In October, I showed why Java vulnerabilities continue to be the top moneymaker for purveyors of “exploit kits,” commercial crimeware designed to be stitched into hacked or malicious sites and exploit a variety of Web-browser vulnerabilities. Today, I’ll highlight a few more recent examples of this with brand new exploit kits on the market, and explain why even fully-patched Java installations are fast becoming major enablers of browser-based malware attacks.
Check out the screenshots below, which show the administration page for two up-and-coming exploit packs. The first, from an unusually elaborate exploit kit called “Dragon Pack,” is the author’s own installation, so the percentage of “loads” or successful installations of malware on visitor PCs should be taken with a grain of salt (hat tip to Malwaredomainlist.com). Yet, it is clear that miscreants who purchase this pack will have the most success with Java flaws.
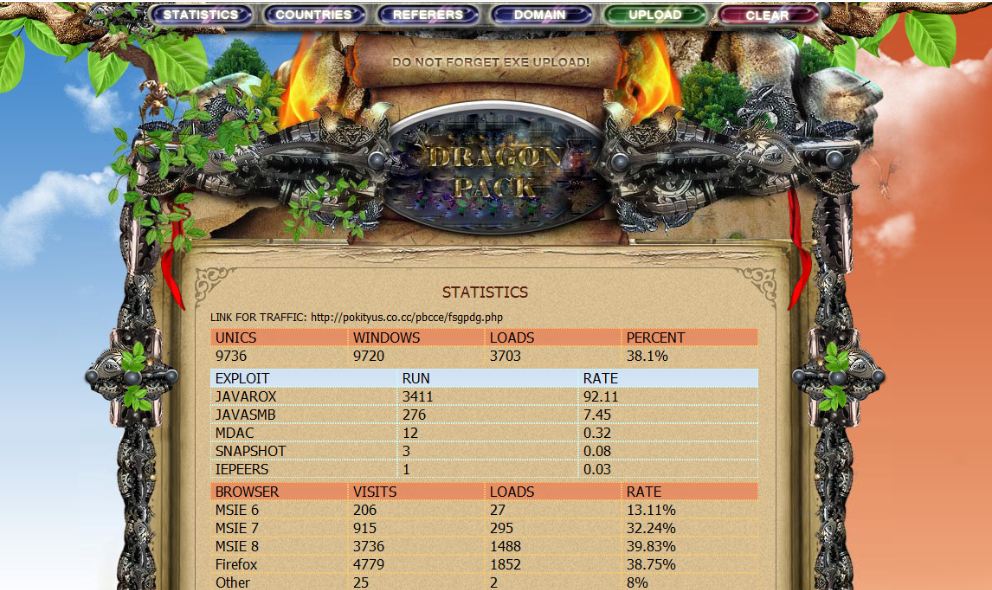
This blog has a nice writeup — and an additional stats page — from a compromised site that last month was redirecting visitors to a page laced with exploits from a Dragon Pack installation.
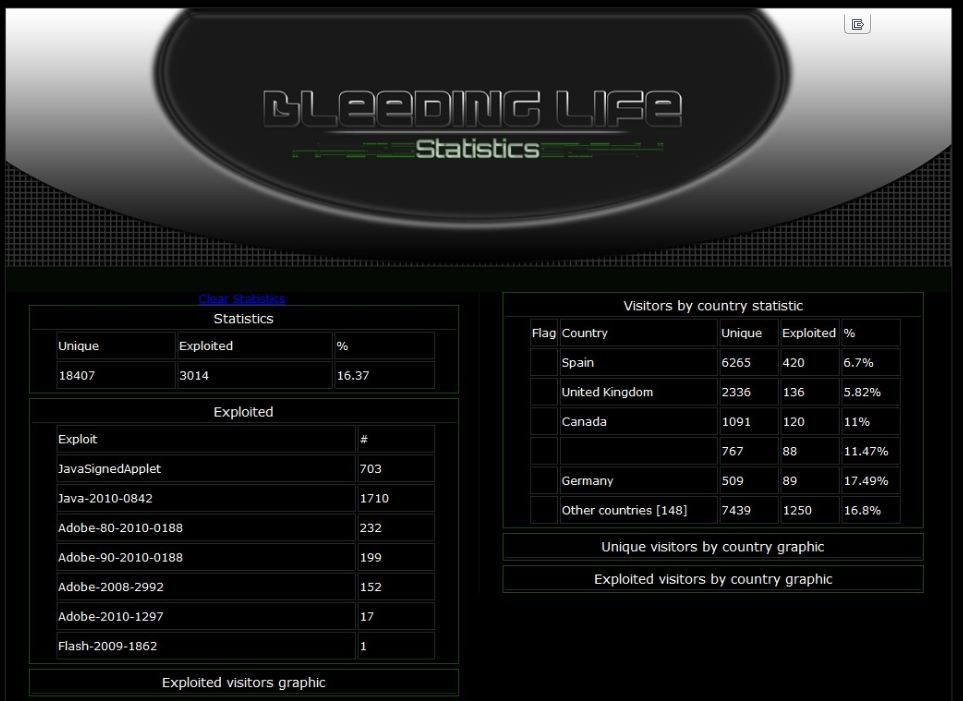
The second image, below, shows an administrative page that is centralizing statistics for several sites hacked with a relatively new $200 kit called “Bleeding Life.” Again, it’s plain that the Java exploits are the most successful. What’s interesting about this kit is that its authors advertise that one of the “exploits” included isn’t really an exploit at all: It’s a social engineering attack. Specifically, the hacked page will simply abuse built-in Java functionality to ask the visitor to run a malicious Java applet.
On Dec. 29, the SANS Internet Storm Center warned about a wave of Java attacks that were apparently using this social engineering approach to great effect. The attacks were taking advantage of built-in Java functionality that will prompt the user to download and run a file, but using an alert from Java (if a Windows user accepts, he or she is not bothered by a separate prompt or warning from the operating system).
 “If you don’t have any zero-days, you can always go back to exploiting the human!” SANS incident handler Daniel Wesemann wrote. “This is independent of the JRE version used – with JRE default settings, even on JRE1.6-23, all the user has to do is click ‘Run’ to get owned. The one small improvement is that the latest JREs show ‘Publisher: (NOT VERIFIED) Java Sun’ in the pop-up, but I guess that users who read past the two exclamation marks will be bound to click ‘Run’ anyway.”
“If you don’t have any zero-days, you can always go back to exploiting the human!” SANS incident handler Daniel Wesemann wrote. “This is independent of the JRE version used – with JRE default settings, even on JRE1.6-23, all the user has to do is click ‘Run’ to get owned. The one small improvement is that the latest JREs show ‘Publisher: (NOT VERIFIED) Java Sun’ in the pop-up, but I guess that users who read past the two exclamation marks will be bound to click ‘Run’ anyway.”
Researchers at Kaspersky Lab also have tracked a sizable uptick in attacks leveraging social engineering via Java. Vyacheslav Zakorzhevsky, a senior malware analyst at the Russian security firm, covered this trend in the company’s December 2010 monthly malware statistics report.
In our November review we wrote about the explosive growth of the Trojan-Downloader.Java.OpenConnection family. These programs act in just the same way as exploits do in the latter stages of a drive-by attack, but instead of using vulnerabilities to download malware to victims’ computers, they employ the OpenConnection method of a URL class.”
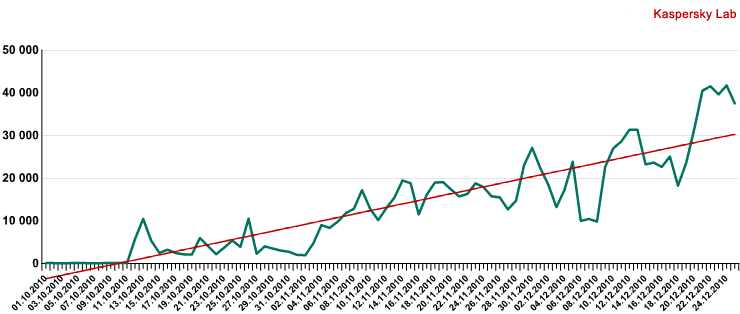
Two representatives of Trojan-Downloader.Java.OpenConnection (2nd and 7th places) were among the Top 20 malicious programs detected on the Internet in December. At the height of their activity the number of computers on which these programs were detected in a 24-hour period exceeded 40,000.”
As we just mentioned, all the representatives of the Trojan-Downloader.Java.OpenConnection family, instead of exploiting vulnerabilities, use standard Java functionality to download and run files from the web. This is currently one of the prime download methods for malicious programs written in Java. It appears that until Oracle closes the functionality this family uses to download files its popularity will continue to grow.
The graphic below shows the number computers that Kaspersky found were infected with Trojan-Downloader.Java.OpenConnection in the last six weeks of 2010.
I’m not advocating mass abandonment of Java, as some readers have charged. But I continue to urge users who have no reason to use this program to get rid of it, particularly on systems that are shared by less careful Web surfers. I have Java installed on a couple of my PCs where a particular software program requires it to run properly, but I have disconnected the Java plugins from the browsers on those systems.
If you’re a Firefox user and a Web site you frequent requires Java, consider installing and using the excellent NoScript extension, which will block Web sites from running Java applets unless you specifically whitelist them.




kasper sux, norton rulez
One of the particular concerns with Java is that the applications I use that require it all produce similar prompts. None of the applications have properly signed components, and so it’s a matter of course to run Java utilitites in the browser which require clicking through a couple of similar warnings. If that is the normal user experience, is it any wonder that they would be ripe for successful social engineering attacks?
In this link that Brian provided:
“Beware of strange web sites bearing gifts …
http://isc.sans.edu/diary.html?storyid=10168
Either or both *.exe and *.bat files attempt to run as part of the exploit. Or, if that fails, through social engineering. The java applet is just a launcher for these executables that do the dirty work.
One can protect against this exploit and social engineering ploy by combining two preventive measures:
1. Create and use a limited or standard user account for your day-to-day PC activities (use the Windows default account only for administering the PC), AND
2. Control executables than run on your PC by enabling Software Restriction Policy whitelisting (for more details, see my posts in Brian’s earlier blog article on the ‘White House’ eCard).
I wonder how much of beating the Sun Microsystems shareholders have taken since Java’s constant security issues keep arising in the media, and the company’s image in the eyes of Tech firms and consumers. While I will give Sun credit for trying to improve their updates, I think they need to look at just how insecure their product has become. I Don’t see how Sun can just keep tweaking their code, I think they need to rip it down and start anew for future releases. It won’t cure the social engineering that will snare some, but to continue to see your name at the top of the eploitable list is going to make them toxic.
Note that Sun was purchased by Oracle (Apr 2009).
http://www.google.com/trends?q=java+exploit only shows graphs for 2010 🙁
http://www.google.com/trends?q=sun+java shows a simple downward trend.
Between SMI’s rename and JAVA’s delisting, it seems that getting useful reports for stock value is pretty much out.
As for Tinker v. Rewrite… It took Netscape’s descendants nearly a decade to recover from the cost of a rewrite. Rewriting is very expensive (in terms of Time to Market).
Sun is now “Oracle America”. Sun started suffering after the Dotcom bubble. Probably one of the reasons Java sucks so much is because what success Sun did get seemed to be all in the hardware space, and so that’s where they invested resources. Maybe things will turn around now they are owned by a larger corporation, but I do not believe that is typically how these stories end.
It is going to take more bad press than Java can manage on its own to make a dent in Oracle stock. I think for all the banner waving for HTML5 as a Flash killer, I’d like to hear someone comment on whether HTML5 will allow me to get Java off my machine forever.
Off topic, but this morning my Gmail account received a request “from Google” to revalidate my ID and password that Gmail failed to recognize as spam.
Ref you comment that you have “disconnected the Java plugins from the browsers on those systems.”, could you post some info on how to do that? Or pointer to same?
In Firefox, go to Tools, Add Ons, Select Plugins, and disable the Java plugin(s). Restart the browser.
The instructions may vary slightly for other browsers, but probably not by much. I’m not in front of a Windows machine, otherwise I’d post the IE instructions as well.
For Firefox, IE, Safari and Chrome:
“Protect Your Computer: Turn Off Java
http://www.help2go.com/content/tutorials/37-protect-your-computer-turn-off-java.html
See “Option #2: Disable Java in your Web Browser”.
Thank you RHM!; you are a credit to Brian’s site, and I’m sure new users everywhere that visit here! 🙂
Java plugins should be disabled by default. Every browser should throw up a “Are you sure you want to run a Java applet?” box when they are embedded. On top of it, the browser should be checking to see if you have the latest version.
I dont expect Firefox and IE to do this, but Chrome’s engineers seem to serious about security (built in pdf reader, flash sandboxing, etc). Maybe they’ll tame the Java beast because Oracle/Sun sure isnt.
Disabling java by default doesn’t necessarily make things better. It more or less encourages sites to offer “install java” links. We already have “install fake codec” links. We don’t need more such things :(.
Note that tossing up dialogs is generally speaking the wrong approach to any problem, it leads users to click “yes, I want to do this”.
If you use Chrome, you may have noticed that when you click a link to download a file, it doesn’t toss up a dialog, instead it sticks an indicator into a tray at the bottom of the window. If you wanted the file, you retrieve it from there, if not, it’s lost eventually. Other browsers use info bars at the top for similar things. The goal of this kind of design is to *avoid* giving the user a dialog where the user will inevitably choose “Yes, please root me”.
Sorry I dont agree. Recently I visited Reddit and one its ad affiliates was hacked and was serving up a malicious java applet. A “are you sure” dialog would have saved a lot of users.
I dislike the “theres nothing we can do, people will click yes anyway” defeatist attitude. No, SOME people will click yes anyway, not all.
Disabling java by default makes a lot of sense, the same way the Flashblock addon makes a lot of sense in Chrome and FF.
As far as the UI goes you can make it work just like Flashblock.
Of course the real solution is to uninstall Java. I cant remember the last time I needed it outside the enterprise space.
Sadly, my bank requires* Java for authentication (it isn’t an American bank, I’m not living in the US, not all of Brian’s readers do). I also happen to use it for a corporate web vpn (this enables me to avoid routing *all* traffic through the VPN / use a 1GB VM w/ VPN for the same purpose).
Brian: I don’t suppose you have any numbers for people doing stupid things like triggering the Melissa virus
and Anna Kournikova ?
The codec problem has been around for years, and we really don’t want to make it worse .
Please note that I’m not saying there’s *nothing* we can do about it. I’m not opposed to FlashClickToPlay or NoScript (I generally use NoScript). The problem with click-to-play is that it’s trivial for a site to trick a user into clicking, and thus that isn’t actually protection, it’s just Security Theater (which is expensive for everyone involved since you learn a new useless pattern, which is immediately defeated by the attackers).
* well, I can use the mobile site if without java, but that doesn’t let me access certain rather basic sections.
It doesnt need to be just a click-through. It could be adding the site to your trusted sites. There are a lot of UI conventions that can be used. I don’t find this “security theater” or “useless patterns.” Ive seen very techphobic people properly use the UAC before, which is exactly what I am suggesting for Java applets.
The problem is that no one really considered security when dealing with browser add-ons like this. These things run with the credentials of the user, they are not sandboxed like IE7/IE8. They greatly increase the attack surface and have led to botnet armies, stolen identities, spam, and other nastiness.
I absolutely cannot agree that not doing anything is the best solution here. The entire system is a mess. Blocking this stuff is the only way to go until we get real browser architecture fixes for this stuff like not allowing them to run unless they are fully sandboxed and not running any Java code via the browser unless its signed. Out of the box security matters. It matters a lot.
I think its pretty obvious that Oracle will never secure this thing. In the meantime I’m happy using Chrome as a non-admin and just leaving the Java plugin disabled. Perhaps your bank should catch up to the 21st century and stop using dangerous technologies. Oh, the irony that a bank is making you use incredibly insecure software to manage your accounts. I feel sorry for you and its customers. Forcing Java on people is more or less a guarantee of a malware infection.
I really want to start seeing the Java backlash begin. People have no problem complaining about Flash and other technologies. Add Java to the shit list because it belongs there.
god save macosx!
Unfortunately, the Secunia Online Software Inspector (OSI)–which I use regularly and find very beneficial–will run only with its Java applets enabled. Disabling Java via Firefox’s (my default browser) options makes running Secunia’s scanner a pain in the a**. Life is full of such trade-offs.
Since you already use Firefox …
“If you’re a Firefox user and a Web site you frequent requires Java, consider installing and using the excellent NoScript extension, which will block Web sites from running Java applets unless you specifically whitelist them.
An excerpt from Brian’s blog.
Maybe someone could consider making the warning pop ups more visually meaningful? We use image icons to symbolize programs because it’s faster to identify the program we’re looking for when we can scan for the pattern and color of the icon we want. While it may look “professional” to have your pop up windows all look consistent, it isn’t helpful for communication. If the reason people click things without reading them is that it’s too time consuming to read the warnings and they’re already perturbed by having an interruption in the middle of trying to load a website, why not color code the warning boxes? The “this information is being sent over an insecure connection” pop up should not be the same size, shape, color and should not have the same border pattern as the one that says, “this website would like to install an executable program on your computer.” Even better, encourage users to choose their own colors (at the bottom of a pop up, give several choices for how it will appear in the future) to frustrate the fake AV programs trying to spoof a Windows pop up.
This is not a new problem, but one that hasn’t seen enough public review thus far so kudos to Krebs here for that! Turrning off Java is not possible for many users however, so there needs to be a better work around. I would suggest a java detector. MS has one called zozzle and nozzle for the server side. But zozzle right now only works for IE I believe. Ergo if your a Firefox or Chrome user you will need something a bit different of your provider will.
Unless I am mistaken, Zozzle, while a promising concept, is still in the research stage and is not available to the public at this time.
Thanks, RHM, for the NoScript tip. I have used this FF add-on for years. I was not aware that, along with a lot of other things, it blocked Java applets, too. Probably because I whitelisted Secunia long ago. If your premise is correct, this should save me the hassle of blocking and unblocking JAVA via the browser controls.
I’m a Windows Administrator in a corporate environment where users do not by default have administrator permission. It definitely cuts down on the number of infections you see at the desktop and keeps malware from spreading its tendrils too far through an affected system. It also tends to be easy to detect the infected executable(s) because they’re running out of the user’s profile rather than a normal location like “C:\Program Files”. Anyone have any experience with a machine infected by one of these exploit kits that goes through Java? What processes or changes do you see on that system that clue you in to the infection? What do you do (apart from disabling Java) to prevent or mitigate the damage?
My advice would be to confine Java installations to non-networked computers only, systems which receive no swapping of Flash drives or other writable medium between them and the networked computers. There are so many nasty java exploits and systems running old versions of Java in the wild, ask yourself if you really need Java installed on a networked machine and why.