Authorities in the United States, United Kingdom and Ukraine launched a series of law enforcement sweeps beginning late last month against some of the world’s most notorious gangs running botnets powered by ZeuS, a powerful password-stealing Trojan horse program. ZeuS botnet activity worldwide took a major hit almost immediately thereafter, but it appears to be already on the rebound, according to one prominent ZeuS-watching site.
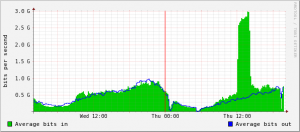
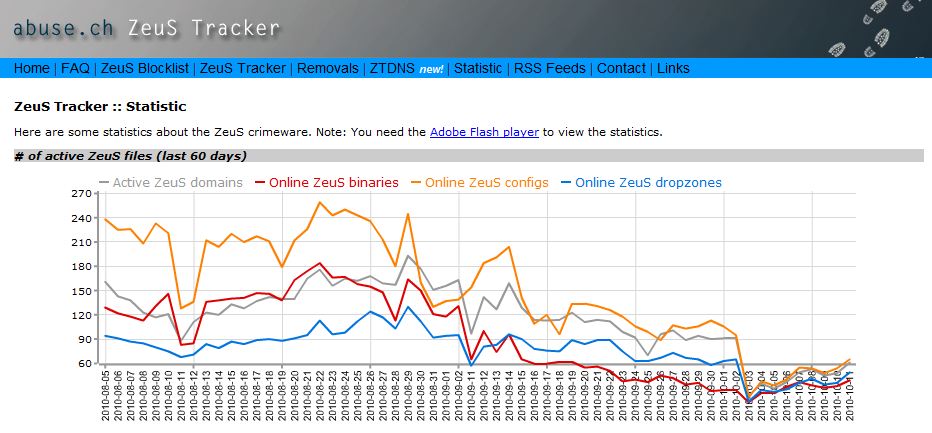 Statistics collected by the Web site Zeus Tracker indicate that while ZeuS botnet activity was already on the wane in the weeks leading up to the end of last month, that activity positively tanked following the recent busts, dipping to its lowest level since the Troyak takedowns earlier this year. For instance, prior to the arrests that began on Sept 29, Zeus Tracker was tracking more than 90 active Zeus control domains. By Oct. 3, that number had fallen to just 20.
Statistics collected by the Web site Zeus Tracker indicate that while ZeuS botnet activity was already on the wane in the weeks leading up to the end of last month, that activity positively tanked following the recent busts, dipping to its lowest level since the Troyak takedowns earlier this year. For instance, prior to the arrests that began on Sept 29, Zeus Tracker was tracking more than 90 active Zeus control domains. By Oct. 3, that number had fallen to just 20.
I contacted Roman Hüssy, the Swiss information technology expert who maintains the tracking site, to see if there could be some technical or glitchy explanation for the dramatic drop. Hüssy said while there are criminal technologies being built into malware that try to prevent ZeuS Tracker from being able to follow ZeuS botnet infrastructure, he’s fairly sure he has managed to bypass it.
“Another thing which I’ve seen is that some [ZeuS botnet command servers] are using geo-IP location, [so that] if a ZeuS group just targets U.K. banks, they will do a geo-location restriction on the [control] server, and allow just bots from the U.K.” to ping the servers, he wrote in an instant message.
Some folks who probably know more about what’s really going on here (targeted takedowns, maybe?) aren’t responding at the moment, which tells me we may hear more about other factors that contributed to this drop in the days or weeks ahead. Stay tuned.