An explosion of online fraud tools and services online makes it easier than ever for novices to get started in computer crime. At the same time, a growing body of evidence suggests that much of the world’s cybercrime activity may be the work of a core group of miscreants who’ve been at it for many years.
I recently highlighted the financial links among the organizations responsible for promoting fake antivirus products and spam-advertised pharmacies; all were relying on a few banks in Azerbaijan to process credit card payments.
In this segment, I’ll look at the personnel overlap between the fake AV and pharma industries. The data is drawn from two places: a study done by researchers at the University of California, Santa Barbara (UCSB) that examined three of the most popular fake AV affiliate services which pay hackers to foist worthless software on clueless Internet users; and the leaked Glavmed/Spamit affiliate database, which includes the financial and contact information for many of the world’s top spammers and hackers.
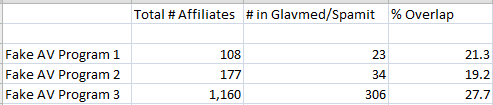
UCSB researcher Brett Stone-Gross and I compared the ICQ instant message numbers belonging to affiliates from Glavmed/Spamit with the ICQ numbers used by affiliates of the largest of the fake AV programs measured by his research team. The result? 417 out of 998 affiliates who were registered with the fake AV distribution service — a whopping 42.2 percent — also were registered pharma spammers with Glavmed/Spamit.
Unfortunately, the other two fake AV affiliate programs had not stored affiliate ICQ numbers in their databases, so we needed to find another basis for examining users of these programs. Instead, we looked for common email addresses among affiliates of the three fake AV programs and for affiliates of Glavmed/Spamit. This is almost certainly a conservative measure of overlap, because miscreants tend to change email addresses more frequently than they adopt new ICQ numbers. Even so, we found that the rate of email address overlap was high, between 19 and 27 percent across all programs:
STRADDLING BOTH WORLDS
A textbook example of this overlap was a key Spamit member, a hacker named “Severa.” Prior to Spamit’s shutdown in September 2010, Severa was a moderator of the “spam” section on the site (like most cybercrime forums, Spamit had sections dedicated to a range of criminal enterprises).
 Severa is short for “Peter Severa,” a Russian who is listed at #5 on Spamhaus‘s Register of Known Spam Operations (ROKSO). According to Spamhaus, Severa is one of the longest operating criminal spam-lords on the Internet. Severa advertises his spamming services on several invite-only cyber crime forums.
Severa is short for “Peter Severa,” a Russian who is listed at #5 on Spamhaus‘s Register of Known Spam Operations (ROKSO). According to Spamhaus, Severa is one of the longest operating criminal spam-lords on the Internet. Severa advertises his spamming services on several invite-only cyber crime forums.
Until last month, Severa ran a fake antivirus distribution affiliate program called Sevantivir, which seems to have counted among its ranks a large number of Glavmed/Spamit members (Sevantivir is not one of the three fake AV services included in the UCSB study).
It appears that Severa has been using his fake AV affiliate program to generate new infections for the botnet that powers his spamming service. Last month, I reached out to French security blogger Steven K., after reading one of his posts about a different fake AV affiliate program. I showed Steven an easy way to obtain a malware download from the Sevantivir affiliate Web site, and he spent the next couple of days studying the malware.
 Steven discovered that the malicious installer that Sevantivir affiliates were asked to distribute was designed to download two files. One was a fake AV program called Security Shield. The other was a spambot that blasts junk email pimping Canadian Pharmacy/Glavmed pill sites. The spambot is detected by Microsoft’s antivirus software as Win32.Kelihos.b. According to Microsoft, Kelihos.b shares large portions of its code with the Waledac worm, an infamous worm that for several years was synonymous with Canadian Pharmacy spam.
Steven discovered that the malicious installer that Sevantivir affiliates were asked to distribute was designed to download two files. One was a fake AV program called Security Shield. The other was a spambot that blasts junk email pimping Canadian Pharmacy/Glavmed pill sites. The spambot is detected by Microsoft’s antivirus software as Win32.Kelihos.b. According to Microsoft, Kelihos.b shares large portions of its code with the Waledac worm, an infamous worm that for several years was synonymous with Canadian Pharmacy spam.
Microsoft targeted the Waledac botnet last year in a sneak attack on its control infrastructure. Microsoft does not consider this Kelihos.b worm to be in the same family as Waledac, as claimed by some researchers. Microsoft states: “Based on our analysis, we have classified this as a new family and not a variant of Waledac. It is important to note that this new family is not communicating with nor is it reactivating the original Waledac which had its command and control infrastructure neutralized last year.”
Stay tuned for the final story in this series, which will look at how recent events have impacted the fake AV industry.




We will stay tuned !!!
Brian,
A nice piece of work so far and I look forward to reading the rest.
Of the few ways of dealing with crime and especialy cyber-crime is to get good intel on the criminals involved, The first step of which is to get a good overview.
Hopefully this will encorage others to get intel on cyber-criminals so that “the powers that be” might just be persuaded to get their acts together without shouting about cyber-war.
Wow, that is some pretty damning evidence really isn’t it.
Upon reflection I’m not all that surprised though I guess – once they have payloads installed it makes sense to maximize each installation for maximum profit – just like any business I might add and no I’m not implying legitimacy but from many previous articles here it’s clear that these operations are run like a legitimate business as far as operations go.
Anyone else have a little wince (chuckle … sigh?) when they noticed this Peter Severa character has named his fake AV Sevantivir ? Guess that illustrates yet again how impervious these folks are or consider themselves.
Still, there’s hope: people sometimes make mistakes and reveal themselves – remember how the Mariposa botherder got identified.
I really don’t like the implication that the “powers that be” get their act together…I really don’t think turning our computers over to the government is going to mean anything in terms of security. Case in point, the new FFIEC guidelines that were released concerning Online Authentication has gone over the regulator’s heads, except states like TX who have their “act” together, and most states have told me its either NOT a priority or they are just going with whatever the feds say is ok. Its really just another game of the blind leading the blind….banks and banking customers are the ones who are going to feel the bite, and the government can’t wrap its tiny pin-like head around IT security….
So relying on the government for security in IT is like relying on the government to keep our borders secure.
Jacob,
Hmm not quite sure where you are comming from.
My comment was in refrence to the likes of Law enforcment. For various reasons they take the attitude that this type of Cyber-Crime is not worth investigating.
It appears to be that either the individual dollar value of a crime or the fact that it is cross jurisdictional appears to be a major impediment to starting an investigation.
However if you look at this work by Brian and others it quickly becomes clear that not only is it serious crime it is also organised crime and probably covered by various racketeering statutes.
So this sort of intel (if considered valid by LEO’s/judges) compleatly changes the game play that LEA’s take…
Good work Krebs – you are going to do more to fight malware than the anti-viruses!
I have been reading Xylibox for months now, isn’t Steven great? I was happy to see you working with him.