The Federal Bureau of Investigation warned this week that cyber thieves have stolen approximately $20 million over the past year from small to mid-sized U.S. businesses through a series of fraudulent wire transfers sent to Chinese economic and trade companies located near the country’s border with Russia.
 The FBI said that between March 2010 and April 2011, it identified twenty incidents in which small to mid-sized organizations had fraudulent wire transfers to China after their online banking credentials were stolen by malicious software. The alert was sent out Tuesday in cooperation with the Internet Crime Complaint Center and the Financial Services Information Sharing and Analysis Center (FS-ISAC), an industry consortium. The alert notes that actual victim losses are $11 million, suggesting that victim banks were able to claw back some of the fraudulent transfers.
The FBI said that between March 2010 and April 2011, it identified twenty incidents in which small to mid-sized organizations had fraudulent wire transfers to China after their online banking credentials were stolen by malicious software. The alert was sent out Tuesday in cooperation with the Internet Crime Complaint Center and the Financial Services Information Sharing and Analysis Center (FS-ISAC), an industry consortium. The alert notes that actual victim losses are $11 million, suggesting that victim banks were able to claw back some of the fraudulent transfers.
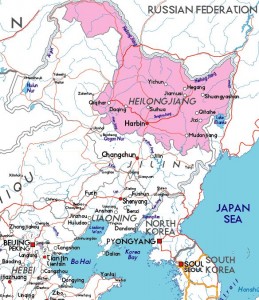
The FBI says it doesn’t know who is behind these fraudulent transfers, but that the intended recipients are companies based in the Heilongjiang province of the People’s Republic of China, and that these firms are registered in port cities that are located near the Russia-China border. The agency says the companies all use the name of a Chinese port city in their names, such as Raohe, Fuyuan, Jixi City, Xunke, Tongjiang, and Donging, and that the official name of the companies also include the words “economic and trade,” “trade,” and “LTD”. The recipient entities usually hold accounts with a the Agricultural Bank of China, the Industrial and Commercial Bank of China, and the Bank of China.
From the advisory (PDF):
“In a typical scenario, the computer of a person within a company who can initiate funds transfers on behalf of the U.S. business is compromised by either a phishing email or by visiting a malicious Web site. The malware harvests the user’s corporate online banking credentials. When the authorized user attempts to log in to the user’s bank Web site, the user is typically redirected to another Web page stating that the bank Web site is under maintenance or is unable to access the accounts. While the user is experiencing logon issues, malicious actors initiate the unauthorized transfers to commercial accounts held at intermediary banks typically located in New York. Account funds are then transferred to the Chinese economic and trade company bank account.”