools or not.
Due to Covid, we have protective overlays on the keypads; I could see how a skimmer’s keypad overlay would now be missed as customers are “trained” to see a silicone cover on the keys.
If I scratch the magnetic strip away from my credit card, so that a reader has no choice but read the chip only, am I safe from thosr skimming devices? After years of reading your blog, I made a habit of covering the keypad while entering my pin, but I now figure this is not enough, if not useless or obsolete. Please advise
I share but can’t answer your question. If I understand Brian’s previous article correctly, ATM units that read the chips need the mag strip to verify card orientation in the slot. (This doesn’t make sense to me as it could use contact to the chip to do this once drawn in. I suspect that in the absence of a strip the machine might not draw in. But it could be that the machine just needs a bit of the strip at the edge to confirm orientation. But I don’t know.)
But one thing I do is to scrape off the 3-digit codes on the back (and additionally the 4-digit on the front if AMEX) and store them in the Autofill section of my Safari settings (this is synced through iCloud to all my Apple devices.). Further, for the newer cards that have the account number printed, not embossed, on the face of the card, I scrape that away and similarly store it too.
These actions don’t solve the mag strip problem but they are better than taking no action at all.
Ps I also don’t sign my cards (why give away a sample of my signature if the card is lost?). Instead I fill the signature block with “Ask For Photo Identification.”
I think it’s possible to rewrite the mag stripe. I’d be more inclined to rewrite it with less data than to just scratch it out. Otherwise you risk having the card rejected by some reader (or worse captured).
I haven’t seen much written about this though…
I pay mostly contactless, but the bigger problem is the online payments, I love to play Online Slots, luckily I`m playing only on certified casinos, not any problem till now. Anyway great article!
Good article. Well done.
In answer to ” is apple pay safer?” Yesterday, yes,tomorrow?
Tap and go has been around since the 80’s. Many individual stores implemented a form of it. They lost money at it. Apple pay is secure right now because of the lack of exposure to money grubbing people. Crooks go for the easy mark, if ap’s exposure gets large enough, it will become big enough to tackle the problems. So, will it become secure tomorrow? No.
Apple Pay is transparent to the reader. The reader thinks it is communicating with an RF chip.
The AP device only gives an alias card number (specific to that device. So if you have a watch and phone, they each have separate and unique alias card numbers. If you additionally have a Mac and iPad too; that would be 4 alias numbers each different from each other and the number on your card.
In addition the AP device delivers a single use PIN code with the alias.
So even if the terminal is compromised, the crooks get an alias number that’s useless because it has to be used in combination with the one time use phone generated PIN code.
Also, the AP device doesn’t submit the number and PIN until you authorize the device to do so.
It’s a lot more secure than a card which has all your info on the faces, and mag strip, and would take an unbelievable magic hack to become useful because AP doesn’t store your account number.
Great reporting!
I don’t worry about my credit cards being skimmed due to zero liability and the fact that my account is setup to notify me immediately of any charges. As for debit don’t have one, have ATM-only card used only for checking acct which is not linked to my savings account so any temporary “loss” from fraudulent activity would be minimal.
If every card and card merchant had the tap feature wouldn’t that end the swipe issue? And yes, someone will build an overlay to read the swipes, but I believe that would be a problem due to the merchant not getting the tap information. I don’t foresee the criminal passing data through his overlay to the merchant so as not to be detected.
Any thoughts on this method?
The need for backwards compatibility is the key vulnerability.
Since there is a need for “some vendor” to “possibly” need it. They card data will have to be available on the mag stripe. And if this data is available, then vendors who don’t use tap or chip/pin EMV… will still want to “fallback” on an insecure method.
Can’t use cash anymore without being severely inconvenienced (just try standing in a shop waiting to pay for gas while 3-4 customers are ahead dumping their chips. cola and hohos on the counter and your kids are out in the car waiting).
Can’t use cards because Brain Krebs says all machines are skimmers so don’t even try
Can’t wave our iphones because a) it’s still not widespread accepted and b) the ever present worry of when it will be eventually hacked (Brian K article coming soon, no doubt)
World’s gone to he!!, no reason to ever go out again. Grow your own crops. Spin and sew your own clothes. Chips rocks to make checkers and chess pieces for entertainment. Etc. Etc.
Has there ever, in the history here, been a positive, glowing article of what technology is and has done for our lives? Would like to see one just once a year, as the constant barrage of beware, stay on guard, don’t this this, don’t do that, plant your flag always, things are just eternally f#cked, etc, etc…it all gets a bit depressing.
Positive, good news does sell, Brian. Just once or twice. Then, rightfully, you can go back to brow beating us and scaring the beejezus out of everyone in this end of the world digital universe raining down upon us poor apes. (and positive news is not the capture and imprisonment of said offenders of things listed above).
There is some good, very good, news going in the world of “security”.
This blog is for security with a particular focus on “ne’er do wells”. Cyber criminals. It doesn’t really lend itself to a “lighter side” file of articles that would bring you the positive news stories your looking for.
Perhaps you can write a blog yourself, focusing on positive news in cyber security.
On the other hand, the web is full of places to get positive, albeit potentially smoke-up-your-pant-leg “good news”. Then again, maybe there’s no good news on this topic. I read this site because it goes straight to the point of what we need to know without candy coating to make it taste good. There’s good news here, it’s just in how you interpret the info – if you can handle the truth. Finding out what is going on for real, that’s what I call good news. Also, part of the problem is that there isn’t really good news to most of this. That’s why this site is so valuable. Thank you Brian! Looking forward to the next skimming article that explains what we can do to not get taken advantage of by the chip card powered skimmers.
Perhaps the question is more like, does the NFC data link have proper encryption put in place? Or is the industry doing it’s usual professional thing & assuming that it’s impossible to have an unofficial device physically touching the same structure? Does the tap area have a security focused standard to be signal isolated from any other part of a terminal & to allow registering a change in ‘sticker height’, should someone attempt to place an overlay on top of the tap area?
For me, it’s inspirational to learn how clever and devious human beings can be in the pursuit of ill-gotten gains. If ever there were a cocktail party again, this blog provides gems of information for conversation. How can you not smile after leaving this blog?
Yeah adimire romanian tech skimmers see how good is engeneered ?
Admire it so closely
and Wait for the nexts..
Mtfk
Admire romanin tech skimmer, see how good engeneered ??
Admire very closely
and wait for the next one in ur
butHOLE
The fuel pump industry has for years won delay after delay in implementing more secure payment requirements for cards (primarily by flexing their ability to favor their own fuel-branded cards, which largely bypass the major credit card networks).
Apple Pay and Google Pay have a process change by allowing people to use the app pay for gas. I used it recently and it is much better than sticking card in the machine.
So doing all this only gets you the chip track data (which can’t be used as magstripe) and the PAN and expiry which may be able to be used online in merchants that don’t require CVV/CVC2. What’s the issue?
Does this work the same as an RFID wallet? I recently got my RFID waterproof wallet from Silent Pocket, and I love everything about it. I feel more safe walking with my cards in town.