The presence of rogue anti-virus products, also known as scareware, on a Microsoft Windows computer is often just the most visible symptom of a more serious and insidious system-wide infection. To understand why, it helps to take a peek inside some of the more popular rogue anti-virus distribution networks that are paying people to peddle scareware alongside far more invasive threats.
 Distributors or “affiliates” who sign up with avprofit.com, for example, are given access to an installer program that downloads not only rogue anti-virus but also ZeuS, a stealthy piece of malware that specializes in mining online banking credentials from infected PCs. ZeuS is the very piece of malware directly responsible for helping thieves steal tens of millions of dollars from small to mid-sized businesses over the past year.
Distributors or “affiliates” who sign up with avprofit.com, for example, are given access to an installer program that downloads not only rogue anti-virus but also ZeuS, a stealthy piece of malware that specializes in mining online banking credentials from infected PCs. ZeuS is the very piece of malware directly responsible for helping thieves steal tens of millions of dollars from small to mid-sized businesses over the past year.
Avprofit says it will pay affiliates roughly $1,000 for every 1,000 times they distribute this installer program, or about $1 per install. Typically, affiliates will embed these installers at porn sites or bundle them with programs seeded on peer-to-peer file-sharing services. The nightmare for the victim starts when he or she responds to the fake anti-virus pop-up warning of supposed threats resident on the victim’s PC, by agreeing to download and run a scanning tool.
What’s remarkable about this entire ecosystem is that in many cases, victims who have this installer run on their systems often end up paying for the rogue anti-virus, in addition to unknowingly giving up their passwords and handing complete control of their computer to the bad guys running this distribution network.
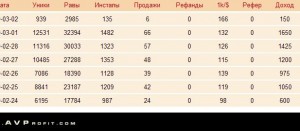
Stats from Avprofit’s internal pages suggest that on average, about 4 percent of victims fall for the rogue anti-virus ruse and fork over their credit card information to purchase the worthless software. For example, on Feb. 28, one affiliate generated some 1,482 installs resulting in 66 sales and $1,650 in commissions. The day prior, the affiliate drummed up 1,323 installs, resulting in 57 sales for a daily income of $1,425.
 A relatively recent copy of the installer that avprofit.com made available to affiliates was sent to two places: Joebox.org, which conducts extremely detailed, automated and free malware analysis, and Virustotal.com, to see how well the installer was detected by various anti-virus tools on the market today.
A relatively recent copy of the installer that avprofit.com made available to affiliates was sent to two places: Joebox.org, which conducts extremely detailed, automated and free malware analysis, and Virustotal.com, to see how well the installer was detected by various anti-virus tools on the market today.
According to Joebox.org, the installer dropped a file with this unique file signature, which also was flagged by another free and automated malware scanner — ThreatExpert — as ZeuS, a.k.a. “Zbot”.
Virustotal found that just 16 out of 42 anti-virus products it used to scan the installer file detected it as malicious.
The e-mail address listed in the Web site registration records for avprofit.com is “abusemaildhcp@gmail.com,” the same e-mail address used to register updatekernel.com, the site that AVprofit’s installer reached out to in order to grab the ZeuS Trojan. That e-mail address also is affiliated with a number of Web sites responsible for helping criminals recruit money mules here in the United States and abroad.
Further reading:
Web Fraud 2.0: Franchising Cyber Crime




This smells familiar : http://borntobebest.biz/
Interesting – I just ran a md5/sha1 analysis at VirusTotal.com of the hashs provided in the ThreatExpert report and each one error-ed out every time.
“Error:
Please check you had introduced a correct hash and copied every character from the control key.”
don’t include the 0x
Thanks! That did the trick.
I really just wanted to see if whether or not my AV program detected it. It does, but the overall results have also improved quite a bit since Brian’s post: 33/41 (80.49%)
Nice Work. Updatekernel.com is also the c&c used in the spearphishing attacks that used portions of your article about spearphishing attacks against .gov & .mil email addresses.
http://www.nartv.org/2010/03/01/the-kneber-botnet-spear-phishing-attacks-and-crimeware/
So I probably shouldn’t click on this:
http://www.failcomputer.com/?p=522
Only if you’re a Windows user.
So what were the “16 out of 42 anti-virus products it used to scan the installer file detected it as malicious”?
I can’t tell you what the 16 out of 42 were, but here’s the link for the current results: http://bit.ly/al6Vrx
I never even heard of the ones that couldnt detect it. AhnLab-V3? Authentium?
The top 10 or so AV products are pretty good at detection and SBE is free for home users. The whole ‘x out y couldnt detect this’ is a lame scare tactic.