A picture may be worth a thousand words, but a single tainted digital image may be worth thousands of dollars for computer crooks who are using weaknesses in Google’s Image Search to foist malicious software on unsuspecting surfers.
For several weeks, some readers have complained that clicking on Google Images search results directed them to Web pages that pushed rogue anti-virus scareware via misleading security alerts and warnings. On Wednesday, the SANS Internet Storm Center posted a blog entry saying they, too, were receiving reports of Google Image searches leading to fake anti-virus sites. According to SANS, the attackers have compromised an unknown number of sites with malicious scripts that create Web pages filled with the top search terms from Google Trends. The malicious scripts also fetch images from third-party sites and include them in the junk pages alongside the relevant search terms, so that the automatically generated Web page contains legitimate-looking content.
Google’s Image Search bots eventually will index this bogus content. If users are searching for words or phrases that rank high in the current top search terms, it is likely that thumbnails from these malicious pages will be displayed beside other legitimate results.
As SANS handler Bojan Zdrnja explains, the exploit happens when a user clicks on one of these tainted thumbnails. “This is where the ‘vulnerability’ is,” Zdrnja wrote. “The user’s browser will automatically send a request to the bad page which runs the attacker’s script. This script checks the request’s referrer field and if it contains Google (meaning this was a click on the results page in Google), the script displays a small JavaScript script…[that] causes the browser to be redirected to another site that is serving FakeAV. Google is doing a relatively good job removing (or at least marking) links leading to malware in normal searches, however, Google’s image search seem to be plagued with malicious links.”
Denis Sinegubko, a Russian malware researcher who has been studying the fake anti-virus campaigns, called this tactic “the most efficient black hat trick ever,” and said it is exceedingly easy to set up. He said he’s received access logs from the owners of several hacked sites, and has used the data to estimate the traffic Google sends to these bogus image search pages. Sinegubko reckons that there are more than 5,000 hacked sites, and that the average site has been injected with about 1,000 of these bogus pages. The average page receives a visitor from Google approximately every 10 days, he said, which means Google is referring about a half million visits to fake anti-virus sites every day, or about 15 million visits each month.
For example, one of the hacked sites Sinegubko said he saw access logs for was in Croatia; It had a Google page rank of zero prior to being compromised with the phony image search scripts. The logs showed that the site had been hacked on Mar. 18, 2011, and that Google began indexing the tainted image pages the next day. “During the next 5 weeks it has indexed 27,200+ doorway pages on this site,” he wrote in a blog post on his findings. “During the same 5 weeks Google Image search has sent 140,000+ visitors to this small site.”
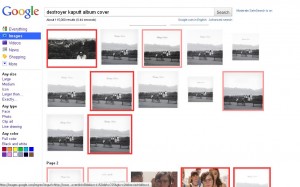
Sinegubko is developing an add-on for Firefox that can flag malicious Google Image search results by placing a red box around images that appear to link to hostile sites; Images with a pale pink box around them are hot-linked and may also be malicious, Sinegubko said. I tested the add-on (which is not ready for public release) searching for the cover art for the album “Kaputt” by the Canadian band Destroyer. As you can see from the image above, most of the images returned link to sites pushing fake anti-virus.
Sinegubko said his analysis of the malicious scripts that do all of the work indicates that the spammy pages are built when Google’s bots try to index them. Each bogus page targets specific keywords, in this case, the word “destroyer.” The script then requests Google’s autocomplete results for the word “destroyer,” and it is given 10 suggested keywords. The script then includes those new keywords in the spammy pages as links to “related searches” (for example, links to “23.php?q=destroyer-droid-start-wars”, and the results in the image above, “23.php?q=destroyer-kaputt-album-cover”. “When Googlebot follows those links, the script generates spammy pages for them, at the same time it inserts links to new suggested searches,” the researcher said in an instant message chat with KrebsOnSecurity. “This way Google suggests new keywords for spammy pages and automatically builds spam and indexes it.”
Several security experts have suggested specific steps that Google could take to cut down on scammers using Google Images, such as bumping sites that hot-link images to a much lower ranking in the search results for a given term.
Google spokesman Jay Nancarrow said the company was aware of the attacks and that it is making “active efforts to improve both the quality of the results and malware detection,” but declined to be more specific. “We’re improving, as are the people trying to put users at risk, and in the interests of those users it’s best if we don’t reveal everything that we’re doing about this.”
Rogue anti-virus scams almost invariably rely on malicious scripts that can be blocked by the excellent Noscript add-on for Firefox, which lets you decide which sites should be allowed to run scripts. If you happen to stumble upon one of these fake anti-virus security alerts, stay calm and avoid the urge to click your way out of it. Instead, simply hit Ctrl-Alt-Delete, select the browser process you are using (firefox.exe, iexplore.exe, etc.) and shut it down.




Brian, I have used the technique you described to terminate Firefox when I get the FakeAV pop-up but I have my Firefox options set to reopen the same tabs when it restarts. To avoid going right back into the same malicious page, I have to restart in Firefox’s Safe Mode which then lets me choose which pages to reopen.
Oh rats, I meant to mention that in the post. Thanks for the reminder, Ben.
here’s a simple workaround for your tab problem, instead of closing firefox open taskmanager and kill the process this way next time you start firefox you get the whoops error page with little tick boxes so you can select what pages you want to reload
For FF:
Tools->Options->Content
uncheck “Enable javascript” checkbox
close popup
navigate to a clean page
check bcak “Enable javascript” checkbox
All this really argues for is more intelligent design. Who wants a browser to reopen with the same thing that caused the browser to crash or was the source of a malware scan? Since when is Google safer than my home page which is a picture on unwritable media? When my browser crashes I want it to come back to a clean state. Usually a history begins to kill you. NoScript is wonderful for Firefox but why are we having to add it in this day and age along with something that puts the tab ordering back the way it was? Since when was download + inject + install intelligent design? I favored the old says where the download and the install were two separate steps. In general, for any change to be good it should be overwhelmingly superior to the old way of doing things or it should not be done. There should be a security guru on every browser and other software design team. If there was and they knew what they were doing we would all be safer by default.
@ Brian: That happened to me today when I was looking for a picture of a birthday cake – guess birthdays are really popular searches.
One question though: Shouldn’t you run a virus scan after shutting down the browser, just to be safe? Seems to me I heard that a scareware attack is sometimes accompanied by a Trojan horse that tries to install other, more malicious intruders, such as keystroke logging programs.
It certainly can’t hurt to run a scan afterward. If your anti-virus product doesn’t detect the file on access or download it’s unlikely to do so on a drive scan, but it never hurts to check.
Generally, if you don’t download the stub installer, you won’t have other stuff dropped on your system. Exceptions generally happen in two cases: You are running some old software or plug-in for the browser that a hacked site fitted with an exploit kit can attack to install or drop a Trojan on your box without warning. The other, more common, scenario when people encounter rogue AV is when their systems are already infected with a bot, and the bot is being used as a vehicle to load malware that is spread by pay-per-install programs. I think the rogue av is probably far more commonly spread over hacked sites and javascript and/or iframes, but there you have it.
So, short answer, just after having narrowly avoided a scareware problem would be a great time to run a scan. I’ll feature a more thorough primer on how to respond to rogue AV attacks in a few days.
Whilst there’s no harm in running an AV scan of course it’s highly likely that attackers as sophisticated as this will crypt their files using private stubs – meaning no AV is going to detect it through signatures.
The best method is to avoid the infection in the first place – as Brian says, NoScript is your friend here.
^ If you weren’t pwnd by an exploit pack.
If you were, the FakeAV could be just one of the components the exploit kits multi-dropper runs for your pawnage pleasure… and possibly the only visible one.
On US and UK redirect to Fake scan an download fake av BestAntivirus2011.exe on Windows and
BestMacAntivirus2011.mpkg.zip (MacDefender / MacSecurity ) on Mac OSX
From Italy, Germany , France
Redirect to Blackhole exploit kit
Hey GmG, that’s pretty interesting information. Can I ask the source of that information you posted in your comment?
I test with some proxy server and different user agent
The fake scan on Mac OSX
https://imageshack.us/photo/my-images/842/cattura4d.png/
iFrames can also be managed with the NoScript add-on for Firefox (similarly to Java and Flash). Details here:
http://techpaul.wordpress.com/2008/11/07/how-to-block-iframes/
No Script is kind of a must…I’ve upgraded to Firefox 4, and still run NS as well as Web of Trust (WOT), which while flawed is better than nothing, and a program that allows me to open a Web window via a proxy server, which helps minimize the possibility of getting one of those pesky viruses.
It was one of those redirect-malware viruses that I had to manually erase and took the Draconian step of re-setting my Time Machine backups to avoid the possibility of keeping the malware in a hidden file. Granted, now I have to run through the three levels of ‘filtering’ to keep my Web image-surfing safe, but my Web moves SOOOOO much faster and smoother! (And I’m not a ‘tech genius’ by any stretch!
Bottom line: I switched to a Mac as Vista was being released, and I’m still glad I did. Sad that I’ve got to ‘armor up’ like I did with my ole PC, but those of us who were smart at least kept up old habits…and are glad we did!!!
Chuckster
I have Firefox with add-on = No Script.
When some site wants to run some script, I get to see list of names of the scripts, and if I unfamiliar with the names, I can back out of the site without the script running.
However, I imagine if a malware was to falsely use the name of a script which is familiar to me as a benign software, I could be spoofed.
I don’t understand why you’d operate in this manner TBQH. Unless you always stick to the same sites most script names are going to be unfamiliar.
I use NoScript with default settings of ‘block all’. If I can’t use a particular function or see a particular element that’s the only time I unblock a script. If there’s more than one script and I can’t figure out what allows the function or element I need then I go through the list and use ‘temporary allow’ until I find what I need to permanently unblock.
Also there’s no need to “back out” of a site, you can still view a page if there’s scripts you aren’t familiar with – they’re just prevented from running.
There is even more interesting scam
For ex., under disguise of attractive captchas, like keycapthca.com, to collect Emails for spamming from registration protected protected by captcha
There are some posts warning about it but in vain, for example:
joomlaforum.ru/index.php/topic,138180.msg882437.html#msg882437
due to massive publicity through social networks and forums
This happened to me earlier this week as I was doing a search on Google for “Shouting”. Several images were included in the text results and clicking on one of a guy shouting started this process.
I used the search results and initial stages of redirect to show my wife and son what this process looks like so they don’t start agreeing to everything the Fake AV tells them to do. Scanned computer afterwards just to be safe and it was clean.
We created a video showing the Google Image search leading to fake AV in action. It also shows the behavior of the fake AV software after it has been installed. The video, also available by searching YouTube for “royal pain stopbadware” is included in the following blog post:
http://blog.stopbadware.org/2011/04/29/fake-av-a-royal-wedding-present
As a Firefox veteran, of course I use NoScript at a “block all” default. I allow a script only with metaphysical certitude that it–and the site it’s on–are safe. I also use the WOT (Web of Trust) add-on–available for all major browsers–in Firefox. Not perfect (what is?) but, on a Google images results page, each image will display WOT’s green (safe) red (unsafe) or Question Mark (safety unknown) halo. Maybe Firefox’s not-yet-public add-on for dealing with this issue will be more effective. We’ll see. Meanwhile, for me, “WOT’s on first.”
I have a few questions, though. Seeing that WOT depends on humans to rate how clean/safe sites are, isn’t there a small chance that some of the bad images could escape their checks?
Also, wouldn’t HTML-based email also be susceptible to the same attacks, as they can pull the images/scripts off the bad servers when the emails are opened/read?
One good rule of thumb to use with site advisers, is to definitely NOT click on any link with the grey or questionable rating. If the site hasn’t been their long enough to be rated, the prudent surfer should ask themselves how bad they want to take the risk.
Concerned, as I said in my post: “Not perfect (what is?)…”
BTW, all software depends on humans. That’s why none of it is foolproof.
Brian, is this issue limited to Google? Do other image search engines such as Bing suffer from similar?
kaputt, album of the year
I found a couple interesting things when digging into some of the hijacked domains hosting the images:
1) The domains are left mostly intact, presumably to hide the exploitation from their owners. (I did notice a broken forum on one site, maybe the hacker closed the door on the way in.)
2) If you take the hosting domain and search for it on Google’s ordinary web search, the two I encountered were already flagged as malicious in web search. The image search, the primary vehicle for the threat, provides no similar warning.
That seemed like really puzzling behavior from Google. They apparently have the data on which sites are hosting these attacks, it’s available to their systems, they’re just not using it to inform users or lower search rankings. I cannot figure that bit out.
Actually, it does seem possible to click your way out of this scam. I tried out what happens if you click the OK or Cancel buttons (while running a Live Linux system, of course).
Just closing the page with the fake virus warnings is possible – you get an Are You Sure? confirmation page, that’s all.
If you click the Remove All button, it tries to get you to download a .exe file, and you get another confirmation message box for that.
Yes new controls are being included in the latest browser versions to deflect some of the vector controls; however you are still taking a big risk clicking anywhere on the desktop/page window/etc. instead of simply opening task-manager and ending the process.
Right clicking the task bar to select task manager has not been risky by what I’ve seen in my honeypot lab.
This happened to me tonight using my BlackBerry PlayBook. I clicked on a Google image page and got a small window that said ESET had detected problems on my PC and wanted to run a scan. The malicious URL was on freewebs.com – don’t recall the exact URL. I was searching for mourning doves. I don’t think the PlayBook Tablet OS with QNX can be infected with Windows malware but it startled me.
All smart phone and tablet operating systems are just as vulnerable especially if using flash/or if java is enabled. Whether you use a version of Chrome, Mozilla, or some cut down Windows browser does not make a difference.
Other browsers may not be affected however.
I tagged my first scam scan offer this morning on Bing. No matter if I clicked Cancel or X to close the page, the scan began without regard to my action. I opened that page several times to test all the possibilities. However, the scan began each time I clicked any option to abort.
I can see where this is going to trap a lot of users because we tend to trust sites that we visit often or have been using for a long time with no problems.
Very nice to know about. Thanks again, Brian.
I’ll be interested to try the add-on when it’s available — thing is, I use the Cooliris add-on to browse Google image searches (it’s *seriously* cool technology), so will likely remain un-notified of problems in advance.
I always use NoScript though, so that will help.
What baffles me is why browsers don’t allow you to disable onclose Javascripts (which is where this “attack” is wedged) or at least give you some way to override them by, say, double-clicking the close button. This would disable these browser hijack “attacks” immediately, without disrupting typical web applications in any way.
Regarding Chrome, the easy way out is to simply click on the tool icon, select Tools, then Task Manager. Select the tab in question from the list, and then click Kill. Note that because of the way Chrome firewalls things, this is quite safe, but you should probably exit Chrome and come back in anyhow after you do all this. Have I mentioned that I consider Chrome to be far more secure than any other browser available for Windows for a number of reasons, and that if you’re not using it for your routine browsing on Windows, you probably should? The only time I browse using something other than Chrome is for those very rare web sites that don’t render correctly in Chrome, but those are very few and very vetted.
Regarding NoScript, Chrome has something of the sort if you turn off Javascript, you then have to explicitly enable Javascript for specific pages. The issue is that this is annoying because most modern web sites incorporate content from multiple places. For example, my credit union’s online banking system is handled by a third-party provider, and displays in an inline frame. So to get my credit union’s online banking system to work, I had to pop open that inline frame in a separate window and click the exception icon for that site, too. For mundanes, that simply is not workable.
In short, I believe the proper fix is a browser fix, not a Google fix. This onclose browser hijack issue has been an issue since, like, forever — one of my first IT experiences was noting a sudden burst of load on our Internet connection, tracking it down to my boss’s office, and when I went there found that he’d been browsing porn and was in a situation where a porn site he was browsing had done it (trying to get him to buy a subscription to the pay section of the porn site), and me telling him to reboot his system to get out of it (HEH!). That would have been in, like, 1998 or so, Netscape 4.x. So you’re telling me that 13 years later, nobody writing browsers has figured out that, uhm, like, you have a problem with malicious websites that won’t let people out of them? YEESH!
Well ****, just went to verify I wasn’t full of beans and while the above worked on the Mac, it doesn’t work on Windows — apparently focus got hijacked too. So your suggestion of kill the browser from the Windows task manager appears to be the only one that works.
My point that this is a BROWSER problem, and is a long-standing one that has existed for literally over a decade, remains. Browser vendors simply do not have a security mindset, and when they do attempt to do anything related to security (such as Google’s disable-Javascript and site-by-site enable for Chrome), make it so awful and difficult to use that nobody will use it.
What is so AWFULL about NoScript? You browse almost without fear, once you go to a site, and you want blocked content you simply right click the page and select the process you want to unblock and whether to do it permanently or once; then you drive on. I’d say that has been one of the best things since sliced bread!
Avast has had an automated script blocker since the first v. 6. It has not failed me yet.
Absolutely. I’ve used it to successfully block infections on pages for years. One advantage it has over turning off Javascript is that it allows the user to turn on specific sources of JavaScript in a given page. This is important because, as one commenter noted, today’s web sites combine content from many different pages. I’ll admit some sites can be annoyingly hard to figure out what I can leave off and which providers I must turn on to see the content I want.
However, the benefits outweigh the detriments and I’ve noticed that I make these decisions in seconds now because I’ve gotten so much experience with the tool. NoScript is one of the few tools that make the POLA concept work successfully in the web browser. It’s best for Windows users to combine HTTPS Everywhere, Noscript, Adblock Plus, Flashblock, a good HIPS, and a backup strategy. This eliminates the vast majority of infections.
Definitely Nick P;
In-depth defense all the way! 🙂
I use separate Administrator and User accounts. Fake Anti-virus programs bounce off Limited User accounts.
I use SandboxIE. SandboxIE sandboxes internet browsing sessions. Fake Anti-Virus are trapped in the sandbox.
I use NoScript (with Firefox). Javascript is blocked by default.
These steps are easy to install. The result is carefree internet browsing. Novice users can live comfortably with these procedures and programs installed.
Stillfiguring, good for you. My point is that 99% of Internet users are *not* going to do what you recommend, because it results in inconvenience for them because most of the web sites they go to in real life — online banking web sites, social networking web sites, webmail sites, etc. — require Javascript to be turned on. And explicitly enabling Javascript for specific websites is inconvenient. So they’ll just enable it for *all* websites, and be done with it.
We must live in the world we live in, not the world we *wished* we live in. My point: Internet web browsers are broken to allow this kind of thing to happen. Saying that plugin this or disable that will stop it from happening is like saying that if I put a Hemi into a Jeep Wrangler, I can make the Jeep Wrangler go 120mph. Yes, it’s possible, but how many people are actually going to do that? We must live in the world we live in, not the one we *wish* we live in. Reality-based security is, alas, rarely encountered in the wild, which seems full of “security experts” recommending things that *WILL NOT HAPPEN* because they inconvenience users, rather than suggesting improvements to the underlying technology that will prevent (or at least allow mitigating) the issue *without* inconveniencing users. And then we blame the users for not following our directions that require them to click things in order to make the web sites they use every day work correctly again (things that they simply will not do — they’ll enable Javascript again, and be done with it), and the cycle repeats itself. We have the end users we have, folks. We don’t get to replace them with perfect automatons that will follow our directions like robots. Sorry. Real life doesn’t work that way. We need to fix the technology, not the users. Period.
Separate Administrator and User accounts are not an option, these are a necessity.
Using separate accounts prevents the vast majority of malware. Not all malware but most. I like to suggest 90%, but I made that number up.
Separate accounts is the standard use of computers. This has been the case for decades. In the case of a business environment, there is one guy who is the Administrator, all others are the Users. This has been the standard method for a long time.
Separate accounts are a small inconvenience, with huge benefit. My experience is that novice users have little problem using separate accounts. The problem is that novice users do not understand how to configure separate Administrator and User accounts on their computer. Once this simple procedure is done for them, there are few inconveniences.
Setting up separate Administrator and User accounts should be part of the initial setup of a computer. Microsoft should have led the users through this procedure, the same as many other setup chores. This should have been done long ago.
The inconvenience of being taken over by a Fake Anti-Virus vastly exceeds that of separate accounts.
Congratulations, you just supported my point, which is that we need to fix the technology to be secure, rather than expect end users to follow (to them) arcane directions that (as far as they can tell) exist only to inconvenience them. Remember, Dilbert’s “Mordac the Preventer of Information Services” is their opinion of IT. As far as they can tell, IT exists only to make their life inconvenient by making it difficult for them to do things that make perfect sense to them. We can force them to do things securely at work via locking down their workstations, but when they get home, they’re going to do whatever they do.
As for the notion that removing administrative access doesn’t inconvenience novices, maybe true — until they go to install software and wonder why it won’t install. “Novices don’t install software!” you say? Uhm, in what world do you live? Surely not this one. My mother’s five-year-old HP inkjet printer died. After consulting with my brother via cell phone while standing in her local Best Buy, she bought a new one and brought it home. Following the directions on the fold-out sheet that came with the computer, she stuck the driver disk into the drive. She got the privilege escalation dialog from Windows 7. She clicked “Yes” on it. The HP software suite loaded into the computer. She plugged in the printer when directed to do so. It Just Worked. And did not require anybody to give her arcane instructions directing her how to switch to a different account or anything like that. We’ve directed her to click “NO” on that privilege escalation dialog unless she is explicitly installing software from a trusted source (and gave her a short list of trusted sources — a driver disk for a new device being one of them). Thus far, it’s worked — no viruses. This is a case where, in my opinion, Microsoft arrived at the right compromise between usability and security. Which the Mordacs of the world need to pay attention to — sometimes the solution is to fix the technology, not to recommend arcane procedures that end users simply won’t follow once they get home to their personal computers. When was the last time *your* mother did everything you told her to do? Exactly.
I agree with your user assessment, which is why I setup a lot of things for them from the start. This eases them into the new reality. Then I add things to the defense as I see that they have learned this new reality and have come to see it as an improvement of the experience instead of an inconvenience.
I remind them of the fact that being taken over by malware far and above exceeds the inconvenience of good security practice and recklessness can only provide magnified grief!
Note that these days, windows should be able to get the printer’s driver (and scanner’s driver) online automatically, without using a web browser and without needing that vendor CD. The cd generally will install junk your mother won’t need (and which you won’t be able to trouble-shoot).
Being willing to accept that authorization dialog is of course somewhat scary. You’d have to be able to ensure your mother doesn’t have any open browser windows… Since Windows 7 groups windows together into a single icon per application, it isn’t too hard to manage.
The kids hit a MacProtector drive-by download via Google images this afternoon, thankfully even they were not fooled by the “security center”. I did manage to snag several copies of the malware zip “anti-malware.zip” and submit to VirusTotal. Only 7 of 42 had coverage this afternoon….
Using standard accounts and CCleaner has been the best fix for these annoying bugs, that I’ve found. Subsequent scans by several anti-malware/virus brands have confirmed the infection is long gone.
For I and my clients it is a quick end to the process with task manager and a cleaning with CCleaner – hardly a few seconds work – life drives on!
If someone was told there’s a minefield out there, and also the area where it was located, why would anyone choose to go through it anyway? ‘Don’t know, but they do.
Common sense dictates avoidance, at least – look for another way to get whatever it is you’re looking for. There are -always- alternatives…
> https://www.ixquick.com/
… until it calms down and they get a handle on fixing the problem.
.
Thank you for investigating this Brian.
I’m hoping Google is going to fix this soon.
That browser add-on is very promising.
Will you let us know when it is released?
I ‘ve read all posts but I didn’t see what is the solution if I have been infected by this malware?How this badware is acting,how to discover it in windows task manager processes,how to be sure that i’m infected?I’m using eset AV and I’m performing now scan on my pc but what if they still don’t have virus signature for that kind of malware?I clicked on google image search,and it started to open my adobe reader but I’ve closed it immediately by clicking on close button,not in task manager,yet my firefox was acting unusual ater that,more slower.Please tell me what this malware does?I don’t want to reinstall my windows if I don’t have to.Thanks in advance…
Dear nvinovi;
When it comes to scare ware an ounce of prevention can be worth a pound of cure. Keep in mind that some malware can morph during their life on your PC, so even if your anti-virus/malware detector finally gets a signature, it may not recognize the culprit. The following is what I do/advise for clients in these particular cases:
1. Never surf the web without using a standard account
2. Never click on an alarming pop-up scare ware – always end the process using task manager
3. Immediately clean all temp files, caches, and folders that could hold page downloads. I use CCleaner for this.
4. A blended defense is always better – so use a combo of one very good firewall, one good AV, at least two good anti-malware(AM), all with real time protection.
5. Some like to disable iFrames, java scripts, and flash in the browser controls, or use NoScript or Avast v.6 to block bad objects(scripts) on web-pages.
6. A good host file to block the malware from accessing a bad server to bring more malware into the attack. MBAM does this using different technology.
7. Don’t disable the UAC on Vista/Win7.
8. Use a web adviser to keep you from clicking on known bad links/pics, and that includes unknown links. Don’t click on them. WOT is popular for that.
9. Try Sinegubko’s add-on whenever he releases it for Mozilla/Chrome or whatever. WOT is almost as good an indicator anyway.
None of it is perfect, but for scareware, it is a good bet you will be covered.
Sorry for the typo novinovi; I forgot that you can keep applications like Adobe, or Foxit(better for PDFs), and other programs updated, by using at least something like File Hippo’s Update Checker, or better yet, also use Secunia PSI, to find vulnerable applications or apps that have ended service life and update, or uninstall them to hopefully close the holes malware look for when they try to pwn your computer!
Hope this doesn’t leave you with your head swimming like it does many of my clients! 😉
All AV packages today have varying levels of heuristic detection as well as signature based detection. If you ask me all AV packages should be suspicious of an encrypted binary. Why do they need to use encryption in their install binary for? eset’s Nod32 is one of the best at doing heuristic analysis. But go look at all of the other execellent remarks here (NoScript added onto Firefox, et al) because you don’t want to dump it all on the AV program. Some of these other things or my PAC filter that blocks on high probability malware hosts can help prevent you from getting infected in the first place.
Thanks JCitizen for your advices.I guess it’s late to prevent since I have been already redirected on some /cgi based site.I did full AV check after that,it cleaned some trojan entries but I guess they were not from that latest attack.I don’t know what else to do now,that’s why I would like to know how this malware will perform,what it will do,so that I could recognieze that process and to be sure that windows is infected.I didn’t saw any pop-ups on that site,and I didn’t even opened it fully,only my adobe reader started to opening but i terminated it immediately.I saw that some removal tools for fake AV are available on the internet,trendmicro’s removal kit for example,but how can i be sure that it’s for this type of malware.Does anyone knows how this malware is acting in the system,how to recognieze it?
If you had an active scareware malware on your PC you would know it for all the popping up and messing with everything you tried to do. If it were one of the powerful ones that inject a .bat file and take over your computer administratively, you would see things like your anti-malware being disabled or literally uninstalled, and/or you wouldn’t be able to run task manager or other mitigation tools in control panel, for example.
I would say you are fine as long as you scan with everything you have regularly for a week. Eventually the definition will come for the bug. It is better to have the attitude that you are already been monitored by one kind of malware or another, and use utilities that run in an infected environment. I was lucky enough as a CNET subscriber to get a free install of a new Emisoft utility called Namutu, that is strictly behavior based, and does not use signatures. I was amazed that, within seconds, it found nearly everyone of the DRM modules that legally spy on me for cable and blu-ray content. It quickly disabled them, and I had to configure them as unmonitored for that functionality at least. This one probably is a trial offer now, so you will have to pay for it later if you find it useful. Some folks like to use the free version of Win-patrol to see what is trying to get into their start up folders, or is already in the startup folders. This should theoretically work whether the AV/AM detects it or not. If you don’t recognize the process running then you have a problem. Using the free tool from Microsoft called autoruns can help you nab unknown processes – downloaded here:
http://technet.microsoft.com/en-us/sysinternals/bb963902
It will be a steep learning curve to master what is a good or bad process, but unknown processes are definitely suspicious – Google is a big help on determining which are those.
Brian & Chrome users:
With growing interest & use of Chrome (now focused for hacking) browser, it should also be bolstered with “NotScript”…making it similar to Firefox & NoScript.
http://www.ghacks.net/2010/08/18/notscript-brings-noscript-functionality-to-google-chrome/
Also, it helps to turn off 3rd party cookies: Chrome> wrench icon> Preferences> Under the hood> Content settings> Cookies (heading): tick “Allow local data…” & “Ignore exceptions and block 3rd party…”> close tab.
Chrome already has something similar to NoScript, though without the abiity to select which exact scripts you’ll run on any given page. Chrome->wrench icon>Preferences/Under the hood>Content settings>Do Not Allow Any Site to Run Javascript.
When you visit a site that has JavaScript, you’ll then see a small icon appear in the right of the URL box with a red line across it. You can click this icon to re-enable Javascript for just this URL, if you so desire. You will then have to refresh the page, at which point the scripts on that one page will run, and will continue to run on later visits to the page or site (if you define the exception accordingly in the Content settings).
Thanks again JCitizen.I will try autoruns tomorrow.I just don’t understand how serious is this new threat about re-directing from google image search.If it’s some small scareware,or hidden monitoring process in background I don’t mind that much since I don’t have anything to hide.I hope it’s not something more serious.BTW,I was always wondering who are those people who are doing all this job with creating this kind of malware,creating so many false websites, etc…What is the purpose of doing that?To steal credit cards’ codes,invading e-mails or what?All that work and obvious knowledge wasting just to get some amounts of money which they could earn on legal way…
As long as you don’t click to install anything you should be okay. Yes, it’ll run a fake “scan”, but the “scan” is fake — it doesn’t actually do anything to your computer. What does something to the computer is at the end of the “scan” when it says it’s found all these threats, and install this software to remove them. The software to “remove” the threats instead makes your computer do crazy things until you enter your credit card information for a “for-pay” “removal” tool. At that point they have your credit card info. They might actually provide you with a tool that makes your computer quit acting crazy. Or maybe they don’t bother. They have your credit card, after all, and that’s what they were after.
As for who is doing it, generally Eastern Europeans. There are few opportunities for legit IT work there and a whole industry has arisen there to do this kind of thing.
But as I’ve repeatedly pointed out, this shouldn’t even be possible in the first place. I first encountered these particular kinds of attacks over ten years ago, in the context of fake porn sites. Maybe as long as they were restricted to fake porn sites nobody cared to fix the underlying problem, which is JavaScript features that allow web applications to hijack browser window close? Hmm…
Good posts ELG;
@novinovi; for me, it is enough to simply end the task using task-manager and run CCleaner to clean out temp files, caches, and other folders that they get into; and of course being as I am on the standard account most malware can’t take anything over as long as I don’t click on it.
Keeping the vulnerability profile lower definitely lowers this possibility also. I haven’t run into a fake scan for quite a while on my honeypot, so the successful ones must be getting fewer for those that run a good in-depth defense.
I got one today in an image supposedly from stocks2boom.com and got the OS-X image about viruses, etc. shown by GmG, which by the way don’t go to the link GmG has on the post, it goes to a Website the pops up a window you can’t close without clicking “Ok” to download some sofware. You have to (force) quit Safari to remove them. Someone should remove the link and probably the user for posting it.
This rootkit is getting pretty gnarly. I get 4-5 of these a week at my small shop and I’ve even seen it a few times on Win7 64bit. I have developed some tricks to remove it over time and I know from experience that attempting to use multiple accounts/plugins/add-on’s don’t work for the average person from a useability stand point, so I don’t even bother recommending them. I end up getting more calls from the restrictions than I’d get if they were re-infested. On the front lines there is no way we could keep up if private tool developers weren’t playing their part. AV developers are either lost or intentionally hamstrung.
I blogged about general removal tips for anyone interested found over here ..http://blog.kitrx.com/2011/05/instructions-removing-win7-antivirus-or.html
Dear Johnny K;
Plug-ins and addons are definitely up in smoke with the new browsers for now; but I rarely get calls from any client that uses standard accounts. Maybe because I give them a simple security primer before giving the PC back to them.
The biggest problem right now is Win7 and their updates on OEM machines. I’ve suddenly jumped 1000% in my work load, and Redmond is usually the only one that is likely to fix many of the problems.