The cybercrime underground is expanding each day, yet the longer I study it the more convinced I am that much of it is run by a fairly small and loose-knit group of hackers. That suspicion was reinforced this week when I discovered that the author of the infamous ZeuS Trojan was a core member of Spamdot, until recently the most exclusive online forum for spammers and the shady businessmen who support the big spam botnets.
Thanks to a deep-seated enmity between the owners of two of the largest spam affiliate programs, the database for Spamdot was leaked to a handful of investigators and researchers, including KrebsOnSecurity. The forum includes all members’ public posts and private messages — even those that members thought had been deleted. I’ve been poring over those private messages in an effort to map alliances and to learn more about the individuals behind the top spam botnets.
As I was reviewing the private messages of a Spamdot member nicknamed “Umbro,” I noticed that he gave a few key members his private instant message address, the jabber account bashorg@talking.cc. In 2010, I learned from multiple reliable sources that for several months, this account was used exclusively by the ZeuS author to communicate with new and existing customers. When I dug deeper into Umbro’s private messages, I found several from other Spamdot members who were seeking updates to their ZeuS botnets. In messages from 2009 to a Spamdot member named “Russso,” Umbro declares flatly, “hi, I’m the author of Zeus.”
Umbro’s public and private Spamdot postings offer a fascinating vantage point for peering into an intensely competitive and jealously guarded environment in which members feed off of each others’ successes and failures. The messages also provide a virtual black book of customers who purchased the ZeuS bot code.
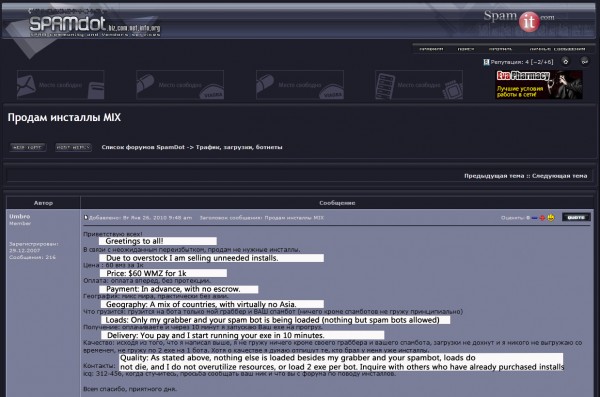
In the screen shot above, the ZeuS author can be seen selling surplus “installs,” offering to rent hacked machines that fellow forum members can seed with their own spam bots (I have added a translation beneath each line). His price is $60 per 1,000 compromised systems. This is a very reasonable fee and is in line with rates charged by more organized pay-per-install businesses that also tend to stuff host PCs with so much other malware that customers who have paid to load their bots on those machines soon find them unstable or unusable. Other members apparently recognized it as a bargain as well, and he quickly received messages from a number of interested takers.
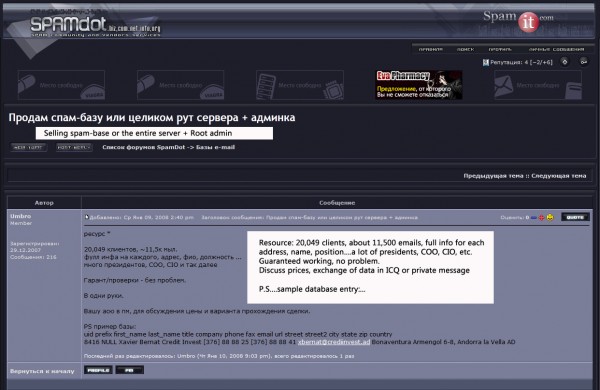
The image below shows the Zeus author parceling out a small but potentially valuable spam resource that was no doubt harvested from systems compromised by his Trojan. In this solicitation, dated Jan. 2008, Umbro is selling a mailing list that would be especially useful for targeted email malware campaigns.
It is not surprising that the Zeus author would frequent such a forum; he is well known to have hung out on other exclusive forums where like-minded cyber thieves set up shop. But Umbro’s messages provide the best proof so far that not only was he the author and main proprietor of a sophisticated Trojan that has helped to steal hundreds of millions of dollars from small to mid-sized businesses, but he also maintained his own sizeable botnets.
Spamdot records show that as often as he sold installs, Umbro turned to some of the top botnet authors to rebuild his private botnets. In an April 14, 2010 private message sent to Ger@ — a Spamdot member I identified earlier this month as the miscreant in charge of the massive Grum botnet — Umbro says he is “ready to buy installs,” and prepared to offer a fair price for buying in bulk. In another communication near that same time, Umbro seeks to rent botnet resources from a business partner of “Google,” the nickname of the individual I identified in January as the author of the Cutwail botnet.
Umbro’s public and private communications reveal how frequently he changed his nicknames, email addresses and other contact details — a common tactic used to confuse and elude law enforcement investigators. By the time Spamdot was closed in Sept. 2010, the ZeuS author was using the nickname “Slavik.” He had just announced that he would be bowing out of the business, and that the code that powers his Trojan would be merged with that of SpyEye.
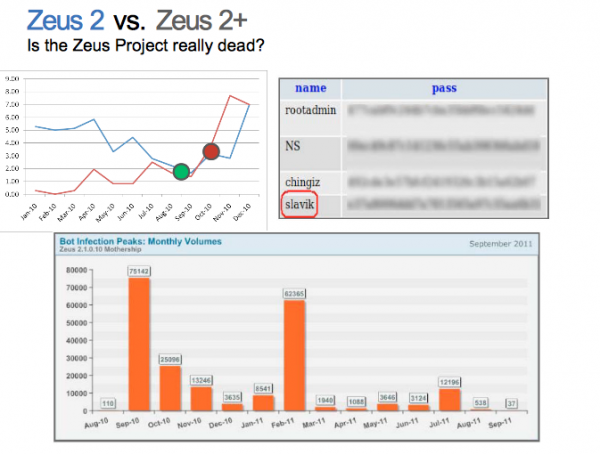
Security researchers at RSA made an interesting discovery at about the same time the ZeuS author was plotting his final disappearing act. They found evidence that the ZeuS author didn’t exactly retire, but rather appears to have gone into the botnet business for himself. RSA’s Uri Rivner said that just before that merger was announced on underground forums, RSA investigators stumbled upon a botnet created in Aug. 2010 with a custom version of ZeuS that was not being sold or distributed in the underground.
That custom version, which RSA dubbed “ZeuS 2,” phoned home to a control server on the Web that the researchers were able to access. They found that between Aug. 2010 and Aug. 2011, more than 200,000 PCs had phoned home to that server, which had helped vacuum up tens of gigabytes of data from host machines. They also learned that miscreants had created four logins that were authorized to access the botnet’s control server: “rootadmin,” “NS,” “chingiz,” and “Slavik” (see screenshot below).
“This ZeuS2 had a lot of improvements, and was created before the ZeuS source changed hands,” RSA’s Rivner told me in an interview last October. “It might be that Slavik decided to move away from selling software and supporting all of his customers to developing infrastructure that can be rented and becoming part of a larger organized crime group.”
According to a security researcher who has access to the same server but asked to remain anonymous, there are now more than a quarter-million PCs compromised by this custom version of ZeuS and reporting home to that same control server.




There’s a strange duplication of much of the text in this article. You may want to review it.
e.g. para 7 is a near duplicate of para 3
Yeah not sure what happened there but it’s fixed now, tx.
I’ll stick my neck out and predict that in the wake of all the information from this forum being leaked, instead of learning to be more careful about what they post online, they will simply start a new forum they consider even more exclusive and continue to post incriminating information.
People crave community. Internet criminals can’t share information about themselves with anyone who isn’t in the “bizness,” but it isn’t safe for them to share with each other, either.
Probably more than likely hehe …
It does surprise me though how lax these guys are about revealing themselves. I mean seriously how hard is it to have a “real” identity used for anything that is not criminal and a “criminal” identity used for anything that is.
They seem to make a sort of half-arsed attempt at concealing themselves, changing nicks for example as outlined in this post, but then leave a trail behind themselves that negates any possibility of the measures they do take to hide themselves.
I sometimes wonder if a lot of these people aren’t abusing various mind-altering substances for most of their work day and do things like rent a server using an account linked to their real identity because they either forgot, got confused wityh multiple identities or just couldn’t be bothered because they had to roll another doobie or whatever they do. It doesn’t appear to be an issue with intelligence based on their clever malware creations.
I mean how hard can it be to seperate identities that are only involved in legit activities from those that aren’t?
I think the main reason they are that lax with their own cover is that they feel even with their cover blown have little to fear, their own government is not particularly interested in locking them and they won’t be extradited. The exceptions (Mega-D) are rather just that, exceptions. They show how safe they feel.
so what ??? . every one knows who he is . but what u going to do about ?? its not much u can do anyway .. ??? Luckily Russia dont have an Extradition treatie with USA.
u r getting lazy Brian , its time to write something usefull not just keep writing the same old story time after time after time ..all u do is going on about them undeground RUSSIAN forums thats all ..
Years ago Russia was known for its vodka and its beautiful women. Now it’s known as a haven for spammers and scammers. The damage to Russia’s national reputation has been significant. I never thought I’d see the day when the great country of Russia was viewed as less than Nigeria but that day is here.
Oh I’m looking forward to much more analysis and revealing of information and dealings between these criminals – I guess the truth hurts the bad guys and entertains the rest of us huh 😉 Not so much fun when the dirty laundry is being combed through is it.
Bring it on.
Also Russian women … still beautiful. Maybe not as gorgeous as Aussie girls but still very attractive <3 🙂
hey Spamdotclon, sounds to me like maybe you’re scared that you’re next on the ‘hot seat’. got something gnawing at your conscience, hmm?
Memorable quotes for
Looker (1981)
http://www.imdb.com/title/tt0082677/quotes [imdb.com]
“John Reston: Television can control public opinion more effectively than armies of secret police, because television is entirely voluntary. The American government forces our children to attend school, but nobody forces them to watch T.V. Americans of all ages *submit* to television. Television is the American ideal. Persuasion without coercion. Nobody makes us watch. Who could have predicted that a *free* people would voluntarily spend one fifth of their lives sitting in front of a *box* with pictures? Fifteen years sitting in prison is punishment. But 15 years sitting in front of a television set is entertainment. And the average American now spends more than one and a half years of his life just watching television commercials. Fifty minutes, every day of his life, watching commercials. Now, that’s power. ”
“The United States has it’s own propaganda, but it’s very effective because people don’t realize that it’s propaganda. And it’s subtle, but it’s actually a much stronger propaganda machine than the Nazis had but it’s funded in a different way. With the Nazis it was funded by the government, but in the United States, it’s funded by corporations and corporations they only want things to happen that will make people want to buy stuff. So whatever that is, then that is considered okay and good, but that doesn’t necessarily mean it really serves people’s thinking – it can stupify and make not very good things happen.”
— Crispin Glover: http://www.imdb.com/name/nm0000417/bio [imdb.com]
“We’ll know our disinformation program is complete when everything the American public believes is false.” — William Casey, CIA Director
“It’s only logical to assume that conspiracies are everywhere, because that’s what people do. They conspire. If you can’t get the message, get the man.” — Mel Gibson
[1967] Jim Garrison Interview “In a very real and terrifying sense, our Government is the CIA and the Pentagon, with Congress reduced to a debating society. Of course, you can’t spot this trend to fascism by casually looking around. You can’t look for such familiar signs as the swastika, because they won’t be there. We won’t build Dachaus and Auschwitzes; the clever manipulation of the mass media is creating a concentration camp of the mind that promises to be far more effective in keeping the populace in line. We’re not going to wake up one morning and suddenly find ourselves in gray uniforms goose-stepping off to work. But this isn’t the test. The test is: What happens to the individual who dissents? In Nazi Germany, he was physically destroyed; here, the process is more subtle, but the end results can be the same. I’ve learned enough about the machinations of the CIA in the past year to know that this is no longer the dreamworld America I once believed in. The imperatives of the population explosion, which almost inevitably will lessen our belief in the sanctity of the individual human life, combined with the awesome power of the CIA and the defense establishment, seem destined to seal the fate of the America I knew as a child and bring us into a new Orwellian world where the citizen exists for the state and where raw power justifies any and every immoral act. I’ve always had a kind of knee-jerk trust in my Government’s basic integrity, whatever political blunders it may make. But I’ve come to realize that in Washington, deceiving and manipulating the public are viewed by some as the natural prerogatives of office. Huey Long once said, “Fascism will come to America in the name of anti-fascism.” I’m afraid, based on my own experience, that fascism will come to America in the name of national security.”
Please get a blog instead of posting off-topic in someone else’s. They’re free.
“The cybercrime underground is expanding each day, yet the longer I study it the more convinced I am that much of it is run by a fairly small and loose-knit group of hackers.”
I read the whole article but it’s the first sentence that stays with me. It’s something I’ve suspected for a while as well.
Brian, in your opinion, what actions should be taken to reduce the damage of the underground economy?
There are two things that can be done: (1) aggressively roll out preventative technologies; (2) hit them in their wallet by going for the banks that they use. I think Brian reported on option 2 in the past. It turns out that most money crooks are making flows through a small number of international banks. Major countries putting a bunch of pressure on these banks might make things considerably difficult. Add shady payment processors and advertising groups & you might hit them so hard that they would hardly make any money.
On option 1, it’s easy enough. I’ve posted on it plenty in the past. There have been OS designs that prevented entire classes of attack or privilege escalation. One of the oldest, MULTICS, was immune to buffer overflows b/c they made the stack move in the opposite direction. SourceT, a recent one, does the same. Then you have safe programming languages, runtimes that prevent incorrect behavior, etc. Crooks have an extremely hard time compromising things built that way. That’s why they’re glad that most developers take a monolithic approach using unsafe languages & methodologies. (sighs)
Interesting post but regarding secure operating systems and languages but I’m a little skeptical. How can you know they’re secure if they aren’t widely used (meaning not having significant numbers of unaware users to boot) which leads to them being widely targetted for exploits in the first place?
There would also seem to be a disconnect between what happens in the real world and your points about developers using unsafe languages and methodologies – if there wasn’t a significant barrier then why are they not being used? You also must know that testing for all possible permutations of what an application can do is simply unfeasible right?
I’m sure Microsoft didn’t set out to develop an insecure operating system with Windows 7 for example but it still has holes poked in it. Certainly one should aim for security of course but until a widely used OS has few or no exploits how are you going to know that it is secure in the real world?
Sorry for the late reply. I’ll try to address your points one by one. First, no OS is “secure” in the absolute sense. I use the word to mean they acceptibly prevent, manage, and/or recover from specific attack avenues. So, to be secure from buffer overflows the design must provably make buffer overflows highly unlikely or impossible. A buffer overflow only occurs b/c how the stack movies causes the attackers code to “overflow” control operators.
In Multics and modern SourceT, the stack moves in reverse so that an “overflow” just means more memory is allocated & the data flows into it. Control operators aren’t affected. By definition & design, a buffer overflow attack can’t be done. You don’t have to test this: it’s just logically impossible for a buffer overflow to occur. I think an algorithm/design to address heap issues was recently published. If mainstream OS’s had these features, two of the main system attack vectors would be neutralized. Safe libraries and languages address many other common causes of crashes or exploits. So, hackers have to find a different kind of attack or have to find flaws in the safe platform. Flaws in the safe platform are usually less in number than to applications in general.
The issue with developers is harder to pin down. Developers largely learn and use what’s in demand. What gets to be in demand is more determined by ease of use, productivity, tool support, cost, time to market, etc. Let’s face it: secure/quality development approaches with safe languages/libraries aren’t as fun as agile coding Rails apps. 😉 So, it’s more of a social and business priority issue than an issue with capability. Want examples?
Praxis Correct by Construction, Cleanroom (economical), and Software Inspection Process are producing low defect code consistently. Praxis warranties their software. (Imagine that.) CompCert C compiler was the only one that had no flaws during a compiler testing. Integrity-178B OS, GEMSOS and Boing SNS firewall/mailguard all survived years of NSA pentesting to get their A1/EAL6/EAL7 ratings. Good parser generators & things like Google’s protocol buffers reduce issues there. Eiffel Design-by-Contract, SPARK Ada and Ocaml are being used by many companies for their quality advantages. Opa, built on Ocaml, is utilizing Ocaml to build a secure web platform (another platform I can’t remember). SIF and E for secure, distributed applications. And so on and so on. They just mostly collect dust & are used by companies that understand their value.
As for Windows 7, Microsoft can’t really make it secure due to legacy issues. Microsoft has so many holes and bypasses in it, by design, that important software depends on, that it can’t be secure period. Vendors would have to redesign software for a built-from-scratch secure underlying platform. Anything this general can’t be secure & will only focus on containment, detection & recovery. One of the last of the old medium to high assurance OS’s to survive, BAE Systems STOP, is an example. Microsoft is just steadily putting bandaids and duct tape on a broken design, while trying to reduce security issues in stuff they made after SDL was introduced.
Want to see an OS built with security/reliability in mind that you can buy today? Look up INTEGRITY OS. LynxOS-SE is medium assurance. OpenBSD minus a lot of fat is another good compromise. Hydra from (Bodacion?). MINIX 3 has potential. SourceT from Secure64 has good design principles. OKL4 is a nice minimalist design b/c it lets you make good tradeoffs. Using a separation kernel to break the system into untrusted & trusted components is a good idea. There’s plenty to work with. It’s just impossible to make a general-purpose, monolithic, high flaw rate OS on commodity hardware secure. Gotta do it differently.
Feel free to check any of these methods, products, languages, etc. out. That’s why I post them. I’m not afraid of scrutiny. 😉
The biggest problem isn’t that the spammers are a small knit group of people. The biggest problem is the corruption in high places that protects them. I’ve looked into that financial side closely and it’s devilish hard to launder large sums of money anonymously unless one is part of a larger network like a mob or a criminal gang using money mules and so on. And that type of activity attracts notice, inevitably, and that in turn means paying the people whose notice you’ve attracted money to look the other way.
There are people who are in positions of legal and political responsibility and trust who know what is going on and let in happen anyway. Those are the real bad guys as far as I see it.
That custom ZeuS version that was mentioned at the end of the post is called
ZeuS version 2.1.0.10.
It has many improved features and some of them are pretty impressive as well.
You can read about it at the following link:
http://blogs.rsa.com/rsafarl/organized-cybercrime-nefarious-sophistication-featuring-zeus-v2-1-0-10/
the real kingpins:
http://pastebin.com/06yi5zCV
ain’t dat dah tooth!
Krebs deletes comments only very rarely. Your inane off-topic post about an IMDB entry was not deleted; it was appropriately buried. You may find this hard to believe, but I wasn’t one of those who thumbed you down. But I *will* go do that now, thanks for the reminder.
Brian, you mentioned “the longer I study it the more convinced I am that much of it is run by a fairly small and loose-knit group of hackers.”
Do you think this might be another “Russian Business Network” thing or one and the same?
Cybercrime is growing with increasing momentum, unfortunately this the reality. Thanks for the article @BrianKrebs
I think a lot of the hackers aren’t as smart as they think they are, if things were actually secure you couldn’t afford to buy them. lol
Good network security is very affordable, it’s just that computer repair people must never really suggest it since they would be working themselves out of work.
You do raise an interesting point about the security people not working hard enough lest they put themselves out of a job. Despite the obvious truth, I think the opposite is true. Most security guys are passionate about their work.
I’ve seen this argument about various professions that “fix” things, most often the medical profession and pharmaceutical industry, but I just don’t think it holds up.
The reason being that if people within the industry are not providing fixes where they could, consciously or not, then that leaves open the door for someone that does to takeover the whole area because they do provide that. And no one wants to go out of business that way.