Authorities seized computers and servers in the United States and seven other countries this week as part of an ongoing investigation of a hacking gang that stole $72 million by tricking people into buying fake anti-virus products. Police in Ukraine said the thieves fleeced unsuspecting consumers with the help of the infamous Conficker worm, although it remains unclear how big a role the fast-spreading worm played in this crime.
The Security Service of Ukraine (SBU) said today that it had seized at least 74 pieces of computer equipment and cash from a criminal group suspected of running a massive operation to steal banking information from consumers with the help of Conficker and scareware, a scam that uses misleading security alerts to frighten people into paying for worthless security software. A Google-translated version of an SBU press release suggests that the crime gang used Conficker to deploy the scareware, and then used the scareware to launch a virus that stole victims’ financial information.
The Ukrainian action appears to be related to an ongoing international law enforcement effort dubbed Operation Trident Tribunal by the FBI. In a statement released Wednesday, the U.S. Justice Department said it had seized 22 computers and servers in the United States that were involved in the scareware scheme. The Justice Department said 25 additional computers and servers located abroad were taken down as part of the operation, in cooperation with authorities in the Netherlands, Latvia, Germany, France, Lithuania, Sweden and the United Kingdom.
On Tuesday, The New York Times reported that dozens of Web sites were knocked offline when FBI officials raided a data center in Reston, Va. and seized Web servers. Officials from an affected hosting company told the Times that they didn’t know the reason for the raid, but the story suggested it may have been related to an ongoing investigation into a string of brazen intrusions by the hacktivist group “Lulzsec.” Sources close to the investigation told KrebsOnSecurity that the raid was instead related to the scareware investigation.
The FBI’s statement confirms the SBU’s estimate of $72 million losses, estimating that the scam claimed at least 960,000 victims. Although the FBI made no mention of Conficker in any of its press materials, the Ukrainian SBU’s press release names and quotes Special Agent Norman Sanders from the FBI’s Seattle field office, broadly known in the security industry as the agency’s lead in the Conficker investigation. Conficker first surfaced in November 2008. The SBU said the FBI has been investigating the case for three years. [Update, June 24, 9:37 a.m.: Not sure whether this was an oversight or a deliberate attempt to deceive, but the picture showing the stack of PCs confiscated in this raid is identical to the one shown in an SBU press release last fall, when the Ukrainian police detained five individuals connected to high-profile ZeuS Trojan attacks.]
“Exchanging information with the Security Service, it became clear that the intelligence services of both countries [were] investigating criminal acts of the same persons,” the SBU said in its prepared statement.
There are no court records of this case publicly available in the United States; a spokesperson at the Justice Department office in the Western District of Washington said the documents remain sealed. She referred questions about the case to the FBI headquarters in Washington, D.C. When asked specifically about the Conficker connection, FBI spokeswoman Jenny Shearer would say only that “there are indications that one of the delivery mechanisms for the scareware in this investigation was a Conficker variant.”
The Conficker element of this case is interesting for several reasons: The worm was so sophisticated and spread so quickly that it prompted unprecedented cooperation among governments and security experts, who formed the Conficker Working Group to help contain the damage wrought by the worm. Conficker certainly wrought financial damage — it is estimated to have infected more than 12 million PCs — but until today there has been little information to suggest that this massive crime machine was used to generate profits for cyber crooks.
I know of two previous instances in which Conficker was linked to scareware scams. The first involved the initial version of the worm, which instructed all infected PCs to visit and download a file from TrafficConverter.biz, the domain of an affiliate program that paid hackers to distribute its brand of scareware. As I reported in a March 2009 story in The Washington Post, the top affiliates for that program were making hundreds of thousands of dollars a month pushing scareware, although it is not clear whether Conficker-infected systems ever received any scareware downloads from the domain. From that story:
“By the time Conficker first surfaced, TrafficConverter was nearing the end of a contest in which the top-selling affiliates competed for prizes, such as computers, fancy cell phones and other electronics. The grand prize? A Lexus IS250, a sports sedan that starts at $36,000.
At first glance, it is tempting to assume that the Conficker worm authors were in league with the operators of TrafficConverter.biz, and thus trying to drive traffic to the site — perhaps in an attempt to push the contest in favor of one or more affiliates. On the other hand, this may have been an attempt by the Conficker authors or a competing affiliate program to hinder and ultimately shutter TrafficConverter.biz, either by causing law enforcement and the security community to focus their attention on it, or by flooding the site with traffic from hundreds of thousands of Conficker-infected systems.”
And flood the site it did. According to [SecureWorks’s Joe] Stewart’s review of the traffic log files for TrafficConverter.biz, during a 12-hour period on Nov. 24, the site was bombarded by more than 83 million hits from at least 179,000 unique Internet addresses.
The traffic from Conficker.A infected systems to TrafficConverter.biz might have translated into monster installs for affiliates of the site. Ironically, all of that traffic from Conficker-infected systems appears to have gone to a non-existent page on TrafficConverter.biz, Stewart said. In short, the site missed a pretty huge opportunity to convert a whole lot of traffic.
Still, had the curators of TrafficConverter.biz actually placed a file at that link for download, the resulting traffic from 179,000 systems trying to download that file at the same time probably would have crashed the site entirely, Stewart said.”
Conficker’s second association with scareware came three weeks after that story. On April 8, 2009, Kaspersky Lab reported that it had seen some Conficker infected systems updated with a scareware product called Spyware Protect 2009. Kaspersky analysts also discovered that infected PCs were seeded with another update: a version of the Waledac worm, which is able to steal data and send spam.
Anyone with information about the identity of the Conficker author(s) could have a lucrative tip on their hands: Microsoft has an outstanding $250,000 bounty for information leading to the arrest and conviction of those responsible for launching the worm.




Compare pictures from article about conficker busts: http://bit.ly/lyrrk1 and pics from article about zeus busts: http://bit.ly/cwufdV
Know why they are same? Because there were no any busts 🙂
Btw do you know what happened with those ‘zeus’ busts in ukraine? Heard about any courts?
Know why you dont? 😉
Off-topic, but it appears someone doesn’t like you. I wonder why 😉
http://www.f-secure.com/weblog/archives/00002191.html
Actually, it’s pretty high praise for a self-employed investigative reporter to be singled out as someone who is considered a threat by criminals all over the planet.
Brian very very good at what he does. You need back up let me know 🙂
The situation is bad enough with malware being getting quickly more and more sophisticated and devious new methods to push it toward victim’s computers, but I just hate when people, through crass carelessness are making the bad guys an easier life.
In late 2009 I was doing some consulting work in a large company (the kind of that has over 100.000 employees around the globe. Because of security rules I was not allowed to connect my laptop to the internal network, therefore I went to one of the employees with a NEW USB stick and asked him to place there some application logs which I was supposed to send to the vendor. He used his office computer to transfer the logs and when returned the stick to me, I noticed right away it was infected with Conficker. I told him about that and he just replied he is aware of it, the antivirus chosen by his company to run on office computers is not able to clean it, a few other tricks he tried to disinfect also failed, what else one could reasonably expect from him to do ?
It just left me speechless, this guy had admin rights and was connecting to equipment which cost millions.
In fairness he was let go by his employer within 6 weeks or so from that incident, though on other causes than those stemming from his work computer being infected.
Reported elsewhere, in the process of shutting down the scareware ring, the FBI also stole servers supporting legitimate websites.
http://blog.instapaper.com/post/6830514157
http://bits.blogs.nytimes.com/2011/06/21/f-b-i-seizes-web-servers-knocking-sites-offline/
Sorry – Brian had NYTimes in article. I missed that I was duplicating.
Regarding Instapaper:
Interesting to see how fast people complained in the comments on the NY Times article that the FBI exceeded its authority and how those same people conveniently ignored the information that Digital One had no personnel at the premises. The physical facilities operator had no way of knowing what company stored used what specific server and so the FBI had to take everything. And the FBI isn’t about to wait for a Digital One employee to arrive because a raid on hardware means no time must be allowed for someone outside the premises to command to overwrite any evidence.
I am amazed these fools don’t realize criminals like to run their operations in close proximity to legitimate businesses, as the old saying goes, you are judged by the company you keep, and the criminals need camoflage.
Another analogy is a leased parking lot. Leave your vehicle parked there. A criminal who just happened to have used a vehicle of the same make and color in a kidnapping parks and abandons that vehicle in the lot. Police arrive but don’t have exact license plate numbers (it’s hard to read some license plates) so they begin searching both vehicles for evidence.
Sometimes I think people live a life that is too sheltered.
Instapaper has nothing to complain about. He should get his own hardware and run it on his own property … oops, that’s expensive ! Cheaper to outsource it ! Get the service from a business located in a foreign company that leases the actual equipment in the same country as the customer.
I wonder if the investigation would have proceeded this fast if there had not been banking info involved. Seems like no one’s chasing the guy that just collects $50 from scareware.
I kind of liked Pavel despite what was written about him. I hope his kids and wife will be OK.
Brian, what date are you showing that he fled the country and what date did the other arrest that caused him to flee happen? I’d like to compare some timelines of things I have. Thanks
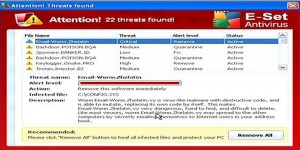
Scareware is the most annoying threat out there. Not only are there people who will fall prey to it through lack of knowledge and naivety, but sometimes the way it pops up on your system can mean you accidentally click on it (which I did a few years ago on an old laptop). Plus it can look very similar to the real thing.
I’m curious about how many criminal groups are actually out there earning this type of money, and where they are in the world. Any idea where I could find that kind of info?
Hi Amy — I should have another post later this week that delves into the answers to your questions a bit more.
This money has moved into the porn biz.
oh… look into montreal-based porn producers. that is all.