Exploit packs — slick, prepackaged bundles of commercial software that attackers can use to booby-trap hacked Web sites with malicious software — are popular in part because they turn hacking for profit into a point-and-click exercise that even the dullest can master. I’ve focused so much on these kits because they also make it easy to visually communicate key Internet security concepts that otherwise often fall on deaf ears, such as the importance of keeping your software applications up-to-date with the latest security patches.
One of the best-selling exploit packs on the market today is called Crimepack, and it’s a kit that I have mentioned at least twice in previous blog posts. This time, I’ll take a closer look at the “exploit stats” sections of a few working Crimepack installations to get a better sense of which software vulnerabilities are most productive for Crimepack customers.
Check out the following screen shot, taken in mid-June from the administration page of a working Crimepack exploit kit that targeted mostly German-language Web sites. This page shows that almost 1,800 of the nearly 6,000 people who browsed one of the stable of malicious sites maintained by this criminal got hacked. That means some software component that 30 percent of these visitors were running either in their Web browsers or in the underlying Windows operating system was vulnerable to known software flaws that this kit could exploit in order to install malicious software.
Peering closer at the exploit stats, we see that one exploit was particularly successful: Webstart. This refers to a Java vulnerability that Oracle/Sun patched in April 2010, a powerful and widely-deployed software package that many users aren’t even aware they have on their systems, let alone know they need to keep it updated. (By the way, I got some serious flack for recommending that users who have no need for Java uninstall the program completely, but I stand by that advice.) As seen from the chart, this single Java flaw was responsible for nearly 60 percent of the successful attacks on visitors to these hacked sites.
Let’s have a look another screen shot from a different, working Crimepack administration page:
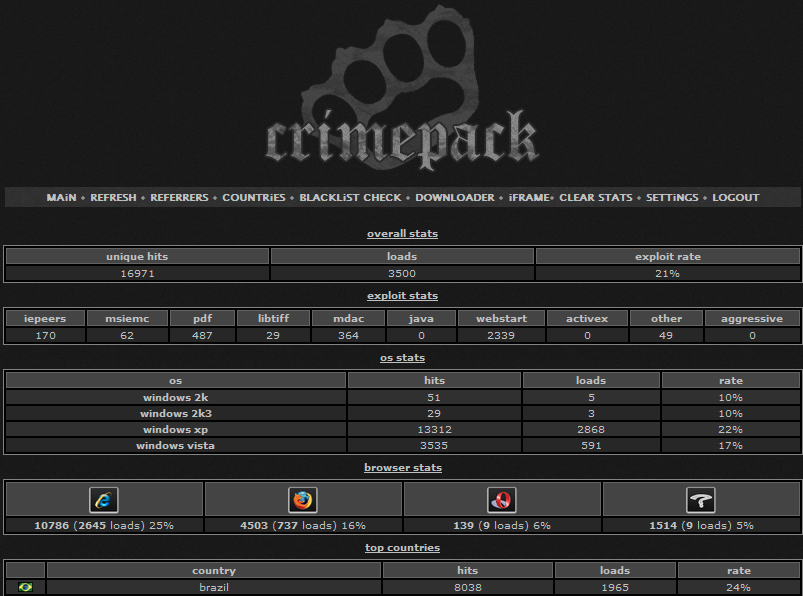
This Crimepack kit was targeting primarily Web sites in South America, but once again we see the same Java Webstart flaw was the most popular exploit. According to the admin page above, 3,500 out of 16,971 (~21 percent) visitors were successfully attacked, and more than two-thirds were exploited due to this one Webstart flaw.
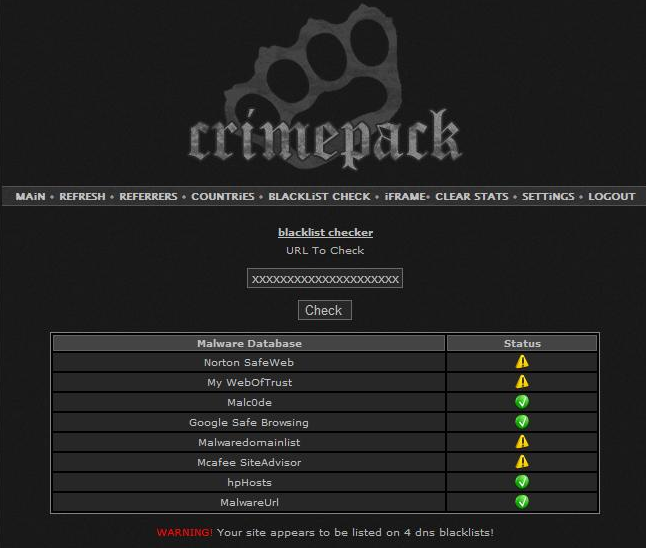
One other interesting feature built into Crimepack lets customers test various Web reputation services to discover whether any include their exploit sites:
I try to keep this blog updated with news about important security patches, but I simply cannot write about them all. If you want a simple way of staying updated on new software patches, I’d suggest downloading and installing the Personal Software Inspector tool from Secunia, which will scan your system and let you know which programs need updating. It also will periodically remind you about outdated programs, and includes direct links to the newest versions, so you don’t have to go hunting for download pages for all of the software products installed on your PC.





It’s one thing when the vendors crunch and rush to patch new vulnerabilities… Its another to get the end-user to patch and not ‘ignore, delay, defer’ the respective patches. Java patches are something i see all the time just sitting in user’ taskbar.
Last Java update I installed seemed to also install an online backup tool. No opt-in/opt-out/notification at all. Has this ever happened to you our your users? And is that a rude gesture from Sun or a sign that something else snuck into my PC?
The only additional software that I have noticed during my java update today is an opted-in yahoo toolbar.
Please can you give more information about how you noticed the additional application so I can validate whether my experience is the same.
There’s no easy solution here. Most end users don’t understand the concept of patching or that their 18 different applications all have their own unique patching process.
What the industry needs to move to is incorporating this stuff into Windows Update. MS has previously worked with Adobe and other vendors to patch serious security holes. Its time these companies moved their updates to Windows Update and also to WSUS for enterprise.
Apple is already doing this in OSX. The Apple updater will update Java.
Now toss in MS Security Essentials by default on all new Windows computers and end-users might have a fighting chance. Right now, malware and trojans are the norm and being free from them is very much an exception.
Unfortunately, Apple isn’t the gold standard here. The reason why Apple offers updates for Java is that the Java package for OS X is built by Apple rather than Sun/Oracle. And this package is regularly hanging months behind in terms of security fixes. So the situation on OS X is only marginally better than on Windows. And Apple doesn’t update third-party software either from all I know.
Yes, it would be nice to have all third-party vendors plug into Microsoft Update. But it is extremely complicated, with all the different update mechanisms used by different vendors only being a small part of the problem. I have my doubts that we will ever see this…
Secunia PSI is a good program but there is another alternative available from FileHippo called Update Checker. One really nice feature is you don’t have to install it to scan you system which makes it a perfect portable app to check multiple computers.
http://www.filehippo.com/updatechecker/
Update Checker is a very different tool – unlike Secunia PSI, it doesn’t scan for security holes, so the proposed updates from Update Checker are based purely on whether the vendor has a new version. Hence it’s really a tool for people wanting the latest features from their applications.
It also probably doesn’t work for apps not hosted on filehippo.com.
Secunia PSI remains the best way to keep Windows PCs patched for home/SOHO users.
This is true, Richard; however for 75% of my clients, they get, on average, a five day jump on zero day threats by watching FB’s update checker like a hawk! I’ve yet to see Secunia discount a new version from File Hippo.
Wait a few weeks and that may change, but on the whole update checker rules in my book. My computer illiterate clients will follow it when they can’t figure out Secunia PSI. It also keeps them from getting lost on Adobe or Sun’s site looking for what the heck they need to update. For some reason many cannot figure out Secunia’s simple console, but whatever!
I am also amazed at just how many applications are supported by this handy tool![File Hippo] I have no particular axe to grind for any software company, and work for myself, so I’m only doing this to further the cause of online security. This is my best wish!
Brian, do you have any information to distinguish the percentage a given exploit is effective against the software it targets? For instance, is Adobe Acrobat/Reader more exploitable than Foxit, or does it have a higher exploit count because it is more ubiquitous?
Removing unused software is always useful for reducing the attack surface, but I haven’t seen clear information on which products are actually most secure (or least exploited) when there are multiple programs that perform the same task, such as web browsing or PDF reading.
Dear Aaron;
In my opinion, the information Secunia gives out in its advisories is sufficient to gauge the vulnerability of a software application. Foxit receives fewer advisories than Adobe, and usually comes out with a patch or upgrade before Secunia gets an advisory on it.
I let File-Hippo notify me on updates, as it usually jumps the shark on Secunia for vulnerable versions of various applications out there. I rarely have to update Foxit, compared to Adobe, and I never have to let Foxit run vulnerable for months like Adobe occasionally does. This is enough to convince me Foxit is superior to Adobe, in a security sense.
Does Secunia PSI not require Java? I thought it did, but maybe it was the OSI only; I don’t see Java mentioned in the System Requirements or FAQ now.
Only if you like to see the history graphs. I’ve run Secunia without java just fine.
Actually, PSI doesn’t require Java to display graphs; it requires Adobe Flash Player.
I don’t have Java or Flash installed on my computer and it states the following under Historic Development:
“Cannot display graph, as Adobe Flash Player does not appear to be installed in Internet Explorer on your computer, or the version installed is older than version 8.x. Install Flash for Internet Explorer.”
One improvement that Secunia could make would be to drop the Flash requirement – animated GIFs would be enough.
Another nice enhancement would be to let users highlight and copy/paste text from the Secunia window.
Still a great tool, though.
You’re right TJ – I “misspoke” there. There are some critical pages on security sites that use java, and when I see the coffee cup symbol I know it is time to download the new version.
I regularly uninstall java because of insecure vulnerability threats; and simply don’t use it until I need it again. If the new version passes the Secunia PSI sniff test; than I leave it in there until the next advisory comes out. Sun is getting to be a pain about things like this – I wished there were an alternative out there.
At least Adobe has kept up with the threat level lately(so far); but they need replaced too! I can’t do without my news feed video – too bad it isn’t silverlight; I never have trouble with silverlight!
I’ve been using Secunia PSI for a few years now, as per Brian’s recommendation. I love it. And, no, it doesn’t require Java, as OSI does. Again, as per another of Brian’s wise suggestions, I removed Java from my computers a couple years ago, and haven’t missed it a bit.
Just curious, but do foreign language editions of Windows have the same security flaws, requiring the same patches?
It amazes me that they are still finding Windows XP flaws after all these years of service packs and patches. Would the latest found flaws affect an original unpatched Windows XP, or are new flaws being introduced in later services packs and patches? Is there some fundamental flaw in the design of an OS that makes security leaks inevitable (for example, to make it extremely easy to use for an end user, you need to allow the OS to do things that can then be done remotely/programatically)?
“Is there some fundamental flaw in the design of an OS that makes security leaks inevitable”
There are, of course, unwise design decisions. But the main problem is complexity. All large, complex systems inevitably have errors.
The secondary problem is market share. Microsoft Windows supports 91 percent of all browsing, As long as any error whatsoever can be found in Windows, that will be exploited to leverage the Windows market share for criminal attacks. No other OS provides near that criminal advantage.
Systems which try to add security after implementation inevitably cannot. Secure systems require limiting options at all levels during design. By allowing only known options, a design can prevent unknown attacks. By allowing new things, we may support creativity and commerce, but also enable new attacks.
I wonder what makes Windows a more vulnerable target than OS X for malware.
A big part of Apple’s user base are non-technical users who can afford its relative high cost. You’d think then, OS X would be a vulnerable and attractive target for malware, and it’s not.
The answer might be that Microsoft sells only the OS, whereas Apple sells the OS and the hardware to run it.
Apple isn’t nearly as concerned as Microsoft if the OS is copied and passed around because it has a captive customer base and the damage is only ever minimal.
Selling only the OS, Microsoft has major how-to enforcement issues when it comes to unlawful copying and distribution.
So, it’s not that Windows is necessarily more insecure. I think it’s plausible that many of these cracks and crevices, by design or chance, are just designated backdoors that are part of their secret enforcement tool chest. Occasionally, these secrets leak out or are found.
Apple can afford the luxury of plugging most if not all of their cracks and crevices, and then appear to have a more secure operating system.
Maybe if Microsoft could just calm down about piracy, they could cement the wells shut.
“I wonder what makes Windows a more vulnerable target than OS X for malware.”
After years of intense patching, Windows probably is *less* “vulnerable” than OS X. But it will always have some error that can be exploited. The difference lies in the desire of attackers to reach the 91 percent Windows market.
On the one hand there is 91 percent, on the other 6 percent, so which do they attack? The choice is not hard or mysterious.
“You’d think then, OS X would be a vulnerable and attractive target for malware, and it’s not.”
I would suggest that OS X *is* vulnerable, but *not* nearly as attractive.
Java scares me more than anything else in terms of malware vectors.
I can guarantee that a large proportion of endpoint machines in most enterprises have an outdated and vulnerable versions of JRE. In our case, a snapshot last year revealed that less than 1% had the latest & greatest version.
Briefly the reasons are (some of these have been addressed but others haven’t)
– New versions left older versions still present and these older versions could be invoked by a specially crafted applet
– Sun used to take their time in updating their ‘verify your java’ page to detect and report on the newly released version…so if someone heard about the new version and used the page to check, they would get a false assurance that they had the latest version.
– Third-party vendors sometimes bundle java with their products and so downgrade your installed version of java without your knowledge. OpenOffice comes to mind.
– The versions of java are confusing to say the least, v6 update 21; 6u21; 1.6.0_21; 1.6.0_21-b07. Yuk!
– Vendors which use java in their products are slow to certify & support new releases of java. I have seen examples where one user has two apps which require java…but one vendor supports one version but not another vice-versa. Ugh!
– Java upgrades have a bad habit of breaking apps that require java. We have had numerous examples of jave upgrades having to be rolled back due to errors in apps the next morning.
All in all, it’s not a great situation and I’m not surprised that the bad guys are using java as a vector
– Tim
This is exactly the problem, Tim. I’ve been doing this for a long time, and the software vendors that build and certify on exactly one version of Java, and do not upgrade or test their code, is negligent and criminal. Mortgage software, dental software, CRM, you name it, I’ve seen it. I am forced to leave older versions on the PC just so their LOB software works. If I’m really lucky I can install a newer Java and have 4 or 5 old ones on the machine for compatibility, and hope that my Software AV and inline UTM device picks up the bad code.
Not sure who you got flack from for the Java recommendations, but I agree with you. I kinda agree with that for any software though; I periodically go through my programs and remove any I don’t honestly think I’ll be using for a while.
Worse case scenario I just download and install the program again when I need it.
Those of us with corporate PCs are often stuck with old versions of Java and many other applications. I have always tried to limit my browsing on my work notebook to very safe sites (if there is any such thing). When i got my new notebook last fall I started only browsing with Ubuntu in vmware player.
Is it possible to selectively disable/remove webstart or do we have to completely uninstall the JRE to get rid of it?
In Chrome, about:plugins and disable “Java Deployment Toolkit”.
Man, who gave you flack for recommending people remove Java if it’s not needed? Sun? It’s not like it’s hard to find if you do need it at some later date.
But even removing software you don’t use doesn’t help much if everything else isn’t kept up to date – and that doesn’t help if you happen to have a system with a zero day on it. We need a whole new model for creating and securing software.
The reason everyone at the small business where I work has a Java update icon sitting in their tray is that they’re not running with administrative privileges. They can try to update Java, but the next time they reboot, it’s un-updated.
And it’s disruptive at a very small business to kick people off their computers when customers are calling during a business day in order to have the administrator log into each computer to run an update every time one is needed — and it assumes a small business can afford a dedicated employee who has no other responsibilities other than to stand ready to install updates. (More likely the duty is the responsibility of the person whose main qualification for being the administrator is that he was also the guy everyone called when the photocopy machine got jammed.)
Patches are easy to automate via gpolicy and msi. I can’t remember the last time I even heard of an issue of a “business call” breaking because of an out of date java install. As an admin I hear all sorts of whining on why end users need admin access and its 100% wrong. You’re much safer with even out of date software and limited rights. The virus you just ran will fail to affect the system files and at worst will mess with your local profile, which is not common.
No arguments about limited privileges still being better. I’m just explaining why those update icons are all sitting in everybody’s tray. Nobody here has any idea what gpolicy or msi are, and if our support vendor does, their techs didn’t choose to implement them.
You hit it on the head about disruptive behavior of the java update process; I’ll have to look into some way to turn that off for the ‘everyone’ setting; if there is a way to do that!?
Kill the marketers of CrimePack in the same manner as the targeting of al Qaeda in Yemen: i.e. do it publicly after reaching a policy consensus.
Thank you,
James
I would really like to know more about webstart. Can you supply example html that illustrates the sorts of things that an exploit uses? I would like to find a way to test for web start vulnerabilities the “direct way” vs inferring what is going on, because java is extremely complicated. Webstart apparently has the ability to install any version of the jre that was specified. Or so was the case back when they wrote some of these pages. http://download.oracle.com/javase/tutorial/deployment/webstart/
I just installed jre 6.21 update and I thought it said web start was included (also they tried to stick me with yahoo toolbar.) Also the web page above says webstart is part of the jre install. But I don’t find webstart in there anywhere. Is it installed? If I go in the java console,
start,settings,control panel, java I find some options regarding “jnlp” in “advanced”. Are any of these any help with the web start security problems?
ok update:
web start creates an entry on the program files menu.
now get this I created a sample jnlp file that called for
an older jre to be installed. (The current jre is 1.6.21 and it automatically installs webstart.) This are the relevant lines:
This was based on a demo jnlp file on oracle/sun’s web site.
Both ie 8 and firefox 3.6.8 would prompt for downloading
the 1.4.2 jre. Then were was a complaint about the certficate that expired. Ignoring that it could be downloaded and installed. But here’s the “good” part, then I got popup
from Symantec Endpoint that that javaw.exe was
a virus!
http://securityresponse.symantec.com/security_response/detected_writeup.jsp?name=CommercialApps.2
Well great was that an actual virus from oracle or was it a false alarm?
The lines were deleted but the crucial aspect was
j 2 s e ver sion = “1.4.2”
The executable for web start is javaws.exe.
Yes but the issue was using webstart to download
the jre 1.4.2. Then the javaw.exe in that jre 1.4.2 was accused of being a virus by Endpoint. These are the items in the bin directory installed that way:
950,371 awt.dll
94,312 axbridge.dll
client
139,363 cmm.dll
139,364 dcpr.dll
24,678 dt_shmem.dll
20,584 dt_socket.dll
61,536 eula.dll
327,800 fontmanager.dll
28,780 hpi.dll
49,247 hprof.dll
24,704 ioser12.dll
20,600 jaas_nt.dll
98,408 java.dll
24,670 java.exe
28,768 javaw.exe
20,581 jawt.dll
61,533 jcov.dll
49,267 JdbcOdbc.dll
102,494 jdwp.dll
122,981 jpeg.dll
82,024 jpicom32.dll
53,352 jpicpl32.cpl
16,490 jpicpl32.exe
94,312 jpiexp32.dll
28,772 jpins4.dll
41,060 jpins6.dll
45,156 jpins7.dll
86,116 jpinsp.dll
73,832 jpishare.dll
139,373 jsound.dll
28,790 keytool.exe
28,786 kinit.exe
28,786 klist.exe
28,784 ktab.exe
266,293 msvcrt.dll
57,444 net.dll
32,869 nio.dll
65,636 NPJava11.dll
65,636 NPJava12.dll
65,636 NPJava13.dll
65,636 NPJava14.dll
65,636 NPJava32.dll
65,636 NPJPI142.dll
65,636 NPOJI610.dll
28,809 orbd.exe
28,796 policytool.exe
106,600 RegUtils.dll
20,579 rmi.dll
28,784 rmid.exe
28,796 rmiregistry.exe
28,821 servertool.exe
28,811 tnameserv.exe
57,442 verify.dll
20,563 w2k_lsa_auth.dll
53,353 zip.dll
So an interesting thing here is that web start can be used to download even a very old jre that is no longer distributed and in this case, it was also accused of being a virus which surprised me. I have not encountered jre’s being accused of being viruses. What gives? I already have another jre in the 1.4.2 lineage which was installed by the oracle 10.1.0 g client:
java version “1.4.2_03”
Java(TM) 2 Runtime Environment, Standard Edition (build 1.
Java HotSpot(TM) Client VM (build 1.4.2_03-b02, mixed mode)
and symantec does NOT accuse it of being a virus. This is a huge problem that enterprise software products depend on very old versions of java, or to put it another way, java versioned itself very very quickly.
It’s best to make JavaWebStart/JavaFX be something that a user has to explicitly invoke like any other application, rather than quietly running stuff in the browser.
Please help. I have read through all of the posts, and need some info. First, I’d like to state that I had no idea that I could run my computer without Java, and I suspect that most “average” computer users do not know this either. Every time I have asked anyone about Java, I always get the answer “Oh, it’s just a computer language”. and…….?????
So, although I have no idea what an “exploit” is, I am tired and worried that MS Security Essentials keeps finding the java exploit on my computer. Also, that MS SE does not seem to find it until I run a full scan, which takes hours.
Your posts here have been only somewhat infomative, because I do not understand all of your computer tech talk. A little more explanation would be nice…. for example, if you say do this, or don’t do this……… telling us how would be great. But maybe your site is intended for more advanced users.
My main question is …………… if I go to Manage Add-ons in my Tools tab, and disable all of the Java stuff, will that take care of the exploit problem, or do I need to actually uninstall Java.
If I do need to uninstall Java, is going to Control Panel, then Programs and uninstalling both Java things (one is for 32 bit, the other for 64 bit) the way to do this? And, will that also get rid of the JavaWebStart and JavaFX that I have read are also unnecessary???
I also read that java and javascript are 2 completely different things, but that I MUST have javascript. By deleting java, as described above, am I correct that this will not affect javascript???
I really appreciate your blog and your posts here.
Someone on one of your blogs re Exploit asked for a website ….. oh nutz…… can’t remember why or what now. But, I looked in Java’s temp files folders, and the only files in there, starting from my first using my computer in 2008, were when Java updated, and the rest were all from the POGO website. Don’t know if that helps anyone, or if that is the info someone wanted. (Sorry… brain shuts down after reading so much “tech” stuff)……. well, “tech” to me. 🙁
Thanks a lot!
Donna
So much to learn, so little time!
Oops, please disregard first sentence of my previous post. It was a copy paste from someone, so that I would remember the 2 java things.
sorry
Donna,
Disabling Java will not protect you against the exploit in question, you would have to uninstall Java. However, as Brian pointed out, that particular vulnerability was patched in April. As long as you only have the latest version of Java installed you’re safe from that one.
If you’re worried about future or currently unknown exploits it’s no big deal to uninstall Java, you do it just like you said. You can always reinstall it if you don’t like life without it. Personally, I would just disable it until you determine whether you need it or not. I do, but maybe you don’t.
It’s hard to say what Security essentials is flagging from here. It could be a false positive, or maybe a remnant of something it couldn’t clean up completely, who knows. You could try downloading Malwarebytes from malwarebytes.org. It will find and remove stuff that many AVs will leave behind. Make sure it’s updated and run a full scan.
Oh they’re so cool, aren’t they? Knuckle dusters for a logo. Heartwarming.
I think I said this in this blog before – I started uninstalling Java from all computers I help maintain even before I read your advice, Brian. And I never got any complains about that. Almost nobody seems to need Java these days – but almost everybody has it installed. And the update experience is really horrible. In particular, it always tries to trick you into installing some other crap as well. So is anybody surprised that even the users who used to update Java stop doing so?
Just recently I installed a financial application – and it installed Java on my computer without asking. Not only that, it was a horribly outdated version (one that didn’t even support in-place updates meaning that it would stay as a second Java instance even after an update). And of course this application only needed Java for a tiny feature that I didn’t want to have anyway. So: yes, I agree with the other commenters, Java scares me a lot. Kill it. Please!