An old but persistent email scam known as “sextortion” has a new personalized touch: The missives, which claim that malware has captured webcam footage of recipients pleasuring themselves, now include a photo of the target’s home in a bid to make threats about publishing the videos more frightening and convincing.

This week, several readers reported receiving sextortion emails that addressed them by name and included images of their street or front yard that were apparently lifted from an online mapping application such as Google Maps.
The message purports to have been sent from a hacker who’s compromised your computer and used your webcam to record a video of you while you were watching porn. The missive threatens to release the video to all of your contacts unless you pay a Bitcoin ransom. In this case, the demand is just shy of $2,000, payable by scanning a QR code embedded in the email.
Following a salutation that includes the recipient’s full name, the start of the message reads, “Is visiting [recipient’s street address] a more convenient way to contact if you don’t take action. Nice location btw.” Below that is the photo of the recipient’s street address.
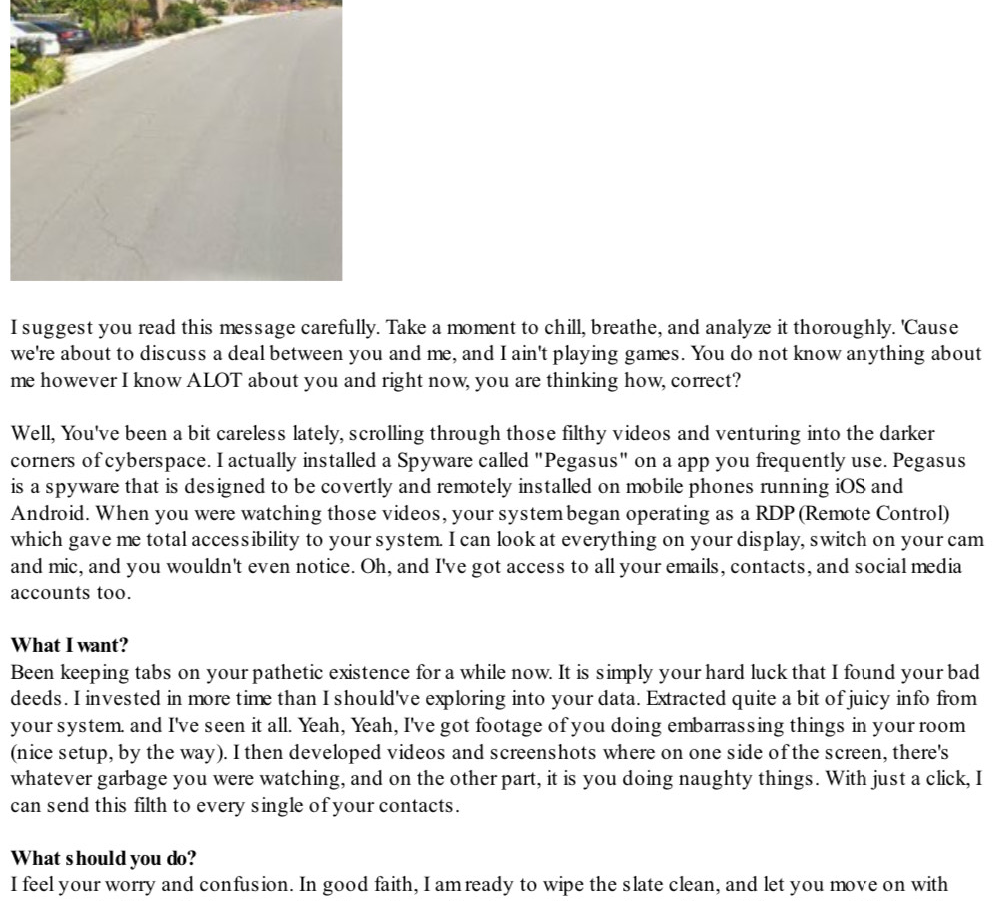
A semi-redacted screenshot of a newish sextortion scam that includes a photo of the target’s front yard.
The message tells people they have 24 hours to pay up, or else their embarrassing videos will be released to all of their contacts, friends and family members.
“Don’t even think about replying to this, it’s pointless,” the message concludes. “I don’t make mistakes, [recipient’s name]. If I notice that you’ve shared or discussed this email with someone else, your shitty video will instantly start getting sent to your contacts.”
The remaining sections of the two-page sextortion message (which arrives as a PDF attachment) are fairly formulaic and include thematic elements seen in most previous sextortion waves. Those include claims that the extortionist has installed malware on your computer (in this case the scammer claims the spyware is called “Pegasus,” and that they are watching everything you do on your machine).
Previous innovations in sextortion customization involved sending emails that included at least one password they had previously used at an account online that was tied to their email address.
Sextortion — even semi-automated scams like this one with no actual physical leverage to backstop the extortion demand — is a serious crime that can lead to devastating consequences for victims. Sextortion occurs when someone threatens to distribute your private and sensitive material if you don’t provide them with images of a sexual nature, sexual favors, or money.
According to the FBI, here are some things you can do to avoid becoming a victim:
-Never send compromising images of yourself to anyone, no matter who they are — or who they say they are.
-Don’t open attachments from people you don’t know, and be wary of opening attachments even from those you do know.
-Turn off [and/or cover] any web cameras when you are not using them.
The FBI says in many sextortion cases, the perpetrator is an adult pretending to be a teenager, and you are just one of the many victims being targeted by the same person. If you believe you’re a victim of sextortion, or know someone else who is, the FBI wants to hear from you: Contact your local FBI office (or toll-free at 1-800-CALL-FBI).




I got one of these emails today. They didn’t even have the right address, but a place of business for their “house picture.” Bunch of idiots.
Got one myself today. My cam is covered even if it wasn’t and they wanted to watch me in my room they would be bored. just the dog and I fighting over the covers. But hey , whatever floats his boat. Watch on.
I got this kind of mail once asking me to pay the ransom for watching porn and pretending that they have a picture of me watching and enjoying prorno, which was completely a fake approach, my password got compromised once and I was getting a bunch of emails with porno.
I got one from the email krcwkraig2@gmail.com
I gotten same in my gmail.
Guys do be proactive and report please:.
https://www.ic3.gov/Home/FileComplaint
download complete email (eml w headers)
contact the from: originating email provider to report a cybercrime (extortion).
Do something, do not just ignore.
Super
I gotten same in my gmail.
Guys do be proactive and report please:.
https://www.ic3.gov/Home/FileComplaint
download complete email (eml w headers)
contact the from: originating email provider to report a cybercrime (extortion).
Do something, do not just ignore.
Super
Hello,
I’ve already received the same emails this month on my website. Obivously, I just blocked it after I read that trash. I also reported to the spam. Please tell me, What else we can do?
https://www.celoxis.com/
Anyone able to share the email details? Did anyone pass the 24 hour mark, did anything happen?
nothing will happen this is an old scam with a slightly new twist.
This just happened. I called the fbi line but it just tells you to report it to wwwic3.gov
I received this email yesterday. It is scary when they have your full name, address, photo of your house and cell #. I am relieved to hear several others received the same email and that it’s fake.
I just got another one of these today and it came from a Gmail address (yet again). Why can’t Google prevent the abuse of their platform?
Wait you mean it was a scam?
awww I just sent them the 2000 in bitcoin.. i knew it was fishy cuz i dont watch porn.
I received this message today, with a photo of my home, my address, and my cell phone number. Very unnerving, to say the least. Tried to report it to ic3 but the form seems to be for people who actually got scammed out of $$, not just solicited.