A malware-laced e-mail that spoofed seasons greetings from The White House siphoned gigabytes of sensitive documents from dozens of victims over the holidays, including a number of government employees and contractors who work on cybersecurity matters.
The attack appears to be the latest salvo from ZeuS malware gangs whose activities over the past year have blurred the boundaries between online financial crime and espionage, by stealing both financial data and documents from victim machines. This activity is unusual because most criminals using ZeuS are interested in money-making activities – such as swiping passwords and creating botnets – whereas the hoovering up of sensitive government documents is activity typically associated with so-called advanced persistent threat attacks, or those deployed to gather industrial and military intelligence.
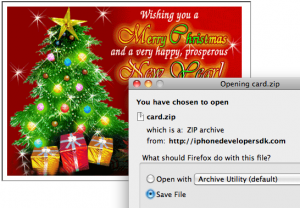 On Dec. 23, the following message was sent to an unknown number of recipients;
On Dec. 23, the following message was sent to an unknown number of recipients;
“As you and your families gather to celebrate the holidays, we wanted to take
a moment to send you our greetings. Be sure that we’re profoundly grateful
for your dedication to duty and wish you inspiration and success in
fulfillment of our core mission.
Greeting card:
hxxp://xtremedefenceforce.com/[omitted]
hxxp://elvis.com.au/[omitted]
Merry Christmas!
___________________________________________
Executive Office of the President of the United States
The White House
1600 Pennsylvania Avenue NW
Washington, DC 20500
Recipients who clicked either of the above links and opened the file offered were infected with a ZeuS Trojan variant that steals passwords and documents and uploads them to a server in Belarus. I was able to analyze the documents taken in that attack, which hoovered up more than 2 gigabytes of PDFs, Microsoft Word and Excel documents from dozens of victims. I feel reasonably confident I have identified several victims, all of whom appear to be employees of some government or another. Among those who fell for the scam e-mail were:
-An employee at the National Science Foundation’s Office of Cyber Infrastructure. The documents collected from this victim include hundreds of NSF grant applications for new technologies and scientific approaches.
-An intelligence analyst in Massachusetts State Police gave up dozens of documents that appear to be records of court-ordered cell phone intercepts. Several documents included in the cache indicate the victim may have recently received top-secret clearance. Among this person’s cache of documents is a Department of Homeland Security tip sheet called “Safeguarding National Security Information.”
-An unidentified employee at the Financial Action Task Force, an intergovernmental body dedicated to the development and promotion of national and international policies to combat money laundering and terrorist financing.
-An official with the Moroccan government’s Ministry of Industry, Commerce and New Technologies.
-An employee at the Millennium Challenge Corporation, a federal agency set up to provide foreign aid for development projects in 15 countries in Africa, Central America and other regions.
The most interesting component of this attack was not the ZeuS variant, which by most accounts was an older, well-understood version of the banking Trojan. Rather, researchers are focusing on the component responsible for stealing documents, which suggests the handiwork of a novice who was quite active in 2010.
As noted by security blogger Mila Parkour, the “pack.exe” file downloaded by the Trojan is a Perl script converted to an executable file by way of a commercial application called Perl2exe. The pack program is the one responsible for snarfing up the documents on a victim’s computer and relaying the data to a file repository in Belarus.
Alex Cox, principal research analyst with NetWitness, a Herndon, Va. based security firm, said the attack bears remarkable similarities to the “Hilary Kneber” ZeuS botnet discovered by NetWitness last February. That discovery (PDF) garnered an unusual amount of coverage from the mainstream media, in part because NetWitness said the attackers had infected some 75,000 PCs on a wide range of government and private sector networks.
At the time, NetWitness said the victims were all part of the same botnet because the Web sites used to control them were all registered with the same hilarykneber@yahoo.com e-mail address. But it turns out that the more telling infrastructure point among the victims was this Perl2Exe component, which Cox says the company intentionally did not mention in its widely-quoted paper on the Kneber botnet.
“We didn’t talk about it at the time because it was somewhat sensitive then,” Cox said. “One aspect of this whole series was this government spear phish that also involved all these Hilary Kneber domains. At the time we thought they were all connected, but in hindsight what I think what was more likely was that this was someone mass-selling a bunch of preregistered domains in the underground. We continued to see that Hilary Kneber address off and on in attacks throughout last year, but this connection – where the [modus operandi] is similar without the Kneber address — is kind of interesting. It says to me that the same guy who was involved back in February is still doing it. It’s either the same guy, or someone is using this guy’s exact same technique.”
Update, Jan. 4, 9:23 a.m.: NetWitness posted its own writeup on this attack, available here.





When I read this post, the first thing I ask myself is, would I have fallen for this?
The first thing I do with every file I download is to run it through VirusTotal. Was the executable in the zip file 0-day, not detectable by any of the AV engines on VirusTotal?
If not, the next line of defense would have been a firewall that blocked unauthorized outgoing traffic by that exe.
Jonathan — Detection for this malware was pretty spotty back when it was first sent out. See:
VirusTotal results: http://bit.ly/glF7Gi
I think we have to assume that spear fishing attacks combined with address spoofing are going to get 90% of the sheep and a humbling high percentage of sophisticated users – maybe not every day, but on those doing-too-many-things-at-once-why-did-I-open-this-message-while talking-on-the phone days.
So…from the standpoint of Data Leakage Protection, what systems do people use to ensure that only permitted files are uploaded from a network? Do firewall vendors offer subscriptions to black/white lists of apps?
Yes, it was a zero day. It has several version all compiled shortly before delivery.
AV is pretty much worthless to detect new threats. Its really only good to tell you whether you’ve been infected, not to prevent it.
LUA, not running unsigned exeuctables, etc is the way to go.
I too ask the “would I?” question. From the Opening card.zip dialogue box above, I hope I’d ask, “why am I getting a card from iphonedeveloperskd.com? Why would the White House use that address to send from?”
Surely the definition of ‘trusted website’ should be known to the folks you’ve noted as falling for this. If I saw something from ANYONE pointing me to elvis.com.au, I would more than think twice.
Sigh, I guess we exit the old year with the same unheeded cautions as always…
To me, this just re-enforces the idea that many people are increasingly prone to lazy thinking resulting in the human element becoming the weakest link.
For instance, while watching the program “When Vacations Attack” yesterday, I couldn’t help but think a more apt name would be “When People make Stupid Decisions”. In almost every instance, the issue at hand came down to human error. I’m not talking about making simple mistakes, which we all are prone to doing. These were jaw dropping “DUH”, smack yourself in the forehead stupid mistakes that in many cases put lives at risk.
I can’t help but have the same reaction for these people who opened the attachment and subsequently got infected, many of whom should’ve known better! Granted we all can be duped in some form or fashion some of the time. But, come on man!
Hmmm…interesting as usual Brian – but I am a little concerned at the amount of detail that is being revealed in Mila Parkour’s post that you link to.
Full details of the FTP drop zone are listed including FTP credentials to login. Until the FTP site gets taken down, there’s nothing to stop everyone from logging in and helping themselves to all that stolen data.
Tim
Anyone who Googles some of the key terms in this article will find writeups from a variety of sources (Sunbelt, ThreatExpert, et. al) with the same information.
The good news is that almost all of the newer victims appear to be researchers who are purposefully infecting their test systems. The attackers have been fairly regularly wiping the FTP server of data to make room for new victim data.
Allow me to clarify my own statement: I don’t know who exactly has been deleting the data. It could be white-hat hackers have been going in and deleting sensitive information every so often. Or it could be the bad guys.
I do believe Brian you could be correct on this ? Great writ Brian been biz on my end .
At first glance I was puzzled with how you were able to “…analyze the documents taken in that attack” but now I see that the repository’s location has become public knowledge so that explains it.
Cheers!
Maybe I’m a little too cyber-trigger-happy, but if I had the resources of the US government, I’d be DDoS-ing that FTP site, and any other site connected with this attack.
Am I way off base? If our government’s sensitive information is under attack, should we not have some way to not just defend but counterattack? The days of true cyber-war are here, if we just organize the digital “troops” or resources, so to speak. I hate to talk like this, but this is exactly the “Coming Storm” that Brian is warning us about.
Even if the government is not so organized yet, we have already seen the escalation of cyber-war (and I don’t mean to hijack the term) in the private sector as Wikileaks-supporting organizations DDoS credit card companies and Paypal for shutting down payment routes.
Tactics. I forgot to add tactics. “The escalation of cyber-war tactics” was what I meant.
I still wonder what the H E double LL our “Cyber-security Czar” is doing to justify his/her position? Or do we even have one?
“f I had the resources of the US government, I’d be DDoS-ing that FTP site, and any other site connected with this attack”
I wouldn’t think so. Government response is driven by policy, and there are probably some strict guidelines about when to “go tactical” and who is allowed (and capable) to execute. DDoSing as policy would quickly cause a lot of new issues. It’d be easy to flip the switch on a thousand cheap blade servers, but public resources (well, non-gov’t any way) bear the burden of delivering such an attack.
If you believe service providers, the data carrying infrastructure of the Internet is near capacity. They want to implement tiered pricing and data caps for access. If our government’s policy was to DDoS sites it determines are bad voodoo, that would be an enormous and sustained burden.
What we see the US gov’t actually trying to do is leverage real-world resources to pre-empt online threats. Think of Thanksgiving 2010, when US Immigration & Customs were seizing domain names:
http://www.nytimes.com/2010/12/14/business/media/14music.html
Eventually, these actions will become more robust. I’m sure these domain seizures will end up in court. If they hold up, I would speculate the next step for the gov’t would be acquiring the power to seize IP address space. That would be a bullet in bulletproof hosting.
Long term there will be probably be treaties and agreements with foreign allies to exchange information and grant similar powers. Since the Internet is more than just the United States, many other domains will end up requiring policing (piratebay.nl etc).
This degree of government intervention makes me uncomfortable. There is no way for takedown and appropriation targets to respond to allegations until they are already victimized. That makes these capabilities ripe for exploitation by the corrupt and the unprivileged. Political opponents or activists, outspoken individuals, competition in the private sector… there are so many unscrupulous parties with their hands in the pockets of those who would control these powers.
I understand the intention is that this allows online policing, ultimately to protect law-abiding citizens and bring justice to victims. Yet I can’t help but think “Quis custodiet ipsos custodes?” (yes I had to Google it).
There is way too much to reply to here. You are assuming a static model though. Many of the threats I analyze use host names that come into DNS and are literally gone 4-12 hours later. Some of the time they map to compromised servers and some of the time they don’t Generally speaking, nobody is home with these host names – the whois is either bogus or nonexistent. I am speaking of host names that either directly or indirectly deliver malware content. In this particular case they used other legitimate hosts that are still there and didn’t even know they were compromised. . Do you DDOS these legitimate hosts? I will leave the rest of the discussion on DDOS to others.
Человек талантливый склонен к самосовершенствованию, поэтому от года к году все талантливые скрипткиддисы становятся талантливыми хакерами. Так было, есть и будет. Слава роботам!
Sorry Alex, I just don’t see any glory in robots. I do like working on them though! =D
Ага, многие ещё не догадываются, что их работодатели – роботы. Вот, к примеру на Форексе давно уже нет людей в топе. Роботы сами себе зарабатывают деньги.
A translation of Alex’s first post:
Человек талантливый склонен к самосовершенствованию, поэтому от года к году все талантливые скрипткиддисы становятся талантливыми хакерами. Так было, есть и будет. Слава роботам!
A talented personis inclined toward self-improvement. Therefore, from year to year all talented script kiddies become talented hackers. So it has been, so it will be. Hail robots!
I probably shouldn’t be, but I am amazed at the stupidity of people with positions who should know better and/or working in organisations that should know better. I would hope these employees were dealt severe reprimands at the very least, maybe even fired depending on the information that was leaked. For Pete’s sake, people! Way to go in lowering the public’s already fragile trust in government. Perhaps all these people should be given Macs or forced to use Linux.
@Jason Wallwork
I was wondering how long it would take for someone to point that out. I block all exe, com, scr, zip (to name a few) at the firewall. If you need to send us any of the above files you have to rename them (and we know to expect them)
this fails for content served via https:
It is really reaching a point where I don’t trust any sort of attachment or link that I get from anyone unless it is something that I requested and am expecting. I got a Christmas card URL via email a few weeks ago, and I had to think about it before I opened it – I noted that the email wished my wife and I a happy new year (and it listed both of us by name), so it was *probably* not botnet generated. But even then I couldn’t be 100% sure.
And if in doubt, I always have the Linux netbook that I can use to test it out on (the assumption being that malware isn’t targeting that little box – not a good assumption, but probably effective in “blocking” >90% of the malware). But it is easier to delete the thing without opening it than it is to go and grab the netbook.
The position of my clients has been to take certain risks as the average cost of doing business online. Their stance has been adopted by me, also. Why let the online thugs destroy the usefulness of the internet?
As long as we take steps to protect our data, why not accept a certain level of risk? My clients refuse to block java-script, flash, and other useful aspects of online life, and I don’t blame them! Why should we allow ourselves to be held hostage to these criminals?
As long as we use the right tools and maintain our awareness to the risk of being pwned by malware, there is no reason to deny ourselves of the very entertaining and useful assets of PC computing.
I regularly run the minefields for folks so I can find out how to deal with problems, when one steps on such mines. The threat-scape and self protection weapons are constantly changing, but we can handle it! We are not little sheep scared of our shadow, and we do not hide our heads in the sand like an ostrich either. It is simply a state of mind that weighs the risk, attempts to mitigate it as best as possible, and drive on!!
I and my clients refuse to capitulate to the criminals. We will continue to use the useful aspects of PC computing and simply deal with the consequences when such actions fall down. We are all grownups after all.
Two comments:
1. pack.exe is an arbitrary executable. Least privilege, while necessary, is no longer sufficient. Just as with Zbot. Execution control via Software Restriction Policy whitelisting using either gpedit.msc or Parental Controls (or TrustNoExe for Windows XP Home) can prevent arbitrary executables from running.
2. Perl, while it can be installed on Windows, is installed by default on Mac OS X and desktop Linux. A wake-up call for users on non-Windows operating systems?
On the other hand it is very unlikely that a file downloaded from the Internet get automatic chmod u+x.
If the email attachment file is named ‘greetings.pl’ , sure.
But, what if this file were placed into an archive file (e.g., greetings.zip, greetings.tar.gz , greetings.tar.bz2) and the email instructed the user to extract the archive into the user’s home directory, double-click the greetings.pl file (now an executable) and select the run command button from the popup window?
That is a good point. It illustrates what allowed the thing to work in the first place – the PEBKAC factor. Don’t rush to uninstall perl on ‘nix systems. On just the top level alone on Ubuntu I have 105 perl scripts in /usr/bin. But the inital point here is showing some ignorance. The file was a stand-alone executable program that was created from perl script. Despite being created with perl it worked just fine without perl installed. So not having perl installed on Windows provided no protection.
Perl is not needed to run malware on Windows. Not with *.exe, *.vbs, *.com, *.reg, and *.bat files. Just to name a few of the executable file types present on Windows.
And as far as removing Perl from one’s Linux (or Mac OS X) desktop, no one suggested that. But, just for grins, I removed both the perl and perl-base packages (and, through various dependencies, a LOT of other packages, some critical to the OS) from my Debian Lenny desktop and got two pop-up windows warning me that removing these packages would make the system unstable. Since I was in a VM with a snapshot, I went ahead and removed all the packages including ‘(ESSENTIAL) to be removed’ packages. Well, no surprise, the system could not shut itself down even though some packages were not removed and I had to close and power off the VM. It rebooted into a root terminal window. VM restored and no damage done.
My point with this exercise is that all OSs have various executable files that are necessary for them to operate. And all OSs have users, some of whom are susceptible to social engineering. And the less hardening that has been applied to a given OS (whether by the mfr, a sysadmin or an end user), the greater the likelihood that social engineering and other exploits will be successful. No OS is immune to this.
Any edge AV/spam filter worth its salt should have caught this. What is the government running?
i think the idea is that people who work for the government have personal addresses and access that mail.
i’m not sure how many people ONLY use their work computers for work and their home computers for personal stuff.
No AV can reliably protect against one-off programs that none of the AV companies know about yet. Some of the AV companies that I have notieed do fairly well with heuristics are McAfee-GW-Edition, Panda, and a few others. Here is the improved detection:
http://preview.tinyurl.com/2923zr2
None of them detecting are invoking heuristics – all of them show a hard detect instead. BTW Brian, please use this URL shortener rather than bit.ly. I have finally had to start blocking bit.ly in my hosts file at SecureMecca.com / HostsFile.org because I kept getting it used to redirect to malware. This way you get a heads up on where you are going. If you still want to get there after seeing where this is headed, go ahead. If anybody knows of any other URL minimizers that provide a preview feature please let us all know what it is here as well as firing off a private email to me (see the header of the PAC filter).
Thanks for the post hhhobbit;
I’m surprised McAfee can do anything right. The best heuristic engine I’ve tested is Avast. It may not find all the viruses, but the ones it doesn’t find lie dormant. CCleaner gets them.
In the last four years I’ve found this to be true:
1. Scanning with Avast will find no viruses if you update it regularly.
2. I’ve followed up with paid independent forensics to see if it missed anything – none found
3. It doesn’t always find malware, but it is not supposed to.
4. If malware don’t trip its engine, AdWatch does.
5. On ALL of the other top 5 anti-virus brands but ESET, I’ve found at least four or five serious threats that weren’t detected – the only exception was Avira, but it was too slow on the heuristics to stop an injection packet that was defined.
I have had so much trouble with ESETs licensing scheme, that I gave up on NOD32, but I can’t prove that it isn’t probably the best. My clients can’t afford it anyway, so back to Avast we go me matey!
I dont understand why the OS just doesnt let people run unsigned executables from the internet. Seriously, just refuse. Make the user go into the folder manually with explorer and get a big ugly UAC prompt with text like “This is most likely malware.”
Also, why cant the OS analyze the executable and try to figure out what it does and produce a permissions list like:
1. Will access My Documents
2. Will access remote FTP server
3. Will attempt to change startup registry keys
4. Downloaded from: http://www.fjfjdjfd.cn
5. Packed execuatable
etc. Basic heuristics embedded into the UAC prompt. I know MS can do stuff like this. Why aren’t they?
@drzaiusapelord
Why aren’t they? This is from a recent Gartner report (link to PDF below – not malicious!!)
“Malware effectiveness continues to accelerate, while vendors are busy polishing increasingly ineffective solutions and doing little to fundamentally reduce the attack surface and protect users.”
and….
“Signature-based malware detection has been limping along on life support for years, yet vendors seem unwilling to aggressively invest in more-effective solutions, preferring to “tweak” the existing paradigm.”
Says it all really…..
http://www.symantec.com/content/en/us/about/media/industryanalysts/Gartner_MQ_endpoint_protection_platforms_17Dec10.pdf
Tim
This has been a frustration of mine for several years now. Every year the malware problem gets worse, and every year the powers that be try and nibble around the edges, but nobody is able or willing to say or do anything that would make a significant change for the better.
I have predicted in the past the death of the internet, and perhaps part of this statement was hyperbole, but we are reaching a point where the internet isn’t safe for things like banking any more. All we will be left with is a place where people can upload pictures of their cats.
A proper fix is going to step on some toes, I think. And nobody wants to do that. But ultimately more and more companies are going to have to implement some fairly draconian filters because the price of not filtering can be some fairly serious data breaches. Employees that want to play on the web while on the job will have to use their own smartphones.
The true answer is within each individual. Once personal responsibility and common sense (critical thinking) return, then and only then will we have a true solution. Instead we have the masses trained in lazy thought processes and relying falsely on ONLY Anti-malware software to protect them from themselves, thus creating a ton of low hanging fruit ripe for the picking.
Let’s stop trying to reduce everything to the lowest common denominator. Like anything in life, there is no magic pill that is going to solve the problem for you. You want a secure computer and online experience, then take the bull by the horns and make it happen. The tools to do so are readily available to anyone. There really are no excuses.
You suffer from the idealization of the past fallacy.
You must cater to the LCD, you must put in proper controls. Humanity as a whole won’t all suddenly become security conscious geeks, ever. The same way we never all became car mechanics or know how to work a sewing machine or a lathe or work with 220 voltage lines or do our own plumbing.
Out of the box security is incredibly important. Autoupdating without user intervention is incredibly important. The less the user does the better. Telling them to go download 10 different tools to help them is ridiculous.
If you hope to instill critical thinking and common sense in everyone who uses the internet, it will never happen. To me this is just passing the buck.
I don’t think you answered d…lord’s question. He asked why the opsys didn’t simply inform what the (newly acquired) exe’s will do. But you respond with info on how ineffective the AV makers are.
Microsoft is improving… and maybe they’ll take a gander at how android apps are being installed, with all the warnings… and do something similar for downloads/etc. The AV makers… don’t do opsyses… they’re afterthought add-ons. The opsys makers should secure it… the opsys. You -can- educate new users, at school… but some will never try – they can have a nanny front-end. Things can be done… not based on profit (AV) models.
I’ve just started playing w/ Nitdroid (Android for the Nokia N900).
I installed ~50 applications in about a day (once I found the Market). The permissions requests remind me of Java from >10 years ago. There was perhaps *one* app that I chose not to install because I didn’t like its requirements. However, I think fewer than 5 apps didn’t make requests, and the vast majority requested things which I felt were unreasonable — but not sufficiently unreasonable to prevent me from tasting.
Basically, I’ve installed roughly 40 apps which are fully capable of spying on me, stealing my data, and doing all sorts of other things.
Roughly speaking, if a user wants candy, they’ll do anything to get it, even when they’ “should know better”.
Does it really matter? “Average” users are pretty idiotic, they’ll end up clicking ‘Run’ anyway.
Because users get too much useful stuff blocked by such a naive policy; this is the basis of social engineering in some ways: the user in unsurprised by this situation they’ve already seen a thousand times and say yes.
There’s no need to wait on 3rd party security vendors to control Windows executables.
Software Restriction Policy whitelisting can be applied to all of Microsoft’s currently-supported Windows operating systems, except for XP Home. Combined with least privilege (i.e., a limited or standard user account), it restricts a user to write where he/she cannot execute and execute where he/she cannot write. Executables are allowed to run only from folders C:\Program Files and C:\Windows (or any other specified folder, such as C:\Oracle Client), where a limited or standard user does not have write permission.
For Windows XP Pro, Vista Business/Ultimate/Enterprise and 7 Pro/Ultimate/Enterprise, use the group policy editor, gpedit.msc:
http://www.mechbgon.com/srp/
For Windows Vista Home/Ultimate and 7 Home/Starter/Ultimate, use Parental Controls to select the applications that a standard user (adults included) needs to run in their account:
http://windows.microsoft.com/en-US/windows-vista/Prevent-children-from-using-specific-programs
For Windows XP Home, use the free, 3rd party program TrustNoExe:
http://www.beyondlogic.org/solutions/trust-no-exe/trust-no-exe.htm
Thank you RHM! I hadn’t been to those sites in a while! I had completely forgotten about them. Very useful!
“standard user (adults included)”
Yes, the thinking in some approaches is limited… in later years, some may find it necessary to apply ‘Parental Controls’ on their own parents (as they become ‘less able’) if they should find themselves caring for them in-house, yet still give them electronic access/communication.
Likewise with user interfaces in general… some simpler interfaces, -and- more secure user interfaces developed perhaps for children, serve just as well for the aged/unable, and simply those less able (educationally challenged or diminished mental capacity). We do have a broad spectrum of people as ‘users’… and not everyone stays as sharp ‘to the end’.
Seems we really have shallow depth in the development of user interfacing, for the sake of immediate profit. I’d like to see more done in most programming to provide a simple/intuitive user ‘menu’/interface, along with a more advanced shell/interface. There are times you/users just want to play some music… not net share converted format files to all devices in the house and beyond, build playlists, update annotations, etc.
But unless you’re technically proficient, it’s “let the user eat cake/beware”… of the interfaces/power they’re given. I don’t like to restrict users, but we can simplify things if the development effort is made/included and expected! Not just one size fits all.
From where I sit, seem to me that the office of the secretary for the president didn’t do their checking very well before sending out and ecard. Ecards have been and are inhearently dangerous and have a long history of being so. Seems also to me that the providers DNS was leaking TTL’s as well as didn’t have DNSSEC implimented which from my point of view is a definate “Do-not-use” read flag.
Troll much?
We had this discussion in the comments of another of Brian’s posts. A large number of government employees insist on sending all content as .doc or .pdf attachments instead of plain text or html, even when the latter would be perfectly adequate.
Emails arrive that say something useless like, “Please see the attached file for the new policy.” Recipients who deal with government agencies become so accustomed to clicking on attachments for every email they receive that they give up being suspicious, expecting useful explanations, or checking the file extensions first.
The explanation offered was that precise format of each Word or Reader files has to be officially approved by a bureaucrat before being sent on behalf of those agencies. I still think it’s sloppy policy, given the fact that the same recipient email inboxes receive all manner of malicious and spoofed messages. If the message has to be that precise, post it on a trusted website and let people view it there. Most of the messages in question aren’t that important, or they wouldn’t be sent by email in the first place.
Out of curiosity: althought being perl-based, the exe was Windows-only, right?
Given how fashionable Macs are lately, I’m a bit surprised we don’t see more of these social-engineering attacks for Macs.
It is a matter of simple numbers. Probably less than 1% of the people the message was sent to use a Macintosh. None of the people that received the message that got infected use Linux. So if you are a hacker, what are you going to send? OTOH, if these people that got infected are supposedly security experts, why aren’t they using Linux or a Mac? That one extra little protection factor (and that is all it is – these other OS are not some magic security solution that does it all) would have saved the day for them. Some of the other methods given here would also have protected them if they are using Windows. For my PAC filter it would have been this rule uncommented:
BadURL_WordEnds[i++] = “.exe”;
Allow the exe files to come only from trusted sources (the GoodDomains). Like I just said, others have given ways to do the equivalent of this here. That doesn’t stop the files named X.php?gobbledygook that are really exe files, but aren’t you supposed to be using a browser / system combo that doesn’t run them?
The PAC thing is cute/clever, but it fails for anything using content-disposition: attachment; filename=…
Do you want the alternative which is most people using Windows XP with only SP1, and no PAC filter and no AV? They refuse to patch because it “causes one or more of my programs to no longer function.” They refuse to run an AV program because it “takes over my machine.” They refuse to use Linux because in their pea-headed brains it is a POS due to the comments made by many Windows advocates here. In this particular instance as in most involving email as the attack vector, the malware is not attached but is frequently the result of clicking on a link that many times is hidden by Outlook with clever mouse over commands hiding the URL in the HTML message to make it look like it is coming from an official source. That just argues for government people using ASCII text instead. It also argues for them using only OpenPGP encryption (GPG4WIN free, PGP commercial) signed email. If it isn’t ASCII text and it isn’t signed it isn’t valid if it comes from co-workers. OpenPGP doesn’t help if the message does not come from a co-worker. But if all normal work flow messages were OpenPGP signed ASCII text messages the content / disposition for something pretending to be from co-workers, especially if it is HTML instead of ASCII text would be a no brainer. Those messages (and this would be one of them) would stand out like a throbbing red thumb that had just been hit by a hammer. DELETE!
What do you have against that little bit of extra protection that the PAC filter and blocking host file I provide gives you? I am having to move the PAC filter out of the way dozens of times each week to pull down the malware. Also, in this particular instance, with that one rule activated (“\.exe”), it WOULD have blocked this particular spear-phishing attack. I do have government employess using what I provide and I do advocate they activate that particular rule if they are using Windows. I sincerely doubt that adding “pack\.exe” would do much good. The hackers will probably never use it again. Or it may be like Butch Cassidy saying “we will hit them on the return trip too.” Look at this one as an example:
http://safeweb.norton.com/report/show?url=mytraff.com
MalwareDomainList removed this host. I am keeping them in my black-list (blocking hosts file) which is the other part of what I provide courtesy of the GPLv2 license. Nevertheless, when I tested one of the links Symantec provided the first host I was redirected to was blocked by the PAC filter without me even knowing what the host name was. Once I gave the first host a white-list rule in the PAC filter to make it past the first block, the second host which was probably dead (no longer in DNS) within 4 hours (it is gone less than 12 hours later) had yet another rule blocking the actual download of the malware due to the file name they used. Here is the scan of the downloaded file and I submitted it to the AV companies via my private channel (the name VT uses is NOT the actual file name):
http://preview.tinyurl.com/25d2phv
Note that just as I said, McAfee’s GW-Edition heuristics (McAfee alone doesn’t have it, it is the GW-Edition that adds the heuristics) kicked in. But if any of these things were done including one more which is these people had been using Linux or a Macintosh we wouldn’t be reading / discussing this, would we? The PAC filter of course doesn’t lend itself to a government solution but the filters the government are using could benefit from studying some of the smarts contained in it and going out and doing likewise. The problem is, NONE of these things other than perhaps patching the machine and running an AV package is being done by the governments. I consider that an inviatition for a disaster to strike, and the disaster HAS now struck. But if you blame the people that got bit and don’t make any changes it will happen again to somebody else.
One more thing needs to to be said. The Windows advocates totally misinterpreted me saying I don’t want ${HOME}/bin first in my path as being I am against Ubuntu Linux. Au-contraire! One of the Linux systems I use IS Ubuntu. The complaint is against any and all unsafe computing practices no matter where I see them. So if Ubuntu is your cup of tea (and it is one of mine), go ahead and use it. Just make sure ${HOME}/bin is positioned to come last in the PATH, not first. But even if these people that just got bit had been using Ubuntu even with the PATH set wrong we wouldn’t be reading their names here.
The government has always appeared to me as trying to look the most competent but always resulted in the highest incompetency in IT security of any single sector.
The military doesn’t do all that much better either. IT security seems relatively new to the DOD despite the fact that DARPA originally developed the internet.
I fear we appear as leaky to our enemies now, as the Axis forces appeared to our military intelligence in WWII.
Can someone post a sample smtp header from the emails?
I’ve been told that the emails spoofed whitehouse.gov and I’m wondering if this is correct.
Dotzero, check out the link to Mila Parkour’s writeup, which I believe contains the information you’re seeking. I don’t think the attackers manipulated the headers, or if they did, it wasn’t to show the whitehouse.gov domain.
To be clear, the plain text “from” information said Jeff.Jones@whitehouse.gov. The headers said something different:
Received: from bondi.myownserver.net (bondi.myownserver.net [118.127.17.43])
(using TLSv1 with cipher DHE-RSA-AES256-SHA (256/256 bits))
(No client certificate requested)
by z.teksimple.com (Postfix) with ESMTP id 7B4E2578002
for XXXXXXXXXXX; Thu, 23 Dec 2010 20:06:41 +0000 (UTC)
Received: from taecnsw by bondi.myownserver.net with local (Exim 4.69)
(envelope-from )
id 1PVrNa-00057R-Go
for XXXXXXXXXXXXXXXXX; Fri, 24 Dec 2010 07:03:14 +1100
Return-Path:
From:
To: “XXXXXXXXXXXXXXXXXXXXXXX”
Subject: Merry Christmas!
Date: Thu, 23 Dec 2010 10:03:14 -1000
Message-ID:
MIME-Version: 1.0
Content-Type: text/plain;
charset=”iso-8859-1″
Content-Transfer-Encoding: 7bit
X-Mailer: Microsoft Outlook 14.0
thread-index: AQIGUvhtW6McP8BIIPWFeDGkYaOI5Q==
Thanks Brian.
It’s interesting that the whitehouse has not moved to implementing things like SPF and DKIM/ADSP (yet). These are not magic bullets but do raise the bar. Even better would be for them to use PGP signing of messages.
Any evidence this causes problems on ANYTHING OTHER THAN WINDOWS?
It really bothers me to see stuff that talks about “computers are vulnerable” when the vulnerabilities are limited to Microsoft products.
I’m not knocking open source here, just to be clear, but when you have files that don’t even need to install to do damage to you, it is just a matter of time, and the popularity of iPhones, and Droids, until it pays for criminals to at least attempt to develop vectors that might make it possible for them to do damage to any person using any popular platform in the open source community.
Remember, it is not the base OS that is the threat, but the popular applications that can compromise the best designs in operating systems.
Maybe I am missing something here, but how is it that our supposedly secure and shielded government agencies have come under this barrage through emails? I mean, is there some sort of directory for email addresses and contact information for various bureaus, agencies, and organizations, that the evil-doers can go to in order to compose a target list? Shouldn’t these email addresses themselves be considered and treated as classified and, therefore, not readily accessible by anyone unaffiliated with these agencies? It seems that the sheer fact that the addresses were accumulated on a hit list would indicate that someone with internal ties carelessly allowed themselves to be targeted. If I am incorrect, pardon my ignorance, but I just have to say, hmmm…
As far as their email addresses being secret, remember that they are technically the employees of the American people, and at least some of their email addresses need to be made known to those employers in order for them to provide the services they were hired to do. Other addresses are probably made public by recipients carelessly hitting “reply all” without using BCC.
So does the government or industry have any email address that any and everyone can forward suspect emails to? This might improve the nation’s response time to such threats.
APWG generally collects Phishing emails and coordinates response across various sectors to reduce effectiveness of Phish attacks – like this one.
http://www.antiphishing.org/
You can also use PhishTank / OpenDNS but do NOT send them malware! Just send them email messages where somebody is pretending to be somebody else:
http://www.phishtank.com/
The signup is free. The reason I say don’t send malware is because some of their URLs redirect to malware and all PhishTank has for choices when I and others review them is phish, no phish, or not sure as the main choices. They don’t have a malware choice. I wished they did. Malware really isn’t any of these choices. For the ones involving malware submit them to ClamAV which does share some of what they get with other AV companies. They want samples so if all you have is a redirecting URL in an email, save the email message into a file. If it is an exe, msi or similar attached file, save that. Alter the exe, msi and simliar files to have either a “.ck” or “.BAD” on the end of the name. Windows normally doesn’t know what to do with either a “*.ck” or “*.BAD” file. Zip the file using encryption with password “virus” and submit the zipped / encrypted file to ClamAV.
http://cgi.clamav.net/sendvirus.cgi
All of this information and much more gets used by all of the browser vendors as well. But that only protects against know threats, not unknown ones. That is why I provide a PAC filter to guard agaisnt threat vectors that are not known yet based on heuristics:
http://www.SecureMecca.com/pac.html
http://www.HostsFile.org/pac.html
The first problem with this is that you are now depending on my judgement of what you people fall for and whether hackers will continue to use it. I am now some sort of god that sees everything. The second problem is that at best it is less thatn 15% efficient – there is a lot I cannot do anything about the problem. The third problem is FPs (False Positives). Frequently I have rules that I know will help and cannot give them to others for fear of the FPs the rules would cause. I have to use the rules privately for a while. Many times by the time I can give the rules to others, by then the rules worthless. The hackers are no longer using that pattern. The AV companies that try to do too much with heuristics rather than signature based detection have the same FP problem I have. So I vehemently disagree with others here criticizing the AV companies. Disclaimer: I do not work for and have never worked for any AV company. The AV companies are swamped and if they put in more heuristics they will eventually need a bail out feature where the “this looks suspicious” gets passed back to the person using the system. But since supposed security experts fell for this one, what can I say? I think the hackers did it just to prove it can be done. Should the AV company trust the user’s decision for something their product deems suspicious? In this case maybe that would have backfired. If I was one of the ones that got had maybe I would resign and do something else. But hopefully I would not be one of them. I use Linux or some BSD system. But I was also using Unix systems long before Windows existed. I am not saying I am immune. I am saying by using something that was not part of this attack vector equation I have bought some extra protection. But it is highly likely if I was working for the goverment I wouldn’t have that choice. They seem to be mandating an all Microsoft Windows solution. It makes me wonder how they managed before these unsafe computers were added to the mix. Things were probably slower but the whole five course meal of information didn’t get siphoned down to a machine half way around the planet!
“I am now some sort of god that sees everything.” I said this facetiously. I don’t even see over 25% of what there is to see!
But that is a lot more than what most people see. Does that make me an expert? I hope not. An ex is a has been, and a spurt is a drip under pressure.
Good stuff here hhhobbit! Nicely done!
Thanks. I don’t have anything against the advice the Microsoft people have for making this less possible. It is good advice. But the reality is too many people run XP SP1 with no AV. My only question is – how easily is it to implement their solution on thousands of machines running Windows 7? I know it can be done with Windows XP with SP3 and all updates (the only way XP should be run). But they are still ignoring the need for OpenPGP encryption. Even the blockers (and I am one) and other computer and network security people won’t get and use encryption tools any more. One blocker drags out this key from PGP from 15+ years ago. It is so hopelessly out of date, with the fact that his key was not on the key servers he should have just abandoned it. Tests showed we could not exchange encrypted email messages and I use Thunderbird / EnigMail which can handle almost everything. So what does he do? He uploads this obsolete key with no expiration date to the key-servers that doesn’t work any more. What he should do now is first, revoke the key (if his software can do it) and upload the revoked ancient key to the key servers. Second, he should delete everything he has (keys, software and all) and download GPG4Win from GPG4Win.org or pay for the commercial version from PGP Corp. I suspect it should be the former since the inertia to not move seems to be tied with the fact that he paid for what he has now. Third, he should create new keys. The default of 2048/2048 RSA/RSA is reasonable. The keys should be set to expire in ten years at the maximum. Make them for only two years if you think you will have something you won’t want five years hence as you learn more. I do have a significant problem with using SHA1 as the Digest (hash) algorithm. I have saw too many SHA1 certs from another company stuffed into malware that passes muster. Only a small percentage (less than 1%) of malware have SHA1 certs showing how difficult it is to do it. But Stuxnet was not the first thing to use purloined SHA1 certs. I don’t think you need what I have which is SHA512 as the preferred first hash. SHA256 is reasonable. Some software won’t support SHA384. AES is more than adequate for the symmetric cipher. If you need more security from prying eyes then use either AES256 or TWOFISH. The CAST5 and 3DES symmetric ciphers are no longer good enough. Nevertheless, they are better than nothing and if Sarah Palin had been using them a kid in Tennessee would not have been able to read one darn thing except for the spam if she has what most of of us have POP that can be accessed using a web-mail interface. I have CAST5 and 3DES as last choices for people that cannot do any of the others. But Sarah Palin is probably still using web-mail with no encryption. She and her close friends and family need to set up POP email and use OpenPGP encryption! If allowing this to be used isn’t written into FISMA compliance then it should be. The most difficult thing is finding a good pass-phrase. Mine depends on both my cognitive and muscle memory and is not written any place. I don’t need to obfuscate things all that much except for nasty host names that may cause problems because the email scanner tosses the message into /dev/null (NUL). I do need the assurance that something really came from somebody and it better work on a Macintosh and Linux as well. But as a point here, if these people had been using OpenPGP signed messages even on Windows with a modicum of common sense we would not be reading this story. Forget FISMA compliance. Despite having a degree in Mathematics I am very short on theory and long on something that works. What these people have isn’t working. You need to have something that works and is as simple as possible, but no simpler. What they have is way too complex (start wading into what is needed for FISMA compliance and you will see what I mean) and doesn’t work. Well, it didn’t work here. There is no magic security bullet, but to ignore OpenPGP encryption as part of the security equation just because it doesn’t come from Microsoft or works with other platforms in addition to Microsoft seems rather dumb to me. I will not accept a Microsoft only encryption solution. One of the other things I already said here is that if these people had been using Macintosh or Linux machines we still would not be reading this story if that was the ONLY thing they had done. Think about that for a long time government people.
Once personal responsibility and common sense (critical thinking) return
Comment: I would never link common sense with critical thinking for there is no such critical thinking in common sense, the sense that is common to the tribe.
Software Restriction Policy whitelisting can be applied to all of Microsoft’s currently-supported Windows operating systems, except for XP Home. Combined with least privilege (i.e., a limited or standard user account), it restricts a user to write where he/she cannot execute and execute where he/she cannot write. Executables are allowed to run only from folders C:\Program Files and C:\Windows (or any other specified folder, such as C:\Oracle Client), where a limited or standard user does not have write permission.
Comment: The average user will have no clue what to do with this or even how to proceed, or even to know if what they are doing is right or wrong.
For Windows XP Pro, Vista Business/Ultimate/Enterprise and 7 Pro/Ultimate/Enterprise, use the group policy editor, gpedit.msc:
There’s some truth to your response, especially as it applies to the Windows Group Policy editor, gpedit.msc, and 3rd party program TrustNoExe. That’s why I included links to good tutorials. However, many average home users are running Windows Vista/7 Home and Starter editions. Creating standard user accounts and applying Parental Controls to those accounts are really not beyond the grasp of average users, once they become aware of these features and their utility.
As for the enterprise, Windows sysadmins are not average users and should be quite capable of setting up Software Restriction Policy whitelisting using gpedit.msc for their users.
And, for the record, Mac OS X includes managed user accounts and Parental Controls. These provide an easy path to harden one’s system just as they do on Windows.
To most users, a computer is a tool for chatting, making so called friends, etc., and beyond that any thought about computer maintenance, installing good anti-malware protection, etc., is not in their realm of thinking.
For people who have a deep love for computers these thoughts are always running through their heads.
For government agencies, the employees in them are pretty much no different than Mary Jane or Bubba sitting at home clicking away for fun things to do. They have no immediate concern of problems. Concern only arises when the computer begins to act funny.
I can understand average people at home falling for this stuff, but many of these departments should have employees who know better.
An employee at the National Science Foundation’s Office of Cyber Infrastructure…
An intelligence analyst in Massachusetts State Police…
An others who borderline might or might not have known better. But these are departments that deal with crime or Internet infrastructure. You’d expect and *should* expect a higher level of conscientiousness on their part. Governments have to recognize that in departments like these that safe computing practices are as important as other credentials they might like for in an employee. I’d hope at the very least these employees were re-educated. In the case of the intelligence analyst, I hope, fired.
Jason,
I truly believe that just about anyone can be social engineered, even “the experts”. It’s all about the social engineering. The SE leverages all sorts of aspects of people as people.
People want to be loved.
People want to be recognized.
People have expectations that can be leveraged.
The experts are just as human as the next person and just as susceptible if the right elements are brought to bear.
How true. Good Point.
In the immortal words of Paul Harvey, and now for the rest of the story. What if these people had been using a Macintosh (NOT open source) or Linux (IS open source). We would not be reading their names in Brian’s thread. Most of the Linux bashing I see going on here ignores one thing – I still have only one piece of Linux malware after years – a toolbar that doesn’t completely uninstall and leaves a resident JavaScript plugin reporting back home to Papa. I have dozens of Windows malware samples flowing in every week if not every day. For now at least that one extra measure of using something other than Windows XP with only SP1 (normal user: “if I update all of these programs I have will no longer run”) and either IE-6 or IE-7 (normal user and even some Windows admins: “I cannot get IE-8 to work with what I must do”) provides one extra measure of protection. I will take hypthetical risks over real ones any day.
There you are, with your stern face, sharing cracking eternal wisdom like “malware gangs whose activities over the past year have blurred the boundaries between online financial crime and espionage”.
Yes, well, no. But what do you expect from an industry that thinks plugging holes in swiss cheese is a valuable contribution to society? For a line to blur it must first be distinct. And that hasn’t been the case since “the competition” specialised into crews that gather data to sell it to teams that process it and sell it to groups that monetise it… somehow.
What that first bunch are after is exactly one thing: Saleable data. Doesn’t matter where it comes from, how they get it, whose it is. Just that it is saleable somehow. That is all.
Is that really the best you can do to compete with these guys? Mumbling about blurring lines? Bah.
ZaUaQx http://gdjI3b7VaWpU1m0dGpvjRrcu9Fk.com