 Oracle Corp. has shipped a new version of its Java software that nixes a feature in Java that hackers have been using to foist malicious software.
Oracle Corp. has shipped a new version of its Java software that nixes a feature in Java that hackers have been using to foist malicious software.
Java 6 Update 20 was released sometime in the last 24 hours, and includes some security fixes, although Oracle’s documentation on that front is somewhat opaque. Most significantly, the update removes a feature that hackers have started using to install malware.
On Wednesday, a popular song lyrics Web site was compromised and seeded with code that leverages this Java feature to plant malicious software.
If you need Java for some specific reason, then by all means install this update. However, I have found that most users can happily do without this powerful and feature-rich program, which is fast becoming a popular vehicle for launching a range of attacks. More on that in a future post. Stay tuned.
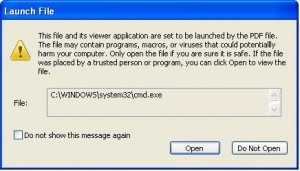 In other news about features in widely installed programs being used as a vehicle to load malware, security experts at M86 Security have spotted a spam campaign aimed at spreading the ZeuS Trojan that exploits a recently-documented feature in at least two different PDF readers. That feature, known as “launch action,” is intended to be used to run an application or to print a document, but recently it was discovered that this feature could be abused to run malicious programs within PDF files.
In other news about features in widely installed programs being used as a vehicle to load malware, security experts at M86 Security have spotted a spam campaign aimed at spreading the ZeuS Trojan that exploits a recently-documented feature in at least two different PDF readers. That feature, known as “launch action,” is intended to be used to run an application or to print a document, but recently it was discovered that this feature could be abused to run malicious programs within PDF files.
Both Foxit Reader and Adobe Reader now warn users if a PDF file tries to invoke this launch action feature, and the alert box will look similar to the one pictured above. If you use these applications and happen to see one of these alerts, it’s probably a good idea to decline launching the file in question.




Thank you, Brian. Took less than a minute to install.
Need it for NYTimes crosswords and California legal stuff.
I tried to install the Java update. Norton told me not to do it and that they are testing it before they give the OK to install. I am holding off.
One thing that might help Adobe and Oracle both in getting these updates pushed out in a more timely fashion – stop using tsr style updaters. Which many “optomizers” both live and software tend to turn off to give you more performance. Why not leverage the functionality of the task schedulers that are available in just about every modern OS?
I currently have Java Version 6 Update 18 installed.
If I enter [Update Now] in the Java Control Panel, it tells me “You already have the latest Java Platform on this system”.
It said the same thing when I tried to install Update 19.
I am using Vista x64 and IE8.
Just go to java.com and get the offline file. Here’s a direct link to the windows executable:
http://javadl.sun.com/webapps/download/AutoDL?BundleId=39494
The download section is located here:
http://www.java.com/en/download/manual.jsp
Same for me – Win7 Ult x64. For some reason java is not wanting to update 64 bit windows.
I hope they fix this because the harder you make it to upgrade, the less amount of people will do it. ( err, I *am* a native speaker, I think )
Bill
In IE8, Security Settings – Internet Zone, should I change Scripting of Java Applets from Enable to Prompt?
Just installed Java 6 update 20. Apparently Norton has lifted the hold.
Does the Java autoupdater still have unwanted, unneeded fluff pre-checked when it installs the latest JRE ? In the past, java updates use to contain a 30 day trial for Carbonite, amongst other pre-checked “fluff”. Since I no longer will allow JREs to be installed on my systems, I don’t know if Oracle has changed Sun’s past practice of opting people into unwanted, unneeded software .
Yes, they had Y! toolbar pre-checked on mine.
Don’t just blindly click-through the dialogs.
Thanks Brian.
I just ran Secunia’s online software inspector (on the “detect only insecure programs” setting–for some reason it took nearly 18 minutes?!). I am running Java 6 update 19, but the scan still shows that as “secure.” Secunia appears to be behind the curve at this writing.
Sun had a history of abysmal documentation of its Java security updates. Oracle seems to have made things even worse.
Looks like Apple is catching up and has released their Apple branded update for these Oracle Sun Java vulnerabilities. http://support.apple.com/kb/HT4171 . This time it didn’t take 6 months.