Over the past few weeks, three of the longest running and most venerated Russian-language online forums serving thousands of experienced cybercriminals have been hacked. In two of the intrusions, the attackers made off with the forums’ user databases, including email and Internet addresses and hashed passwords. Members of all three forums are worried the incidents could serve as a virtual Rosetta Stone for connecting the real-life identities of the same users across multiple crime forums.
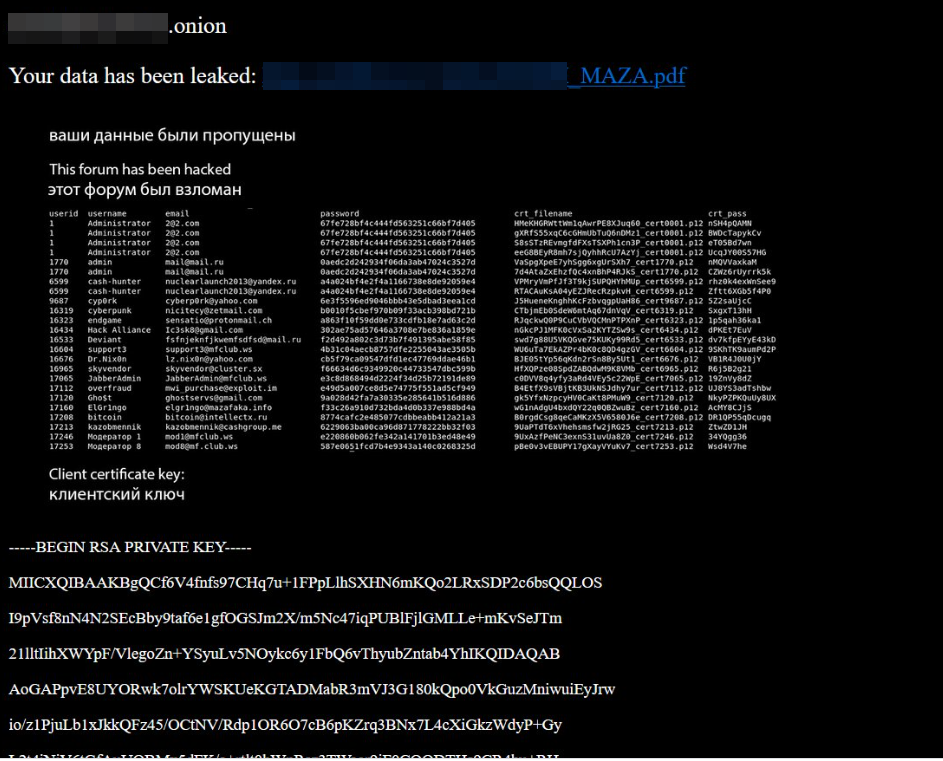
On Tuesday, someone dumped thousands of usernames, email addresses and obfuscated passwords on the dark web apparently pilfered from Mazafaka (a.k.a. “Maza,” “MFclub“), an exclusive crime forum that has for more than a decade played host to some of the most experienced and infamous Russian cyberthieves.
At the top of a 35-page PDF leaked online is a private encryption key allegedly used by Maza administrators. The database also includes ICQ numbers for many users. ICQ, also known as “I seek you,” was an instant message platform trusted by countless early denizens of these older crime forums before its use fell out of fashion in favor of more private networks, such as Jabber and Telegram.
This is notable because ICQ numbers tied to specific accounts often are a reliable data point that security researchers can use to connect multiple accounts to the same user across many forums and different nicknames over time.
Cyber intelligence firm Intel 471 assesses that the leaked Maza database is legitimate.
“The file comprised more than 3,000 rows, containing usernames, partially obfuscated password hashes, email addresses and other contact details,” Intel 471 found, noting that Maza forum visitors are now redirected to a breach announcement page. “Initial analysis of the leaked data pointed to its probable authenticity, as at least a portion of the leaked user records correlated with our own data holdings.”
The attack on Maza comes just weeks after another major Russian crime forum got plundered. On Jan. 20, a longtime administrator of the Russian language forum Verified disclosed that the community’s domain registrar had been hacked, and that the site’s domain was redirected to an Internet server the attackers controlled.
“Our [bitcoin] wallet has been cracked. Luckily, we did not keep large amounts in it, but this is an unpleasant incident anyway. Once the circumstances became clear, the admin assumed that THEORETICALLY, all the forum’s accounts could have been compromised (the probability is low, but it is there). In our business, it’s better to play safe. So, we’ve decided to reset everyone’s codes. This is not a big deal. Simply write them down and use them from now on.”
A short time later, the administrator updated his post, saying:
“We are getting messages that the forum’s databases were filched after all when the forum was hacked. Everyone’s account passwords were forcibly reset. Pass this information to people you know. The forum was hacked through the domain registrar. The registrar was hacked first, then domain name servers were changed, and traffic was sniffed.”
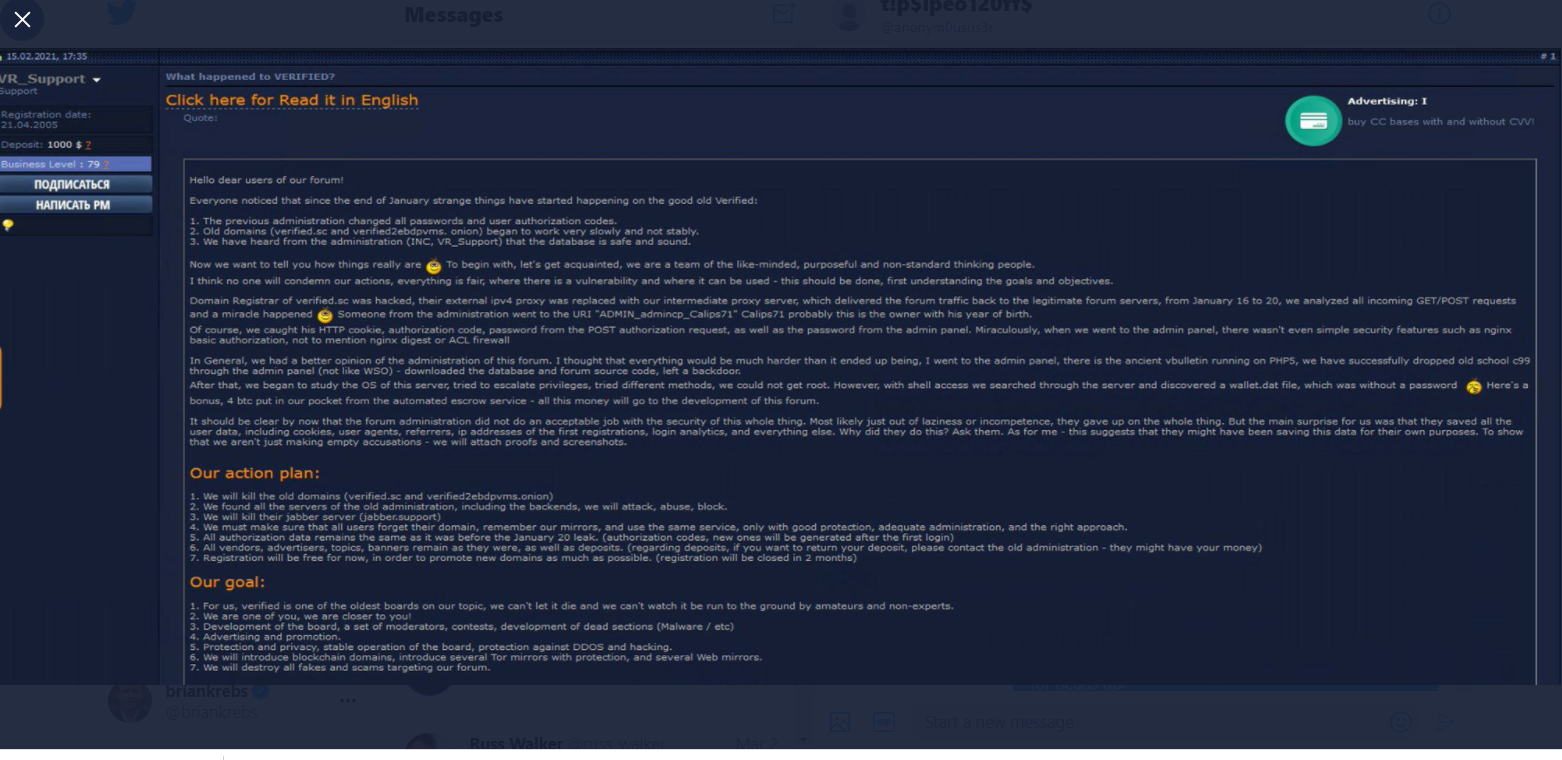
On Feb. 15, the administrator posted a message purportedly sent on behalf of the intruders, who claimed they hacked Verified’s domain registrar between Jan. 16 and 20.
“It should be clear by now that the forum administration did not do an acceptable job with the security of this whole thing,” the attacker explained. “Most likely just out of laziness or incompetence, they gave up the whole thing. But the main surprise for us was that they saved all the user data, including cookies, referrers, ip addresses of the first registrations, login analytics, and everything else.”
Other sources indicate tens of thousands of private messages between Verified users were stolen, including information about bitcoin deposits and withdrawals and private Jabber contacts.
The compromise of Maza and Verified — and possibly a third major forum — has many community members concerned that their real-life identities could be exposed. Exploit — perhaps the next-largest and most popular Russian forum after Verified, also experienced an apparent compromise this week.
According to Intel 471, on March 1, 2021, the administrator of the Exploit cybercrime forum claimed that a proxy server the forum used for protection from distributed denial-of-service (DDoS) attacks might have been compromised by an unknown party. The administrator stated that on Feb. 27, 2021, a monitoring system detected unauthorized secure shell access to the server and an attempt to dump network traffic.
Some forum lurkers have speculated that these recent compromises feel like the work of some government spy agency.
“Only intelligence services or people who know where the servers are located can pull off things like that,” mused one mainstay of Exploit. “Three forums in one month is just weird. I don’t think those were regular hackers. Someone is purposefully ruining forums.”
Others are wondering aloud which forum will fall next, and bemoaning the loss of trust among users that could be bad for business.
“Perhaps they work according to the following logic,” wrote one Exploit user. “There will be no forums, there will be no trust between everyone, less cooperation, more difficult to find partners – fewer attacks.”
Update, March 4, 6:58 p.m. ET: Intel 471 says there was a fourth crime forum that got hit recently. From the blog post they just published on these events: “In February, the administrator of another popular cybercrime forum, Crdclub, announced the forum sustained an attack that resulted in the compromise of the administrator’s account. By doing so, the actor behind the attack was able to lure forum customers to use a money transfer service that was allegedly vouched for by the forum’s admins. That was a lie, and resulted in an unknown amount of money being diverted from the forum. The forum’s admins promised to reimburse those who were defrauded. No other information looked to be compromised in the attack.”




Very interesting article…
“Da”
Can only assume these criminals appreciate the irony – hackers being hacked.
What are the odds this was a nation-state (aka the US) who staged the attacks? 9-in-10?
Too bad they can’t re-release Stux 🙂 (and yes, I know that would be bad… just dreaming)
Hi Krebs,
You article is inaccurate.
4 Russian cybercrime forums have been hacked.
https://www.shadowbanker.io/2021/03/hydra-admins-doxed-maybe-spotlighting-billions-minted-from-bath-salts-trade/
Let’s apply the mosaic theory of intelligence here.
This is the biggest “shakeup” in the Russian cyber-world since Milhailov went down.
It’s too perfect. I wonder if it’s the disinfo everybody at the super competent NYT beats off about
“Inaccurate?” I don’t think so. Maybe incomplete or not comprehensive of all actions lately. Hydra is more of a dark market than a forum. Also, Exploit, Maza, Verified all go back much, much further in time. Maza and Verified date back to the early to mid 2000s.
Sorry incomplete. I wasn’t trying to be an asshole to you. I’m sorry if it came off that way. Just being provocative.
But I would argue any forum that offers a significant cybercrime as as a service component is a cybercrime forum.
Look at the revenue too. $3.4 billion since inception. That we know about.
The timing is also convenient. 2.5 months after SolarWinds announced.
Sorry again. I’ll be more mindful of etiquette in my next post.
Okay Shadow what you got less talk more grill
Brian is right. Hydra is selling drugs. I don’t think they can be in the same storyline.
Hey read my story.
Chainalysis says Hydra as an an active criminal services market in addition to drugs. They are all part of the same ecosystem. Less exclusive than maza and verified, sure. But there is material overlap between ecosystems.
“obfuscated passwords”. And I wonder why the other information is not “obfuscated”?
Krebs you are a retard, Exploit is not breached. Maza and Verified have issues as well as XSS, but Exploit have not got any issues. Stop spreading rumors!
“but Exploit have not got any issues” = How would you know?
How exactly are you proving this is true to anyone?
You are on forum? No? Then don’t speak of what you don’t know stupid whore
SHAME SHAME!
Hit a nerve, did he
Put a bounty on the hackers heads, let them be harvested for profit.
Nothing like a hacker head drying in sun to brighten the worlds day.
Hackers should be sent to Gitmo for torture before drowning the ignorant sucking traitors.
Rippers scammers everywhere
I Don’t see point in carding business
Long time ago the omerta was legend Now its all rippers scamers!
Omerta Forum was best, Rip!
Sucks to be hacked, doesn’t it?
Good for the goose..
Bad people doing things to other bad people. There are worst things in the world.
You don’t know that ‘bad people’ did it.
Victims themselves are blaming a foreign spy agency.
Remmeber also. This news breaks 2.5 months after SolarWinds. Could easily be an NSA hit.
Or a private offensive cyber firm operating with Biden’s consent.
…maybe, but probably not – while you could argue about such things by and large the US does not break US laws and this is illegal activity under various laws here…
“by and large the US does not break US laws and this is illegal activity under various laws here…”
And there are plenty of loopholes in those laws for “national security”.
And it could be performed by Israel or one of the Five Eyes with the go-ahead from Biden.
Ah, but remember that Mr. Biden did say there would be consequences for Solar Winds. Nobody on this side of the Atlantic is stupid enough to think that the “dark IT arts” ecosystem in the Motherland and the GRU are all that separate…
KARMA !
Russians going into hiding right now, I heard that all flights to Siberia this week were sold out
Nah, there’s no need for them to hide, they can break all the laws they want in other countries, and even break them in Russia too so long as they keep up bribes to the right officials.
Russia never extradites their criminals and strenuously protests every time a criminal travels to a country with an extradition treaty.
That’s exactly the problem, and that folks don’t ask where their bribes are coming from, and just how that money is generated either. Careful records are kept of all those bribes and leverage ensured.
Verified DB on sale on raidforums https://raidforums.com/Thread-SELLING-verified-sc-verified-forum-full-database-and-source-code–127837
“Price $20k”
4 minutes ago
No sample/proof?
“Just traaast me, I’m a professssional.”
Any proof that isn’t personalized should be easy to fake, just ask the seller for information regarding your account…
I am also pretty sure that the threat actor behind the leaked credentials did so for free too, I saw screenshots elsewhere on another news site where someone dumped some of not all of the credentials for free on a fileshare site.
You are confusing with the Maza dump.
*Like*
What’s that age old adage? There’s no honor among thieves? Guess it’s true…..
A. Play stupid games, win stupid prizes.
B. Poetic justice.
Your choice.
Another great article !
It’s the sense of injustice that comes over from the forum’s comments that makes it really satisfying. Boot, other, foot, springs to mind.
I think it was Chuck Norris – every now and then he finds the hackers and smacks them around a little just to make sure they are awake
Shutdown the gangs and safequard the $$$, thanks to the military, keep it up!
Very interesting, hackers been hacked
Something I had noticed with my Mac system and iPhone being compromised a Jabber field was added to the set up fields that are standard in contacts. Since I was fumbling through everything I learned that Jabber uses the same base system as iPhone messages. I am below a novice on cyber security but it made me wonder if that was how my 2FA using messages could be compromised along with other messages. Someone might want to look at that if it’s possible. If it’s not, sorry for a useless post.
This sounds inaccurate. At some point in the past, iiuc, iMessage supported XMPP (which Jabber also uses). At some point, iMessage apparently dropped this support.
Yes, Apple includes Jabber as a possible field value in Contacts, no, that isn’t particularly interesting.
If you’re using iMessage, you probably have things synced between multiple devices, and I’d be more likely to blame something that’s running on your Mac than your iPhone.
Those hackers should be investigated anyways.
If you steal the money and hold it and you get robbed the police still have to protect you still .
It’s about time the White Hats started fighting back and exposing these criminals …..
What kicked this off was when they started attacking hospitals about a year ago in the middle of the Pandemic and some elite groups were formed to start fighting back ….. Locking out hospitals in the middle of the worst pandemic in 100 years was just going way too far
Dont be silly any criminal are criminals white hats are blackhats the good person ae not even capable to harm bad person if you harm or hack or do spmething bad you are criminal ,period !!
bull$#17
Why would US do that? Get the data and use it in years to come – dumping it in the open is stupid. Not sure who and why, but that is not how serious people operate.
Well, if ‘they’ just so happened to come across said database dumps being publicly shared, ‘we’ could, and should, assume that’d abrogate whatever legal expectations of privacy afforded for ones’ transgressions being shared in confidence.
Kill the chicken to scare the monkeys. The Biden administration is doing this.
I have exactly the same problem. Anyone got a suggestion? This is quiet a common issue
In summary, watch out for IP transit. Things can happen in the middle.
Pretty sure someone did this after both their bank accounts and debit cards were used, tracing it back to this. Vigilante justice .. and might be turning the info over to make life hell for the people. I did something similar taking down a card ring who was using wifi from a local motel/hotel to upload the data.
Nah man, unlikely
Just saying maybe someone got their card taken to both their bank accounts, from a payment processor maza had taken info from with enough skills to go after them… oddly specific but not identifying as that person. Some of us DGAF when it comes to these guys when it happens to us. I’m hoping this was an internet John Wick scenario.
Hi Brian,
Thanks for covering this.
Best news I’ve seen yet in 2021!