Criminals who operate large groupings of hacked PCs tend to be a secretive lot, and jealously guard their assets against hijacking by other crooks. But one of the world’s largest and most sophisticated botnets is openly renting its infected PCs to any and all comers, and has even created a Firefox add-on to assist customers.
The TDSS botnet is the most sophisticated threat today, according to experts at Russian security firm Kaspersky Lab. First launched in 2008, TDSS is now in its fourth major version (also known as TDL-4). The malware uses a “rootkit” to install itself deep within infected PCs, ensuring that it loads before the Microsoft Windows operating system starts. TDSS also removes approximately 20 malicious programs from host PCs, preventing systems from communicating with other bot families.
In an exhaustive analysis of TDSS published in June, Kaspersky researchers Sergey Golovanov and Igor Soumenkov wrote that among the many components installed by TDSS is a file called “socks.dll,” which allows infected PCs to be used by others to surf the Web anonymously.
“Having control over such a large number of computers with this function, the cybercriminals have started offering anonymous Internet access as a service, at a cost of roughly $100 per month,” the researchers wrote. “For the sake of convenience, the cybercriminals have also developed a Firefox add-on that makes it easy to toggle between proxy servers within the browser.”
The storefront for this massive botnet is awmproxy.net, which advertises “the fastest anonymous proxies.” According to Golovanov, when socks.dll is installed on a TDSS-infected computer, it notifies awmproxy.net that a new proxy is available for rent. Soon after that notification is completed, the infected PC starts to accept approximately 10 proxy requests each minute, he said.
“For us it was enough to see that this additional proxy module for tdl4 was installed directly on encrypted partition and runs thru rootkit functionality,” Golovanov told KrebsOnSecurity. “So we believe that awmproxy has direct connection to tdl4 developer but how they are working together we don’t know.” The curators of AWMproxy did not respond to requests for comment.
The service’s proxies are priced according to exclusivity and length of use. Regular browser proxies range from $3 per day to $25 monthly. Proxies that can be used to anonymize all of the Internet traffic on a customer’s PC cost between $65 and $500 a month. For $160 a week, customers can rent exclusive access to 100 TDSS-infected systems at once. Interestingly, AWMproxy says it accepts payment via PayPal, MasterCard, and Visa.
Awmproxy.net currently advertises more than 24,000 proxies for rent. The number of available proxies varies greatly from day to day, even within a single 24-hour period. That’s because the TDSS-infected systems aren’t always turned on: Their legitimate, oblivious owners sometimes turn their PCs off at night and on weekends.
This is explained in AWMproxy’s FAQ:
“Q: Today quality/speed/number of proxies decreased, can you do something?
A: There are time periods when the proxies quality, number and speed decrease, and we are really unable to help it much as we would like to. It is impossible to provide the same number of proxies in the day time and at 3 a.m. The same is true for weekends.”
The renting of hacked PCs for anonymous surfing is only one of the many ways the TDSS authors monetize their botnet. In a blog post published today, Golovanov discusses how TDSS is being used for mining Bitcoins, an electronic currency.
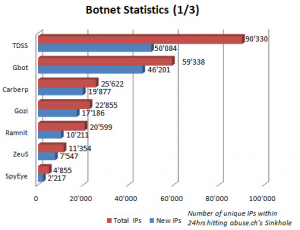
Statistics collected by Abuse.ch, the curator of ZeuSTracker, show how TDSS stacks up against other bots.
Other researchers have been exploring the activities of a new TDL-4 variant that uses infected PCs for a massive click fraud operation. Joseph Mlodzianowski, a malware researcher who blogs at sub0day.com, found that machines infected with this new version periodically download “campaign” files, listings of Web sites that botted systems are instructed to visit, apparently to generate ad revenue for the targeted sites.
“What I think they’re doing is renting to these sites the ability to have people visit them so they can get paid for display ads,” Mlodzianowski said. “A campaign file is a list of about 15 sites. The [bots] don’t hit just one page, they crawl through and visit two to three pages on each site, so it looks like a real user is doing that. All of this happens so that it is invisible to the user.”
It’s not clear yet whether the fraudsters running the TDSS botnet operate a similar public storefront for click fraud clients. But it’s remarkable that those responsible for TDSS feel so invulnerable that they are comfortable advertising their work in such a public fashion.
Update, Sept. 9, 9:28 a.m. ET: Check out the follow-up post to this article, Who’s Behind the TDSS Botnet?, which follows a trail of digital clues that lead back to an individual who appears to be closely tied to this criminal operation.




I find it amusing that there is a bank that processes MC & Visa payments for the access to hijacked PCs. PayPal as a method payment is also quite funny. Hopefully someone will do sting purchases and these billing methods will be shut down now. This crap should only be purchasable with crime-friendly payment methods like LR or Bitcoin.
🙂 They also take Webmoney and Liberty Reserve.
ah, yes, I forgot WM as another crime-friendly payment method 🙂
These botmasters may have a high profile in the malware market, but to ordinary websurfers and the Mainstream Media they’re nonexistent. These are the kind of WWW crooks well loved by the government of Mother Russia, which used their services during the attack on Estonia and the war with Georgia.
Does anyone believe that FSB or any other Russian law enforcement will arrest, let alone convict these miscreants as long as they pay their bribes and don’t attract mainstream attention?
We had a laptop at our place infected with TDSS/TDL4. It managed to survive a complete wipe & reimage of the laptop in question. First time I have ever seen that!
It may be worth adding to your article that Kapersky supplies a utility to locate and remove this nuisance – TDSSKiller. It did the job nicely for us.
http://support.kaspersky.com/viruses/solutions?qid=208283363
Thanks, Tim. I had meant to add that in the original version of the story. Perhaps I still will.
It’s worth noting that the research on the Tld-4 variant discussed at the end of this blog post says that removal tool does not detect/remove this latest variant, although that will likely soon change.
Apparently it already has as this page indicates it removes TDL4:
http://support.kaspersky.com/viruses/solutions?qid=208280748
John – You may be right. I’m just repeating what the researcher said in his blog post, linked in the story above:
http://sub0day.com/?page_id=2
“This Stealth trojan malware (TDL4.2) uses the victims computer to browse websites with out any signs. It doesn’t display the common browser redirects or annoying popups, which normally alert users to the fact that they are infected. TDL-4 is detectable and can be removed by Kasperskys TDSS Killer, however, this variant will download and update itself becoming undetectable. [At least for a while]”
Only one person really knows for sure…whoever has written the latest version of TDSS.
Tim – Is it possible that the image contained the rootkit so when you did the reimage you placed it right back onto the wiped drive?
If I understand properly how TDSS works, it writes itself to the tail end of the master boot record (MBR), which — depending on how you format a machine — may not be touched by a reinstall of the operating system.
No – our image is rock-solid.
As Brian notes, this devious malware infects the MBR so our standard re-imaging process did not touch it. As soon as the standard image was reloaded and added back to the LAN, the malware was off & running again.
It’s worth noting that the way we noticed this malware was by reviewing our proxy/firewall logs. I get a weekly report showing all communications from internal endpoints to known (or suspected) malware domains. the domain looked suspicious to me and a few minutes research showed that it was indeed a known TDSS C&C server.
Reviewing logs can be a tedious process…but it’s an essential part of the ‘defence-in-depth’ approach.
Would the rootkit survive if you did a fix MBR or restore MBR command?
I theory, yes, that should work. However, blowing away the MBR and writing a new one would be safer, IMHO, as long as you’re reinstalling.
One of the things I’ve always loved about Acronis True Image is the ability to boot from a recovery CD and re-image just the MBR.
I guess I’m assuming you would have pulled the HD and attached it to another system via an external drive then deleted the partitions and then formatted the drive. Wouldn’t that wipe the MBR out completely so you’d be starting fresh?
MBR is at track0, sector0 and is 12.5% of the HD space created when the drive is initialized. Formatting does not write a new MBR. The MBR is backed up and some fixes attempt to replace the infected MBR with the backup. Seldom works.
Use a zero-fill utility (killdisk, etc.) to write zeros to entire disk surface before reinstalling. Single pass OK, more passes better.
Avast aswMBR can detect TDS and repair the MBR (uses Gmer technology. Worked once for me but didn’t cure entire infection. Zero-fill, reinstall.
Brian, I have received 2 (bogus) notifications about new comments to the bank fraud in Pittsfield NY:
************
There is a new comment on the post “FBI Investigating Cyber Theft of $139,000 from Pittsford, NY”.
http://krebsonsecurity.com/2011/06/fbi-investigating-cyber-theft-of-139000-from-pittsford-ny/
Author: Celesta Delio
Comment:
i awesome post. i will come back. thank you pal
************
However, there is no such comment (in either of the 2 notifications I received.) Are you deleting the comments or is there something nefarious going on here?
Eric,
Thanks for subscribing. My apologies. The blog spammers have really stepped up their attacks on my blog, and I’m working hard to keep them from abusing my site’s reputation. Sometimes, spammy comments slip through the net, though, and I always delete them as soon as I notice them.
Heh … that’s pretty amateurish as far as link spam goes.
Many marketers use far more sophisticated methods that make automated posts that many webmasters would be hard pressed to mark as spam and therefore provide the all important anchored backlink that lives a long time.
For example one can use a program such as Scrapebox to search for blogs using whatever keyword is being targetted, scrape tweets filtered using the keyword using a program such as TweetAttacks and then post the tweets. Done right this method leads to ~80% of links being there in 3 months (ie. not deleted as spam) and often higher rates if one simply uses a trending topic in Google and hits blogs that are following the trend with Tweets.
Actually sometimes this can lead to posts that are actually genuinely useful which leads me to question whether they can be called spam in the first place despite being an automated process.
And that’s just one way of doing it …
Given that they claim to accespt Visa and Mastercard, if law enforcment was so inclined, they could buy the product, check their Visa bill for the merchant id, provide that info to Visa to have that merchant and all related blacklisted. They could also track the bank acocunt into which the merchant id is funnelling the cash, sieze it or monitor withdrawals, follow the mule to the owner of the account and thus the botnet.
Also this could be done through civil suits and subpoenas if a victim were to file suit
Hey EJ, are you still involved in battling click fraud? I’d be interested in your thoughts on that aspect of this botnet.
I am still involved as “click fraud ” is one of the ways hackers profit from stolen data. The term click fruad only related to cost per click campaigns, the real money is int he Cost Per Acquistion fraud.
Im over simplifying this but, in short a hacker gets stolen credit cards and info. then he partners (I say partner because he is unlikely to be able to be an affialite himself) with a CPA affialite and drives traffic to the affialites link on various offers.
The affiliate will be paid a commission ranging for $.25 to $40 per sign up/acquistion. The partners share the profit.
But, if all the traffic comes from the same IP most affilaite networks are smart enough to see that it is fraud. Now some will wait for the advertiser to complain because the affiliate network is also paid based on the traffic and cpa. But the legit ones like Epic Media Group (full disclosusre EMG owns my firm Online Intelligence) actually block/void the traffic and payment to the affialite as soon as the pattern is detected.
Enter the botnet, hacker/affialtie will run traffic through the rented/owned botnet so the IPs, browser data and other tell tales are gone and thus the fraud is not detected by those groups without a skilled anti-fraud/anti-abuse team.
So I run through 50 botnet IPs at $30 per sign up (CPA) = $1500 and the cost for the rent is $300 a month? I like the $1200 profit. Best par tis I can do this with 100 stolen identities/cards or 100,000
Sadly very few LE investigators know truly how hackers/ malware/phisher/botmasters profit from their trades.
Its a complicated process but once you see the pattern its fairly easy.
Fascinating article. How do the botted systems perform the clickfraud within the client browser without the end user seeing this?
They’ll using something like wget or curl to request the pages and “click” on the links. No need to involve the end user’s graphical browser.
I haven’t actually looked at how they’re doing it.
However, most browsers are pluggable, which means there are a number of ways they *could* do it.
Among them:
1. Most browsers support NPAPI [1] (the original “plugin” API) (the exception is IE which uses ActiveX [2]).
2. Most browsers have an extension model (for IE this is called BHO – Browser Helper Object [3], for Firefox the equivalent is roughly xpcom extensions [4])
3. Most browsers have a way to add toolbars which rely on their extension model.
4. On Windows one can register to be a Windows LSP [5], in theory you’re claiming to help with network connections to interesting things (NetBIOS/NetBUI, whatever).
5. One can also be truly evil and just use DLL injection [6] — this was definitely done by viruses at some point in time, but if you want to target browsers you can use any of the other techniques instead.
Most of these will eventually result in a DLL [7] being loaded, in the case of plugins this might only happen if plugin scanning is triggered, but typically the others happen roughly during browser startup.
Note that browsers have started taking action to prevent some of these things (especially LSPs, since ignoring the malicious ones, many are just plain crashy). There are also techniques to try to lock out unsigned libraries (Google bought one of those vendors), unfortunately, some of Microsoft’s libraries aren’t signed (typically these are shim libraries as opposed to the real libraries, but if you need the shim, you’re in trouble if you don’t load it)* [or weren’t signed when I looked 2 years ago]. But again, if your system is 0wned, then a browser really can’t defend itself against attack.
When a DLL loads, it typically gets a DLL_PROCESS_ATTACH [8] message. Roughly around this time, the library can create a thread [9]. In the thread, the code can then do whatever it wants to do. This has relatively minimal affect on the Browser itself, but it means that the code is running inside the browser. If the Browser has enough threadsafe APIs, then it’s possible for the thread to safely access and use cookies and other credentials (or ask the browser to make a request, this is more or less how XMLHttpRequest[10]s work — although browsers generally have APIs for making direct requests too). If not, then the code might need to send messages to some other thread asking it to do the work (this is perfectly legitimate, and since it *is* the Browser, there’s no reason for the browser not to trust it). Remember that we’re dealing with malicious code, so it’s possible for the code to take shortcuts if it wants to, it could for instance try to read data directly instead of using APIs, as long as it’s relatively careful, it could get relatively good data most of the time, and that might be sufficient for its purposes.
This of course assumes that someone wants to bother to do the work of living inside a browser. Keep in mind that the article describes a vendor who was willing to write a Firefox extension for procurement purposes, which means they are willing to do some of this stuff.
Once could simply try to do reads against the file system to get rough cookie/password/cache data. It’s less reliable, and might be more prone to breaking, but for most purposes it probably doesn’t matter what technique one uses. As long as the code doesn’t crash (because one doesn’t want the user to notice), some slightly bad data shouldn’t negatively (the definition of “negative” here is “show up in logs as surprising and trigger an audit”) affect the results that the targets (i.e. the web sites who are being “clicked”) see. — but someone already mentioned curl/wget, so talking about that would be a duplicate.
[1] http://en.wikipedia.org/wiki/NPAPI
[2] http://en.wikipedia.org/wiki/ActiveX
[3] http://en.wikipedia.org/wiki/Browser_helper_object
[4] http://en.wikipedia.org/wiki/XPCOM
[5] http://en.wikipedia.org/wiki/Layered_Service_Provider
[6] http://en.wikipedia.org/wiki/DLL_injection
[7] http://en.wikipedia.org/wiki/Dynamic-link_library
[8] http://msdn.microsoft.com/en-us/library/ms682583%28v=vs.85%29.aspx
[9] http://msdn.microsoft.com/en-us/library/ms682453%28v=vs.85%29.aspx
[10] http://en.wikipedia.org/wiki/XMLHttpRequest
ooh, this got an awaiting moderation. Brian: is that because I included too many links, or because of the aforementioned spammers which caused you to switch to moderating all comments?
I’d rather not say why it got moderated 🙂 But yes, having a metric ton of links in a comment tends to spook the system. It’s approved now.
Yeah, sorry, I wouldn’t want you to disclose the details :). The question was written because I knew it would work as an automatic test (and there’s no harm in it being down-modded). I switched to [] urls because each time I try to post inline urls, I use [lt]url[gt] which triggers some filter which eats the url resulting in poor articles — I really could use a “preview” option.
I need to find a site that uses http://wordpress.org/extend/plugins/live-comment-preview/ so I can find out if it would solve my problem :).
Re: the user not seeing the clicks. Many ways have been provided above but since the broswer/user agent is often collected by the anit-fraud teams at the affiliate networks, the browser is actually opened in a 1×1 pixel window (some times as a mobile emulator). The malware opens the window shrinks the size (not minimize) clicks thru and inputs the information on autoform fill then closes the window. The time of “opening” varies and most users would not notice the open window unless they specifically look for it in taskmanager or under the windows tab.
Another way is to route all requests thru another site and then falsify the pakets being sent with the traffic but this can be highly complicated and often throws up red flags for the compliance teasm if they know what to look for…
Here’s the link to a direct download of the ZIP file containing the rootkit killer:
http://support.kaspersky.com/downloads/utils/tdsskiller.zip
— timeless
Seriously? Did you even bother to read what drzauisapelord wrote? He wrote it like 3 hours before your post.
I don’t know if you wrote all of that crap because you like to “hear yourself talk” or if you actually believe you know what you’re talking about…. lol.
Dude, malware as sophisticated as this (it removes over 20 competing viruses!) isn’t gonna use any crappy / clumsy methodology like all that blathering you went on about. All they have to do is set up a simple proxy server on the infected host and that’s it. It’s not the browser that the botnet is after, moron, it’s the IP address / internet connection.
It seems that TDL4 author does not stop improving it. Kaspersky issues an update to the tsskiller tool every week (sometimes even twice). The bad thing is that TDL4.2 does not give you a clue that you are infected – no redirections, nothing. Hmm, scary in fact.
As always – perfect article Brian, keep it going!
Read “Fatal System Error,” and you’ll see *why* they feel invulnerable.
Is there any particular reason why genetically cyberciminal countries, like comminust China, Brazilia, Nigeria and Russia (better the entire ex-USSR) should be tolerated on the US-invented net?
The USA Navy has the special ops submarine and ROV capability to sever undersea cables. The free world should send the russkies back to the abacus age, the tool which they used during communism to count in shops what they did not have on the shelves.
They do not deserve the computer and the Net and there is no God-given right for tyranny-loving, born criminal nations to enjoy and abuse the net. There is no need for the net to buy russian oil, gas and ore, the fax will suffice and they have nothing else to offer.
Why do we allow Red China to hack away and steal all of USA’s industrial and military secrets? Why not sever their undersea net links and send them back to the bamboo paper based bureaucracy era, which so effectively held their large country in stagnation for many centuries.
The developed, civilized countries must keep the Net for themselves and the scum who are not worthy of it, shall be expelled.
Why do Americans allow criminals to infect our computers? In most cases, the users could have avoided it by being better trained at recognizing fraud and/or by being more responsible about running antivirus/antimalware programs.
Why do we allow ISPs to have users with infected computers on high speed internet connections providing a US springboard for Eastern European and Asian criminals? Rather than seeing their proliferation as cause for alarm, ISPs seem to regard it as a reason to consider disinfecting them all as a hopeless task.
You can cut all the cables you want, but half the problem is on this side of the oceans.
I agree, I’m having visions one day of a network that can’t be accessed unless countries pull their weight in law enforcement. Not enough questions were asked or thought of in the early 1990s when the WWW was being pushed out into the world.
Typically I ignore trolls, but I will make an exception for you. The simple truth is that cybercriminals constitute a very small share of any country’s population and therefore the idea of cutting off the countries just because certain (very small) percentage of population is engaged in cybercrime, is absurd.
Good luck debating that!
http://zapatopi.net/afdb/
IIRC, if you cut the cable to China, you’ll lose Australia and New Zealand, too.
You just now learn AMS is TDSS?
Brian, you are slacking! =)
“… this additional proxy module for tdl4 was installed directly on encrypted partition …”
Would this partition show up in the Windows disk mgmt module the way Truecrypt partitions do?