Leading malware developers within the cyber crime community have conspired to terminate development of the infamous ZeuS banking Trojan and to merge its code base with that of the up-and-coming SpyEye Trojan, new evidence suggests. The move appears to be aimed at building a superior e-banking threat whose sale is restricted to a more exclusive and well-heeled breed of cyber crook.
Underground forums are abuzz with rumors that the ZeuS author — a Russian hacker variously known by the monikers “Slavik” and “Monstr” — is no longer planning to maintain the original commercial crimeware kit.
According to numerous hacker forums, the source code for ZeuS recently was transferred to the developer of the SpyEye Trojan, a rival malware maker who drew attention to himself by dubbing his creation the “ZeuS Killer.” The upstart banking Trojan author constantly claimed that his bot creation kit bested ZeuS in functionality and form (SpyEye made headlines this year when investigators discovered it automatically searched for and removed ZeuS from infected PCs before installing itself).
In an era when it has become a truism to say that malicious hackers seek riches over renown, the SpyEye author — a coder known as either “Harderman” and “Gribodemon” on different forums — appears to have sought both, boasting on numerous forums about the greatness of his malware, using flashy logos to promote it (see below), and granting an interview with security researchers about the riches it will bring him. Although the ZeuS author chose to license his botnet creation kit to private groups through multiple intermediaries, the SpyEye creator has peddled his kit directly to buyers via online forums and instant messages.
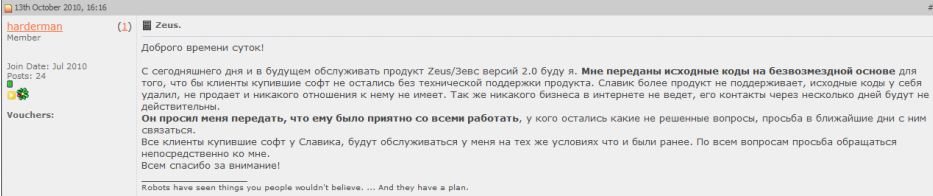
But — very recently — the public rivalry died down, and forum members on different sites where Harderman maintained a presence began complaining that they could no longer reach him for support issues. In an Oct. 11 message to one of the UnderWeb’s most exclusive hacker forums, Harderman can be seen breaking the news to fellow forum members. A screen shot of that message is below, followed by a translated version of it:
Good day!
I will service the Zeus product beginning today and from here on. I have been given the source codes free of charge so that clients who bought the software are not left without tech support. Slavik doesn’t support the product anymore, he removed the source code from his [computer], he doesn’t sell [it], and has no relationship to it. He also doesn’t conduct any business on the Internet and in a few days his contact [information] will not be active.
He asked me to pass on that he was happy to work with everyone. If you have any unresolved issues remaining [there is a] request to get in touch with him as soon as possible.
All clients who bought the software from Slavik will be serviced from me on the same conditions as previously. [I] request that [you] come directly to me regarding all issues.
Thanks to everyone for [your] attention!
In another conversation, Harderman says existing ZeuS clients will get a 30 percent discount on SpyEye, and that the two malware families will soon be “merged into one powerful Trojan.”
 At the same time, Harderman has been busy changing his nicknames and contact information, and asking various online crime forum administrators to remove many of his previous posts about SpyEye, such as the deletions seen in the screen shots to right and below, taken from two different hacker forums.
At the same time, Harderman has been busy changing his nicknames and contact information, and asking various online crime forum administrators to remove many of his previous posts about SpyEye, such as the deletions seen in the screen shots to right and below, taken from two different hacker forums.
 Experts say all this commotion about ZeuS is natural and unsurprising, and that even criminal economies have market corrections — usually aimed at distancing the herd from threats that manage to make front page headlines. The planned assimilation of ZeuS coincides with a massive international law enforcement push to arrest a number of individuals responsible for using Zeus in hundreds of high-dollar e-banking heists from U.S. and U.K. businesses. The FBI says the password-stealing ZeuS Trojan played a central role in enabling the theft of more than $70 million from nearly 400 organizations in the United States over the last several years.
Experts say all this commotion about ZeuS is natural and unsurprising, and that even criminal economies have market corrections — usually aimed at distancing the herd from threats that manage to make front page headlines. The planned assimilation of ZeuS coincides with a massive international law enforcement push to arrest a number of individuals responsible for using Zeus in hundreds of high-dollar e-banking heists from U.S. and U.K. businesses. The FBI says the password-stealing ZeuS Trojan played a central role in enabling the theft of more than $70 million from nearly 400 organizations in the United States over the last several years.
Steve Santorelli, director of global outreach for Team Cymru, an organization that monitors underground economy activity, said his group has been predicting this change for months now.
“Each time you have a group or piece of malware that starts to get near the level of heat or public attention that ZeuS has gotten over the past year, it’s inevitable that the bad guys are going to transition to something that’s not on everyone’s radar,” Santorelli said.
Security firm Trusteer has warned that the recent industry focus on Zeus is making it easier for other Trojans, like Bugat, SpyEye, and Carberp which are less wide spread but equally sophisticated, to avoid detection.
“We are in an arms race with criminals,” said Trusteer CEO Mickey Boodaei. “Although Zeus gets a lot of attention from law enforcement, banks and the security industry, we need to be vigilant against new forms of financial malware like Bugat and SpyEye which are just as deadly and quietly expanding their footprint across the internet.”
In response to urging from other members on the exclusive forum who apparently want fewer hackers to be able to afford the kit, Harderman acknowledges that he may have to dramatically increase — perhaps even double — the price of SpyEye, to several thousand dollars per license.
In exchange, the malware developer says he will overhaul the kit to include the best of both ZeuS and SpyEye. Specifically, Harderman says he wants to turn the guts of the Trojan into a rootkit, and to build additional functionality on top, in the form of modular plug-ins. “We have a bunch of work on the way!” he promises in one online posting.
Interested buyers can probably expect the amalgamated software to contain some undocumented features. One of the more fascinating threads that survived the recent Harderman posting purge on the web forums comes from the Russian language board “DamageLab.org”, which chronicles an incident earlier this year in which fellow hackers managed to “crack” the technology the author uses to prevent SpyEye buyers from making unauthorized copies of the software.
Using the handle Gribodemon here, the software developer scoffed, saying he had secretly built in a backdoor that would allow him to seize remote control over PCs infected with his bot. “Ah, yes. I forgot to mention that in the ‘leaked’ version there is still a backdoor which I have now activated,” Gribodemon wrote. “Thank you, rogue, for the completion of my botnet.”




It would not be the first time the author has claimed to get out of the game:
http://www.securelist.com/en/images/vlpub/1107_q3_threats_pict6.png
It’s just a technique they use repeatedly in trying throw people off their trail. We’ve seen it with Nuclear Grabber, Pinch, Hupigon, and others.
I’ve always wondered what ever happened to the Apple, C64, Amiga large scale organized groups that made ROMS, cracked and distributed the software throughout the 70’s, 80’s .. and so on.
I remember many wares BBSs carried news of merges, disbandments & retirements and such.
I wonder if there is a similar trajectory for today’s criminal software, ASM and ROM coders.
I wouldn’t be so much concerned about the merger – the two trojans are probably already similar enough that technically there is little to be gained from it. For the ZeuS author this simply seems to be a way of getting out of support obligations as well as getting rid of undesired publicity. The SpyEye author welcomed this opportunity of course, he was aiming for the ZeuS market share from the very start. Very soon he will also discover that supporting a larger user base takes time away from development and hinders SpyEye progress.
However, I agree with Don – it is too early to write off the ZeuS author. He will change his names and contact addresses and start something new. And he will try to make it as stealthy as possible to fly under the radar. Unfortunately, he should have enough experience to pull this off.
I doubt the author is retiring from criminal activity, but may be retiring from involvement with ZeuS.
I doubt that ZeuS has the same ROI that it had in the first quarter of this year. If you compare the number of domains registered for the ZeuS-Avalanche botnet in february of this year with the domains registered in the 2nd and 3rd quarters there is a significant drop, not only in the number of domains registered but in the number of registrars used. Whether the new merger and technology will be more successful remains to be seen.
There appears to be a much higher ROI in the fake pharmacy exploits and I have noticed a large increase in the number of domains being registered and emails reported for the fake pharmacies since the decrease in ZeuS botnet activity. This area should be more profitable for the criminals as the general public appears to be against any effort to regulate it. What would not be tolerated in the brick and mortar world is protected on the internet with the bumper-sticker mentality of “invasion of privacy” and the tired warning of “not being able to put the genie back in the bottle” (a variation on the domino theory).
On the internet, you can sell any product without even having to disclose who you are. And no browser is going to warn you about it.
Krebs now you are banned on maza )) Looser
Ohnoes!
Brian, mess with the best, be defrauded like the rest. Mac won’t help.
Krebs I got yo back 🙂
How’d you know I was using a Mac??
Ohnoes!
They can’t be too concerned about attracting attention from law enforcement if they’ve registered barakobrama.com as a command and control center. See https://zeustracker.abuse.ch/monitor.php
zeustracker.abuse.ch uses an invalid security certificate.
The certificate is not trusted because it is self-signed.
(Error code: sec_error_untrusted_issuer)
How exactly do we know that old Slavik hasn’t been capped? I keep bringing this up – there’s so much money in this “trade” that it’s not unconscionable for events to turn in the direction they’ve gone in Mexico around drug profits (and routes – the analog of which would be the malware code base).
Something’s fishy here.
– mkh
“How exactly do we know that old Slavik hasn’t been capped? ”
We don’t 🙂
I’m mildly bemused by the Spy Eye advertising banner which Brian reproduced in the article: “Hack the Planet! Take YOUR money!”. I was under the impression a would-be criminal buying and running this kit would be more enticed to take OTHER PEOPLE MONIES.
Well it’s all about money , probably SpyEye Author don’t have many sales like Zeus , and Zeus Author is not available in such of forums where Harderman is on , so Harderman post that he merged SpyEye with Zeus to get more sale in future , and increase the price for SpyEye .
( JUST THINK Slavik IS NOT CRAZY TO GIVE HIS LIFE PROJECT TO HIS SALE ENEMY FOR FREE )
unless if they are the same person
Informaton o zeus zdes
http://bratva.name/forum/showthread.php?t=603
Which is the current address of Maza.la? I’ve got the :777 but it changed for sure
You’re not even going to be able to see that site without a special browser certificate installed.
Could you give me it? I can provide information from there.
I have a copy of the cert from when it was at 777 but I don’t know where it moved to. If Brian is willing to share then that would make me happy. 🙂
Could someone explain how maza works with the cerrtificate system and the http port changed.
This could be a good blog entry
….
Relax, Mr. pleasedontruinanymoreOSINT@noobs.com (yeah, I know who you are). Nobody’s going to publish that on this site, least of all me.
That’s just looking for trouble Brian , he should play in some other person sand box.
https://mfsoft.info:555 )) new domain of maza.la
Krebs your blog comes more and more popular. You will need to integrate captcha here or you will get spammed by these bad bad russians.
As you can see here http://www.youtube.com/watch?v=YEG_JXsyvG0&NR=1
the correct model of russian scamer and americans.
I like this movie 🙂
Zeus botnet model:
http://www.youtube.com/watch?v=vHfzvwTKkCs
have you considered the possibility that Hardeman and Gribodemon are different fronts for a single person/organisation?
well, yes. i say that in the story above:
“the SpyEye author — a coder known as either “Harderman” and “Gribodemon” on different forums…”
Brain can you tell me how to get in this forum maza do i need vouchs or i need to pay or what to get that Cert and port + if you got contacts for admin or support that let ppl in can u provide or send me your icq or add me at icq to tell me if u dont like to share here any help would be appericated thanks 😉
The SpyEye/Zeus merger is beginning to adopt many capabilities of The Perfect Virus, 22 components of which I’ve identified over the past year.
heard on the forum’s for your head announced award, don’t u afraid?
heard on which forum? care to post what you’re talking about? thanks.
Maza example, how did u get access? Maybe some member help u, couse there are only russian speaking people. Who’s the traitor ? Tell us please
Maybe continue talking in Jabber? i have some interesting question’s.
Possibly. I dont’ currently have access to Maza. Are you saying that’s where this threat you speak of was uttered? Or was it someplace else?
It was there. Waiting u’r jabber or icq.
My english is bad, but if u’re interested u’ll understand me. For example ask me something knew only maza member’s.