Microsoft is urging Windows users who browse the Web with Internet Explorer to use a free tool called EMET to block attacks against a newly-discovered and unpatched critical security hole in IE versions 7, 8 and 9. But some experts say that advice falls short, and that users can better protect themselves by surfing with an alternative browser until Microsoft issues a proper patch for the vulnerability.
EMET, short for the Enhanced Mitigation Experience Toolkit, is a tool that can help Windows users beef up the security of commonly used applications, whether they are made by a third-party vendor or by Microsoft. EMET allows users to force applications to use one or both of two key security defenses built into Windows Vista and Windows 7 — Address Space Layout Randomization (ASLR) and Data Execution Prevention (DEP).
Put very simply, DEP is designed to make it harder to exploit security vulnerabilities on Windows, and ASLR makes it more difficult for exploits and malware to find the specific places in a system’s memory that they need to do their dirty work.
Before I get into the how-tos on EMET, a few caveats. EMET is a great layer of security that Windows users can and should use to enhance the security of applications. But EMET may not block the exploit code now publicly available through the Metasploit framework. In fact, Tod Beardlsey, an engineering manager with Rapid7, the security firm that manages Metasploit, told The Associated Press that EMET does not appear to be completely effective against this exploit.
I asked Metasploit founder HD Moore what he thought was the best way to block this exploit, and he pointed out that the exploit available through Metasploit requires the presence of Java on the host machine in order to execute properly on IE 8/9 on Windows 7 and Vista systems (the exploit works fine without Java against IE7 on XP/Vista and IE8 on XP). Obviously, while the lack of Java on a Windows machine may not prevent other exploits against this flaw, it is a great first start. I have consistently urged computer users of all stripes to uninstall Java if they have no specific use for it.
Using a non-IE browser such as Chrome, Firefox, Opera or Safari is a far safer approach, at least until Microsoft releases a proper patch for this flaw (note that Windows 8 and Internet Explorer 10 are not affected by this vulnerability).
If you decide to stick with IE, I’d encourage you to read closely the security advisory Microsoft published last night. It describes a number of tweaks that users can make to ratchet up security settings in IE, and details the process of setting up IE to use EMET.
EMET can force individual applications to perform ASLR on every component they load, whether the program wants it or not. Please note that before you install EMET, you’ll need to have Microsoft’s .NET platform installed. And while it does technically work on Windows XP (Service Pack 3 only), XP users cannot take advantage of mandatory ASLR and some of the other notable protections included in this tool.
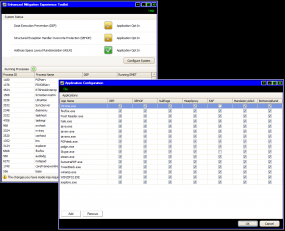
To proceed with EMET, download the program and install it. To wrap Internet Explorer in EMET’s settings, launch the program and click the “Configure Apps” button in the bottom right corner of the application window. Selecting the “Add” button in the next box that brings up a program selection prompt; browse to C:\Program Files\Internet Explorer, and then add the “iexplore.exe” file. It should be okay to accept all of the defaults that EMET adds for you.
While you’re at it, add the rest of your more commonly used, Internet-facing apps. But go slow with it, and avoid the temptation to make system-wide changes. Changing system defaults across the board – such as changing ASLR and DEP settings using the “configure system” tab – may cause stability and bootup problems. I’ve been using it on a 64-bit Windows 7 system and phasing in some of my most-used applications on-by-one with the “configure apps” button just to make sure the added security doesn’t crash the programs (see screen shot below). So far, the only problem I’ve run up against was Skype, which didn’t seem to like being forced into using the six different protection mechanisms that EMET employs by default when you manually add application: It simply would crash upon startup.
Just keep a running list somewhere of the apps you have set to use EMET, and if you experience problems or glitches with these programs going forward, you may be able to fix said bugginess simply by tweaking EMET a bit.




Is anyone still using IE?
See colored map at http://en.wikipedia.org/wiki/Browser_wars
It helps IE that it is the default browser in Windows. Many unknowing users stick with IE because it is all there is to them.
I do, I just downloaded Chrome last week and it looks messy and junkie. I also don’t like the way it has it’s bookmarks/tools.
Odd, because I have an Android phone.
I use IE9 with high security settings, and I really like it. I really prefer the clean look. I didn’t know before today that IE10 had come out; I don’t know if it’s in full release or just beta.
IE10 is for Windows 8. Somebody can correct me if I am wrong.
This is true. Right now, IE 10 is only available on Windows 8. When fully released, it will be available for Windows 8 and Windows 7.
I do agree with Chris though. I enjoy using IE more than any other browser. I’ve tried Chrome and it’s just not for me. I like the features, look and speed of IE. It’s quick and works well.
A lot of companies can only use IE. The reason is so many companies are Microsoft shops only and write there code to work in IE. Insurance companies are the some of the worst when it comes to this, but I’ve seen this with banking, and healthcare.
Also, on 64-bit systems, protect both instances of IE, since you have an extra Program Files (x86) instance of it.
Or, in the Configure Apps section of EMET, you can click File > Import… and import one of Microsoft’s preconfigured and tested apps lists, which are located in EMET’s Deployment\Protection Profiles folder. This is in the location you installed EMET to, such as C:\Program Files (x86)\EMET.
“Is anyone still using IE?”
Yes. IE is a pretty good browser these days, with a long, guaranteed support lifecycle and central manageability/enforcability/auditability/deployability/patchability via Group Policy, MBSA, and WSUS respectively.
I’ve used EMET since the first release and had only a few programs run afoul of its mitigations on 64-bit Win7. I’m currently on the 3.5 Tech Preview release, which adds some mitigations against Return-Oriented Programming techniques. If anyone’s decided “yeah, I’m going to try EMET,” then I do suggest using EMET 3.5 Tech Preview since it also has a notifier that’ll tell you precisely which mitigation tweak crashed your program, if that were to occur.
Very interesting and useful comment, mechBgon. Thanks.
What about Proactive Threat Protection module, part of Symantec Endpoint Protection? could it be used to mitigate these kind of threats?
Oh, and on the Configure System tab, I haven’t seen anyone having trouble on XP, Vista or Win7 with these settings:
DEP: Application Opt-Out (allows you to grant exceptions the way we’ve done it since WinXP SP2)
SEHOP: Application Opt-Out
ASLR: Application Opt-Out
My apologies for an error in the post just above… That last setting (ASLR) should’ve read Opt-In, not Opt-Out.
There’s a hidden (and reportedly risky) “Always On” setting for ALSR that only appears with a Registry edit.
I’m not sure why people downvoted your comment. It was relevant and helpful. Sometimes the voting on here makes less sense than reddit.
I encourage everyone to read Dan Guido’s Exploit Intelligence Project for a little more insight into web browser security.
Very insightful post. One thing though 3.5 is a beta. 3.0 is production ready and also has the notification feature you mentioned.
Hi Sweetz,
Thanks for mentioning that v3.0 of EMET also includes the Notifier feature and that 3.5 is a test version.
My apologies that I duplicated your comment by also mentioning these points.
Hi mechBgon,
I would not advise using EMET 3.5 Tech Preview at this time since it a preview version and has not been fully tested unlike v3.0. This is why it is called a Tech Preview. It is not ready for production use at this time.
EMET 3.5’s ROP mitigations are not compatible with all programs and will require far more testing since there are 5 more mitigations to enable/disable.
The Caller Checks and Simulate Execution Flow mitigations are not compatible with all programs and are most likely to cause issues. This info is contained in the EMET 3.5 User Guide in the folder that you install it in.
Finally, one last reason to avoid installing this version right now is that its mitigations are not perfected yet and have been shown to be vulnerable to workarounds by malicious programs. Please see the following forum thread about this:
http://social.technet.microsoft.com/Forums/en/emet/thread/b0deb3b8-eb70-4e30-a1e5-6828f5304913
The fully tested V3.0 also features the Notifier feature so that you are informed if EMET blocks an exploit or it finds an incompatibility with a program that you are protecting with it. This way you can easily disable the mitigation that is causing that program to crash.
A detailed explanation of all of the mitigations contained in EMET is provided at the following link:
http://www.infoworld.com/t/microsoft-windows/microsoft-shuffles-windows-security-deck-emet-21-831
The explanation is pretty much word for word from the Microsoft EMET User Guide that is included after you install EMET.
Articles on the effectiveness of EMET can be found at the following links:
http://www.rationallyparanoid.com/articles/emet-testing.html
http://blogs.technet.com/b/security/archive/2012/08/08/microsoft-s-free-security-tools-enhanced-mitigation-experience-toolkit.aspx
http://www.rationallyparanoid.com/articles/microsoft-emet-3.html
I have used EMET since February 2011 beginning with EMET 2.0.0.3 and it only caused me minor issues which I resolved in a few minutes. I have used EMET 3.0 since it was released in May this year and it is very un-obtrusive. I am also very familiar with the security mitigations that are in use in EMET, Windows and IE. I can provide as much information as necessary to answer your questions.
I hope this helps. If I can answer any further questions, please let me know.
Thank you.
Hi JimboC, I actually have a dozen production systems using EMET 3.5 Tech Preview since shortly after its release, including ROP mitigations enabled on nearly every executable on the systems, including the entire contents of the System32 directory and many others.
Based on the near-zero problems I’m having, I’ll stand by my recommendation on EMET 3.5 TP, particularly since it will not enable any ROP mitigations even if the user imports one of Microsoft’s predefined baselines.
The EAF mitigation will crash Microsoft’s own MMC.EXE (Microsoft Management Console), and ROP mits will make Snipping Tool crash when capturing a screenshot from Internet Explorer 9, which Elias at Microsoft informs me is already being addressed in the final release. So it’s been pretty smooth. My systems are mostly 64-bit Win7, with one Windows Home Server 2011 and one Win8 Enterprise test system.
Thanks for your input, I see you put a lot of effort into it 🙂
Hi mechBgon,
Thanks for the extra info about EMET 3.5. In my testing of this version, it did cause some problems for the applications I was trying out. Looks like I was simply unlucky and it is good news that 3.5 is such a success.
Thanks also for the details of the only incompatibles that you have found, this will make deploying v3.5 easier for me.
All of my systems are also 64 bit, Windows 7 and Windows Vista and a Window 8 64 bit Release Preview test PC.
It didn’t take long to write my comment above since I had been using similar information to answer questions on other websites and forums.
– https://www.net-security.org/secworld.php?id=13614
18 Sep 2012 – “… Microsoft… offers instructions on steps the users can take to mitigate – but not yet remove – the threat:
• Deploy the Enhanced Mitigation Experience Toolkit (EMET) and configure it for Internet Explorer
• Set Internet and Local intranet security zone settings to “High” to block ActiveX Controls and Active Scripting in these zones
• Configure Internet Explorer to prompt before running Active Scripting or to disable Active Scripting in the Internet and Local intranet security zone.
These steps could bring -additional- problems to the users, such as being bombarded by a slew of security warnings, so until Microsoft releases a definitive patch for the hole, maybe it would be easier for IE users to take Rapid7’s advice and switch to another browser for the time being.”
.
Brian,
I took your advice and removed Java from my machines. Should I install the EMET tool just for good measure?
I do use IE9 from time to time, but my default browser is Chrome (beta channel release) and I don’t plan on using IE9 until MS releases a fix and/or you say it’s OK again to use the browser.
Thanks!
For sure every Tom, Dick and Harry expects Microsoft to handle their critical security hole in time and make their browser safe. – Now again news are full of warnings not to use Internet Explorer, in some countries even in TV and radio…
… on the other hand Microsoft doesn’t care to update out-dated browser plugins or even to inform their customers about the most recent security risks:
“Internet Explorer – Experience a more beautiful web” (… and enjoy some of the latest exploits on your exciting journey through distress and frustration…)
In fact there’s not even a warning at Microsoft’s Safety & Security Center (or every other Microsoft site) that Tom, Dick and Harry could find… (maybe that’s the reason for their shrinking market share: 23.65% and dropping)
As best I can tell, MS still requires you to use IE for manual updates apart from automatic critical updates. So there’s no way to avoid at least occasional use of IE.
Brian, your first link to EMET, in para 2, takes you to V.2.0. You may want to update it to V.3.o or even V.3.5.
Thanks, Bill. I’ve fixed that.
In fact, the metasploit exploit needs a Java 6 or older plugin to work on Vista/Windows7. That particular exploitation technique (jre msvcr71 rop) has been fixed in Java 7 update 7 (and older Java 7 versions as well, but you do not want them because of the last 0day anyway).
So, if you need Java, better use the latest and greatest Java 7 Update 7 since it reduces your attack surface compared with the latest and greatest Java 6 Update 35 version.
If you don’t need it, uninstall it of course 🙂
Microsoft never recommends, even if for a very limited time, that their customers use an alternate browser such as Google Chrome*, Mozilla Firefox (with the NoScript add-on) or Opera. For less technical users, an alternate browser is the preferred option until Microsoft patches this vulnerability and the patch gets applied to one’s system.
* For less technical users, Google’s Chrome browser has good security attributes such as transparent updates (for the browser itself as well as bundled Flash Player/PDF Reader plug-ins), sandboxing (even on Windows XP) and blocking the Java plug-in for a website if the plug-in is out of date.
From the article:
“Microsoft is urging Windows users who browse the Web with Internet Explorer to use a free tool called EMET to block attacks against a newly-discovered and unpatched critical security hole in IE versions 7, 8 and 9. But some experts say that advice falls short, and that users can better protect themselves by surfing with an alternative browser until Microsoft issues a proper patch for the vulnerability.
Hi Rabid Howler Monkey,
You are correct.
Microsoft acknowledged that EMET does not provide a 100% guarantee of protecting you from this flaw in the FAQ of their security advisory:
http://technet.microsoft.com/en-us/security/advisory/2757760
The German government is now warning against this Internet Explorer exploit and is advising users to run an alternate web browser until IE is patched or otherwise fixed:
http://www.cbsnews.com/8301-501465_162-57515204-501465/german-watchdog-warns-of-internet-explorer-breach/
What’s wrong with this: Uninstall both Java and IE (9, 8, whatever) and use Firefox as your browser, with the IE Tab Plus add-on. So when you need to open a webpage in IE, just open it from within Firefox using the IE Tab option. The add-on uses the inbuilt IE engine to open it, even though the uninstalled IE browser isn’t available on your machine.
Frank, that could work (EMET would still be a great add-on). Personally, I would be more receptive towards FireFox if it had anything that compared to Chrome’s sandboxing or IE’s Protected Mode. Enterprise manageability would also help their market penetration, and IMHO they’re being a little ridiculous by ratcheting up the version number every six weeks no matter what.
@mechBgon
>>they’re being a little ridiculous by ratcheting up the version number every six weeks no matter what.
I’ve always thought that was a response to Chrome.
In 2010, Chrome went from v4 to 8. Since 2011 it’s gone from v9 to 21.
Seeing that, FF followed suit so as to not appear outdated to those unawares of the oneupmanship war going on.
Had it not, it would now be around v4 or 5 at the pre version-war pace of version changes.
Great suggestion , Frank. I just installed IE Tab V2 (similar to IE Tab Plus, but has fewer negative comments), and tested it with MS updates, and it worked perfectly.
The IE Tab V2 forum points out that, after installation, you may need to right click in the icon area and click on customize, then add the icon for this FF add-on, as I had to do. But not a problem doing this.
Uninstalling IE9, I got IE8 , and was getting the impression uninstalling IE8 that I would get IE7, which gave me the feeling that somehow I don’t actually have full ownership of ‘my pc’.
Hi nikol,
That is not true. Please allow me to provide reassurance. You do have ownership of your PC and what you have experienced is expected behavior if you are using Windows 7.
If you are using Windows 7, uninstalling IE9 will revert you to IE 8. IE 8 was the built-in browser of Windows 7. Windows 7 never included IE 7.
Allow me to explain, IE 7 became available for download in November 2006 for consumers (corporate customers received it in October 2006). 3 years later, on October 22nd 2009, Windows 7 was released while IE 8 had been released on 19th March 2009 so it makes sense that Windows 7 included the most recent version of IE available and not a version from 2006. IE 8 was designed to be the built-in browser of Windows 7.
Internet Explorer 7 was designed to be the default and built-in browser of Windows Vista.
This trend continues with IE 10, the built-in browser of Windows 8.
Windows Vista did not allow Internet Explorer to be removed as it was deeply integrated into the structure and fabric of Windows. Windows 7 allowed IE to be removed since removing it was becoming a more popular request and not having the ability to do so was seen as an important issue to be resolved.
Further information about uninstalling Internet Explorer 8 from Windows 7 is available from the following links. This will leave you with no version of Internet Explorer installed.
http://www.howtogeek.com/howto/2734/uninstall-disable-delete-internet-explorer-8-from-windows-7/
http://support.microsoft.com/kb/957700
If you require any further advice or clarification, please let me know and I will be happy to assist.
Thank you.
“Yes. IE is a pretty good browser these days, with a long, guaranteed support lifecycle and central manageability/enforcability/auditability/deployability/patchability via Group Policy, MBSA, and WSUS respectively.”
laughable that you need W$U$ to keep it secure. maybe that works at an enterprise level, but would you let your parents pay their bills or shop ebay with IE ?
usability != security
John, W$U$ costs zero $, so it’s actually OK to spell it the regular way 🙂
As for the home users, no WSUS is needed… just the usual Automatic Updates. WSUS’s attraction for the enterprise is partly that the IT staff can deploy the patches across the enterprise *after* testing them for any issues they might cause. It also reduces bandwidth consumption, since the WSUS server can download the patch once and deploy it internally, instead of having 10,000 systems all downloading the same patch for themselves.
@Brian:
The incompatibility of EMET with Skype was documented long ago in the following forum thread:
http://social.technet.microsoft.com/Forums/en-US/emet/thread/1e70c72b-67b2-43c4-bd36-a0edd1857875
Simply disable the EAF mitigation and all will be well. There is no need to disable any further mitigations in order for Skype to work normally. That way you will gain the maximum benefit from the protection that EMET has to offer.
I hope this helps. Thank you.
Thanks Jimbo. I figured it out a while back. If you look at the screenshot on this post, you can see that. But thanks for making it explicit here for others.
Hi Brian,
Thanks for your comment and apologies for not noticing that you had already resolved it in your screenshot.
This seems to be mentioned as part of the settings available in the distributed ADMX/ADML (as of v3.0) along with the following:
Microsoft Works, Works Calendar and Works Calendar Reminder- all mitigations
Microsoft Office XP- all mitigations except DEP
Microsoft Office 2003, 2007, 2010- all mitigations
Adobe Acrobat 8,9,10- all mitigations
Adobe Acrobat Reader 8,9,10- all mitigations Windows Media Player- all mitigations except MandatoryASLR
Skype- all mitigations except EAF
Microsoft Lync- all mitigations
Windows Live Writer- all mitigations
Windows Live Mesh- all mitigations
Windows Live Sync- all mitigations
Windows Live Messenger- all mitigations
Google Chrome- all mitigations
GoogleTalk- all mitigations
Mozilla Firefox- all mitigations
Mozilla Thunderbird- all mitigations
Adobe Photoshop- all mitigations
Winamp- all mitigations
Opera- all mitigations
WinRAR- all mitigations
Winzip- all mitigations
VideoLAN VLC- all mitigations
RealPlayer- all mitigations
mIRC- all mitigations
7zip- all mitigations
Safari- all mitigations
QuickTime Player- all mitigations
iTunes- all mitigations
Pidgin- all mitigations
Java Runtime Environment 6- all mitigations
So MSFT also did the duty of testing current versions of software for us.
– https://technet.microsoft.com/en-us/security/advisory/2757760
V1.1 (Sep 18, 2012): Assigned Common Vulnerability and Exposure number CVE-2012-4969 to the issue. Also -corrected- instructions in the EMET workaround.
– http://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2012-4969 – 9.3 (HIGH)
“… function in mshtml.dll in Microsoft Internet Explorer 6 through 9 allows remote attackers to execute arbitrary code via a crafted web site, as exploited in the wild in September 2012…”
.
There is no better security information than can be found here. Thank you Mr Krebs. This is pure Quality with a capital Q.
– https://blogs.technet.com/b/msrc/archive/2012/09/18/additional-information-about-internet-explorer-and-security-advisory-2757760.aspx?Redirected=true
18 Sep 2012 – “We will release a [u]Fix it[/u] in the next few days to address an issue in Internet Explorer… It will not affect your ability to browse the Web, and it will provide full protection against this issue until an update is available. It won’t require a reboot of your computer. This Fix it will be available for everyone to download and install within the next few days…”
.
From the article:
“the exploit code now publicly available through the Metasploit framework
How long will it take the malware miscreants to add this exploit to their “packs”?
A ‘fix it’ will be helpful for Windows sysadmins and power users that keep up with these things, but Ma and Pa Kettle along with Joe and Jane six-pack, that use only IE for their browsing, will know nothing of the vulnerability, the exploit based on the vulnerability and the forthcoming ‘fix it’.
Should Microsoft issue an out-of-band patch for this vulnerability? The next Patch Tuesday is October 9, 2012, which is three weeks from today.
I don’t really understand why you need these extra tools. This exploit is caught by both Symantec Enpoint Protection and also the freely available Microsoft Security Essentials. What am I missing here?
You have a remarkable amount of trust in antivirus software. I’m not sure that is the most prudent place to put your trust when it comes to 0day vulnerabilities, against which there can be any number of different exploits.
Well so far every variant I have thrown at it has been caught by Symantec Endpoint. If you can show me one that will get through then I would consider it a bigger deal. The heuristics of the attack are caught over and over. Putting trust in the A/V is much better than putting trust in some sort of patch from the vulnerable software maker. I will opt for the condom rather than trusting that the girl has been vaccinated at this time.
Hi Jim Williams,
Brian is right, you should not rely 100% on your anti-virus software. Since I use Symantec Norton Internet Security 2013, I too have found that its heuristics are excellent at detecting such exploits. The fact that it updates itself every 5 to 15 minutes is also an extremely fast reaction time. However, should the exploit change in a way that the heuristics cannot detect, you are once again vulnerable.
Relying on any one thing for security is never a good idea, if it fails, you are compromised.
Internet Security 2013 also incorporates a firewall and intrusion prevention signatures (among other defences). This firewall is far less intrusive than the Windows 7 firewall. I have also tested this 2013 firewall using GRC’s Shields Up service (https://www.grc.com/x/ne.dll?bh0bkyd2 ) and it found no flaws (there weren’t any in the other recent versions either).
In addition, I use EMET (as discussed by Brian (above)) enabled on all of my applications that I use regularly as well as keeping all of the applications up to date . Windows 7 64 bit and Internet Explorer 9 are also kept fully up to date as well as plugins such Adobe Flash 11.4 and Microsoft Silverlight 5.1. This makes it a lot harder to compromise such a system.
When I began working in the Anti-malware industry 2 years ago, I saw exploits and fake AV software/malware defeat up to date AV signatures every day and that is not an exaggeration. I do NOT work for Symantec but services such as VirusTotal (now owned by Google) would not exist if AV software was 100% effective.
The following 3 blog posts from Symantec should change your mind about why AV software now includes advanced heuristics and reputation technologies:
http://www.symantec.com/connect/articles/detecting-complex-viruses
http://www.symantec.com/connect/blogs/not-all-reputation-technologies-are-created-equal
http://www.symantec.com/connect/blogs/reputation-based-security-suspiciousinsight-detections-virus-total
Thankfully polymorphic and metamorphic infections are rare but their ability to evade detection is un-paralleled and this is why relying on AV software is not enough.
Finally, let me briefly explain what heuristics are:
Heuristics are actually the name of the technique that are used to detect a particular kind of malware (i.e. malicious software)(not all malware are “viruses”). Heuristics are a tool or technique that enhances the ability to detect certain and potentially common code patterns.
Heuristics are useful when creating generic malware definitions for a malware family that contains many variants. This is beneficial since one signature/definition can then detect and remove many/all of the variants of a malware family rather than creating an individual signature for each variant (some malware families have thousands of variants).
I can provide further information should you have any other questions.
Thank you.
R H Monkey is so right! No matter how “easy” the Fixit is, you have to know about it, and you do have to have a bit of a techie bent to understand the nuances and apply it. Therefore, it is out of league for average computer users, who don’t read Brian. Such a techie user would probably be fairly safe anyway.
What’s needed is something an average user can do in cases like this. Maybe a Panic Button (seriously) to lock IE (or Windows)down with DEP, ASLR, and any other initials that would help!
Regards,
Hello all,
I wrote up a quick tutorial on how to centrally deploy EMET and control settings using Group Policy:
http://mbrownnyc.wordpress.com/technology-solutions/implement-the-enhanced-mitigation-experience-toolkit-emet-enterprise-wide/
Check it out and let me know what you think!
Thanks,
Matt
Hi Matt,
Thanks for the tutorial. This is very useful.
No problem. Thanks for the compliment.
I have also performed a simple performance analysis of EMET’s affect on RAM I/O speed which may help understand the cost of implementation:
http://mbrownnyc.wordpress.com/performance-analysis/enhanced-mitigation-experience-toolkit-emet-memory-speed-analysis/
Good suggestion, but only applies to the top two versions of Win7. What about Home Premium, et al., which don’t have Group Policy available?
You can go ahead and install EMET as you wish on a system that doesn’t support Group Policy.
From my shallow investigation, I pointed out some registry keys that could be populated, that are checked by EMET when it starts (I can’t exactly determine when that is, but I imagine it is part of the kernel subsystem), then EMET translates them into the stable “EMET store” (which appears to be a bit more secure).
This struck me in confusion, because it took me two reboots for the app policy to be learned by the EMET client. Even then I had to do some massaging with the policy (like enabling one of the pre-defined list of apps, looks to kick the EMET client to get it to learn the app policy).
BUFFERSHIELD by sys-manage.com
Windows NT, 2000 and XP users have an alternative tool available. It’s called BufferShield and it can be found at http://www.sys-manage.com/
BufferShield is said to use PaX technology as developed for Linux. It does come at a modest price of around 20 dollars. It takes care of DEP with or without Nx bit.
Needless to say I use it. It is particularly good for my ancient hardware as the AMD XP 3000+ CPU does not make it possible to use ‘Never eXecute’ so EMET 3.0 DEP protection is useless for my system. I do use EMET for protection from SEHOP, NullPage, HeapSpray, EAF and BottomUpASLR exploits.