Computers running Microsoft‘s antivirus and security software may be flagging google.com — the world’s most-visited Web site — as malicious, apparently due to a faulty Valentine’s Day security update shipped by Microsoft.
Not long after Microsoft released software security updates on Tuesday, the company’s Technet support forums lit up with complaints about Internet Explorer sounding the malware alarm when users visited google.com.
The alerts appear to be the result of a “false positive” detection shipped to users of Microsoft’s antivirus and security products, most notably its Forefront technology and free “Security Essentials” antivirus software.
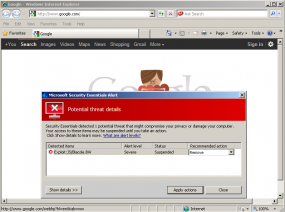
I first learned of this bug from a reader, and promptly updated a Windows XP system I have that runs Microsoft Security Essentials. Upon reboot, Internet Explorer told me that my homepage — google.com — was serving up a “severe” threat — Exploit:JS/Blacole.BW. For whatever reason, Microsoft’s security software thought Google’s homepage was infected with a Blackhole Exploit Kit.
I could be wrong, but it doesn’t appear that Google is in fact infected or serving up exploits. Fortunately, clicking the default “remove” action prompted by Microsoft’s antivirus technology did virtually nothing that I could tell; the program reported that it was unable to find the threat (psst, Microsoft…that’s because there isn’t one). Judging from the responses in the Microsoft forum, the company appears to be aware of and responding to the bogus alerts.
False positives happen to every antivirus vendor, and this one was fairly innocuous as these things go: It’s not like it deleted or quarantined essential operating system files, rendering host computers useless, as faulty updates from other vendors have in the past. But Microsoft is probably smarting from this episode: The company is expected to ship a version of its antivirus technology with Windows 8, the next version of Windows due to be released later this year.




I just went to google.com in IE9 and got the MSE alert.
I was on my netbook and on Google using IE9 and got the MSE prompt but I thought it was coming from another site.
Now I’m on my desktop and on Google with IE9 and MSE alerted me. I wonder if it might be IE and not MSE? Since Chrome and Google don’t prompt and MSE alert.
The same thing happen to me in my PC.
Microsoft has confirmed the issue, per http://isc.sans.edu/diary.html?storyid=12589&rss –
“UPDATE: As of 20:11 GMT-5 Feb 14 2012, we received confirmation from Microsoft stating that this problem is a false positive and will be corrected in the update 1.119.1986.0 or higher for the antivirus.”
Well – the name of this this blog is in the core of the whole problem.
Krebs is the german word for cancer. Thus, there is only one small small correction:
Microsoft is the cancer _of_ security.
The problem (it was a false positive) was noticed, identified, and fixed in a matter of hours with the next definition release. That’s excellent responsiveness. It was probably a simple error – easily resolved. If you still have the problem, just update your definitions and that will fix it.
All this hoopla over a simple mistake is far more than is warranted. Even this blog is unworthy of such a minor event hardly worth mentioning. Nobody’s perfect, no company is perfect, and no AV/AM/AS product is perfect. We all need to examine our expectations to see if they are reasonable.
Respectfully, I don’t see where Brian said that any company is perfect; in fact, he said, “False positives happen to every antivirus vendors, and this one was fairly innocuous as these things go:” I think it might be your expectation that needs examining if you think that a security expert has to divine what every reader deems minor or relevant. Even events you consider “minor” are helpful to many of us in terms of a bigger picture. Brian is experienced at both security and communications, after all, and that is why we read his blog.
This “Minor event hardly worth mentioning” shows Microsoft isn’t testing its updates even against the “world’s most-visited Web site” – affecting millions of people. This raises the question: Do they test their updates at all? Who authorizes a untested update to be released? Workflow my ass!
I disagree that there seems to be “nothing” to this. I woke this morning to a DNS failure on my Win7/IE9 machine that’s isolated in the DMZ on my Check Point Safe@Office (managed hardware device) firewall. I could see from the taskbar icon that I had no internet access so I started the troubleshooter. Since its not uncommon for the icon not to reset after an earlier interruption when the system is setting idle, I went ahead and opened IE9 before the troubleshooter came back with the DNS failure. The result was that even though I did not connect with my Google homepage, nor did a cached page open, MSE still alarmed on the Blacole.BW exploit. In addition, I let MSE go on to take about 30-45 seconds to remove the exploit and it completed with a history entry with the following tagged file> C:\Users\%username%\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\XEDFHAOO\google_com[1].htm. At this, I continued on to try to resolve the DNS issue and so decided to reboot first. On reboot I got the tell-tale scenario where the MSE icon stayed red until nearly everything else had loaded, and then went to its green status, which is pretty typical of the presence of a rootkit. My next move was to secure the rest of my network by going to my Check Point firewall and creating a rule to block the entire google.com domain. At this point I’m still trying to sort everything out. The remainder of my network (not in the DMZ) is a Windows SBS 2011 Essentials, which I’m pretty new at, so I’m proceeding cautiously. The DMZ machine was patched early in the day on the 14th, while the Server environment was patched late yesterday and this moring. It also happens that the DMZ machine had been offline for several weeks before I patched it and scanned it, yesterday morning, so maybe it was already infected. Something else pretty weird happened during the late-night patch of the Win7/IE9 machine that I’m using right now. Not all the patches installed before a reboot was needed, and when I rebooted, MSE alerted saying my Windows 7 OS had not passed it’s genuine MS validation, and that MSE would be non-functional in 30 days. I didn’t click on any of the alert’s links or buttons, but went straight to Windows Update and let it finish installing the .NET Framework and Silverlight updates. On reboot I never got the alert again. Anyone else seen anything similar? Anyone have any advice?
“Do they test their updates at all?”
I guess there are two possibilities: No one at Microsoft uses Google, or none of them use IE.
“Who authorizes a untested update to be released? Workflow my ass!”
It is a stretch to say they released an untested update.
Google changes the main page every day so it is conceivable that they added a component to the main page which triggered the false positive after the release. Indeed from the image showing yesterday’s main page it did have a animated title.
I am happy if they test a release sufficiently and then respond if any of a million web pages or applications cause a false positive.
Brian said is no big deal, why make it one?
Yes, these things happen. A couple of years ago everyone with a Zone Alarm firewall got knocked out on Patch Tuesday.
This is, of course, not a “bug” but an undocumented feature.
The malware that Microsoft AV found was true but i can say there wont be any bug on google,The bug I am finding from my PC is on IE9 with MSE alert.