Criminals have been conducting complex, targeted e-mail attacks against employees at more than 100 e-mail service providers (ESPs) over the past several months in a bid to hijack computers at companies that market directly to customers of some of the world’s largest corporations, anti-spam experts warn.
The attacks are a textbook example of how organized thieves can abuse trust relationships between companies to access important resources that are then recycled in future attacks. According to multiple sources, the so-called “spear phishing” attacks in this fraud campaign arrived as virus-laden e-mails addressing ESP employees by name, and many cases included the name of the ESP in the body of the message.
The poisoned missives used a variety of ruses, but generally included an invitation to view images at a Web site URL included in the message — such as a link to wedding photos or an online greeting card. Recipients who clicked the links were redirected to sites that attempted to silently install software designed to steal passwords and give attackers remote control over infected systems.
 Neil Schwartzman, senior director of security strategy at e-mail security provider Return Path Inc, said the spear-phishing attacks have targeted e-mail marketing companies that manage opt-in campaigns for some of the biggest corporate brands in existence.
Neil Schwartzman, senior director of security strategy at e-mail security provider Return Path Inc, said the spear-phishing attacks have targeted e-mail marketing companies that manage opt-in campaigns for some of the biggest corporate brands in existence.
“This is an organized, deliberate, and destructive attack clearly intent on gaining access to industry-grade email deployment systems,” Schwartzman said. “Further, the potential consequences should ESP client mailing lists be compromised at this time of the year is unimaginable.”
Update: Nov. 25, 12:33 p.m. ET: Return Path is now saying that it also was compromised and that its clients are reporting that they have received spear-phishing attacks over the last 24 hours. Read on past the jump for more on this update.
Original post:
Chris Nelson, a security manager at an ESP that was compromised by these attacks, spoke with KrebsOnSecurity.com on condition that his employer not be named. Nelson said he traced the attack used to infiltrate his company’s servers back to Internet addresses in the Netherlands, where he found evidence that at least a dozen other ESPs were similarly compromised. The attacks, he said, appear aimed at gaining control over customer accounts and e-mail address lists that could be used in future spam and scam campaigns.
All of the evidence suggests these attacks have been going on for several months, Nelson said.
“Back in April of this year, we started seeing some delivery results that were way off for accounts that we had,” he said. “For instance, a small church in [the South] that had maybe a couple of hundred members on their list all of a sudden e-mailing 500,000 to 1,000,000 people.”
 Nelson said he believes that the attackers leveraged a vulnerability in one of his employer’s internal software applications that allowed “account hopping” and access to his employer’s client database.
Nelson said he believes that the attackers leveraged a vulnerability in one of his employer’s internal software applications that allowed “account hopping” and access to his employer’s client database.
“It took us until September to get the full visibility into what [and] how this was being done,” he said. “What we pieced together was a compromise through our image uploading [feature]…a .jpg file with malicious code in it.”
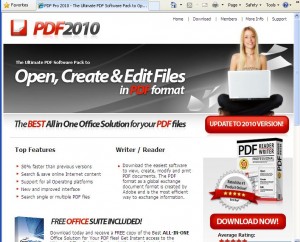
According to Nelson, the spam missives sent to customers of his company’s clients were identical to the spam campaign detailed this week in a writeup by Lenny Zeltser, an incident handler with the SANS Internet Storm Center. Those messages urge recipients to download or upgrade “Adobe Acrobat and Reader 2010” from a variety of Web sites (see image above). Zeltser said Adobe has confirmed that the messages are part of a campaign that began in September.
“The sites advertised as part of the spam campaign attempt to convince the person to provide his or her credit number to obtain PDF reader/writer software using a form that’s hosted on secureonline.ru,” Zeltser wrote. “We haven’t checked whether the software is actually malicious, but we’re doubtful of its intentions.”
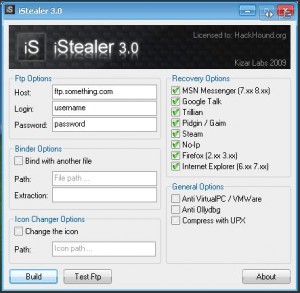 According to Return Path’s Schwartzman, the software foisted by the malicious images in the spear-phishing e-mails installed a commercial password-stealing program called iStealer (shown on the left). I grabbed a copy of the program from one of the malicious links included in a phish sent to one of the victims, and scanned the file at VirusTotal, which scours submitted files using more than three dozen anti-virus products. The result: Only two of the anti-virus products detected it as malicious or even suspicious.
According to Return Path’s Schwartzman, the software foisted by the malicious images in the spear-phishing e-mails installed a commercial password-stealing program called iStealer (shown on the left). I grabbed a copy of the program from one of the malicious links included in a phish sent to one of the victims, and scanned the file at VirusTotal, which scours submitted files using more than three dozen anti-virus products. The result: Only two of the anti-virus products detected it as malicious or even suspicious.
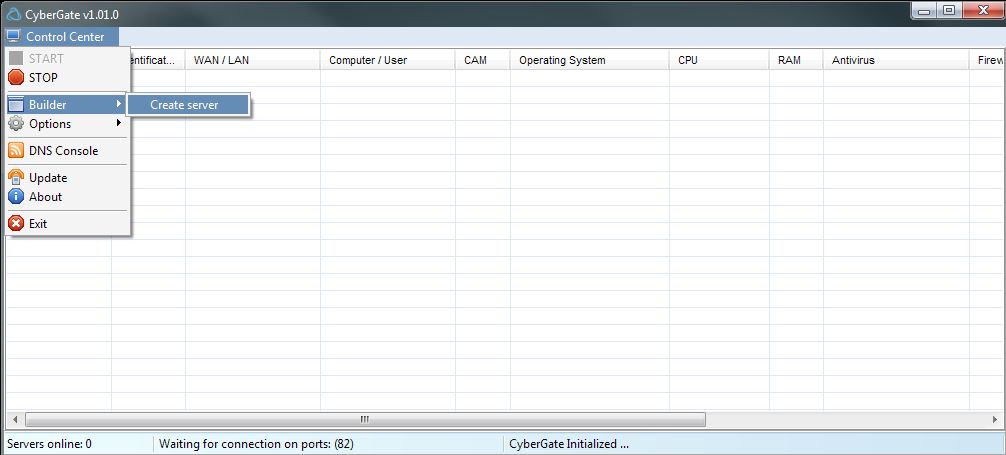
Schwartzman said the iStealer Trojan was accompanied by another commercially available tool — CyberGate (pictured below), a point-and-click remote administration tool that lets the criminals control an infected computer from afar.
Update: In a blog post published today, Return Path said it has received data from its ESP partners and some clients “that make us suspect that some of our data within Return Path may have been compromised as part of this same phishing scheme. Our concern at this point is that a fairly small list of our client email addresses (those used to receive system alerts from us) might have been compromised. Even though this is a small list, it is still a serious issue since many of the addresses on the list themselves have downstream access to larger email lists. As a reminder, Return Path does not warehouse large consumer mailing lists or deploy any client email campaigns directly.”
Interestingly, Schwartzman said the spear phishing campaign that targeted Return Path’s clients spoofed American Greetings and Yahoo brands in the link, but the link itself redirected users to a site hosting e-card malware (the Clean MX writeup on that domain is here).




The “PDF2010” site is a MarketBay affiliate, those affiliates have been hugely active lately with spam runs and other dubious ways of pushing MarketBay’s products.
If you want to research MarketBay, first look at “Three W Networks Ltd” and yourclick.com, the name the company used to be, it now calls itself “Media Entertainment Group” and uses a recently bought domain of marketbay.com. Everything runs offshore in the Bahamas so is a little difficult to trace.
I had cause to look at a MarketBay affiliate a little here: http://blog.dynamoo.com/2010/11/evil-network-mango-ideas-gsidnet.html
If Chris Nelson wants to keep his employer from being named, it might help not to post enough details to find him easily on LinkedIn.
Brian,
Thanks for the great coverage.
To the commenter Mr. Wilkinson: Mr. Nelson’s forthright comments are to be congratulated, not disparaged, in my opinion. I’m pretty certain he was aware of the existence of LinkedIn and Google prior to speaking to Mr. Krebs.
FWIW, comments at Word to the Wise indicate this issue is also affecting mail infrastructure vendors: http://blog.wordtothewise.com/2010/11/esps-being-targeted/
This issue, if messages I have received are to be believed, is very widespread and successful from the adversary’s standpoint (far more than has heretofore been admitted to publicly in terms of actual breaches) and underscores one unavoidable conclusion:
Anti-virus software is worse than useless.
It doesn’t catch 80% of the viruses out there (reports say 33% of all viruses, ever, were written in 2010), running several a/v packages simultaneously is too resource hungry to be practical and the incremental increase in protection likely to be minimal, propagation is ever-increasingly usurping email for drive-by infections in poison search engine results, webpages and social network social engineering. and ultimately:
Anti-virus software gives people a false sense of security, but to not run any is a dumb idea too.
Frankly, I don’t have a positive conclusion or even a notion as to how to fix this issue.
Oh happy days.
—
Neil Schwartzman
Senior Director
Security Strategy, Email Intelligence Group
Receiver Services – Return Path Inc.
Two words: Application Whitelisting.
So long as a system is allowed to arbitrarily run any executable, attempting to isolate “bad” programs simply Will Not Work in the long run (otherwise known as the logical fallacy of “Enumerating Badness”). Instead, identify executable code that is allowed to run on the system (legitimate operating system components and known, trusted applications) and prevent everything else from executing by default.
The only thing stopping Microsoft or Apple from implementing this as a default policy in Windows or OS X is the concern as to who gets to decide what a “legitimate” executable on a system is.
That’s basically what things like firewall software or Noscript do — they make the human user approve each new process before it can execute. But most people in the workplace aren’t terribly concerned if their employer’s computer gets pwned and just click “okay” on everything that pops up without reading it.
Then there’s the folks who want to see the dancing bunnies and will find a way to circumvent any safeguards you install to stop them.
I understand your position, and while it seems application whitelisting is inevitable, remember that ‘locks only keep the honest man, honest’.
“Frankly, I don’t have a positive conclusion or even a notion as to how to fix this issue.”
Move to a more secure operating system and application software.
Anybody else notice both of those malware apps are built using what appears to be XULRunner?
Re: Anti-virus software gives people a false sense of security, but to not run any is a dumb idea too.
Apple don’t include anti-virus on iOS and I wouldn’t call them dumb
“Topic : Antivirus-Software on iPhone (OS 3.x) … which mobile antivirus-software can you suggest to use on iPhone (OS 3.x)? … There are none that are compatible with the iPhone”
http://discussions.apple.com/thread.jspa;jsessionid=E9D424576BAAA5D1F8C81A600BD05943.node0?messageID=11594343�
Search for some of the phrases from the email and you’ll see it’s wide spread, hitting everyone everywhere. I saw no indication that it was focused. The ZIP/exe’s from October were Pilleuz/Mariposa.
Subject: Hi JoAnn
Hi JoAnn , its Ashley here, it was such a long time , how is it going with you there ? I heard that you got a new job, didnt you? Is everything ok there ? Hey, can you believe it! I got married to Mike ! Yes I did. I tried to call but you did not answer. You have changed your number, havent you? Just give me your current telephone number if you read this mail. Its really a pity that we did not see you in our wedding. I wanted to invite you so much. Well, here Im sending you a few pics taken in our wedding :
http://www.[hacked site].com/photos/ashley/
Let’s keep in touch then.
Love,
Ashley & Mike
Clarifying…Chris Nelson with Delivra is not quoted in this article. There is another Chris Nelson in the ESP space. Delivra hasn’t been compromised.
Chris Nelson, Delivra
It looks like Garnet Hill is another example of a email provider data breach victim. Looks like it’s related to Silverpop. Here is the notification:
http://wp.me/pymfm-qV