Not long ago, there were only a handful of serious so-called “exploit packs,” crimeware packages that make it easy for hackers to booby-trap Web sites with code that installs malicious software.
These days, however, it seems like we’re hearing about a new custom exploit kit every week. Part of the reason for this may be that more enterprising hackers are seeing the moneymaking potential of these offerings, which range from a few hundred dollars per kit to upwards of $10,000 per installation — depending on the features and plugins requested.
Take, for example, the iPack crimeware kit, an exploit pack that starts at around $500.
Its name and cute logo aside, iPack has nothing to do with Apple’s products. According to Jorge Mieres over at the Malware Intelligence blog, the software vulnerabilities targeted by exploits contained in this package are all for Windows platforms, including:
MDAC (CVE-2006-0003) – (MS06-014)
PDF collab.getIcon (CVE-2009-0927)
PDF Util.Printf (CVE-2008-2992)
PDF collab.collectEmailInfo (CVE-2008-0655)
PDF Doc.media.newPlayer (CVE-2009-4324)
Related Posts:




loved the details in those screenshots, are they real or are they a fudged-up demo version? Can’t trust any vendors about demo sw!
Thanks for the info, Brian. One suggestion: With regards to PDF, it would have been less alarming if you said Adobe, because I don’t use Adobe as my pdf reader. Given just the word pdf, raises fear that one is still vulnerable even if they’re not using Adobe.
I would guess that the exploit names come from the exploit pack itself, same as for Eleonore. But Brian only copied them over from Jorge Mieres’ post.
There’s no really good way to name them. Technically you could call them “Adobe Reader and/or Adobe Acrobat exploits”, but I seriously doubt humans will abandon the much shorter “PDF exploit” for that mess.
In this case, it is an actual PDF exploit – the issue is with the specification that allows execution.
Other than a popup that warns you “hey, this PDF wants to run this file”, the code will run and bad things can happen.
With Foxit (until a very recent fix) the exploit would run without even the popup to warn you – The issue is with the PDF specification, not with a program bug.
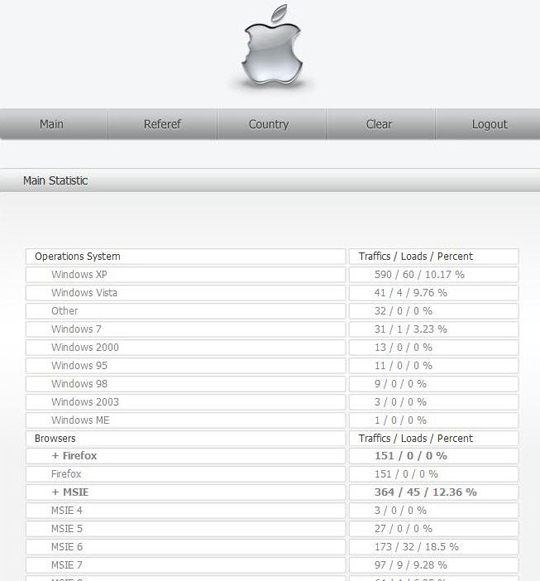
The original screenshot also shows the details for Opera. And once again we see Opera’s infection rate comparable to Internet Explorer (lower than IE6 but higher than IE7 and IE8) while the infection rate for Firefox is zero. With Eleonore I was betting on a programming bug in the exploit kit but with a second exploit pack showing exactly the same behavior this gets unlikely. But still, an infection rate of zero (not a single infection with iPack and only four infections with Eleonore which are all attributed to extremely outdated Firefox versions) pretty much excludes any factors based on user behavior. I am puzzled…
Wladimir,
Since Opera is my primary browser, I also noticed the disproportionate level of traffic and successful loads affecting it. Given Opera’s minuscule worldwide market share, this data just doesn’t make sense. In fact, it really makes me question the validity of the entire data set. Per these stats, Opera’s “traffic” was more than that Firefox and almost half that of MSIE (all versions), yet Net Applications’ April browser market share data shows that Opera currently has barely 2% worldwide penetration.
Tom — If you’re referring to the larger image at Jorge’s site, I can’t speak to the validity of those numbers. But you’ll see from that image that of 177 times an Opera user hit the exploit pack, 17 times it actually found a vulnerability to exploit. That’s about 10 percent of the time. Not terribly hard to believe, given that Opera does not contain anything close to an auto-update feature. My guess is a large percentage of Opera users surf with older insecure versions (in fact, studies have suggested this is the case with Opera more than any other major browser).
Jorge’s list of exploits doesn’t include mention of an Opera-specific exploit, although the PDF reader plugins et. al can certainly be an effective infection vector with Opera as well. I mention it only because when I wrote about the Eleonore kit that Wladimir was referencing above, I later learned that the version of the kit I was looking at indeed included an Opera-specific vulnerability (I think it was a telnet flaw)
Brian – Sorry for breaking the thread with my previous comment.
However, in regards to your comment about Opera not having an auto-updater, they actually added a very good one back in September with the release of Opera 10.
http://help.opera.com/Windows/10.52/en/autoupdate.html
But that does not really help people who are stuck with Opera 9, since they might not even know about Opera 10.
Brian – Thanks for the response. (And yes, I am referring to the larger image at Jorge’s site.)
That said, I’m in no way questioning the load percentage or the ability of iPack to find and target vulnerabilities in Opera. What perplexes me, however, is the wildly disproportionate traffic numbers associated with Opera. As I stated above, Opera’s worldwide market-share is barely 2%. Firefox is roughly 25% and MSIE just above 60%. So why on earth does this sample reflect traffic numbers for Opera that are greater than that of Firefox and just under 50% of that MSIE?
This specific sample provides traffic numbers that are clearly not representative of real world browser use; therefore, I find it difficult to assess the validity of its overall findings.
Tom, for the Eleonore exploit kit I noticed that the data was mostly referring to Russian and Ukrainian users – which explains the large number of Opera users, Opera is pretty popular over there (easily more popular than Firefox for some user groups). So while I’m not sure where this data sample comes from, it might get its traffic from malicious Russian websites again. The browser usage stats make sense then.
All PDF readers should have JavaScript turned off.
Using Firefox, as default browser, with “NoScript” add-on further diminishes the threat of these types of exploits.