A new version of the infamous Koobface worm designed to attack Mac OS X computers is spreading through Facebook and other social networking sites, security experts warn.
Security software maker Intego says this Mac OS X version of the Koobface worm is being served as part of a multi-platform attack that uses a malicious Java applet to attack users. According to Intego, the applet includes a prompt to install the malicious software:
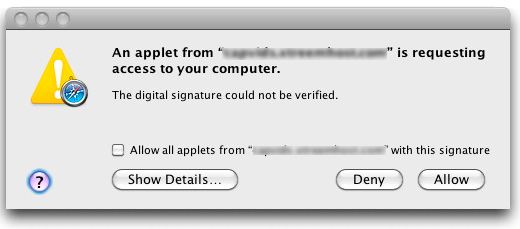 Intego notes that if the download is allowed, “it runs a local web server and an IRC server, acts as part of a botnet, acts as a DNS changer, and can activate a number of other functions, either through files initially installed or other files downloaded subsequently. It spreads by posting messages on Facebook, MySpace and Twitter, usually trying to get people to click a link to view some sort of video.”
Intego notes that if the download is allowed, “it runs a local web server and an IRC server, acts as part of a botnet, acts as a DNS changer, and can activate a number of other functions, either through files initially installed or other files downloaded subsequently. It spreads by posting messages on Facebook, MySpace and Twitter, usually trying to get people to click a link to view some sort of video.”
SecureMac also has a writeup on what appears to be the same threat, which it calls OSX.Boonana.a. SecureMac says that “there have been reports of similar behavior in recent trojan horses targeting Microsoft Windows, but they have not included cross-platform capabilities until now.”
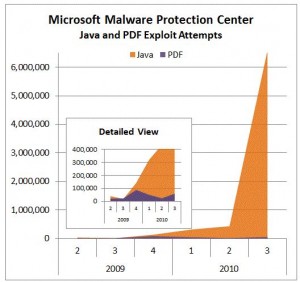
It is not surprising that attackers would begin leveraging Java to attack Mac users with threats that have traditionally only menaced Windows users. My research shows that Java is now the leading vector of attacks against Windows systems, findings that recently were buttressed by oodles of attack data released by Microsoft. Also, Java was designed to be a cross-platform technology that would allow applications to run seamlessly regardless of the operating system relied upon by the user. It makes sense for attackers to consider Java as a platform-agnostic vehicle for delivering platform-specific malicious software.