The U.S. Federal Bureau of Investigation (FBI) disclosed today that it infiltrated the world’s second most prolific ransomware gang, a Russia-based criminal group known as ALPHV and BlackCat. The FBI said it seized the gang’s darknet website, and released a decryption tool that hundreds of victim companies can use to recover systems. Meanwhile, BlackCat responded by briefly “unseizing” its darknet site with a message promising 90 percent commissions for affiliates who continue to work with the crime group, and open season on everything from hospitals to nuclear power plants.
A slightly modified version of the FBI seizure notice on the BlackCat darknet site (Santa caps added).
Whispers of a possible law enforcement action against BlackCat came in the first week of December, after the ransomware group’s darknet site went offline and remained unavailable for roughly five days. BlackCat eventually managed to bring its site back online, blaming the outage on equipment malfunctions.
But earlier today, the BlackCat website was replaced with an FBI seizure notice, while federal prosecutors in Florida released a search warrant explaining how FBI agents were able to gain access to and disrupt the group’s operations.
A statement on the operation from the U.S. Department of Justice says the FBI developed a decryption tool that allowed agency field offices and partners globally to offer more than 500 affected victims the ability to restore their systems.
“With a decryption tool provided by the FBI to hundreds of ransomware victims worldwide, businesses and schools were able to reopen, and health care and emergency services were able to come back online,” Deputy Attorney General Lisa O. Monaco said. “We will continue to prioritize disruptions and place victims at the center of our strategy to dismantle the ecosystem fueling cybercrime.”
The DOJ reports that since BlackCat’s formation roughly 18 months ago, the crime group has targeted the computer networks of more than 1,000 victim organizations. BlackCat attacks usually involve encryption and theft of data; if victims refuse to pay a ransom, the attackers typically publish the stolen data on a BlackCat-linked darknet site.
BlackCat formed by recruiting operators from several competing or disbanded ransomware organizations — including REvil, BlackMatter and DarkSide. The latter group was responsible for the Colonial Pipeline attack in May 2021 that caused nationwide fuel shortages and price spikes.
Like many other ransomware operations, BlackCat operates under the “ransomware-as-a-service” model, where teams of developers maintain and update the ransomware code, as well as all of its supporting infrastructure. Affiliates are incentivized to attack high-value targets because they generally reap 60-80 percent of any payouts, with the remainder going to the crooks running the ransomware operation.
BlackCat was able to briefly regain control over their darknet server today. Not long after the FBI’s seizure notice went live the homepage was “unseized” and retrofitted with a statement about the incident from the ransomware group’s perspective.
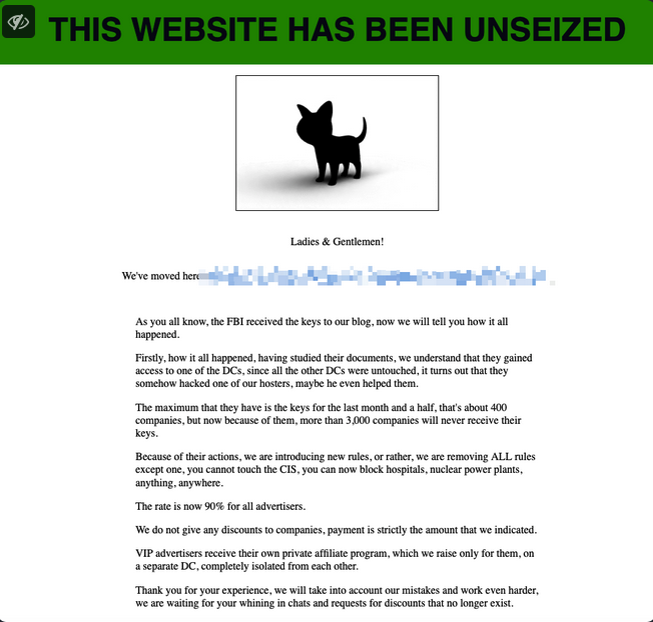
The message that was briefly on the homepage of the BlackCat ransomware group this morning. Image: @GossiTheDog.
BlackCat claimed that the FBI’s operation only touched a portion of its operations, and that as a result of the FBI’s actions an additional 3,000 victims will no longer have the option of receiving decryption keys. The group also said it was formally removing any restrictions or discouragement against targeting hospitals or other critical infrastructure.
“Because of their actions, we are introducing new rules, or rather, we are removing ALL rules except one, you cannot touch the CIS [a common restriction against attacking organizations in Russia or the Commonwealth of Independent States]. You can now block hospitals, nuclear power plants, anything, anywhere.”
The crime group also said it was setting affiliate commissions at 90 percent, presumably to attract interest from potential affiliates who might otherwise be spooked by the FBI’s recent infiltration. BlackCat also promised that all “advertisers” under this new scheme would manage their affiliate accounts from data centers that are completely isolated from each other.
BlackCat’s darknet site currently displays the FBI seizure notice. But as BleepingComputer founder Lawrence Abrams explained on Mastodon, both the FBI and BlackCat have the private keys associated with the Tor hidden service URL for BlackCat’s victim shaming and data leak site.
“Whoever is the latest to publish the hidden service on Tor (in this case the BlackCat data leak site), will resume control over the URL,” Abrams said. “Expect to see this type of back and forth over the next couple of days.”
The DOJ says anyone with information about BlackCat affiliates or their activities may be eligible for up to a $10 million reward through the State Department’s “Rewards for Justice” program, which accepts submissions through a Tor-based tip line (visiting the site is only possible using the Tor browser).
Further reading: CISA StopRansomware Alert on the tools, techniques and procedures used by ALPHV/BlackCat.




The FBI needs to read “The Art of War”.
explain
Sooner the integrated empire Russia fractures into its constituent parts the better the whole world, including the citizens of Russia, will be.
Like how the US hobbled the former tyrant Gaddafi… leading to civil wars and unrest in Libya that continue to this day? A free-for-all isn’t necessarily good for the local populace.
Russia is wrong to invade / occupy Ukraine. And again, not so different from what we did to our little neighbor, Mexico. What are the medium-to-learn term dynamics between Russia and Ukraine? Probably similar to those between US and Mexico. The smaller state does its best to survive and not make trouble. And the larger state contents itself that the border is ‘secure’ and refrain from outright annexation.
And finally, with increasing antics like unilateral declarations of who can (or cannot) trade with whom or face sanctions… many hold the same opinion about USA weakening or breaking up not dissimilar to your view on Russia.
The crucial difference lies in the lack of internal demand for Russia’s fragmentation. Unlike the Soviet Union, where national aspirations of its diverse republics fueled its breakup, Russia lacks a similar grassroots movement for secession. Imposing an external solution disregards the right of the Russian people to determine their own future.
Furthermore, Russia’s aggression against Ukraine stems from the ambitions of its current leadership, not the inherent instability of its internal structure. Focusing on Russia’s potential breakup risks overlooking the need to hold accountable the individuals and systems responsible for the current crisis.
This is whataboutism at its finest, Just Another Opinion.
Brian – Maybe this all sound jarring to you… because you (and others) are so much on the receiving end of our own government and media bias?
I think you will agree with me that “de-nazification” is a completely ludicrous excuse from Russia!? But think about it… what about our own country’s invasion/occupation of Iraq under the banner of “defending world freedom and democracy”? Remember how twenty years ago, our government (and media) were screaming about Iraqi WMD and its ‘imminent’ nuclear attack capability? All made up.
Whataboutism is too often used as a conversation stopper. But whataboutism does nothing, absolutely nothing, when used to defend / deflect hypocrisy.
What does this have to do with cybersecurity? This isn’t a political blog.
But even if it was, pointing out that other (basically all) governments have engaged in some despicable behavior does not excuse any government for that behavior. But again, security blog, not political.
Very telling how you didn’t direct your question to RWKOS’ post.
Of course if you actually understood the meaning of the term whataboutism you’d understand that nothing you posted was, in any way, an answer to RWKOS’ post. Maybe you should stick to Russian language sites, there you won’t be exposed to topics that could land you in hot water with the FSB.
Good reply. Too bad the US as “white hat” myth runs so deep that any serious criticism is taboo and draws the usual facile and empty defense. The “whataboutism” canard is a perfect example of that, which generally translates as “do as we say, not as we do, and if we did bad it was only with the best of intentions”. The US (supported by it’s inculcated citizenry) acts with impunity globally while castigating any other country doing similar in it’s own backyard. Been doing this with regularity post WWII.
“Not so different from what we did to our little neighbor, Mexico.”
Quite different, unless you have ~zero specific understanding…
Iraq did have dirty bomb capability and delivery means, historical WMD use. Chemical weapons are WMD. Nuclear/bio programs were tabled, but existed. “We” have a free press and can discuss it openly, (even simplistically…) no doubt it’s an obvious distinction to as famed an historian as yourself…
“Whataboutism is too often used as a conversation stopper.”
– as you have attempted to demonstrate.
There’s not really any point in arguing with someone who begins and ends with it; you make no actual comparisons, provide no details or real insight about anything, are not even pretending to talk about the actual topic of discussion here at all. (I ask you no questions and require no response other than perhaps for you to you break down an unwarranted pseudo-ego and evaluate your own hypocrisy before continuing to be pointless in an attempt to derail the original discussion. Good luck.)
Free press? You must be delusional. If you’d ever consider reading any real investigative journalism (which globalists sponsored corporations are not) you might have a clue about what’s happening in Russia, or the world at all to this day.
Swap Russia out for the US and your comment is 100% accurate
He who is without sin cast the first stone, and the oldest ones left first. Go figure…
Say it in Moscow. Criticize that system from within, I dare you troll.
What do you think is the best strategy to disrupt these groups? I think refusing to pay ransoms helps, but so long as someone still pays they’ll always exist. Hopefully ALPHV allowing the targeting of critical infrastructure will bite them in the arse. I foresee more sanctions against them and more pressure on companies not to pay them.
Eliminating cryptocurrency would make it much more difficult for ransomware operators to collect their ill gotten gains.
Crypto is not going away. (Disclaimer: I do not use Crypto – and wouldn’t). Ragged as it is right now – Crypto ill inevitably improve and be adopted by more mainstream networked users. Right now it’s at the same stage as a gold rush – lawless for the most part.
How could you possibly remove crypto currency? It’s decentralized, may as well take down the internet at that point.
You can block cashing out, you can make trading it illegal, etc.
Enforcing that would be a challenge no doubt, but you could.
You could tax it to hell…
They rob people, get mad that people get mad about being robbed and try and stop them, so they decide to hurt everyone they can. It’s sad but the only thing these leaches of society need is Karma. Thank goodness my database is all still on paper, I’m sure they would take me down if they could.
As an American expat who is a permanent resident in Central Europe, it’s clear to me that this also has geopolitical significance related to the Russo-Ukraine war.
With the BlackCat group lifting all restrictions except one, attacks inside the CIS are prohibited, this appears to enter the realm of 21st century terrorism. Since the BlackCat group likely operates out of Russia, they cannot do what they do without direct or tacit approval from the Kremlin.
That said, the question from my perspective is “what is the red line for the western world?”, because this isn’t just a US vs. Russia issue. We know that attacks on here and there on hospitals and pipelines haven’t crossed the red line so far, but those successful attacks haven’t been strategically grouped close together (yet).
How will the West respond if clusters of refineries or hospitals, or energy generation facilities are targeted? I’m not familiar with the safety protocols of nuclear power plants, but I would assume there are air gaps for critical systems.
I contend that if there were an attack grouping that seriously impacted one or more nations, that could be used as a justification for either extraordinary rendition (exceedingly difficult inside of Russia) or targeted assassinations of the BlackCat developer team.
The statement issued by BlackCat ups the ante to a level that western governments may have no other viable option in the future than to have covert strike teams remove BlackCat developers from the board permanently.
Covert strike teams never get Russian visas because their activities are illegal here. You should undertsnd it as a level-headed, rule-based and resonable intermediate middle class Wystern person.
In the wake of the Colonial Pipeline hacking, the Darkside hacking group that was responsible for the hack announced that it was shutting down due to pressure from U.S. law enforcement. My intuition tells me that the NSA probably got involved as they have a well known reputation for hacking (ex: they were aware of the Apache Heartbleed bug that allowed Equifax to be hacked and kept quiet about it). So, to answer your question, I think you will see an in-kind response on the darknet to state-sanctioned non-state actors going after CIS. If they want to play in the big leagues, they will be dealt with. Period.
theory: there are no real air gaps…
This fake company postofficejobplacement.com charges job applicants a fee of $39 online through cards, the post office says applying for a postal job is free for everyone. It misrepresents itself as an official US postal hiring service
and responsible for a major data breach, exposing the personal information of thousands of US customers.
Shocking Read: https://thenationstime.com/scam-alert-federaljobplacement-com-is-a-fraud/ and https://digitalhubcare.com/2023/12/24/federaljobplacement-com-scam-exposed/
I have my suspicions that the Russian government is working with these ransomware groups. The Russian government may be providing legal cover, or building the tools and then giving them to hacker groups to harass the US and other countries.
The FBI became hero in this incident head of to you FBI , You Siezed the attackers websites and Criminal in Russia Alphav and Blackcat they are very big criminals and FBI seized their websites.
The FBI should really fight fire with fire, and announce that any American cybercriminal who exclusively targets Russia will not only *not* be prosecuted, but may even be rewarded. And that goes for all Russian targets — state assets, Russian military, Russian companies, even random Russian citizens.
Any and all types of cybercrime: ransomware, identity theft, bank and credit card fraud, whatever. Total free reign.
That’s the only thing the Kremlin will understand.
Disagree, actually. The US leans the other way as we are (even now, /s) still a nation of laws.
Lowering ourselves to the standards of any authoritarian kleptocracy, Russia, China, etc,
that’s just a race to the bottom. What the Kremlin may understand (eventually) is isolation,
if/as we are able to inform and incentivize the world to act to uphold international norms.
We accomplish that by replacing their (few) exports, further undercutting their influence.
Enabling scammers and criminals locally only feeds that parasitic ecosystem long term –
Nations of law must further isolate, not emulate state-sponsored criminal networks.
The very, very first move is to remove authoritarian nations from the UN security council,
otherwise that body remains as toothless and irrelevant as we’ve seen of late.
a small world cup is a must-have for fans of football and casual gamers alike.
Wasn’t it found out to be the Ukrainians and Usa? Are to blame for the colonial pipe attack not some haxkers.
Thanks for all you do!
Have you looked into the ransomware attack that took the Kansas District Court portal down for 2.5 months? There was a “security incident” on October 12, and the state shut down all electronic court records, including public portal access and e-filing for attorneys. They finally brought the portal back up three days ago, but it will still be several weeks until dockets are up to date, since all of the paper files need to be scanned and uploaded into the system. Of note, from a November 7 article on StateScoop:
“The security incident last month in Kansas followed an ongoing project initiated in 2018 to centralize the court system into one online system called Odyssey. That project is run by the Dallas software firm Tyler Technologies, a major IT service provider to the public sector.”