A ransomware group called Dark Angels made headlines this past week when it was revealed the crime group recently received a record $75 million data ransom payment from a Fortune 50 company. Security experts say the Dark Angels have been around since 2021, but the group doesn’t get much press because they work alone and maintain a low profile, picking one target at a time and favoring mass data theft over disrupting the victim’s operations.

Image: Shutterstock.
Security firm Zscaler ThreatLabz this month ranked Dark Angels as the top ransomware threat for 2024, noting that in early 2024 a victim paid the ransomware group $75 million — higher than any previously recorded ransom payment. ThreatLabz found Dark Angels has conducted some of the largest ransomware attacks to date, and yet little is known about the group.
Brett Stone-Gross, senior director of threat intelligence at ThreatLabz, said Dark Angels operate using an entirely different playbook than most other ransomware groups. For starters, he said, Dark Angels does not employ the typical ransomware affiliate model, which relies on hackers-for-hire to install malicious software that locks up infected systems.
“They really don’t want to be in the headlines or cause business disruptions,” Stone-Gross said. “They’re about making money and attracting as little attention as possible.”
Most ransomware groups maintain flashy victim leak sites which threaten to publish the target’s stolen data unless a ransom demand is paid. But the Dark Angels didn’t even have a victim shaming site until April 2023. And the leak site isn’t particularly well branded; it’s called Dunghill Leak.
The Dark Angels victim shaming site, Dunghill Leak.
“Nothing about them is flashy,” Stone-Gross said. “For the longest time, they didn’t even want to cause a big headline, but they probably felt compelled to create that leaks site because they wanted to show they were serious and that they were going to post victim data and make it accessible.”
Dark Angels is thought to be a Russia-based cybercrime syndicate whose distinguishing characteristic is stealing truly staggering amounts of data from major companies across multiple sectors, including healthcare, finance, government and education. For large businesses, the group has exfiltrated between 10-100 terabytes of data, which can take days or weeks to transfer, ThreatLabz found.
Like most ransom gangs, Dark Angels will publish data stolen from victims who do not pay. Some of the more notable victims listed on Dunghill Leak include the global food distribution firm Sysco, which disclosed a ransomware attack in May 2023; and the travel booking giant Sabre, which was hit by the Dark Angels in September 2023.
Stone-Gross said Dark Angels is often reluctant to deploy ransomware malware because such attacks work by locking up the target’s IT infrastructure, which typically causes the victim’s business to grind to a halt for days, weeks or even months on end. And those types of breaches tend to make headlines quickly.
“They selectively choose whether they want to deploy ransomware or not,” he said. “If they deem they can encrypt some files that won’t cause major disruptions — but will give them a ton of data — that’s what they’ll do. But really, what separates them from the rest is the volume of data they’re stealing. It’s a whole order of magnitude greater with Dark Angels. Companies losing vast amounts of data will pay these high ransoms.”
So who paid the record $75 million ransom? Bleeping Computer posited on July 30 that the victim was the pharmaceutical giant Cencora (formerly AmeriSourceBergen Corporation), which reported a data security incident to the U.S. Securities and Exchange Commission (SEC) on February 21, 2024.
The SEC requires publicly-traded companies to disclose a potentially material cybersecurity event within four days of the incident. Cencora is currently #10 on the Fortune 500 list, generating more than $262 billion in revenue last year.
Cencora did not respond to questions about whether it had made a ransom payment in connection with the February cybersecurity incident, and referred KrebsOnSecurity to expenses listed under “Other” in the restructuring section of their latest quarterly financial report (PDF). That report states that the majority of the $30 million cost in “Other” was associated with the breach.
Cencora’s quarterly statement said the incident affected a standalone legacy information technology platform in one country and the foreign business unit’s ability to operate in that country for approximately two weeks.
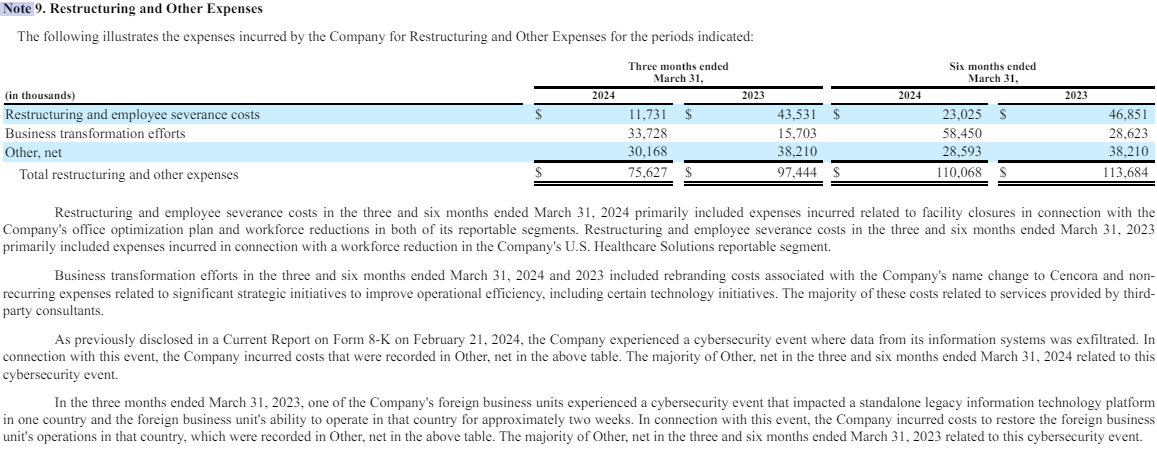
Cencora’s 2024 1st quarter report documents a $30 million cost associated with a data exfiltration event in mid-February 2024.
In its most recent State of Ransomware report (PDF), security firm Sophos found the average ransomware payment had increased fivefold in the past year, from $400,000 in 2023 to $2 million. Sophos says that in more than four-fifths (82%) of cases funding for the ransom came from multiple sources. Overall, 40% of total ransom funding came from the organizations themselves and 23% from insurance providers.
Further reading: ThreatLabz ransomware report (PDF).




No honor among thieves.
How is it possible to know, specifically and certainly, that somebody collected 75 million dollars from a “Fortune 50 company”, without knowing that company’s name with equal certainty and specificity?
… and why, *why* is it still legal to pay these ransoms?
Presumably because nothing in the SEC disclosure requirements require victim companies to clearly state when they have paid a ransom demand, and if so what their outlays for that are. Because then these disclosures would actually be useful.
I’m still not understanding. Where did the “75 million dollars” and “Fortune 50” information come from in the first place?
If it came from Dark Angels, well, it’s worth knowing that they *say* that happened, but I don’t implicitly *believe* them. At the least the fact that it came from them is noteworthy and should follow the information around.
If it came from “security experts”, how come they’re not naming names? If they don’t *know* the names, then how are they getting the “Fortune 50” information? And where do they say *they* got whatever information they have? And for that matter who are they? Some people are more credible than others.
There are a number of security professionals (and firms) that track cryptocurrency platforms and assets known to be used by known threat groups. And sometimes that monitoring shows these groups receiving huge payouts. The ransom groups will often briefly list or reference new victims without publishing their data, mainly as a way to pressure the victim into paying. At which point the ransom group removes the victim’s name from their site. That removal is tracked by different parties as well, and often it’s not hard to draw a correlation between payments and the resumption of operations. I’m not saying that’s exactly what happened here, but that’s my understanding.
How much could it have cost that company to have a first-rate computer system and department, with a person in charge who is on the Board or reports directly to the CEO? The CEO and board committee responsible for computer security should be fired forthwith, with no bonuses or other financial rewards for their laxness.
For one year? Or a full OPex vision for persistent security in the enterprise? In other words… over 10 years, $75M save on this ransomware translates to spending $7.5M / year. This, I think, is what all of us in InfoSec struggle with working through the financial side of their enterprise: this kind of compromise is not a one-off event, until you invest in re-architecting the security controls, after which you can prevent this specific security vector. But! It should be obvious that there will be other major incidents.
That is an InfoSec professional perspective, NOT a business perspective.
From their side: I’ve paid this $75M, I cannot afford to put up *another* $7.5M/year for staff and tools, I have to hope that I can make it 10 years before another such event after a 3rd party comes in and fixes what they can, year 1, for lets say: $2M. After all, the next breach will only be $2M as Brian notes above. I can swallow that almost 2x / year w/out the business rework for InfoSec.
‘C’ managers are not smart – they are your normal high-school popular kids now turned adult, they can talk, socialize and politicize. While there are exceptions, ours is not their world, and they do not like you for including them in it!
“ours is not their world, and they do not like you for including them in it!”
Bravo! Somebody actually said the quiet bit out loud.
Problem is, they don’t understand and don’t want to understand; until it affects them.
*IT operations running smoothly*; “What are we f##king paying you for?”
*Sh#t is really hitting the fan*; “What are we f##king paying you for?”
The vast majority of IT operations can be mundane and boring but all the automation in the world will not replace a well trained set of eyes keeping things running smoothly. Keeping systems and processess polished comes at a cost.
Effective IT managers have to upskill themselves in finance, forecasting and risk just so they can successfully communicate their requirements to keep an organisation safe and secure, and even then they have to fight tooth and nail for basic needs.
It is a shame C Suite can’t even be bothered to meet them halfway and learn the basics so they can better understand issues and make better judgement calls going forward. *Shrugs*
I hope to see greater collaboration between the private sector, law enforcement, and the cybersecurity community to identify, disrupt, and dismantle groups like the Dark Angels.
Not at all. What you will see is prolification of Crowdstrike-like “cyber-secoority” sham services which do more harm than those who they supposed to protect against
You are SO spot on/correct.
And to think, in any Fortune 500 company with thousands of endpoint devices, all that is needed to exfiltrate data at scale is one un-monitored endpoint. More like 500 fish in a barrel…
Brian, has there been any indication of how the initial breach occurred ? Was it social engineering, poor patching regime, etc ? Thanks for your continued insights btw !
Brian, any evidence on how the initial breach was achieved ? Was it social engineering, a poor patching regime, etc ?
I’m sorry I don’t have any of that information. It’s possible that could come to light at some point, but I doubt it will come voluntarily from the victim.
I’m tired of these companies paying the thieves. The data is arguably out on the Internet once it’s exfiltrated from the source, right? Perhaps this group is different, and they really do wipe the data once the ransom is paid. If companies stopped paying, would the ransomware organizations cease to exist? It’s just frustrating to see how effective these organizations are.
If ransomware payments were never made, it may stop some of these groups. But there are other ways to make money off stealing company data like offering the stolen data to a competitor for a price. And there are hackers in certain countries that specifically want to see US companies (and governments) fail so they will continue to do whatever they can to interfere with being able to conduct business. And there are those that just “do it for the lulz.”
Having said that, $75 millon is a great incentive to other hacker groups to do the same.
A person who wants to spite the mugger can say “I’m not giving you my ATM PIN” and take the bullet. A company can’t do that, as they’re answerable to their shareholders. Any officer who did something that decreased shareholder value, such as failing to pay the ransom and letting the criminals destroy the company, would be subject to lawsuits.
That is a load of BS and a right cop out. The mindset of the general public and government officials needs to change drastically concerning the handling and protection of data, whether it be confidential company or personally identifiable information. Legislation needs to be passed that hold C Suite FULLY accountable by way of REAL penalties that include gaol time and not just puny fines that just become a cost of doing business. Until that risk is placed at Directors/Boards feet NOTHING will change and only embolden and strengthen hacker groups with the resources to do more. Lock down security properly, take the reward away and the incentive decreases. Shares would go up and shareholders would be happy they’re not losing $75M in dividends everytime there is a breach.
It would take a politician/s with real balls to ignore lobbyists and affect real change globally, but one can live in hope.
Boards of investors can file lawsuits over literally anything they like. That doesn’t mean they’ll win.
As long as criminals can make money the groups like Dark Angels do then they will never go away. That is the new reality we live in. I miss the days before the Internet, because it has become almost like the old west where the man (or woman) with the biggest and fastest gun wins. Until companies like Microsoft, Apple, Google, etc. make the technology impregnable to attacks they will just keep coming; again welcome to the new reality. Happy 2024 so looking forward to 2025.
I was shocked a few minutes ago when I told a relative about this and he expressed the opinion that no government should prosecute frauds or other crimes.
He seems to be of the opinion that if someone steals from you, it is your fault for letting them steal and that whatever they stole is now theirs to keep.
For what it’s worth, I have long thought that his ideas were pretty much along the lines of sovereign citizens. I’m now convinced that more that ever.
Watch out for the relative if he claims to be a sovereign citizen.
https://youtu.be/9Fu05LodYlA?si=epxrKTBuTmolS9MW
Brian, will you write about WWH breach?
https://storage.courtlistener.com/recap/gov.uscourts.flsd.672601/gov.uscourts.flsd.672601.1.0.pdf
Great summary. Microsoft has been the target of attacks because of its market share.