A number of cybercriminal innovations are making it easier for scammers to cash in on your upcoming travel plans. This story examines a recent spear-phishing campaign that ensued when a California hotel had its booking.com credentials stolen. We’ll also explore an array of cybercrime services aimed at phishers who target hotels that rely on the world’s most visited travel website.
According to the market share website statista.com, booking.com is by far the Internet’s busiest travel service, with nearly 550 million visits in September. KrebsOnSecurity last week heard from a reader whose close friend received a targeted phishing message within the Booking mobile app just minutes after making a reservation at a California hotel.
The missive bore the name of the hotel and referenced details from their reservation, claiming that booking.com’s anti-fraud system required additional information about the customer before the reservation could be finalized.

The phishing message our reader’s friend received after making a reservation at booking.com in late October.
In an email to KrebsOnSecurity, booking.com confirmed one of its partners had suffered a security incident that allowed unauthorized access to customer booking information.
“Our security teams are currently investigating the incident you mentioned and can confirm that it was indeed a phishing attack targeting one of our accommodation partners, which unfortunately is not a new situation and quite common across industries,” booking.com replied. “Importantly, we want to clarify that there has been no compromise of Booking.com’s internal systems.”
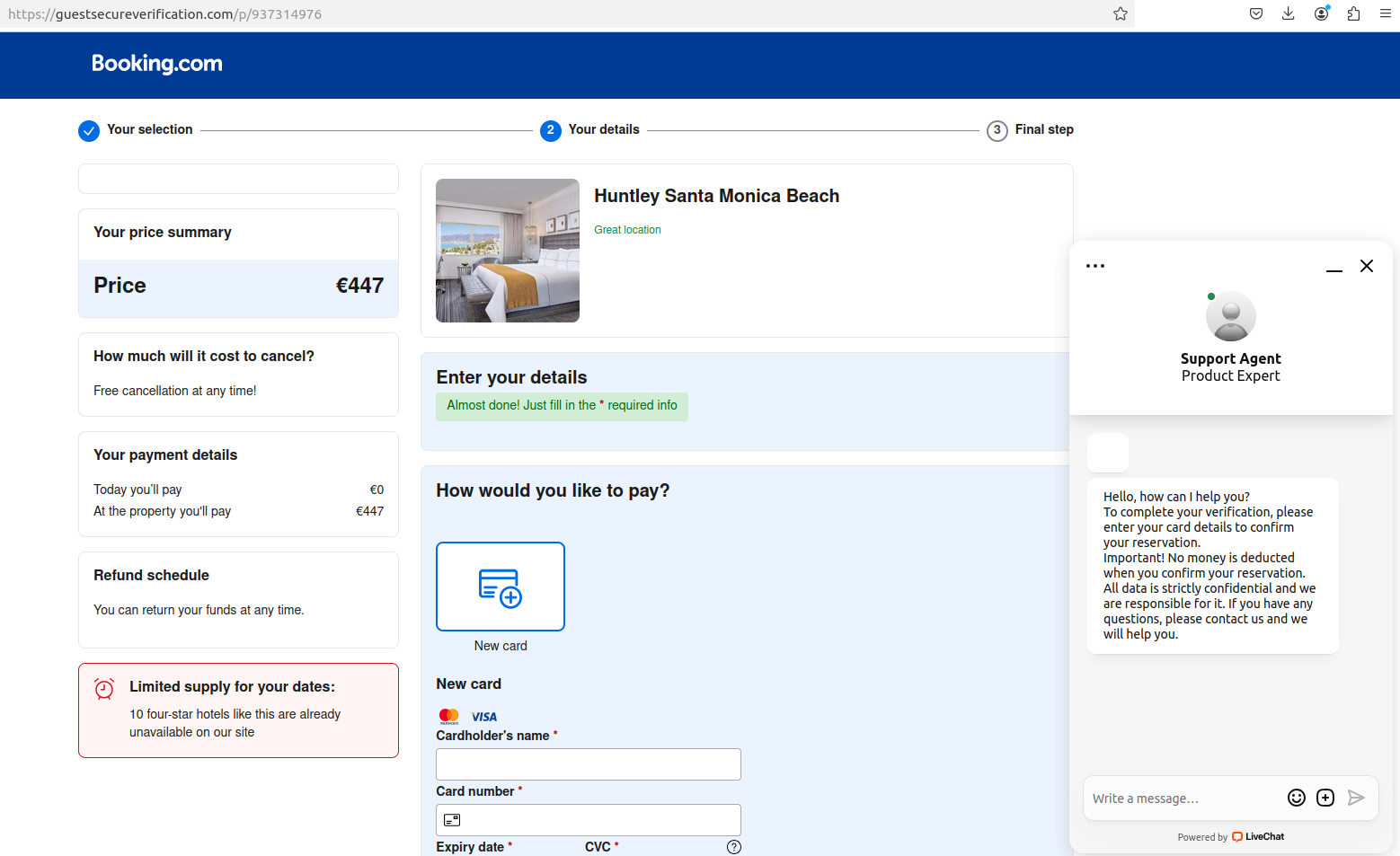
The phony booking.com website generated by visiting the link in the text message.
Booking.com said it now requires 2FA, which forces partners to provide a one-time passcode from a mobile authentication app (Pulse) in addition to a username and password.
“2FA is required and enforced, including for partners to access payment details from customers securely,” a booking.com spokesperson wrote. “That’s why the cybercriminals follow-up with messages to try and get customers to make payments outside of our platform.”
“That said, the phishing attacks stem from partners’ machines being compromised with malware, which has enabled them to also gain access to the partners’ accounts and to send the messages that your reader has flagged,” they continued.
It’s unclear, however, if the company’s 2FA requirement is enforced for all or just newer partners. Booking.com did not respond to questions about that, and its current account security advice urges customers to enable 2FA.
A scan of social media networks showed this is not an uncommon scam.
In November 2023, the security firm SecureWorks detailed how scammers targeted booking.com hospitality partners with data-stealing malware. SecureWorks said these attacks had been going on since at least March 2023.
“The hotel did not enable multi-factor authentication (MFA) on its Booking.com access, so logging into the account with the stolen credentials was easy,” SecureWorks said of the booking.com partner it investigated.
In June 2024, booking.com told the BBC that phishing attacks targeting travelers had increased 900 percent, and that thieves taking advantage of new artificial intelligence (AI) tools were the primary driver of this trend.
Booking.com told the BCC the company had started using AI to fight AI-based phishing attacks. Booking.com’s statement said their investments in that arena “blocked 85 million fraudulent reservations over more than 1.5 million phishing attempts in 2023.”
The domain name in the phony booking.com website sent to our reader’s friend — guestssecureverification[.]com — was registered to the email address ilotirabec207@gmail.com. According to DomainTools.com, this email address was used to register more than 700 other phishing domains in the past month alone.
Many of the 700+ domains appear to target hospitality companies, including platforms like booking.com and Airbnb. Others seem crafted to phish users of Shopify, Steam, and a variety of financial platforms. A full, defanged list of domains is available here.
A cursory review of recent posts across dozens of cybercrime forums monitored by the security firm Intel 471 shows there is a great demand for compromised booking.com accounts belonging to hotels and other partners.
One post last month on the Russian-language hacking forum BHF offered up to $5,000 for each hotel account. This seller claims to help people monetize hacked booking.com partners, apparently by using the stolen credentials to set up fraudulent listings.
A service advertised on the English-language crime community BreachForums in October courts phishers who may need help with certain aspects of their phishing campaigns targeting booking.com partners. Those include more than two million hotel email addresses, and services designed to help phishers organize large volumes of phished records. Customers can interact with the service via an automated Telegram bot.
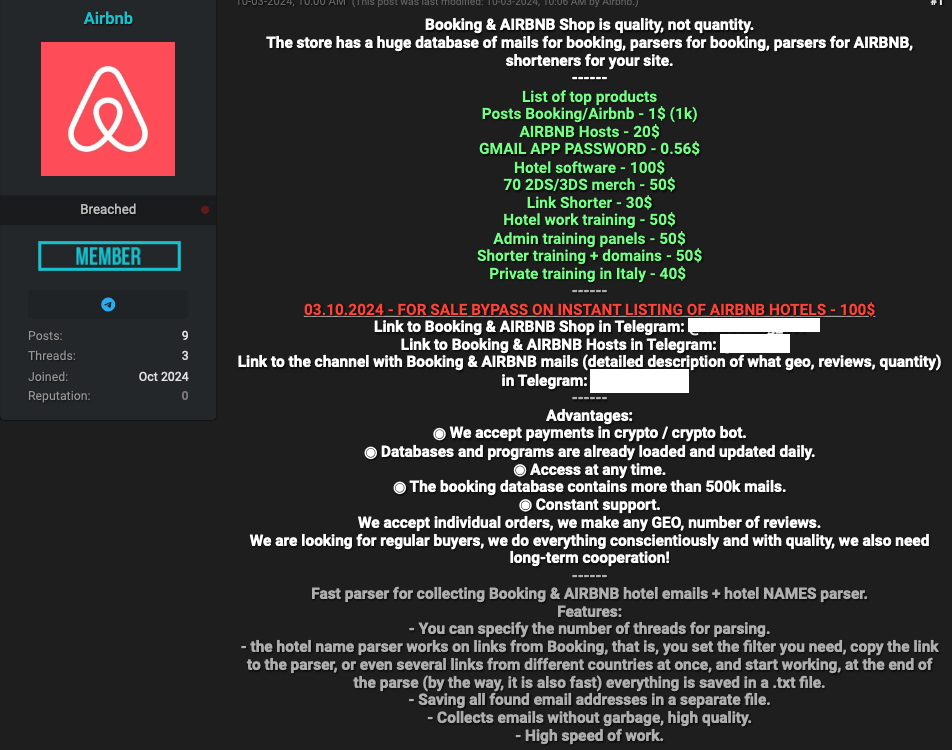
Some cybercriminals appear to have used compromised booking.com accounts to power their own travel agencies catering to fellow scammers, with up to 50 percent discounts on hotel reservations through booking.com. Others are selling ready-to-use “config” files designed to make it simple to conduct automated login attempts against booking.com administrator accounts.
SecureWorks found the phishers targeting booking.com partner hotels used malware to steal credentials. But today’s thieves can just as easily just visit crime bazaars online and purchase stolen credentials to cloud services that do not enforce 2FA for all accounts.
That is exactly what transpired over the past year with many customers of the cloud data storage giant Snowflake. In late 2023, cybercriminals figured out that while tons of companies had stashed enormous amounts of customer data at Snowflake, many of those customer accounts were not protected by 2FA.
Snowflake responded by making 2FA mandatory for all new customers. But that change came only after thieves used stolen credentials to siphon data from 160 companies — including AT&T, Lending Tree and TicketMaster.




I booked two hotels in New Zealand earlier this year and got spam messages like this for both. Figured maybe it was an NZ thing. I went to one website and got suspicious. Tried to contact the hotel through Booking.com with the email, but Booking.com bounced MY inquiry as suspicious. Great.
Emailed the hotels directly and they both said no, not them. Also that they hadn’t been hacked and this was Booking.com’s problem. Booking.com, naturally, denied any knowledge at all. A Google search showed it’s been rampant for quite a while.
Yes, Booking.com should require 2FA for all of their hotel partners immediately. But they just don’t care I guess.
Anyway, no more Booking.com for me. I learned my lesson, luckily without a problem.
“Antifroud” would make me think something was rotten in Denmark even if I wasn’t booking a Scandinavian vacation.
Poor spelling, fractured English (or any other language), and urgency of action are all hallmarks that you’re being hacked.
Also using a virtual card can limit the damages of being hacked. Search ‘one time use credit card’.’
VCC is a high-risk indicator, too. Are you trying to help facilitate cybercrime, here in the comments?! Gee golly gosh darn it!
We booked through Booking.com recently, and got a message that the place needed to verify our identity to prevent fraud. They wanted a picture of a driver’s license and a picture of the credit card we used. Obviously that’s nuts so we called Booking.com and they called the place and it was legit. This places booking procedures were indistinguishable from a scam, and Booking.com was completely OK with it and said we should do it. It worked out for this trip but we’re never using Booking.com again.
A colleagues client was caught up in this mess and said dealing with Booking.com support staff was a nightmare. They were so condescending and getting them to implement even the most basic security on their end was non existent. The fact that they pat themselves on the back for having implemented AI offensive security tools prior to June 2024, yet have only just implemented MFA defensive policies since September 2024 is telling and proves that the decision making in the C Suite is severely lacking and investors should really take note.
Of even more concern is their statement to Brian;
““[We] can confirm that it was indeed a phishing attack targeting one of our accommodation partners, which unfortunately is not a new situation and quite common across industries,” booking.com replied. “Importantly, we want to clarify that there has been no compromise of Booking.com’s internal systems.””
Attempts at normalising this activity and a companies lack of response or empathy for the real victims is wrong on so many levels and decision makers need to be held accountable. It doesn’t have to be COMMON, it’s just you can’t get your sh*t together, won’t admit it and ONLY wish to blame others for your inactions. This is just corporate gaslighting at its finest.
welcome to Merica.. home of the projectors, manipulators, karens, and woke dodo birds
they love to make that score, but then cry when they get caught or end up 86
It’s not very clear what your anecdotes have to do with the comment you’re replying under. Care to explain?
He thinks Obama runs Booking.yeah because reasons. Nothing to explain.
You can go about your business.
I fell for a Booking.Com phish last year. It worked because it was a message that I received within their mobile app from the hotel. They knew my name, the hotel I was booked into, the reservation dates etc. The message was from the hotel’s actual account. I received it on my phone after a long flight. I was jetlagged so it was just the sort of situation where one is less likely to pause about clicking the link. I realized once I had provided a new card that I’d been phished and had my bank cancel the card.
Booking.com never responded to any of my calls and emails. Doing a web search I discovered that Booking.Com has had poor security on its systems for years and these types of compromise of hotel booking.com accounts are common.
I now use booking.com as a search engine to find hotels and book directly with the hotels. I use Expedia and other travel sites in the same way. If something goes wrong, dealing with a third party is often a nightmare.
I was just getting ready to post the same suggestion. Leaving out the middleman is always a better way to deal with any reservation, especially the airlines. I actually had a hotel in Italy find me a room in a competitor’s hotel on a holiday weekend when I had a problem with a reservation that was partially my fault. Try to get Booking.com to do that.
A better suggestion. might be to use Booking.com as a search tool and then book the reservation directly with the hotel. Most small hotels I have discussed this with have said that they would gladly match or beat any Booking.com rate since the fees Booking.com charges them are substantial. When dealing directly with the hotel you take out the middleman if there are problems with the reservation. I actually had a hotel in Italy find me a room in a competitor’s hotel when I had a problem with a reservation which was partially my fault. Try and get Booking.com to do that.
In many countries booking.com charges the hotel / provider 15 or even 20%. Unsurprisingly many will offer you a lower rate if you contact them directly quoting booking.com’s rate. In some cases where I have booked through booking.com, the owner has asked me to cancel the reservation and pay them a lower rate directly. Win-win !
I used booking [.]com once to get tickets to Silver Dollar City and a hotel in Branson. The day of my booked visit there was a fire and they closed the park, giving us rainchecks that were only good for 30 days. There was no way we could come back another time so decided to stay an additional night. Contacted booking and they were no help in securing the room for an additional night. The hotel (Raddison Inn) would let us extend our stay but at its normal rate, not the one we got from booking.
Me too, I booked a hotel in Italy via Booking.com. Was supposed to pay as soon as I arrive but suddenly received a message (28.11.2024) on the official Booking.com app saying I must pay straightaway. I tried to ask questions but nobody answered. The spelling was rather bad too. They told me to follow the link and pay ASAP, so I did. Soon after that the hotel wrote me a message saying it wasn’t them and that I shouldn’t pay. I have complained to Booking but they ignored me for a couple of days. Later they responded that they were investigating the case. I asked if they were going to return me the money but they never answered.
So you noticed typos yet decided to pay immediately anyway, through the provided link associated with the errors, rather than going through your own known-good URL or confirming the charges via known-good support #.
This should be a larger lesson – don’t just blindly follow misspelled directions from an assumed source asking for money or credentials. Think about what you’re doing before you do it. If you want to investigate, use known-good URL’s and support numbers. Never. Click. Links. Blindly.
Don’t you think it is a little weird to victim shame people in the comments of somebody else’s blog? Let’s not even get into the fact that you write like deaf people speak.
If one feels ashamed by their actions presumably they (may) learn from them, and if the actions lead to (perhaps easily avoidable) financial or PII losses, I’d presume most people would prefer the “shaming” as you’d describe it to those outcomes. However, it wasn’t shaming at all. It was a valid recap, emphasis mine. I didn’t call the person names nor was that at all the point, as I pointed out points of failure were in their decision making should similar occasions occur. *(Yo dawg, I heard you like alliterations..)
But as you’d clearly prefer to critique an offhanded comment’s “writing style” in some e-browbeating type of pedantry, I don’t really find your perhaps small minded critique of “pretty weird” to be valid based as it is in a false premise of your own limited imagination. May you be deaf or at least mute in the next life, sir, to know the difference and appreciate it perhaps.
George Washington —
‘If freedom of speech is taken away, then dumb and silent we may be led, like sheep to the slaughter.’
imho george washington just gave you a high five – mealy
respect for saying the truth
Someone sure didn’t stay at a Holiday Inn Express…
The Guardian has endless stories on this scammy business: A few examples:
https://www.theguardian.com/money/2023/nov/21/more-bookingcom-customers-come-forward-about-scam-confirmation-emails
https://www.theguardian.com/australia-news/2024/jan/31/bookingcom-scams-surge-australia-accc
Small hotels are also victims of their business practices:
https://www.theguardian.com/business/2023/oct/01/booking-com-hotel-fees-unpaid-millions-technical-issue
https://www.theguardian.com/business/2023/oct/03/bookingcom-makes-a-fortune-so-why-is-it-leaving-its-bills-to-small-hotels-unpaid
same here – I got such a message after booking a Hotel in Bruges (Belgium) through booking.com. As the procedure “security verification” seemed new and unusual to me, I emailed the hotel **directly through the address posted on their website, not through the booking.com interface** and they confirmed my suspicion that this was not their doing, but that they had experienced a hack earlier. After this I ignored the matter. I figured if it was legit, there would be follow-up messages with higher urgency, which never arrived.
I also second the suggestion to book with the hotel directly where, and whenever possible.
booking.com is a big ripoff
Precisely zero native English speakers start sentences with the word “kindly.” Immediate red flag.
Right? Dear Sir, kindly enter your details to prevent da froud.
Another reason to not use booking.com is they give your full, unencrypted card details to the partner hotel. Other travel sites, I’m told, give a virtual card number. Not booking.com. Your full card info is shared.
Just noticed an odd sentence in the 2nd paragraph. “whose close friend received a targeted phishing message within the Booking mobile app just minutes after making a reservation at a California.” Should that say California hotel?
We book online but go directly to the hotels website. Sham on the fool that uses 3rd-4th or 5th party sites trusting internet. lol
The biggest problem is i have gotten quite a few legit links in emails but between tiny links and them also using different domains for stuff. Its impossible for a normal person to sort out what is a scam and what is just poor link setup.
CloudFlare reports the web host for the phishing site as “Karina Rashkovska” associated with Ukr[.]net.
More great work from Ukraine.
Gotta take issue with your analysis there, Lime. It appears that name is the contact name for an autonomous system that says it is in Ukraine. But both of its main IP ranges appear to be based in Russia. This is from spur.us:
“as”: {
“number”: 215789,
“organization”: “Karina Rashkovska”
},
“infrastructure”: “DATACENTER”,
“ip”: “147.45.47.0”,
“location”: {
“country”: “RU”
},
“organization”: “Karina Rashkovska”
}
—
{
“as”: {
“number”: 215789,
“organization”: “Karina Rashkovska”
},
“infrastructure”: “DATACENTER”,
“ip”: “147.45.44.0”,
“location”: {
“country”: “RU”
},
“organization”: “Karina Rashkovska”
}
BTW it’s incredibly common for RU threat actors to use resources in Ukraine to make it look like they’re based in Ukraine. The other thing to keep in mind is that large portions of Ukraine are now effectively Russian-controlled.
Just had the same happen to me with a hotel in Japan, the scam domain was registered yesterday (winginternationaltokyo[.]com)!
A friend had the same issue with a hotel in Thailand. Booking.com are responsible for the chat in their own app, they can just disable links to begin with…