TalkTalk, a British phone and broadband provider with more than four million customers, disclosed Friday that intruders had hacked its Web site and may have stolen personal and financial data. Sources close to the investigation say the company has received a ransom demand of approximately £80,000 (~USD $122,000), with the attackers threatening to publish the TalkTalk’s customer data unless they are paid the amount in Bitcoin.
 In a statement on its Web site, TalkTalk said a criminal investigation was launched by the Metropolitan Police Cyber Crime Unit following “a significant and sustained cyberattack on our website.”
In a statement on its Web site, TalkTalk said a criminal investigation was launched by the Metropolitan Police Cyber Crime Unit following “a significant and sustained cyberattack on our website.”
“That investigation is ongoing, but unfortunately there is a chance that some of the following data has been compromised: names, addresses, date of birth, phone numbers, email addresses, TalkTalk account information, credit card details and/or bank details,” the statement continues. “We are continuing to work with leading cyber crime specialists and the Metropolitan Police to establish exactly what happened and the extent of any information accessed.”
A source close to the investigation who spoke on condition of anonymity told KrebsOnSecurity that the hacker group who demanded the £80,000 ransom provided TalkTalk with copies of the tables from its user database as evidence of the breach. The database in question, the source said, appears related to at least 400,000 people who have recently undergone credit checks for new service with the company. However, TalkTalk’s statement says it’s too early to say exactly how many customers were impacted. “Identifying the extent of information accessed is part of the investigation that’s underway,” the company said.
It appears that multiple hacker collectives have since claimed responsibility for the hack, including one that the BBC described as a “Russian Islamist group” — although sources say there is absolutely no evidence to support that claim at this time.
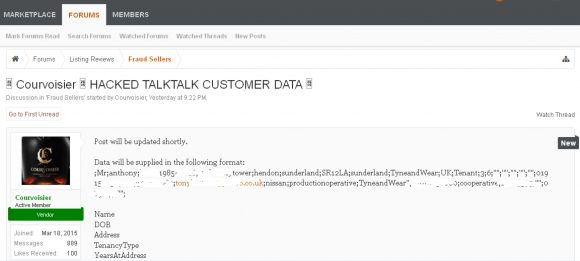
Separately, promises to post the stolen data have appeared on AlphaBay, a Deep Web black market that specialized in selling stolen goods and illicit drugs. The posting was made by someone using the nickname “Courvoisier.” This member, whose signature describes him as “Level 6 Fraud and Drugs seller,” appears to be an active participant in the AlphaBay market with many vouches from happy customers who’ve turned to him for illegal drugs and stolen credit cards, among other goods and services.
It seems likely that Courvoisier is not bluffing, at least about posting some subset of TalkTalk customer data. According to a discussion thread on Reddit.com dedicated to explaining AlphaBay’s new Levels system, an AlphaBay seller who has reached the status of Level 6 has successfully consummated at least 500 sales worth a total of at least $75,000, and achieved a 90% positive feedback rating or better from previous customers.
“Post will be updated shortly,” Courvoisier promised in an AlphaBay message thread Friday. “Data will be supplied in the following format:
Name
DOB
Address
TenancyType
YearsAtAddress
MonthsAtAddress
HomeTelephone
MobileTelephone
Email
Employer
EmploymentTitle
EmploymentLocation
EmployersPhone
Bank
AccountNumber
SortCode”
This roughly tracks the details that TalkTalk has said might have been accessed on customers:
Name
DOB
Address
Email Address
Telephone Number
TalkTalk Account Information
Credit Card and Bank Details
According to my source, the intrusion started with an attack technique known as SQL injection (SQLi), a method which abuses a misconfiguration in a database that causes the database to cough up or dump information. The source said the SQLi attack was punctuated by a denial-of-service attack that sought to prevent legitimate users from visiting the targeted site, and that the debilitating assault may have been launched to distract from the database hack.
Several individuals on Twitter also have been posting information suggesting they may know how the breach occurred, and that there were only a few thousand customer records exposed in the breach.
On October 18, 2015, a person using the screen name “Fearful” and alias “Glubz” reported a vulnerability in the videos section of TalkTalk’s Web site (videos.talktalk.co.uk). The flaw was reported via xssposed.org, a site that operates as a sort of public clearinghouse for information about unpatched Web site vulnerabilities. Xssposed.org said it verified the flaw indeed existed in the TalkTalk videos page, but that no technical details were being disclosed to the public in order to give website owner time to patch the vulnerability without putting its users at risk.
Interestingly, a Twitter user with the Twitter handle @Fearful has been posting about expecting a raid from the U.K. authorities at any minute. The Twitter profile links to the (possibly compromised) Web site elliottg[dot]net, which currently redirects to a page with scrolling images of a blond-haired young man, the TalkTalk logo, and a U.K. policeman.
A Google-cached version of the site indicates that Glubz has “continuously found website exploits ranging from non critical and critical exploits/bugs. I’ve always wanted to work for a company that specialises in stuff like this and that time has finally come. Being paid for something you enjoy is probably the best job ever. You may also find me on XSSPOSED under the username ‘Glubz‘.” Indeed, a listing at xssed.org ranks Glubz among its Top 50 Security Researchers, and says Glubz’ Twitter handle is “@Fearful”.
TalkTalk apologized for the breach and said that since discovering the breach on Wednesday it has undertaken a full security review of its Web site and had taken “all necessary measures” to secure the site. The company also is offering customers 12 months of free credit monitoring through Noddle, a credit reporting service offered by the credit reference agency CallCredit.
Extortion attacks put victim companies in a bit of bind, because even if they do pay the ransom demand, there is no guarantee the data was not already shared with or stolen by other attackers — or that the extortionists won’t simply go ahead and publish the data even if they are paid.
As I noted in a Reddit Ask Me Anything interview Friday, there is, unfortunately, a great deal of room for growth in cyber attacks that leverage some type of ransom or extortion.
“It seems like the crooks are getting better situational awareness when they break in somewhere, which of course increases the potential for an opportunistic attack (drive-by download, database hack, malware-laden spam blast) to mushroom into something much bigger and more costly for the victim or organization,” I wrote.
Update, 11:17 a.m. ET: Added information about vulnerabilities reported in the video portion of TalkTalk’s Web site.




It’s not just the 4 million existing customers but talktalks ex-customers. Talktalk did not delete ex-customers and their information even when asked to do so, (mail shots through the post point to not deleting).
British data protection law does not give individuals the right to have their data deleted and, in fact, it may have to be kept to meet various regulatory requirements such as compliance with accounting law.
Probably the same requirement for many western countries.
This shows another wide-spread mentality: Why keep so much data online instead of archiving it on off grid solutions? Everywhere i’ve worked so far, there was the same stupid mentality of keeping everything, even decades-old stuff on their online servers. No one was questioning this and the security risk related to it. And still today, I find data older than 2005 on my company’s file server. And I’m talking database extracts made by ex-employees who left 10 years ago and where the file has been left unread and untouched since. Why not put it on an offline backup systems and recall it if needed?
I was told, in case of we needed it… Well, one thing for sure: They’ll need to contact all ex-clients in case of a data breach. ($$$)
The scenario I outlined above is like looking into a prism of CISA (Cybersecurity Information Security Act). Secure cell phone, open cable and software. Like companies justifying their view of morality. The name is fishy to me for personal wire transfer reasons.
Wrong.
Principle 5 requires the deletion of personal/sensitive personal data when the organisation is no longer providing any services to the customer.
In my case, I signed up with TalkTalk, provided all relevant signup info (personal data) but cancelled prior to service being provided. Yet, TalkTalk did not delete my personal data as required. No regulatory need for the data to be kept as no service ever provided.
This is a direct contravention of Principle 5 and I’ll be asking ICO to investigate if their initial report fails to cover it.
alert(“l”)
Cash cow similar name; weird. This is about the money. Need to watch my wallet. TalkTalk seems to think customers safe from having money stolen. Skimmed over the company info and they were accused of slamming in 2005. It’s like US cable companies offering promotional service then upping your rates with a notification letter by 20% or so. When you call they talk about upgrading your service after reviewing what you have watched, not lowering your rates. This is the opposite of how cell phone service has changed. Having problem with phone apps when purchasing hotel stays, pay for a discount price and being charged 50% more. 45 minutes on phone to correct.
I’ve had/seen problems with multiple phones where Verizon tells you you’re using X% of your data limit, would you like to buy more (no, I’m not using that much) only to find it was apps in the background using crazy amounts of data. On my own iphone, it was Mail, Apple’s own app, yet I was unable to actually get my mail onto the phone, which was very easy to see. I kept explaining, I went into the store several times (this is all tactics by them), clear the usage, wait and see, only to show on the fourth time, a month later, that the phone WAS, in fact, NOT receiving data. They structure resistance in, figuring there will be some attrition and people will just give up and pay a bill, fair or not. They’ve got to love defective apps.
Interesting.
In pretty much any other area of commerce, there is a reasonable expectation [and likely legal safeguards] to ensure that a purchaser can have a reasonable expectation of being able to know in advance what they are buying and what it will cost them. If I go to a grocers for a kilo of potatoes and come out with 800g of turnips I’d have cause to complain…
Yet what you [correctly] outline here is a scenario in which a product is offered for sale [an application] that may have no indication of the fact that loading it into your handset is going to cost you money [through i.e. data usage charges] or given you any basic information to enable you to calculate the likely cost such that you can make an informed decision with respect to that purchase.
I completely concur with your assessment, but at the same time would suggest that there is a basic, fundamental flaw in the offering of software applications [for sale or otherwise] when the vendor/party offering the product can have reasonable knowledge that use of the product will bring costs to the client.
Absent such basic information, the vendor simply cannot show that an informed choice can be made.
There are countless examples of case law what would support this view. As a consumer, surely you have a basic right to information that would let you understand the cost of what you are signing up for?
I don’t know UK law, but it seems like there could be some serious liability for Talk Talk here. Why did they have that data stored to begin with? Once you run a credit check, storing detailed information seems iffy to me even absent explicit requests to delete…and it seems there were those too.
Simply paying is no guarantee that the information has not already been, or will be, exposed.
On paying such ransoms Kipling wrote
http://nc3.mobi/references/2014-summary/#20141111
Jonathan @NC3mobi
Brian – I have a few questions. In your expert opinion,
1) What are the methods by which say 90% of data is illegally obtained?
2) What percentage of illegally obtained data is acquired by hacking a database remotely whether through the Internet, poorly constructed networks or whatever vs other methods?
3) Is there any unavoidable reason that sensitive data MUST be online 24/7/365 or are all the reasons ones of convenience and efficiency?
I routinely make payments to my credit card accounts online. It makes it easier for me if I can see exactly how much I owe and how much the last bill was for. I can then authorize a payment based on that information. However, to perform this task does not require that I can see my mailing address or my email address or my credit limit or pretty much anything in my account other than what I owe and the nicknames I have for the bank accounts I use to pay.
If I need to change info in my CC account, why does my account have to be on a server that is online? Yes that is convenient but is it NECESSARY? Why can’t I just submit my request for the change I want, the request be immediately sent to my email address of record and I either send back an approval or the change doesn’t go through? If approved, the request is physically transported to the server containing my account, the change made, and notification of the change goes to my email address of record the next business day. Yes that’s less efficient but I would submit that if holders of sensitive data were required by law to pay the costs caused to consumers of every identity theft they allowed, the costs would be so high that hiring a team to process the physical transport of information between their master databases to online servers would pale to insignificance by comparison. The key is those companies are NOT required to fix the problems their policies allow to occur. It IS cheaper to leave sensitive data online than to segregate it offline.
My last question is, “Why should we consumers pay the costs for data breaches when the companies responsible are making billions of dollars providing us with ostensibly secure services?
Laziness is the basic answer.
You need a database to store account information.
You need a database to store credit report inquiry information.
You need a method to add data to both databases.
You need a method to change billing information for accounts.
You could have careful one-way bridges between the application process and the report inquiry database and another one-way limited data bridge for reporting responses to the inquiries to the account database.
Instead, I’d bet there’s a single database with tables for the different tasks. And clearly no useful data limiting (e.g. limit 10 rows, or limit to a certain number of transactions or a certain amount of data per query).
Diane: Unfortunately, we live in a world where we want X, Y, Z now. Not in 2 minutes and especially not tomorrow. And if company A offers a 5-minute delay service, the competitor will offer it in 2 minutes and so on and on.
Most people will ask for a faster but less-secure service over a slower and secure service. And I don’t see why and where the trend should stop.
One Question, and that is: Do you actually trust the postal mail process to get your package from point a to point b without it getting lost and opened up? Do you trust that the mailbox at your street wont be tampered with, do you trust the blue box won’t be tampered with? Do you trust that the postman will actually deliver the request on time? http://www.reuters.com/article/2015/07/23/us-usa-pennsylvania-mail-idUSKCN0PX26H20150723. I for one do not, and love the fact that I can log in to any of my accounts and change my information on a whim, and report fraudulent charges so the bank can protect me. I also hate dealing with phone support, as the process is far to long and complicated, and not to mention the tech support people I have talked could barely speak English.
Can’t trust postal mail as well. However, when there’s a breach, a limited amount of people is impacted whereas hacking targets thousands/millions of people at once.
Postal mail fraud is easier to investigate than hacking dealing with international frontiers. Prosecution rate is much much higher (I presume)
How much of our mail actually contains our DoB, SSN, CC info, etc.? While online databases containing these information is just sitting there, waiting to be stolen by hackers.
Brian
The TalkTalk CE, Dido Harding, was asked in several interviews she gave on Friday that she did not know if any of the data was unencrypted.
Firstly, that is such a fundamental question, and scary to her customers. I am amazed she did not have an answer to it. She had several hours between the interviews to find the answer.
Secondly, are there any circumstances when personal data would be held in plain text?
Brian
Oh I think she knew. I just don’t think she wanted to tell everyone the true answer.
I think we, and especially the media, are being a little unfair on the CEO – to a degree. Unless you know exactly where within the transaction process or infrastructure the data was compromised you may not be able to give a definitive answer as to whether the data was/should have been encrypted.
Securing the data in transit (ie. across networks) and whilst at rest (ie. in databases) is considered security best practice (lets not go into why majority of businesses consistently fail to, or don’t, implement best practice) – however, at some stage an application will need to process ‘clear text’ data to fulfil the transaction … unless utilising something like tokenisation …
That said … TalkTalk would appear to have been grossly negligent in their duty of care to protect both themselves and, critically, their customer information.
The only point in ‘clear text’ is to make it human readable. Clear text is a non-issue when the sender and the receiver understand and agree with each other that a data set actually does mean a particular thing (software to software, computer to computer). This gets to the very spirit of encryption in the first place. The use of tokens becomes just a method.
Plot twist: Krebs pays Vrubelvski (spam nation, anyone?) to hack TalkTalk so he can promote his AMA on Reddit 🙂
On a serious note, I’ve read a report saying that credit card numbers are stored on another server and with X’s for most the numbers. Probably just bluff on the hackers end.
I get your joke, but unfortunately, breaches and data leaks are now a byproduct of the services they offer. Perpetual motion may not exist in real life, but in the IT world, it exists and its accelerating… (data leaks rate and such.)
They’ll release the info anyway … better to go after these criminals and throw them in prison then give in.
They’ll never sit in jail unless they set foot in a country where extradition laws to UK exist.
It’s Noddle, not Noodle . The credit rating site
Not sure I see the point here.
Bitcoin? A currency substitute that can be much much more susceptible to theft, counterfeit, abuse, and fraud. But, there are some that seem to demand it’s use. Well, whatever.
TalkTalk? There is nothing that this company can provide that cannot be just as easily had without it.
This whole thing sounds more like a manufactured story from beginning to end. It’s been said that we hold the keys to the chains that bind us.
How is SQL injection a “method which abuses a misconfiguration in a database “? What database configuration can prevent SQLi? This is NOT a configuration issue.
Sanity-checking input fields, data validation of input fields, and truncating inputs that are too long for the expected query makes sure that only expected commands are allowed in the input field. This is a key part of properly configuring database access methods.
Yes, that was kind of my point – there is no configuration setting that will do input validation for you. This is a development/coding issue, not a configuration issue.
80,000 pounds? That’s all? This is like that Austin Powers movie where the guy has just gotten out of prison and does not appreciate the inflation that has happened, and is going to blow up the world or something unless he gets a ransom of $100,000 or some such.
The only way TalkTalk would even consider an offer is if the amount is not too high. Over a certain limit, they wouldn’t even bother looking at it.
That and the fact that there’s no guarantee that the info won’t be made public. We’re not talking microfilms or a kidnapped person here…
> This is like that Austin Powers movie where the guy has just
> gotten out of prison and does not appreciate the inflation
> that has happened,
http://www.imdb.com/title/tt0118655/quotes?item=qt0367876
> Dr. Evil: Here’s the plan. We get the warhead and we hold
> the world ransom for… ONE MILLION DOLLARS!
>
> Number Two: Don’t you think we should ask for *more* than
> a million dollars? A million dollars isn’t exactly a lot
> of money these days. Virtucon alone makes over 9 billion
> dollars a year!
>
> Dr. Evil: Really? That’s a lot of money.
The £80,000 in question here might be their considered goal as being high enough to make it all worthwhile, but not so high that law enforcement will make more than a token effort to find them, and TalkTalk may consider it a painful but not fatal go-away cost to pay.
TalkTalk is a serial offender having experienced two previous breaches of security since mid-2014. I wouldn’t touch it with an infinitely long bargepole. TalkTalk is held in very low regard.
It is said that Baroness Harding is an establishment figure with connections in high places and that she owes her position to that rather than her apparently tenuous grasp of technical matters. Her recent performances at interview on broadcast media seem to confirm that.
Take that 80K and solidify the network perimeter.
I bet a Donut that the sophisticated attack was a password reuse or a device that was not compliant.
Ok, bet off. Donut gone.
The weakest link in any office network is the person sitting at the desk, all it would take is a simple social engineer via help desk call or a spear phish attempt with a malicious RAT attached to it.
After that is accomplished your best defense perimeter will not stop a suspected authorized log in.
In this specific case, that would be a SQL injection attack. So, I would add that the weakest link was the person sitting at the desk… and doing the programming.
Here I go ranting again. But someone is going to pay extortion again, just to keep their business open. A shame. But we are all forgetting the bad guy again. A fine for the company, what third notice? Big, big fine, and bad publicity. But what will the extortionist get? A slap on the wrist? Or not even sought out? And have fun with the money. A web site that tells you what the vulnerabilities of a company? Open too the public? Meaning the exploits are known to security, interesting, culpable? Sorta like, if I have an exploit I want to try, look here for victims? Almost snorted coffee on that…
“According to my source, the intrusion started with an attack technique known as SQL injection (SQLi), a method which abuses a misconfiguration in a database that causes the database to cough up or dump information.”
SQLi is better described as an application layer attack which the attacker manipulates data sent to the database. The most common cause is a poorly written application that does not sanitize it’s data prior to that data getting sent to the database.
75,857 subscribers for /r/DarkNetMarkets
Brian, if you wanted to, all you have to do is send a PM to /r/reddit.com and this sub would get shut down.
You do not know how reddit works I can tell. That sub is not getting shut down by admins over a message lol.
Send a PM on reddit to /r/reddit.com and that sub will get removed, or is it better to monitor since its public?
Heard a 15 year old boy from Ireland has been arrested and charged with this intrusion.
Boy 15 Arrested in Northern Ireland.
http://www.bbc.co.uk/news/uk-34643742
Note on data vs configuration vs program:
I think Brian’s description is fine, particularly since the division between classifications is basically arbitrary.
-databases can run scripts that configure access control (especially useful when automatically generating schema). Are the scripts the configuration, or the program?
– one of sql’s strength’s is the ability to join tables and return a new ‘virtual table’, including calculated fields. Is the calculated field configuration, programming or data?
– Sql in particular supports stored procedures, which are generally stored in their own tables, with their own permissions. Is the data in these tables a database, or is it configuration of access methods, or is it program?
These procedures can be fairly elaborate, and should include the kinds of things mentioned in other posts, such as bounds checking, for example.
It’s also worth remembering a lot of the underlying structure of the indexing in sql comes from isam/vsam so even something as simple as a fetch is either reading data, or running a program, depending how you look at it.
At some point it starts to look like paper, scissors, rock ‘all over again’ (hat tip to yogi).
Bottom line is brian’s description strikes a fine balance without getting lost in the semantics.
A 15 year old hacked this place? No wonder the small amount of cash wanted. Obviously the trail to him was not that hard to find. Geesh. It goes to show, that there’s not much to whacking some of these companies.
There’s the press’s super sophisticated attack theme.
is it worth getting the noodle credit call check? Or if I sign up for that am I entangling myself in yet another unknown mire?
The only person on AlphaBay selling TalkTalk records is a vendor called “Martian” which is a Level 1 seller.
http://pwoah7foa6au2pul.onion/listing.php?id=49429
Huong dan cham soc da hieu qua
They are not “letting” businesses share threat info….they are “forcing” them to share threat information. As an admin at a business I see this first hand.
sorry this was meant for a diff article.
Еncryption, encryption, and encryption!
Learn, learn and learn – as said Lenin.
but if fearful reported the XSS vuln on xssposed, why would he then go on to attack the site? surely he would have kept it quiet (at least until after the attacK0
also, wasnt it an sql attack, so why would the xss thing matter?