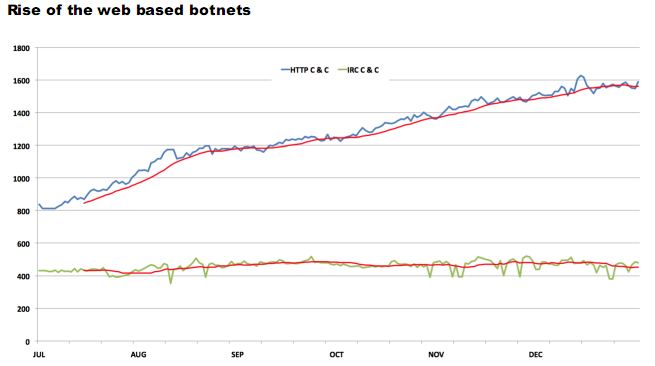
New reports released this week on recent, high-profile data breaches make the compelling case that a simmering Cold War-style cyber arms race has emerged between the United States and China.
 A study issued Thursday by McAfee and the Center for Strategic and International Studies found that more than half of the 600 executives surveyed worldwide said they had been subject to “stealthy infiltration” by high-level adversaries, and that 59 percent believed representatives of foreign governments had been involved in the attacks.
A study issued Thursday by McAfee and the Center for Strategic and International Studies found that more than half of the 600 executives surveyed worldwide said they had been subject to “stealthy infiltration” by high-level adversaries, and that 59 percent believed representatives of foreign governments had been involved in the attacks.
A more granular analysis issued Thursday by Mandiant, an Alexandria, Va. based security firm, focuses on data breaches it has responded to involving the so-called “advanced persistent threat,” or those characterized by highly targeted attacks using custom-made malicious software in the hands of patient, well-funded assailants.
Mandiant notes that the scale, operation and logistics of conducting these attacks – against the government, commercial and private sectors – indicates that they’re state-sponsored.
The Chinese government may authorize this activity, but there’s no way to determine the extent of its involvement. Nonetheless, we’ve been able to correlate almost every APT intrusion we’ve investigated to current events within China. In all cases, information exfiltrated by each set of attackers correlates with a need for intelligence related to upcoming major U.S. / China mergers and acquisitions, corporate business negotiations, or defense industrial base acquisition opportunities [emphasis added].
The reports come just days after the Christian Science Monitor revealed that three Texas-based oil companies – Conoco, ExxonMobil and Marathon – were alerted by the FBI that their systems were penetrated back in 2008. The Monitor story said the attacks, thought to have originated in China, targeted “bid data” about oil reserves and potential drilling sites.
Continue reading →
![]() Microsoft today released a baker’s dozen of software updates to fix twice as many vulnerabilities in its various Windows operating systems and other software. Translation: If you use any supported version of Windows, it’s time once again to update your PC.
Microsoft today released a baker’s dozen of software updates to fix twice as many vulnerabilities in its various Windows operating systems and other software. Translation: If you use any supported version of Windows, it’s time once again to update your PC.