Anyone who’s run a Web site is probably familiar with the term “malvertising,” which occurs when crooks hide exploits and malware inside of legitimate-looking ads that are submitted to major online advertising networks. But there’s a relatively new form of malware-based advertising that’s gaining ground — otherwise harmless ads for illicit services that are embedded inside the malware itself.
At its most basic, this form of advertising — which I’m calling “crimevertising” for want of a better term — has been around for many years. Most often it takes the form of banner ads on underground forums that hawk everything from cybercriminal employment opportunities to banking Trojans and crooked cashout services. More recently, malware authors have started offering the ability to place paid ads in the Web-based administrative panels that customers use to control their botnets. Such placements afford advertisers an unprecedented opportunity to keep their brand name in front of the eyeballs of their target audience for hours on end.
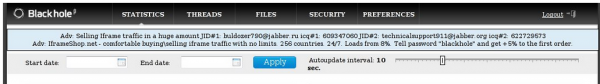
The author of the Blackhole exploit pack is selling ad space on his kit's administration page, as seen in this screenshot.
A perfect example of crimevertising 2.0 is the interface for the Blackhole Exploit Kit, crimeware that makes it simple for just about anyone to build a botnet. The business end of this kit is stitched into hacked or malicious Web sites, and visitors with outdated browser plugins get redirected to sites that serve malware of the miscreant’s choosing. Blackhole users can monitor new victims and the success rates of the compromised sites using a browser-based administrative panel.
In the screen shot above, the administration panel of a working Blackhole exploit kit shows two different ads; both promote the purchase and sale of Internet traffic. And here is a prime example of just how targeted this advertising can be: The most common reason miscreants purchase Internet traffic is to redirect it to sites they’ve retrofitted with exploit kits like Blackhole.
 I wanted to find out how much it would cost to place such targeted ads, so I chatted up the author of this kit — a hacker who uses the nickname “Paunch.” He said an ad that would run on administration panels across the entire Blackhole user base would cost me $700 per month. He declined to say just how many “impressions” that money would buy, or exactly how many Blackhole users there are today.
I wanted to find out how much it would cost to place such targeted ads, so I chatted up the author of this kit — a hacker who uses the nickname “Paunch.” He said an ad that would run on administration panels across the entire Blackhole user base would cost me $700 per month. He declined to say just how many “impressions” that money would buy, or exactly how many Blackhole users there are today.
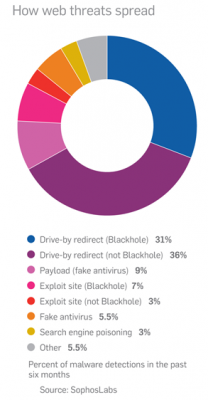
But it’s probably quite an audience: According to security firm Sophos, Blackhole is now by far the most popular method of delivering drive-by attacks. In its 2012 Security Threat Report, the company found that “in the second half of 2011, 67% of [malware] detections were redirections on compromised legitimate sites. Of these, approximately half are believed to be redirections to Blackhole exploit sites.”
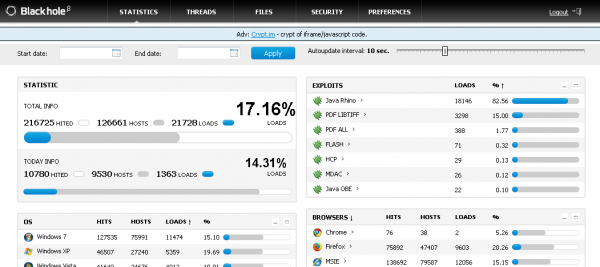
Interestingly, when Paunch doesn’t have ads to run from paying customers, he runs ads for his own ancillary services. In the screen shot below (taken from a different working Blackhole exploit kit) Paunch can be seen pitching his subscription-based malware obfuscation service.
I suppose it’s possible that miscreants could try to place malware-laced crimevertisements in a bid to hijack the browsers of other hackers, but that’s probably unlikely to happen as long as malware authors like Paunch are manually reviewing purchased ads and disallowing anything other than plain text. In the end, crimeware kit buyers may have more to fear from a kit’s author himself: The author of the infamous SpyEye botnet creation kit once acknowledged adding a hidden backdoor to his software that let him remotely access all customer installations.




What character set did you use to make that post? The apostrophes and quotation marks look weird when converted to UTF-8…
I’m not really sure that we need yet another term for this practise such as “crimevertising”. It’s just another ad network and advertising certain good and services really isnt it?
I guess it does replace descriptions like “advertising goods services of a criminal nature” but still …
In any case another interesting article on a world mostly hidden to those not operating within it. Thanks.