There are 1,001 ways to swindle people online, but the hardest part for crooks is converting those ill-gotten gains into cash. A new service catering to purveyors of ransomware — malware that hijacks PCs until victims pay a ransom – levees a hefty fee for laundering funds from these scams, and it does so by abusing a legitimate Web site that allows betting on dog and horse races in the United States.
Ransomware is most often distributed via hacked or malicious sites that exploit browser vulnerabilities. Typically, these scams impersonate the Department of Homeland Security or the FBI (or the equivalent federal investigative authority in the victim’s country) and try to frighten people into paying fines to avoid prosecution for supposedly downloading child pornography and pirated content.
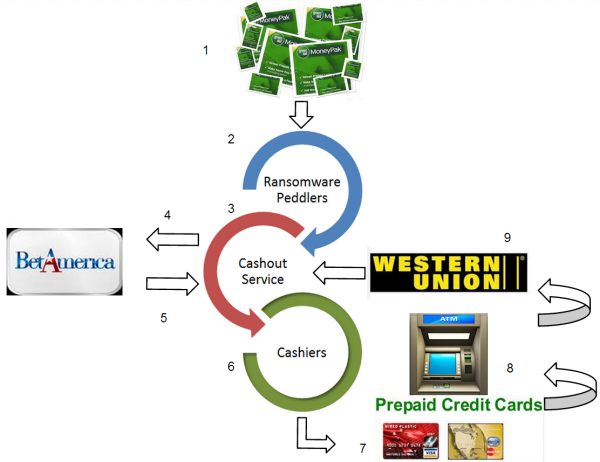
Ransomware locks the victim’s PC until he either pays the ransom or finds a way to remove the malware. Victims are instructed to pay the ransom by purchasing a prepaid MoneyPak card, sold at everything from Walgreens to Wal-Mart (some scams tell victims to pay using a PaySafe or Ukash card). Victims are then told to send the attackers a 14-digit voucher code that allows the bad guys to redeem those MoneyPak vouchers for cash.
Trouble is, taking funds off of a MoneyPak requires either spending it at stores that accept it, or hooking it up to a U.S. bank account, to PayPal, or to a prepaid Visa or Mastercard. What’s more, most miscreants who are even halfway competent at spreading ransomware can expect to collect dozens of MoneyPak codes per day, so cashing out via the above-mentioned methods simply does not scale well for successful bad guys (particularly those who live outside of the United States).
Last week, I stumbled on a ransomware cashout service hosted in Minsk, Belarus that helps simplify the process. It checks the balances of MoneyPak codes by abusing a feature built into betamerica.com, a legitimate and legal site where gamblers can go to bet on dog and horse races in the United States. Specifically, the ransomware cashout service queries a page at betamerica.com that lets customers fund their betting accounts using MoneyPak.
I reached out to Betamerica.com’s operations team and spoke with a woman who would only give her name as “Leslie.” Leslie said the company had already flagged the account that was being used to check the MoneyPak voucher codes.
“This account was already flagged as some type of bot or compromise, and was set to non-wagering,” she said, explaining that this status prevents customer accounts from placing bets on races. Leslie said Betamerica scrutinizes the Moneypak activity because fraudsters have tried to use the codes to launder money.
“We are pretty diligent, because in the past we have had [individuals who] will try to do a Moneypak deposit and then do a withdrawal, basically trying to launder it. Bottom line is that money has to be wagered. It’s not going to be returned to you in another form.”
When I first encountered this ransomware cashout service and discovered the connection to Betamerica, I was sure the miscreants were trying to launder money through the betting site. But after my conversation with Leslie, the true scope of this ransomware operation began to come into focus. It appears to involve the cooperation of several sets of actors:
- The ransomware victims who agree to purchase MoneyPak vouchers to regain control over their PCs.
- The guys operating the botnets that are pushing ransomware, locking up victim PCs, and extracting MoneyPak voucher codes from victims.
- The guy(s) running this cashout service.
- The “cashiers” or “cashers” on the back end who are taking the Moneypak codes submitted to the cashing service, linking those codes to fraudulently-obtained prepaid debit cards, and then withdrawing the funds via ATMs and wiring the proceeds back to the cashing service, minus their commission. The cashing service then credits a percentage of the MoneyPak voucher code values to the ransomware peddler’s account.
How much does the cashout service charge for all this work? More than half of the value of the MoneyPaks, it would seem. When a user logs in to the criminal service, he is greeted with the following message:
“Dear clients, due to decrease of infection rate on exploits we are forced to lift the price. The price is now 0.6. And also, I explained the rules for returns many times, we return only cheques which return on my side if you cash them out after then we lock the account! There are many clients who don’t return anything, and I will work only with these people now. I warn you.”
In a different portion of the cashout site, there is another ad that offers “huge deposits” of PaySafe cards from Mexico for a quarter of the price of their balances.
“There are huge deposits Paysafecard – Mexico – for 25% of the face value! Get rid of the stocks!”
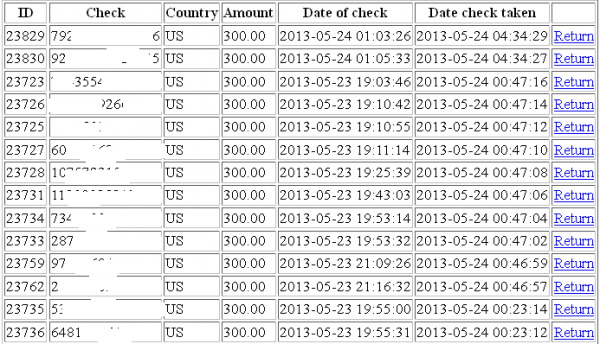
Interestingly, this service also employs a free CAPTCHA service from Microsoft, ostensibly to block or to limit the number of successfully checked MoneyPaks that a customer can redeem at any given time. It’s not clear which ransomware scam(s) these MoneyPaks are coming from, but the bulk of the MoneyPak voucher codes submitted to the service indicate that the scammers responsible for collecting the vouchers are extorting their victims for $300.
I can’t be certain how many MoneyPak voucher codes have been cashed using this service, but there appear to have been nearly 24,000 MoneyPak codes checked through it so far. At $300 apiece, that would mean this service has cleared more than $7 million in ransom money from ransomware victims.
To say that international law enforcement bodies are interested in cracking down on ransomware schemes is probably a major understatement. Ransomware scams frequently accuse victims of downloading child porn, and I think it’s worth noting that the drive to incarcerate those responsible for producing and spreading child porn has a funny way of engendering cooperation between international law enforcement agencies that don’t always work so well together to fight other types of cybercrime. I’d wager that the only way to ratchet up that level of cooperation is to invoke the specter of child porn and to do so by impersonating nearly every major national law enforcement agency on the planet.
For some perspective on how rampant these ransomware schemes have become, look no further than the FBI’s 2012 Internet Crime Report (PDF), released May 14: According to the FBI, “the most common complaints received in 2012 included FBI impersonation e-mail scams, various intimidation crimes, and scams that used computer ‘scareware’ to extort money from Internet users.”
I’d like to thank Alex Holden, chief information security officer at Hold Security, for his invaluable assistance in researching the workings of this cashout service.





Despite the message on the site being written in Russian, i don’t believe it’s operator’s native language.
The second part of the message is misspelled (and grammatically distorted) almost beyond understating. People just not talking this way, even illiterate ones.
I am thinking from an Asian language to ‘Russian’, with maybe English in between.
The federal incarcerations periods for people who receive and disseminate child pornography is quite severe for the level five to ten rated images . Just the thought of seeing a message that they where involved in such a thing would scare anyone into paying the ransom. If someone thinks they are going to do over ten years in a federal prison , then this is enough to evoke a person to act on this type of social engineering tactic.
…Especially if you take into account that a greater percentage of investigators are dedicated to this in the ‘cybercriminal investigation deptartments’ than pretty much everything else, and the stigma attached to it. Even the insinuation of being associated with child pornography is something that is leaned on a lot by people or agencies trying to ruin reputations. To take it one step further, however, it also probably needs to be mentioned that these same ‘criminals’ have access to these ‘victims’ computers and email accounts on probably the highest levels. It is already “game over” for the ‘victim’ by the time they get one of these ‘warnings’. In a way the $300 is probably their way of attempting to beg or bribe an angry and unseen god to be merciful to their reputation more than to their desire to avoid prosecution.
That’s assuming the criminals are competent.
I know of a grandmother who got hit with ransomware because the criminal thought pictures of her grandchildren were child porn.
She tried paying the ransom with an expired credit card. Good thing I happened to be in town visiting my sister that weekend…
Thank you for actually making me laugh while drinking my morning coffee (obscenely early here :)).
I tend to think that different areas of cybercrime attract different types of people, and that competence sometimes comes into play when it comes to schemes — the more complicated the scheme, generally, the less lazy and perhaps more intelligent the perpetrator, maybe?
I would actually be curious to know something we will probably never know — what percentage of ransomware people ‘purchase’ more out-of-box services from the underground (traffic, installs) as opposed to obtaining their own tools and installs from the ground up, compared to, say, those who do banking, or DDoS, or etc.
I am glad to see your grandmother did not wind up paying. It of course brings up the age-old question of what constitutes child porn in a world where people take pictures of their young children taking baths, or cultures that are less ‘puritanical’ (some take baths with their children — other cultures might be bothered by this). I have often wondered about this.
It would seem 50% is a high cut to take but it doesn’t seem like it leaves the bad guys a lot of choice, not that I feel sorry for them one bit, after all they are scamming people.
I see once again there is a WesternUnion connection as there seem to be with the Crooks that are cleaning out business accounts with transfers from those hijacked business account at whatever bank it is they deal with.
It would seem that the crooks are really dependant on getting that money wired to them whether it is with Western Union or MoneyGram but one of the two.
I said this in another stories comments as that you have to have ID to pick up a wire transfer and usually have to have some of the information on the sender.
The fact that in this case the wires are in smaller denominations may make it harder to detect rather than the bigger amounts from the business account scam wires.
That being said, the crooks wouldn’t be spreading these out too much for such a small amount of cash as they might with wires that are in the higher 5 to 9 thousand range.
One would have to believe that in these cases some of the same Western Union/MoneyGram locations are being utilized to help with these wires due to the fact that you need ID, you can only pay mules so much to pick them up on that side( which I don’t see them doing , or using the same people)
So wouldn’t you see the same stores or same franchisee popping up on the radar on Western Union or Money Grams end? I mean they must see some patterns in the transfers and the stores and locations being used.
I have to really wonder how much of an effort they are putting forth to make sure their stores/franchisee/agents are using to check and make sure about the people getting these wires.
I also wonder how much of an effort they are putting into stopping these, because they are making a lot every time a wire is sent through them and the more you are sending the more they are making.
I realize a lot of legitimate wires are sent, but for the fraudulent wires they must seem some patterns, ( same area, same store/franchisee/agents being used in frequency ) they obviously would have some type of way to track wires when their is a report of fraud involved after the fact.
What I am getting at is what safeguards to they have in place to prevent it and what are they doing to prevent wires obtained in crime.
I do wonder though how concerted their effort is in preventing it, because it would seem in a lot of cases of the business account fraud transfers their are some serious amount of wire transfers going to the same areas over seas in that under 10k area, but in short spurts when an account is being cleaned out.
I just have to wonder how much effort they put in to really stop it, because this has been going on a long time, with these small transfers it might be harder to detect due to the dollar amount, but I could be wrong about that to if it is always in similar denominations and in short spans.
You never heard much out of Western Union or MoneyGram on it, but yet for years the criminals are using their services over and over so it would see they either know their is no real risk, or they have stores/agents/franchisee’s that are complicit in it, or maybe they have invested in some locations to help get around the safeguards from the inside.
If they were in on the inside they could easily have someone prevent no documents and say they did by putting in bogus info, or with some phony id and process it knowing so, and that if any questions arise, claim it was an honest mistake…
I’d love to hear Western Union/ MoneyGram’s take on this
WoW, now this is one thing I can say never happened to me yet.
I guess i have no money, don’t run my own business, so nothing worth ransoming haha. But man what a horrible feeling that must be.
As far as western union goes. If you read the article apparently they are the very last part of the laundering scheme. Its just a more reliable mail system. I mean I wouldn’t expect anyone to go after the american post office either. I’m sending a money order right now to pay a beer ticket lol.
and they are using betamerica too? That is crazy! and I guess once again. They still need guy on the inside….
‘To say that international law enforcement bodies are interested in cracking down on ransomware schemes is probably a major understatement.”
So, international law enforcement is going solely after miscreants in this scenario of ransomware money transfers going through legal websites; meaning that the prepaid card services (MoneyPak, PaySafe or Ukash) and legitimate and legal sites (betting site betamerica in this instance) are operating legally? Are the prepaid card servicers and legitimate webites not required to be FinCen registered?
MoneyPak, parent company GREEN DOT CORPORATION, is FinCEN registered and seemingly money laundering. http://www.fincen.gov/financial_institutions/msb/msbstateselector.html
Paysafe–parent company paysafecard, Ukash– parent company Smart Voucher Ltd, and betamerica–parent company Lien Games Racing LLC, I did not find in the FinCEN database.
If I’m understanding this correctly, and they are charging 60% to get the money out, couldn’t they place bets through Betamerica spread out across all contenders in a race, and take the losses as a cost of doing business? That would launder the money.
I think they just want to cash the money out though. Unless you mean they should just learn how to bet on some horses and use the money for fun? hey why not. lol.
40% of something is better than 100% of nothing as they say.
(I realise that one would receive some percentage from betting even if you just blindly put all your money on the favourite but these people don’t appear to be idiots so I can only assume that percentage is less than 40).
In all fairness you can’t put the spotlight on WesternUnion. Yes criminals use their service, so do MANY legit people. If you look at the big picture they have so many locations worldwide its staggering. They are just another medium that is being used. Yes they profit from transactions and yes they most likely have very little incentive to change their policy but we really need to look at the root cause of the problem.
People need to do their homework! If you know for a fact you weren’t doing anything wrong ie. downloading child porn then why would you be scared? Call your local FBI field office or whatever and straighten it out with them.
It seems to me that the biggest flaw in most cases is human error.
yes i’m sure the amount of criminals and also ratio to legit customers is one of the biggest factors in these cases.
and your right. If I was innocent of any wrong doing and did really truly need to feed my family? I would be relentless calling every number and writing to every address i could find.
Ridiculous to believe any reason not to.
I do agree with you however the prospect of potentially being associated with child exploitation – even if a person is exonerated in the end – is very scary and potentially life altering and not for the better due to stigma, career and so on. And of course many users are not at all savvy with computer crime also.
I can easily see why some people would pay up which unfortunately just makes this despicable scam more alluring for criminals.
and where do you draw the line 16, 17, or 18? and is it just some gov’t agent looking at a picture guessing a girls age that can determine a mans future?
Its ironic how Hoover started keeping lists on homosexuals in the 50’s, when he was a huge homo himself.
Just as ironic as all these religious folks wanting to crucify guys for looking at 17, 18 year old teen girl pics….When they are usually the ones in society marrying 14 yr olds lol.
Apparently they can and do, which is how they get young-looking people to lure paedophiles to meet them in order to get arrested. As an added bonus your Supreme Court made just getting arrested an acceptable reason to obtain and store your DNA. And of course your court records are public. So does it matter if one cannot be sure? Too many cases in your country of females getting into bars that are in their teens, getting ‘taken home’ and then having someone claim ‘I did not know they were underage, after all they were in a 21 or over establishment”. Since you said you like rap/hip-hop, I will give you the example of Akon.
Two points to keep in mind:
1) How long before the ransomware guys actually load some child porn on the compromised PC – for whatever reason? And possibly conceal it so that you don’t even know it’s there.
2) It is illegal to even LOOK at child porn. Seriously. If the FBI forensic analysis shows you viewed any of the images someone else downloaded to your machine, you are in trouble. If there is ANY suspicion that it’s yours, you are in trouble.
You get hit with ransomware related to child porn:
1) Make sure you’re backed up with a CLEAN image, and/or
2) Wipe (full wipe and reformat) and reinstall from scratch or from a known clean image. or
3) Destroy the hard drive with a hammer, get a new one, reinstall from scratch – if you don’t know how to clean a hard drive.
Much easier to protect yourself by using browser protection tools like NoScript and making sure your browser and Flash are up to date – and Java is disabled.
NoScript is updated regularly with new protections against new hacking methods and is a must for Firefox. I don’t know if the equivalent scripts on Chrome are as good as NoScript, but there are several worth checking out.
Script blocking in browsers is a nuisance but absolutely necessary.
Фgreed. And if I were this sort of criminal probably the trickiest way of ensuring this would be to take a legitimate file the owner has and uses often and not often, duplicate the timestamps and names, and replace these files with offending images, virtually guaranteeing such a thing happening — maybe even before the ransoming demand for extra terror. It is a good thing I am not a criminal.
One problem with your idea is pretty obvious if you think about it — destroying data makes one look guilty like a criminal (obstructing justice, destroying evidence). And one never knows how ‘bad’ the actor one is up against may be, or how desperate. Just like some people have no problems with ‘swatting’ people other people would have no problems with putting in an ‘anonymous tip’ who knows how far down the line. One never knows the intent, level of maliciousness, or the desperation of the people they are up against, which means this sort of thing will always work in the criminal’s favour.
If these were truly malicious people (and as the well dries up when/if few people pay) I could see the sums asked for greatly rising with target specificity. It always goes on a spectrum with the majority of people going one of two ways: Fewer victims, larger ‘takes’ or many victims, smaller takes. This $300 (which seems about average for any ‘reload card’ scheme) figure is somewhere in the middle edging toward the latter. As a rule of thumb, it probably makes the most sense to consider the cost that the market would bear, and combine it with the criminal’s perception of how much money they ‘should make’ in a given time frame or for a certain amount of ‘work’ and not particularly per victim).
From another perspective, people who tend to think the best of people in general, or try to put themselves into the mindset of the ‘criminal’ without letting go of the way they themselves think probably think that it is cheaper to pay the ‘criminal’ off than it would be to deal with the hassle of cleaning the machine or the possibility of being hassled by law enforcement. Even if they called the FBI as a victim, and obviously the FBI will not respond or investigate to most of these smaller claims, but let us imagine they would… How many people would really want anybody going through their private files, love letters, drunk sex pictures, possible accounting records, or the possible loss of their machine for an unknown period of time. Again, the criminal comes out ahead.
@voksalna
Well, I don’t think the miscreants pulling this scam would go to such lenghts to convince victims to pay. First of all that would themselves in touch with kiddieprn. While running their ransomware scam might be tolerated in their country to various degrees, activelly loading illegal images on victimspcs would place them higher on the radar screen, while, I guess not increasing significantly the success rate. It pains me that people are paying and perpetuating this scam in this way but the reason the victims decide to pay is not always related to have something to hide. They simply are computer illiterate but need their computer or the data on their computer. If they seek help from a computer professional, as they should, they reason the fees would run anyway into 150-200 USD range (many ransomware scams seem to ask less than 300USD), they also might think it would take more time to fix the computer and that they might lose their data (as a computer-fixing professional would make no attempt at data recovery before reformatting the computer or, if he does, it will charge data-recovery fees.
For $300? No. But when/if the victims dry up or people try to get more money out of a similar scam they will. More work for more money, and especially more likely as people rely more and more on social networking and companies screen based on Google. So for $300, no, but if you add a zero or two (or more, who knows) on the end, it is a lot more likely — just like the hauls from things like banking trojans take more work to get out of the system, they pay off more when they do. There is a math/science to it, a form of game theory if you want, which is not exact but it does exist.
I just clean an infection from someone that had the FBI virus, with the moneypak ransome. The screen even has the user’s face (access to laptop camera) and an alert that there is childporn on this machine.
It really scared them, and the user called me within minutes. Having him pull the battery on this PC and await till I got on it, cleaned it of the rogue and all appeared good.
We talked on where he was last (obvious a porn site but he “never” downloaded, only typed the URL in then within seconds…). My advice, made a bootable USB drive with a browser on it. Made a duplicate (USB drives are cheap). Boot from it, do your browsing. If something happens, shutdown, wipe the key, clone from the master. Rinse. Repeat.
I wonder what some folks would do without Krebs, let alone me 😉
ya wow…welcome to 2013. I basically have to buy a new hdd. the one i have had an emergency firmware update…that i got way too late. only after did already start having boot problems did i realize.
I don’t have the fbi virus. But i just live with it cause i figure what else am I going to do. as long as i an do what i want to do on it without any problems.
Let the vigilante deluded psychotic self righteous religious nutsos, who are probably snitch-o-matics, spy on me like the true perverts in the world. Spies = why the human race is doomed for failure. But i guess nescessary to fight fire with fire.
Thats a great idea to have like a disposable hdd almost. I even did diskpart /cleanall and it didn’t work.
and then i figure am i going to stop going to porn sites? not likely. am i gonna stop playing the latest online pc video games? nope. am i gonna stop going on facebook. doubt it.
so why bother? especially if they are at least catching other hackers trying to profit off of me, bully me, or worse?
You also bring up the excellent point that. All you need to do is visit a url….and booom. You should see how many ips you connect to on port 80, 443, 53 etc… its scary. and whos who. most times its just a rented server.
They intercept websites on a regular basis now as well. Lots of websites are virused.
And you still here these littler nerds and online companies still trying to blame the user…..taking no responsibility for their security at all…. its drives me nuts.
^ I look like a foreigner typing here…lol
Hey i love foreigners. I was just reminded recently about how foreigners have kept alot of my music and culture alive. For example Hip Hop.
Not the hip hop on the radio…but the real hip hop for real heads. If it wasn’t for the internet and foreigners supporting the real artists with their wallet and servers….my hip hop would be dead.
The foreigners know more of the history and about the culture then Americans do now. no lie. For the past 15 years they have been supporting all the old artists they no longer play on the radio, and underground artists that never got air play.
they have also been the ones who have been keeping breakdancing and dj’n competitions alive. I owe the foreigners alot….and i guess thats one good thing that came out of having American soldiers stationed in other countries…lol
You can never convince me the world doesn’t love America. or that America doesn’t love the world.
I need to stop posting Sorry for the spam Mr K.
You should also flash your BIOS.
Bootable USBs FTW! I have a handful of those lil guys and their great. Nice to get a field report Ed Ski. I wonder if any employees working for the feds ran into this? Lol oh the irony!
p.s. CooloutAC, switch to decaf 🙂
lol I’m a Mavis Beacon fan.
“How much does the cashout service charge for all this work? More than half of the value of the MoneyPaks, it would seem.”
This is what I mentioned in an earlier post: the cost of doing business in the underground economy. It’s like fencing physical goods: if the fence gives you more than 15% of the value of the stolen goods, you’re doing good.
Bootable USBs for porn sites? I go to porn sites all the time. The wonders of Linux and NoScript! 🙂
50-60% actually makes sense if you take into account these peoples’ business models, how much a casher would typically get for ‘carding’ and risks for that vs earnings (less probably) and risks (fewer almost certainly) for this, the intermediary’s earnings, the cost for each intermediary step, plus the fees involved for the actual purchases and transfers. To put it into perspective, read some of Brian’s other articles about how much a ‘casher’ might make, or at least one that is not part of a big gang with a ‘leader’ (though that might provide some context for how much they probably make for doing this).
yo, krebzy. get these ransomware bitches out of biz, get their asses firing, all true crabz are tired of them! they shit where they eat. without them everyside would be gladfull )
thecc team )
Just had to deal with this yesterday (not on my computer). Thanks for the info.
This was the link that helped me remove it, a little tricky:
http://malwaretips.com/blogs/fbi-lock-screen-virus/