The FBI and authorities in The Netherlands this week seized dozens of servers and domains for a hugely popular spam and malware dissemination service operating out of Pakistan. The proprietors of the service, who use the collective nickname “The Manipulaters,” have been the subject of three stories published here since 2015. The FBI said the main clientele are organized crime groups that try to trick victim companies into making payments to a third party.
One of several current Fudtools sites run by the principals of The Manipulators.
On January 29, the FBI and the Dutch national police seized the technical infrastructure for a cybercrime service marketed under the brands Heartsender, Fudpage and Fudtools (and many other “fud” variations). The “fud” bit stands for “Fully Un-Detectable,” and it refers to cybercrime resources that will evade detection by security tools like antivirus software or anti-spam appliances.
The Dutch authorities said 39 servers and domains abroad were seized, and that the servers contained millions of records from victims worldwide — including at least 100,000 records pertaining to Dutch citizens.
A statement from the U.S. Department of Justice refers to the cybercrime group as Saim Raza, after a pseudonym The Manipulaters communally used to promote their spam, malware and phishing services on social media.
“The Saim Raza-run websites operated as marketplaces that advertised and facilitated the sale of tools such as phishing kits, scam pages and email extractors often used to build and maintain fraud operations,” the DOJ explained.
The core Manipulaters product is Heartsender, a spam delivery service whose homepage openly advertised phishing kits targeting users of various Internet companies, including Microsoft 365, Yahoo, AOL, Intuit, iCloud and ID.me, to name a few.
The government says transnational organized crime groups that purchased these services primarily used them to run business email compromise (BEC) schemes, wherein the cybercrime actors tricked victim companies into making payments to a third party.
“Those payments would instead be redirected to a financial account the perpetrators controlled, resulting in significant losses to victims,” the DOJ wrote. “These tools were also used to acquire victim user credentials and utilize those credentials to further these fraudulent schemes. The seizure of these domains is intended to disrupt the ongoing activity of these groups and stop the proliferation of these tools within the cybercriminal community.”
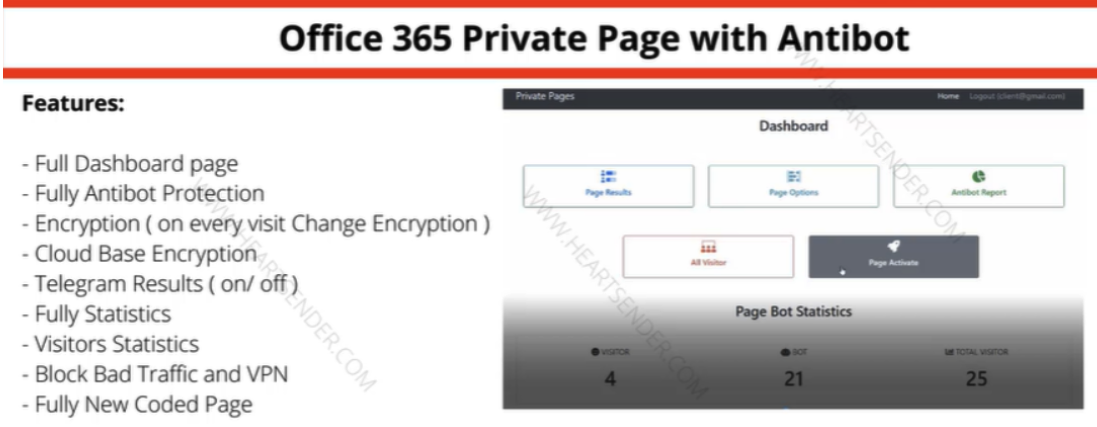
Manipulaters advertisement for “Office 365 Private Page with Antibot” phishing kit sold via Heartsender. “Antibot” refers to functionality that attempts to evade automated detection techniques, keeping a phish deployed and accessible as long as possible. Image: DomainTools.
KrebsOnSecurity first wrote about The Manipulaters in May 2015, mainly because their ads at the time were blanketing a number of popular cybercrime forums, and because they were fairly open and brazen about what they were doing — even who they were in real life.
We caught up with The Manipulaters again in 2021, with a story that found the core employees had started a web coding company in Lahore called WeCodeSolutions — presumably as a way to account for their considerable Heartsender income. That piece examined how WeCodeSolutions employees had all doxed themselves on Facebook by posting pictures from company parties each year featuring a large cake with the words FudCo written in icing.
A follow-up story last year about The Manipulaters prompted messages from various WeCodeSolutions employees who pleaded with this publication to remove stories about them. The Saim Raza identity told KrebsOnSecurity they were recently released from jail after being arrested and charged by local police, although they declined to elaborate on the charges.
The Manipulaters never seemed to care much about protecting their own identities, so it’s not surprising that they were unable or unwilling to protect their own customers. In an analysis released last year, DomainTools.com found the web-hosted version of Heartsender leaked an extraordinary amount of user information to unauthenticated users, including customer credentials and email records from Heartsender employees.

Almost every year since their founding, The Manipulaters have posted a picture of a FudCo cake from a company party celebrating its anniversary.
DomainTools also uncovered evidence that the computers used by The Manipulaters were all infected with the same password-stealing malware, and that vast numbers of credentials were stolen from the group and sold online.
“Ironically, the Manipulaters may create more short-term risk to their own customers than law enforcement,” DomainTools wrote. “The data table ‘User Feedbacks’ (sic) exposes what appear to be customer authentication tokens, user identifiers, and even a customer support request that exposes root-level SMTP credentials–all visible by an unauthenticated user on a Manipulaters-controlled domain.”
Police in The Netherlands said the investigation into the owners and customers of the service is ongoing.
“The Cybercrime Team is on the trail of a number of buyers of the tools,” the Dutch national police said. “Presumably, these buyers also include Dutch nationals. The investigation into the makers and buyers of this phishing software has not yet been completed with the seizure of the servers and domains.”
U.S. authorities this week also joined law enforcement in Australia, France, Greece, Italy, Romania and Spain in seizing a number of domains for several long-running cybercrime forums and services, including Cracked and Nulled. According to a statement from the European police agency Europol, the two communities attracted more than 10 million users in total.
Other domains seized as part of “Operation Talent” included Sellix, an e-commerce platform that was frequently used by cybercrime forum members to buy and sell illicit goods and services.




Wow! Just … wow. Amazing article. Thanks, Brian.
You said it all, Donna.
It’s kind of ironic to be praising the Dutch for recognizing a Tulip Bubble when they see one, but word seems to be getting around in the Law Enforcement Community.
The united states government (the international law by now probably) is so blatantly over reaching… crazy. thankfully police and courts still remain independent and have to follow local laws.
Transnational organised crime by its very nature (and naming convention) is syndicated criminal groups operating in tandem across borders. So when domestic investigators chasing leads, find themselves in another jurisdiction, their hands are tied and cannot act without the collaboration of local law enforcement in that jurisdiction. I don’t know what is so hard to understand about that, seriously, Interpol has been around since 1923.
These fools think they are safe operating out of Pakistan, but if they were coordinating off hardware based out of The Netherlands and targeting victims in the US, well more fool them. It looks like the Dutch have taken point on this and seized their local servers/domains but the US DOJ will hound them for the rest of their lives for reparations and I for one don’t have a problem with that.
What’s overreaching about seizing domains linked to scammers breaking local and international laws?
Nothing at all, silly. Those seizures go through the courts just like anything else.
wth is even this, a birthday cake? stolen accounts? ehhhh, of course they never cared? anyway hopefully we’ll hear more news about nulled soon
Brian, is there any news about the seizures of cracked[.]io, cracked[.]to, nulled [.]to, starkrdp[.]io, mysellix[.]io, and individuals behind them?
I’m also awaiting more information on this from krebs. All these other news articles rehashes on the topic don’t do it the “krebs deep dive” it deserves
normally, Brian is fairly open with content and not shy of naming names. I suspect that in this case, authorities may have asked him to withhold some of that due to ongoing investigation.
To be quite honest, when I read this article, I did feel a wee bit more compassion with the perpetrators, maybe because they were not shown with pictures showing an unsympathetic person with their overpriced sportscar, but rather a corporate cake, which shows at least some degree of being nice to their employees. I admit that’s not logical, but maybe it is because I like cake a lot 😀
https://www.ccinfo.nl/menu-nieuws-trends/opsporing/opsporing-cyber-nieuws/2298821_heartsender-opgerold-internationale-samenwerking-legt-phishingnetwerk-lam
Good news for a change. Thanks for your deep dive, Brian.
As for the perps, I’m amazed that they stay in their sh#t countries (obviously being immune from prosecution) and then use our equipment and infrastructure to attack us. What do you expect gonna happen, dummies?
This is ironic because there are thousands if not millions of illegal spam hives in the NL, and Politie refuses to do anything. The list is a mile long.
because it’s not illegal. leave these people alone. netherlands is independent country.
Ok, independent country, but interconnected internet. So the solution is to mandate that criminal scammers using a country as a safe haven results in that country having an “independent” internet. A localnet. They don’t necessarily have a “right” to the w3 if they’re going to abuse the system everyone else pays for, which they don’t own and independently operate.
Good to see these guys finally faced the long arm of the law.