I have long urged readers who have no need for Java to remove the program, because failing to keep this software updated with the latest security patches exposes users to dangerous, ubiquitous attacks. In this blog post, I’ll show readers how attacks against Java vulnerabilities have fast emerged as the top moneymaker for authors of the best-selling “exploit kits,” commercial crimeware designed to be stitched into hacked or malicious sites and exploit a variety of Web-browser vulnerabilities.
Take one look at the newest kit on the block — “Blackhole” — and it is obvious that Java vulnerabilities continue to give attackers the most mileage and profit, and have surpassed Adobe flaws as the most successful exploit vehicles.
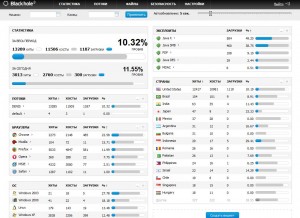 I spoke briefly via instant message with the developer of this Blackhole kit (pictured at right), and he assured me that these images were taken from a working installation. The screen shot here shows the administration panel for this exploit pack, which lists the number of hits (хиты) and downloads (загрузки). The statistics show that on average this kit finds a working exploit that it can use to install malicious software on a visiting host about 10 percent of the time.
I spoke briefly via instant message with the developer of this Blackhole kit (pictured at right), and he assured me that these images were taken from a working installation. The screen shot here shows the administration panel for this exploit pack, which lists the number of hits (хиты) and downloads (загрузки). The statistics show that on average this kit finds a working exploit that it can use to install malicious software on a visiting host about 10 percent of the time.
Granted, as exploit pack administration pages go, this one is very young (13,289 hits at the time this screen shot was taken), but already some patterns emerge from the data. For example, we can see that Java vulnerabilities are by far the most useful, comprising more than 90 percent of all successful exploits.
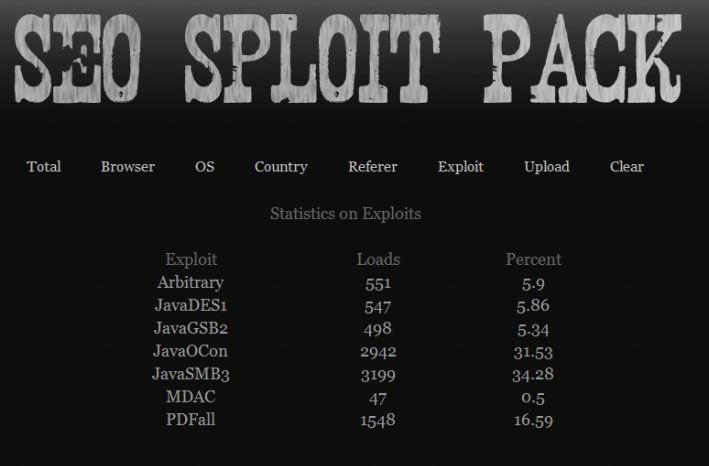
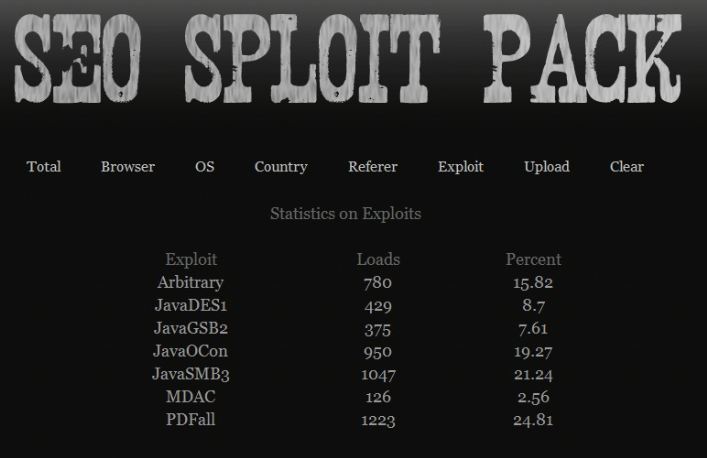
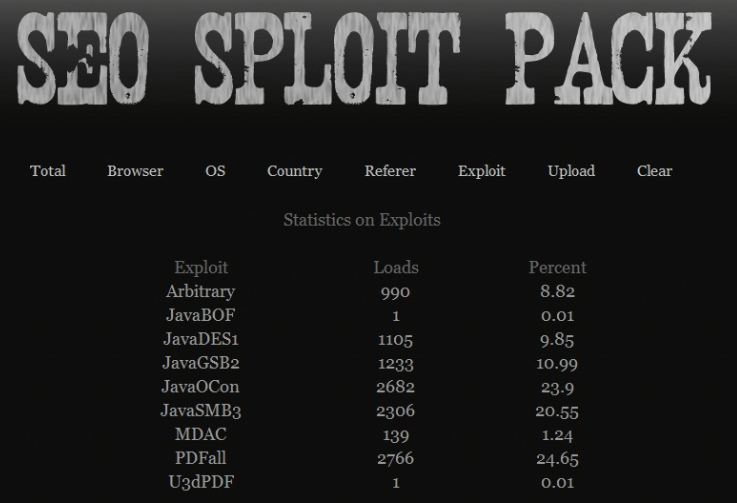
This pattern is not confined to Blackhole. Have a look at the following three screen shots, taken from the exploit results pages of three different working installations of SEO Sploit Pack, another common exploit kit. All three screen shots clearly show Java vulnerabilities are the most productive, accounting for between 50 and 65 percent of malware installs or “loads” (thanks to Malwaredomainlist.com for help on this).
For those who have not been following along, I also found Java flaws to be the leading exploit vectors for both the Crimepack and Eleonore exploit packs.
I believe that there are two reasons for this pattern: First, Java’s maker, Sun — now part of Oracle Corp. — for too long considered itself an enterprise software company, and chose to ignore that its software also is installed on something like 85 percent of the desktop computers on the planet (and 75 percent of Krebsonsecurity.com readers, according to Google Analytics). Also, it seems that many consumers simply aren’t aware that they have this software installed, or that it needs fairly frequent updating.
Adobe has taken some lumps over the past year for the number of critical vulnerabilities that hackers have found and exploited in its software. But for some reason, Java seems to get a pass from the tech and security press, even though Java flaws consistently are found to be the most useful for attackers who wield these automated exploit kits.
If you don’t use Java, consider removing it. You can always reinstall it later if you find you need it. If you do use Java, then please keep it up to date. Java ships with a built-in updater that by default checks for updates on the 14th day of every month. However, this may not be frequent enough to keep users caught up with the latest version. The program can also be set to check for updates every day or every week, although I have found Java’s updater often fails to detect when a new version is available. Alternatively, programs like FileHippo’s Update Checker and Secunia’s Personal Software Inspector can help users stay up to date on the latest security patches.
Update, Oct. 12, 6:19 p.m. ET: Oracle just released an update — Java 6 Update 22 — that fixes 29 security flaws in the most recent version of Java.




If you want 16 reasons why Java should *not* be used check http://multisingular.wordpress.com/2010/09/09/why-i-hate-java .
After finding at least 23 different varients of Java Exploits on my Windows 7 computer. I am questioning why this has not been addressed more in the media. We focussed so much on Flash but it does seem that Java is just a severe of a problem if not worse. Even though I run and update my Anti Virus program on a regualr intervals. I was surprised to find so many exploits made it past detection and never was discovered until a Full computer scan was done. Obviously even Anti Malware companies seem to be ignoring to some extent the sevarity of the Java issues.
Is there some way to disable Java from being accessible through the browser, for people who need it for programming, but don’t care to run java stuff coming from the web?
Either during installation, you untick something or disable java plugin in Firefox. Not sure if this will disable javascript too.
You should be running NO-SCRIPT for firefox. This will prevent the majority of these attacks.