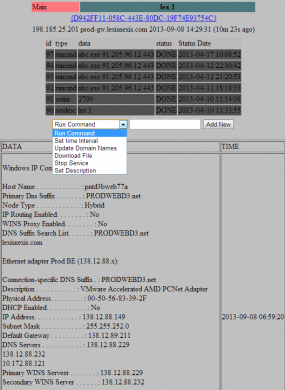
Defendant Charged With Drug Trafficking, Hacking, Money Laundering
Prosecutors in New York today said that federal agencies have taken over the Silk Road, a sprawling underground Web site that has earned infamy as the “eBay of drugs.” On Tuesday, federal agents in San Francisco arrested the Silk Road’s alleged mastermind. Prosecutors say 29-year-old Ross William Ulbricht, a.k.a “Dread Pirate Roberts” (DPR), will be charged with a range of criminal violations, including conspiracy to commit drug trafficking, and money laundering.
A screen shot of the Silk Road Web site, taken Oct. 2, 2013.
The Silk Road is an online black market that as late as last month was hosting nearly 13,000 sales listings for controlled substances, including marijuana, LSD, heroin, cocaine, methamphetamine and ecstasy. Much like eBay sellers, merchants on the Silk Road are evaluated by previous buyers, who are encouraged to leave feedback about the quality of the seller’s goods and services.
The Silk Road is not available via the regular Internet. Rather, it is only reachable via the Tor network, an anonymity network that bounces its users communications across a distributed network of relays run by volunteers all around the world.
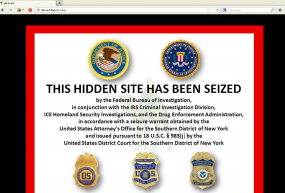
That is, it was until this week, when FBI agents arrested its alleged proprietor and seized the Web servers running the site. The feds also replaced the Silk Road’s home page with a message saying that the site had been seized by the FBI, Homeland Security Department and the Drug Enforcement Administration.
According to a complaint unsealed this week, Ulbricht alone controlled the massive profits generated from the operation of the business. The government alleges that Ulbricht also controlled and oversaw all aspects of the Silk Road, including: the maintenance of the computer infrastructure and programming code underlying the Silk Road Web site; the determination of vendor and customer policies; decisions about what could be sold on the site; and managing a small staff of online administrators who assisted with the day-to-day operations.
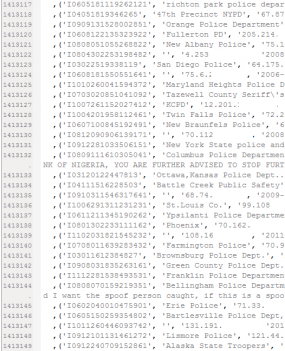
The Silk Road didn’t just sell drugs. For example, the complaint identifies 801 for-sale listings under “digital goods,” which included banking Trojans, pirated content, and hacked accounts at Netflix and Amazon. The “forgeries” section of the Silk Road featured 169 ads from vendors of fake driver’s licenses, passports, Social Security cards, utility bills, credit card statements, car insurance records, and other forms of identity documents.
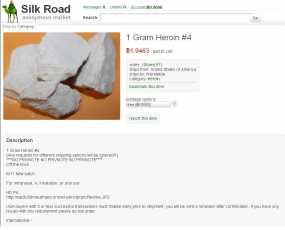
An ad for heroin on the Silk Road. Notice this seller has 97 feedback points.
Another popular section of the Silk Road included 159 listings for generic “Services,” mostly those listed by computer hackers offering such services as hijacking Twitter and Facebook accounts of the customer’s choosing. Other classified ads promised the sale of anonymous bank accounts, counterfeit bills, firearms and ammunition, and even hitmen for hire.
FBI investigators said that on or about March 29, 2013, Ulbricht contacted a Silk Road seller “Redandwhite” to see about hiring him to to take out another Silk Road user — someone going by the nickname “FriendlyChemist” — who was threatening to release the identities of thousands of users of the site.
From the government’s complaint: “Asked what sort of problem FriendlyChemist was causing him, DPR responded in a message dated March 30, 2013, ‘[H]e is threatening to expose the identities of thousands of my clients that he was able to acquire….[T]his kind of behavior is unforgivable to me. Especially here on Silk Road, anonymity is sacrosanct.'” As to the murder-for-hire job he was soliciting, DPR commented that “[i]t doesn’t have to be clean.”
Later that same day, redandwhite sent DPR a message quoting him a price of $150,000 to $300,000, “depending on how you want it done, ‘clean’ or ‘non-clean’.
On March 31, DPR began haggling over the price, responding: “Don’t want to be a pain here, but the price seems high. Not long ago, I had a clean hit done for $80k. Are the prices you quoted the best you can do? I would like this done asap as he is talking about releasing the info on Monday.”
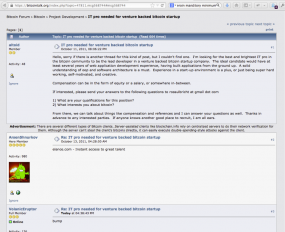
DPR, allegedly using the nickname “altoid” seeks to hire a tech expert for the Silk Road via bitcointalk.org
According to investigators, the two ultimately settle on a price of $150,000, and that Ulbricht paid for the transaction using Bitcoins — an anonymous virtual currency — sending the would-be hit man 1,670 bitcoins for the arranged hit. Bitcoin currency rates fluctuate quite a bit from day to day, but historic sites that track Bitcoin rates show that one bitcoin around that date in late March 2013 was worth about USD $90, meaning investigators believe Ulbricht paid approximately $150,300 for the hit.
The government’s complaint states that the hit wasn’t carried out, but it also doesn’t seem that FriendlyChemist was the source of investigators’ break in this case. That would come on July 23, 2013, when investigators gained access to a Silk Road server and made a complete copy of the data on the machine.
Nicholas Weaver, a researcher at the International Computer Science Institute (ICSI) and at University of California San Diego, said the information contained on the server seized by investigators indicates that Ulbricht/Dread Pirate Roberts routinely failed to heed his own advice to fellow Silk Road users: Prominent on the Silk Road site were links to tutorials DPR penned which laid out the technologies and techniques that users should adopt if they want to keep off the radar of federal investigators.
“This shows me that the head of the Silk Road wasn’t using [encryption] for all his communications, because [the government] wouldn’t have all of this information otherwise, unless of course he stored his encryption key on the server that was seized,” Weaver said. “Either [the government] got his encryption key off of this server or another server that they were able to access, or he wasn’t using encryption at all.”
The complaint also suggests that in June 2013, Ulbricht accessed a server used to control the Silk Road site from an Internet cafe that was 500 feet from the hotel he was staying at in San Francisco.
Continue reading →












![The botnet interface used by the miscreants who own and operate ssndob[dot]ms](https://krebsonsecurity.com/wp-content/uploads/2013/09/SSNdobBotC2-600x118.png)