A 2011 hacker break-in at banking industry behemoth Fidelity National Information Services (FIS) was far more extensive and serious than the company disclosed in public reports, banking regulators warned FIS customers last month. The disclosure highlights a shocking lack of basic security protections throughout one of the nation’s largest financial services providers.
 Jacksonville, Fla. based FIS is one of the largest information processors for the banking industry today, handling a range of services from check and credit card processing to core banking functions for more than 14,000 financial institutions in over 100 countries.
Jacksonville, Fla. based FIS is one of the largest information processors for the banking industry today, handling a range of services from check and credit card processing to core banking functions for more than 14,000 financial institutions in over 100 countries.
The company came under heavy scrutiny from banking industry regulators in the first quarter of 2011, when hackers who had broken into its networks used that access to orchestrate a carefully-timed, multi-million dollar ATM heist. In that attack, the hackers raised or eliminated the daily withdrawal limits for 22 debit cards they’d obtained from FIS’s prepaid card network. The fraudsters then cloned the cards and distributed them to co-conspirators who used them to pull $13 million in cash from FIS via ATMs in several major cities across Europe, Russia and Ukraine.
FIS first publicly reported broad outlines of the breach in a May 3, 2011 filing with the Securities and Exchange Commission (SEC), stating that it had identified “7,170 prepaid accounts may have been at risk and that three individual cardholders’ non-public information may have been disclosed as a result of the unauthorized activities.” FIS told the SEC it worked with the impacted clients to take appropriate action, including blocking and reissuing cards for the affected accounts. “The Company has taken steps to further enhance security and continues to work with Federal law enforcement officials on this matter,” it declared in its filing.
FIS’s disclosure to investors cast the breach as limited in scope, saying the break-in was restricted to unauthorized activity at a portion of its network belonging to a small prepaid debit card provider that it acquired in 2007. But bank examiners at the Federal Deposit Insurance Corp. (FDIC) who audited FIS’s operations in the months following the 2011 breach and again in October 2012 came to a very different conclusion: According to a report that the FDIC sent May 24, 2013 to hundreds of FIS’s customer banks and obtained by KrebsOnSecurity, the 2011 breach was much larger than previously reported.
“The initial findings have identified many additional servers exposed by the attackers; and many more instances of the malware exploits utilized in the network intrusions of 2011, which were never properly identified or assessed,” the FDIC examiners wrote in a report from October 2012. “As a result, FIS management now recognizes that the security breach events of 2011 were not just a pre-paid card fraud event, as originally maintained, but rather are that of a broader network intrusion.”
Indeed, the FDIC’s examiners found that there was scarcely a portion of the FIS network that the hackers did not touch.
“From review of the previous investigation reports, along with other documentation provided by FIS, examiners and payment card industry experts identified over 2,000 touch points that indicated a broad exposure of internal FIS systems and client related data,” the report notes. “These systems include, but are not limited to, the The New York Currency Exchange ATM network, prime core application systems, and various Internet banking, ACH, and wire transfer systems. These touch points also indicated approximately 100 client financial institutions, which appear to have had sensitive data exposed by the attackers.”
In an emailed statement, FIS maintained that “no client of FIS suffered any monetary loss as a result of the incident, and stressed that the report is based upon a review that was completed in October 2012.
“Since that time, FIS has continued to strengthen its information security and risk position, including investments over two years of $100 million or more, as part of our goal to provide best-in-class information security and risk management to each of our 14,000-plus clients. We have openly and regularly communicated these initiatives, our progress and results to our clients and shareholders through meetings, monthly updates, quarterly public disclosures, Board materials, educational webinars, and more.”
WHAT DOES $100 MILLION BUY?
Nevertheless, investors may be less than pleased about how FIS is spending its security dollars. The FDIC found that even though FIS has hired a number of incident response firms and has spent more than $100 million responding to the 2011 breach, the company failed to enact some very basic security mechanisms. For example, the FDIC noted that FIS routinely uses blank or default passwords on numerous production systems and network devices, even though these were some of the same weaknesses that “contributed to the speed and ease with which attackers transgressed and exposed FIS systems during the 2011 network intrusion.”
“Many FIS systems remain configured with default passwords, no passwords, non-complex passwords, and non-expiring passwords,” the FDIC wrote. “Enterprise vulnerability scans in November 2012, noted over 10,000 instances of default passwords in use within the FIS environment.”
The bank auditors also found “a high number of unresolved network and application vulnerabilities remain throughout the enterprise.
“The Executive Summary Scan reports from November 2012 show 18,747 network vulnerabilities and over 291 application vulnerabilities as past due,” the report charges.
What’s more, investigators probing the breach at FIS may have been denied key clues about the source of the intrusion because FIS incident response personnel wiped many of the compromised systems and put them back on the network before the machines could be properly examined.
“Many systems were re-constituted and introduced back into the production environment before data preservation techniques were applied,” the report notes. “Additionally, poor forensic preservation techniques led to numerous servers being re-imaged before analysis was completed and significant logging data was inadvertently destroyed. Several servers, key to the investigation process, were re-introduced into the production environment and subsequently re-compromised due to misconfigured baselines and inadequate security testing outside of corporate policy.”
Analysts say FIS’s problems almost certainly stem from having to cobble together various networks and systems that it inherited from a long series of corporate acquisitions over the past few years. The FDIC report notes FIS had originally set a target completion date of year-end 2012 for this project, but has since revised the projected completion date to June 30, 2013.
“It appears the extension is necessary due to the immense scale of the project, which consists of approximately 30,000 servers and operating systems, another 30,000 network devices, over 40,000 workstations, 50,000 network circuits, and 28 mainframes running 80 LPARs,” the FDIC examiners wrote. “The vast scope of this project is being addressed in a formal process which requires additional time to complete. Nonetheless, this information asset inventory and risk rating process is critical to effective information security and risk management efforts; and they should have been implemented prior to regulatory intervention.”
MATTERS REQUIRING ATTENTION
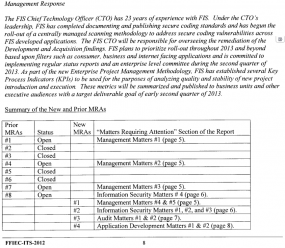
In its initial audit in 2011, the FDIC found eight MRAs, or “matters requiring attention.” Ron Lindhart, a former bank examiner for the Office of the Comptroller of the Currency (OCC), said MRAs are extremely serious matters that financial services firms ignore at their peril. In its Oct. 2012 follow-up report, the FDIC said while FIS had addressed four of the eight MRAs it identified earlier in the year, the agency had since documented an additional four MRAs.
Lindhart called FIS’s eight MRAs a “high average” score on a report card in which high scores are not a mark of achievement.
“I’d say in a typical examination, you might have two or three, maybe four MRAs, so eight is a significant number,” said Lindhart.
Financial institutions that fail to address MRAs in a timely manner and to the satisfaction of the banking regulators can face fines and can even be shut down. But FIS is a service provider — not a bank — and while the company’s role as a core provider for thousands of banks means that it can be audited by regulators, those regulatory agencies can’t levy fines against the company or shut it down directly.
Rather, Lindhart said, the FDIC’s leverage comes from taking their case to FIS’s customers. Perhaps that is why the FDIC’s May 24, 2013 letter attached the report began with the message, “We are sending you this report for your evaluation and consideration in managing your vendor relationship with FIS.”
Translation? Get FIS’s customer banks to pressure FIS and create the fear that they may lose business by not adequately addressing the security weaknesses. “It’s very effective in getting corrective action when the serviced banks find out about the situation,” Lindhart said.
Julie Conroy, a research director with the retail banking practice of Aite Group, a Boston-based research and advisory firm, said a major reason FIS is receiving such regulatory scrutiny is that the company is not just a credit card processor: thousands of small financial institutions outsource their entire information technology systems to FIS.
“It’s basically outsourced IT infrastructure for these banks, including all of their customer information — names, SSNs, DBAs, account balances — all of that is sitting at FIS,” Conroy said. “These kinds of security lapses threatens a key part of the trust relationship that these banks have with the core processors, and [the banks] expect state-of-the-art security.”
But Avivah Litan, a fraud analyst for Gartner Inc., said many of FIS’s customer banks are smaller institutions that can’t exactly afford to pick up and move their operations to a competing service provider, such as Fiserv or Jack Henry.
“It’s very hard for these banks to switch processors,” Litan said. “The pricing is typically the same, but it takes a lot of manpower to test new systems, to stage it and roll it out in a way that doesn’t disrupt your service.”
Litan said for these institutions, switching service providers is akin to the hassle most consumers experience in trying to switch their Internet service from a cable to a DSL provider – only 100 times harder and more expensive.
“So many of these processors neglect security and have awful customer service, in large part because the switching costs are so high that they can get away with it,” Litan said. “There needs to be more heat on these processors, and I think this is a pretty savvy and important move by the regulators.”
CONNECTIONS TO OTHER ATM CASHOUTS?
The $13 million ATM cashout against FIS in 2011 bears a remarkable resemblance to several similar heists involving organized crime, malware and ATM cashouts. In May 2013, federal prosecutors in New York unsealed indictments against eight defendants allegedly involved in two separate cyberattacks that used prepaid debit cards to siphon a total of $50 million from ATMs across the globe; the first was a breach around Christmas 2012 that netted thieves $5 million from an Indian prepaid network, while the second siphoned $40 million from a bank in the United Arab Emirates in February 2013.
Meanwhile, the hackers responsible for coordinating the ATM heists, raising the daily withdrawal limits and monitoring the withdrawals were not named in the New York indictments.
In its emailed statement to KrebsOnSecurity, FIS said the criminal actors involved in 2011 attack on its own networks “are currently the subject of an ongoing federal criminal law enforcement investigation, and several individuals have been arrested and charged with various crimes.” FIS declined to say whether those arrested were involved in the two thefts connected to the New York investigation.
The FIS breach and the two separate incidents encompassed by the New York case are eerily similar to an intricate 2008 attack against RBS WorldPay. In that heist, crooks obtained remote access to RBS’s systems, raised the daily withdrawal limit and used 44 counterfeit prepaid cards to suck more than $9 million from at least 2,100 ATM terminals in 280 cities worldwide.
Federal prosecutors alleged that the 2008 RBS theft was orchestrated by at least eight men from Estonia and Russia — the alleged ringleader, Sergei Tsurikov, was extradited to face charges in the United States. His trial is pending and much of his case remains sealed.
Another key figure in that case was Viktor Pleschuk of St. Petersburg, Russia, who monitored the fraudulent ATM withdrawals remotely and in real-time using compromised systems within the payment card network. Pleschuk and Russian accomplice Eugene Anikin were arrested and charged in Russia. Prosecutors asked the court for five- and six-year sentences, but those requests were ignored. In February 2011 (around the time of the FIS breach) Pleschuk and Anikin agreed to plead guilty for their roles in the RBS heist in exchange for suspended sentences — probation, but no jail time.





Im in IT security incident response industry for quite a while and there is one thing people fail to realize.
The point here is simple: those who attack with high skill, are not enginers nor have studied any computer science at all, yet they excel(!) at writing and debugging C/ASM code. People who build and manage IT infrastructure are educated engineers who think, act, work in predictable ways and with predictable mistakes, they are educated and trained in one way, likewise they solve problems and look into thing in exactly same ways.
Well those who attack think out of the box, they dont have any CS degree, so they will act in ways no engeneer will imagine and has forseen, i have seen this over and over again.
I think its time to seriously push out-of-the-box style thinking into IT security guys, otherwise well be spending hundereds of milions into nothing but paperweight.
The problem is you cannot. That type of thinking is either a part of a person’s unique neurochemistry and/or it is developed and nurtured from a very young age. The best they could do is attempt to create a facsimile of that method of thinking based on case studies. Not everybody can “think out of the box”. In fact, most cannot. Of course, now none of this is very original, but back when these sorts of cashouts were first happening, it was. So such predictive thinking now can be possible for things like this. There will always be the next “black swan”.
The ability to think outside the box has no relation to one’s possession, or lack, of degree. People who perform these types of attacks are generally more out of the box thinkers because it’s a requirement of the job, not because they don’t have a CS degree. Process oriented thinkers don’t exist in that environment, not because they have a CS degree, but because they aren’t a fit within the criminal organization. Correlation does not imply causation. Especially in this case.
This has nothing to do with degrees or education or even thinking outside of the box. But its for the same reason you should separate your QA and programming teams. because building the system gives you tunnel vision focusing on it working not breaking.
I always have found the best approach is to have two QA teams when you can afford it — one given a white box to exhaustively test typical use cases, and the other (smaller) team given a black box to test against which will probably provide more insight into ‘edge cases’ the former team would not think of.
I don’t think ability to “think outside the box” or disassemble C/ASM had anything to do with being able to guess default or blank passwords on thousands of devices. Similarly I don’t think formal engineering training prevented the IT people from setting sane passwords and access controls.
I believe attackers do view the problem of [in-]security from a different perspective than those who try to defend. Attackers had an advantage because then are mostly in control. They determine who, when, where, how, etc. I also believe, in general, attackers have a greater level of motivation than do the defenders.
Attackers, in general, are self motivated and thus don’t follow the same rules, conditions, POLITICS, BUDGETS, etc that defenders often have to. So I believe are less likely to be conditioned to be IN-the-box thinkers.
In my opinion, we ALL can think out of the box. It is our conditioning/ believes that we are exposed to that changes this.
As children, I think by default, we are always making observations, pushing boundaries and finding ways to do things that may not be obvious to those around us. Simply because as children, the “blinders” have not fulling been “installed” yet.
We as adults, install similar blinders on our children, as those that were installed on us by family, government, media, SCHOOL, TRAINING, WORK, etc because those “blinders” have now become our comfort zone.
So in terms of security, IN/OUT of the box thinking is really not the issue as much how comfortable and willing are we to try things that we previously did not think/ believe were worth a try?
Just an example for discussion –> Maybe try utilizing non-technical artists, marketeers, etc to assist to see a problem from a perspective that a technical person would never see it — and actually listening to them. Because non-techies don’t have the same ‘blinders’ that techies may have.
Just my thoughts 🙂
The problem is that bankers and today’s IT pro’s are airheads. The blind leading the blind.
They have no concept of “property.”
Communists.
QUESTION:: If you put confidential data on a hard drive, and then later sell that drive on eBay, then… who owns your data????
QUESTION: If a bank puts HIGHLY confidential data on SOMEONE ELSE’S disk drive… who owns the data????
Only an airhead couldn’t figure that one out. So, why are America banks allowed to store YOUR American data on organized crime servers in ?????
Cloud Computing is for Airheads and Communists. Airheads are clueless. Communists know EXACTLY what they are doing.
How can those guys (Viktor Pleschuk and Eugene Anikin) get off scot-free after pleading guilty in taking part in the RBS theft?-something is going on here. 🙁
It’s obscene IMO – particuarly when non-violent and “victimless” crimes such as mere possession of an amount of narcotics deemed to be for personal use only routinely get much harsher (read prison) sentences. Or for that matter larceny such as shoplifting.
I use “victimless” (quotes) not to get into a debate on illicit drugs but to illustrate how absurdly light I think the sentences these guys have recieved after directly violated other people’s property on such a large scale.
Its because apparently Russia approves….
Because like my grandfather said,
“AT THE END OF THE DAY IT’S NOT ABOUT MONEY. IT’S ALL ABOUT MONEY”.
40,000 workstations and 30,000 servers for only 14,000 clients.
Gee, two servers for every girl and boy. Plus 28 mainframes with 80 LPARS! How can they stay in business?
They could just use paper since they seem to have several employees for each client as well. They could actually have a person assigned to each customer.
Client != 1 person. Reading the article gives the clue. Clients are banks and other money processing companies.
Many systems are also virtual.
SgSanford – Maybe their clients are all banks? Deep-pocket clients providing multiple streams of income from all over the country might require all that compute power..
I like how in this article that it points out the similarities between the case of FIS with the large cash outs that happened in New York City and across the globe. I find this fact to be rather fascinating. maybe Mr. Krebs is onto something here. Only time will tell……..
‘FIS incurred a loss of approximately $13.0 million, or $0.03 per share, during the first quarter of 2011 related to unauthorized activities involving one client and 22 prepaid card accounts on its Sunrise platform.’ (from the SEC filing)
When put in terms of $0.03 per share, these sorts of cashouts almost seem like a very small crime to a very many people — i.e. less harm to individuals, more to the ‘system’ — as opposed to POS grabbing, which tends to cause many individuals quite a bit of pain and loss of money/time.
Obviously the costs of the breach get passed on to FIS’s clients, who then pass it on to their own customers (I am sure with some padding in each step along the way), but I do wonder if this is not a kinder ‘carding crime’ than crimes involving POS sniffing/scraping. It strikes me that the further back from interface with actual individuals, the less it actually hurts ‘more people’ — that is, the loss shrinks compared to volume.
“Devil’s advocate” stance?
How would you know if this didn’t hurt anybody?
What if one of the 8,000 accounts was some unlucky poor person who had trouble keeping his account in the first place? I mean they weren’t even admitting to how much was compromised. The bank auditors exposed most of it. It might even be more accounts then that. what if now poor people will be paying higher banking fees at those institutions?
Just because this is not a face to face crime does not make it any less harmful. I mean just like when u get your house robbed, even if you have insurance, its a horrible feeling that will haunt you for the rest of your life. I mean if you stole 1000s from me and i found out who you were? I don’t care if you didn’t put a gun to my head dude.
Your not robin hood fighting he system dude. Your just robbing poor people. Get a grip on reality. I told you to grow up already. Community organize, vote, go into public office, sign petitions, hold non-violent protests in the street….etc…. the world is always changing for the better…..robbing banks does nothing but make it worse. Your simply greedy.
Fighting the system? These hackers are nothing more then selfish thieves with giant egos. They think they are superior to other humans, have absolutely no empathy, like the bots they are…. nothing but a virus on humanity.
the barbarians of the internet age. Doing nothing but creating fear among poor people, ruining country relations and economies, pushing us closer to world war.
You are your own worst enemy if you don’t want more of a police state.
Hillary was right about one thing.. We are losing the propaganda war. Even if its only to young children. We have to start getting more Americans online.
And for the 2 guys that stole 9 million dollars to get only probation and no jail time? Thats an insult to my country. It seems the Russian government openly supports hacking of American citizens now.
I see more drone attacks in the future.
You clearly missed the part where a ‘client’ is a financial institution, and, in fact, what FIS does. All I have to say to you.
Yeah, it’s pretty central to the story: This is not about consumers. FIS is probably the largest service provider to banks. As stated by one of the experts quoted in the story, many banks completely outsource their internal and back-end operations to FIS.
I assume each bank/client/account, is responsible for someones money? In the end thats who gets hurt the most isn’t it? These banks will make up the money some how, I’m sure they are not gonna take a cut in their christmas bonus. In the end it will be the poorer customers most affected imo.
This guy voksalna is trying to imply these guys should get a slap on the wrist for robbing 13 million? A victimless crime? They are good people?
Not when insurance premiums and fees go up and some good people who did nothing wrong get dropped or laid off. I don’t agree. Businesses are people after all, even our supreme court says so now. They are def full of human beings that are affected by this.
Were these hackers doing us a favor by exposing the security flaws? no. thats just another typical hacker response that to me is always disingenuous no matter what the circumstances. They robbed people…..nothing more.
now if they were working with some security firm hired to try and expose flaws thats diff.
Sorry, one more thing: you apparently think I am Richard Nixon or something, still. Quit attacking peoples’ character randomly, or you will next have me asking why the hell should anybody bother being legitimate if you’re just going to accuse them of whatever your warped brain concocts.
But I gave up on you so this is my last reply ever to you. I wish you well in life. Maybe someone will teach you a lesson about how to be a rational, caring, and non-prejudiced human. I hope for your sake they do. I may not care what you accuse me of being but somewhere down the line you will wind up insulting the wrong person, having them act ‘inappropriately’ towards you, and then you will probably go around calling yourself a victim and saying you knew it all along. You seem to like sayings about reaping what you sow, so I will say only that you should be careful to not sow such bad things upon people who have done nothing to you.
I am not Buddha. So that is all you will get from me. Have a very good life. 🙂
You hope someone teaches me a lesson huh? lol.
Your nothing but a Russian hacker to me….. I hope someone teaches you one.
“we only hack you because you deserve it” ya i’ve heard that one before. typical hacker excuse.
Watch it unless you want a visit from me because you’re catching my eye. “Coolout” bud.
maybe instead of going after pedophiles for looking at 17 yr olds. Or gov’t officials taking pictures of their dick. or some redneck sheriff taking a bribe to let the quarterback out of jail.
maybe hacker groups like anonymous should go after other hackers, that virus and rob their family members…..
hackers are the biggest terrorists in the world right now, and the biggest threats to national security.
Again, like my grandfather said,
“AT THE END OF THE DAY IT’S NOT ABOUT MONEY. IT’S ALL ABOUT MONEY”.
my grandpops says…..”money talks shit walks”
Heh. Well he got that right anyway. 🙂
No, you’re not the devils advocate in this instance.
Two keys in this article are:
1. $0.03 per share.
I was always told the banking industry would rather pay out $2 million in fines, restitution and other expenses than pay $100 million to secure their operation. The only thing that has changed in many operations is the added overhead of $200 million in executive bonuses.
Once the banking industry adds two factor authentication to client accounts and puts a hold on the classic money mule deposit check, immediately wire out most of the cash, I will see that as a step in the right direction.
Hell, even the MMPORG I play requires two factor id.
2. The network had blank, default and easily guessed passwords.
LOL…seriously. A big mistake I see people make regarding passwords is: hard to type = secure. Not the case. Using long passwords, especially with a non-standard character set, really ups the difficulty of cracking the password. The other standards are encrypting the authentication traffic and disabling the “admin”, “administrator” and other default admin logins.
If they have not taken the step of changing the default password are they even base-lining their systems and traffic, monitoring connections, check-summing the key OS commands, running nmap, Metasploit and Nessus against their systems, keeping off-server syslogs and bash histories? Probably not.
We assume they have any idea what those assets are. Incident Response and Technology Solutions mean nothing if you don’t know what your assets are, where they are located, and what they’re used for. If they know about 30k, they probaly have twice as many that they don’t even know exist.
Unfortunately, so many financial institutions put all of their faith in their core processor. We’ve talked to a number of banks who have been told by FIS and their cohorts that they are providing all the security the bank needs.
My COO actually just wrote about this problem about a month ago. http://blog.digitalarmored.com/2013/05/myth-my-core-processor-handles-security.html
I worked for FIS in the Business Continuity department for 2 years. The main problem with the company is their management across the board. The company has been on a mission to lay off numerous employees across the board. They let go of several people I knew in IT that could do the job better than their managers.
I hope this report makes Gary Norcross see what his company is turning into. It’s time to look at your management practices.
Brian,
From what I can make out they are insinuating that the incursion had to do with eFunds’ systems. I had thought maybe it was via Metavante’s and from there to FIS to eFunds? I saw they lost a lot of audit trails.
That’s what happens when you fire your best cyber security talent and outsource it to Asia…
Security 101 was missed! Change default passwords and make them expire every 90 days. It doesn’t take an IT genius to follow good common sense.
Plus make the p/w complex. One does not need a MENSA IQ to perform basic security.
provided you don’t send them over the network in clear text….
or worse wirelessly in clear text….
Based on what little security they had, I would have to put 98% of the blame of this on FIS and the other 2% on the attackers. This is the 21st century and whatever IT idiots convinced FIS that this form of security solution was adequate proves that any idiot with security credentials s and no experience can fleece a company just as bad as attackers can fleece the same company.
The real criminals are FIS and not the hackers. If you have something of value and know it is valued and wanted and you do nothing to protect that item, you are just as guilty if it gets stolen.
When will clients such as those FIS had begin to demand a thorough scrutiny of a security solution BEFORE putting others at risk?
what? wait what? lmao. I don’t even know what to say to that. holy !@#$.
another typical hacker response imo.
You do realize it was peoples money in those accounts? Like human beings?
You hackers can find an excuse to hack anybody. And then tell yourselves its a rare occasion, when really its becoming an epidemic.
i’m not saying FIS doesn’t deserve alot of blame. but 98-2? and then you say FIS is the real criminals not the hackers? lol…..
“You do realize it was peoples money in those accounts? Like human beings?”
Good question. Did management ask themselves this? It’s not Joe Bob’s One-Stop shop. It’s a financial institution with 35,000 employees providing services to thousands of companies.
Default and blank passwords? My grandmother knows better.
“You hackers can find an excuse to hack anybody. And then tell yourselves its a rare occasion, when really its becoming an epidemic.”
I would like to leave a million dollars in a parking lot and go for coffee and have it be there when I get back. It’s my property. Do I expect that to happen? Hell, no.
We regulate trucking companies. We inspect them for safety, license them, limit their loads and require them to tie down their loads. If these steps are not followed, we take the truck off the road. If the trucker has a fatal accident and is found negligent, we charge him criminally and fine the company, sometimes revoke their operating license.
With banks and financial institutions, a simple “trust us” seems to be sufficient. Blank and default passwords are the same, in my book, as leaving the cash out in the street.
Or did banks just become targets of criminals recently?
You do know all three credit bureaus in the united states outsource all our information? I mean literally all our socials, all our bank account numbers. all our credit info. to 3rd world countries. These indians even ask you for your full social over the phone most times. It used to be only last 4 digits lol
We need more security across the board. Most American CEO’s still dont’ take this seriously. We need better security for every industry in America. Not just financial institutions. I understand FIS was a huge company with alot of clients, but you might as well say all of America is more criminal then hackers and deserve to get hacked. Its our own fault we should thank these hackers for letting us know how dumb we are?
Shame on you if your American. But if your a criminal hacker i can understand you being extra defensive, soft on the hackers, and why you continue with this propaganda.
With your thinking we can find every bank that ever got robbed by hackers at fault. Thats a hacker mentality and another hacker response.
In every business i ever went to. Take My mothers hospital for example. Where they store peoples medical records. They will change the computer passwords every 90 days. But not the routers. And they only use windows passwords, not bios…which some of you hackers know is useless. All you need to do is stick in a thumb drive with the right code on it.
which is what it usually boils down to. Someone on the inside. now maybe thats not the case here. But i wouldn’t be surprised.
Most American CEO’s don’t take it seriously b/c it won’t affect them. They’re in a higher class. They have resources to deal with little issues like identity theft and such.
Many people also forget about the concept of externalities. “Let someone else worry about it.” In a capitalist system, externalities are good business. The less you deal with, the less cost and the more profit. Banks will only care if they’re forced to. This will be hard to do seeing how much money they give to politicians and seeing that a few private banks own the money itself.
Its more like they don’t believe it can happen to them, or don’t even know it does.
And i guess once they do find out about a big heist, with something like this. They thnking is oh it will never happen again…. lol
And i guess I agree in a huge corporation they can take the loss i guess. But until they change their attitude….the small businesses and little guys, mostly the home users….are going to get hurt.
Completely agree… there appears to be a complete lack of best practice here:
– No patch management
– No password standard (or at least none that has been implemented across the enterprise)
– Lack of system hardening
– Lack of gold build standards
– No removal of vendor supplied credentials
– Lack of an internal vulnerability scanning process or at the very least no proactive response with subsequent patching of vulnerabilities
Taking care of the basics does not require out of the box thinking. It requires process and staff that stick to that process. Unfortunately breaches are going to happen but there is no point making the job easier for the would be attacker.
You call these basics. So don’t you think every industry should implement these steps? Not just FIS?
Cause I’ll tell you what. FIS to me is the typical American company, that everyone uses credit with…..
I understand they are a major financial institution. But that makes no difference to me. These hackers steal as much money from department stores lol.
My aunt just got her credit card stolen from staples. (but it was a girl on the inside who is now fired) Most of these stores don’t have updated computers let alone security…lol.
although i’m glad to see its not just americans for a change.
oh we weren’t the carders but it was us still getting robbed i guess.
Thieves steal because thieves steal.
http://www.zdnet.com/wi-fi-hack-caused-tk-maxx-security-breach-3039286991/
45 million credit cards stolen with the hackers on the network for at least 18 months.
IIRC, TJ Maxx was also the company how had the check out stands using wireless. So the check out process sent the customers CC numbers, etc in clear text. All the crackers needed was to sit in the parking lot and capture traffic….which they did.
No, it’s not just the banks, FIS, TJ Maxx or other stand alone companies. Much of this data lives in the “cloud”, an apparently magical kingdom according to execs and white paper authors. Of course, the cloud storage and SaaS space is getting very crowded, guess what expense gets cut first in most instances?
Where I come from, there are two sorts of companies.
1. Those that have been hacked or could be hacked, but realize it and are taking ongoing steps to mitigate the risks.
2. Those that have been hacked or could be hacked, and don’t have a clue.
3. Liars.
Ah… yep… every company should do the things I mentioned. That is why they are the basics:)
Out gov’t has woken up but I don’t think most corporations have yet.
The upper management probably sets the standards for password security. If the top people at the company personally have trouble remembering complex passwords, good luck to the IT staff trying to get password complexity policies enforced company-wide.
The ability to memorize a large variety of complex passwords seems to be a skill you either have or you don’t. Companies need a way to address that problem, because the executive suites of large companies are full of people who lack that skill, and they set the tone for the rest of their organizations.
Many are missing the big issue. Yes, the dollar amount stolen is immaterial, but banking is based on one foundation: confidence in the banker’s ability to protect the client’s assets (be it privacy, loan balances, business relationships, deposit balances – checking, savings, CDs). If your customers lose faith, the bank will be short lived (see Greek banks and customers with pitchforks demanding their assets).
I’m sure hardworking people are already getting laid off, who were not at fault.
“Shame on you if your American. But if your a criminal hacker i can understand you being extra defensive, soft on the hackers, and why you continue with this propaganda.”
Lol. You’re heart is in the right place but you are clueless otherwise.
Hackers hack because it’s there. Crackers crack because there’s a credit card number there. Hackers are just people who like to experiment. i.e. my mother hacks in her garden.
The key is permission. If you get on a network without permission, you are violating the law. That includes insecure wireless networks you can access in your own home. If you don’t own the network and you don’t have the owners permission.
Basically what you are saying is that if you gave me a million dollars and I left it in the street, you’d be upset with the thieves, not me. Those darn hackers, what will they think of next?
“That’s a hacker mentality and another hacker response.”
Thanks for the compliment.
What you don’t get is that to secure a network, you have to be able to see what they see, think like they think and keep up on trends in the industry. And test your own network. i.e. that darn permission thing again.
I understand outsourcing and social security cards. Do you get social networking? You don’t need a Facebook account to have your every inclination mapped out, they can do this by seeing who your friends and family are as long as they can associate you with your friends and family who use Facebook. Do you really want to be denied a job or insurance based on this?
All it takes to pwn a network is to send an email to some clueless exec who clicks on the link telling him he’s been given some award as the biggest ego in his industry (spear phishing). The link downloads software to his computer that appends code to the executable he uses to launch his email program which opens a back door and phones home to his system every time opens his email. With default password, anyone on his system can explore at will. That network is compromised. Actually, people don’t need to explore, there are automated tools to do that. Have you paid any attention to what Krebs has been blogging?
By your analogy, anyone with a gun is a criminal….that includes every law enforcement officer. And anyone who knows how criminals operate is clearly a criminal. Do you think they get caught by pure chance?
I don’t know voksalna but he’s clearly clued in. He stated FIS needs a black hat team and white hat team. One probes the network, another hardens it and tries to detect the intrusion….with permission. In the military, they call it war gaming.
Or do you think a company with 35,000 employees can’t afford 3 “black hats” and 3 “white hats” to secure their systems?
http://www.bizjournals.com/jacksonville/stories/2010/04/12/daily31.html?page=all
“Fidelity National Information Services Inc. tripled Executive Chairman Bill Foley’s compensation in 2009 along with several executives who received retention bonuses largely based on the Metavante Technologies Inc. acquisition that closed in October.
Foley’s total compensation in 2009 was $21.5 million, up from $7.5 million in 2008, according to the proxy released with the U.S. Securities and Exchange Commission Thursday. Foley received a $1.4 million bonus as a retention incentive from the Metavante merger, along with Corporate Executive Vice President of Finance George Scanlon, who received a $75,000 bonus and Francis Sanchez, corporate executive vice president of strategic solutions, who received a $500,000 retention incentive.”
I wish I could get a $14 million raise by overpaying for a company, changing the stationery and having my cronies declaring me irreplaceable.
I have no idea what you are saying here. I agree with most of it?
I find it interesting though in the computer industry how even Legtimate software companies…always blaming the uneducated user for their technical difficulties, assuming their dumb and its their fault. Taking absolutely no responsibility.
And now you guys blaming the FIS and banks trying to convince the world these hackers should bear no responsibility.
Everyone with a gun is a criminal what?
Heres a simpler analogy. If i leave the door open to my house and I get robbed. Its not 98 percent my fault. I don’t deserve it. And you did me no favors by proving how lapse my security was.
And if my homeowners insurance replaces everything, it doesn’t mean its a victimless crime.
I also agree the fact these guys were servicing banks, I agree is disturbing because you’d think banks would have more security then most companies…….
but in the bigger picture credit information is everywhere. And, imo every company should have the same security if they connect to the internet period.
I can’t be as hard as some of you guys on FIS but maybe this will wake up some American CEO’s who still think this just happens in the movies….
“I find it interesting though in the computer industry how even Legtimate software companies…always blaming the uneducated user for their technical difficulties, assuming their dumb and its their fault. Taking absolutely no responsibility.”
Basic security is the end users responsibility. I used to try to help people to secure their systems but found they don’t give a hoot. For the most part, I leave them to their own devices. Not my problem. If they were actually interested, I would help.
If you buy a car, you have to be licensed. And you will be held liable if you are driving the speed limit in a snow storm and you cause an accident, because you were operating the car in an unsafe manner. You can’t blame the car company.
Same with computers. Everyone should know by now their computers can get a virus. That includes linux, Apple and Windows. Companies should fix vulnerabilities and many do via patches but people don’t install them.
“And now you guys blaming the FIS and banks trying to convince the world these hackers should bear no responsibility.”
Not at all. Criminals are criminals and they should be held responsible. But FIS should have known better. They seem to have had lax to no security.
“Everyone with a gun is a criminal what?”
You seem to think that everyone that is interested in privacy or computer security is a criminal. Not so. Many “hackers” as you would call them alert companies to security flaws without releasing the details publicly. Often companies go after the researchers. If a vulnerability exists, do you think the bad guys are going to alert the company? No, they will steal as much as they can. Lax security just makes it easier for the crooks.
“Heres a simpler analogy. If i leave the door open to my house and I get robbed. Its not 98 percent my fault. I don’t deserve it. And you did me no favors by proving how lapse my security was.”
No, you don’t deserve to get robbed. But the single most common cause of burglaries is unlocked doors. That’s reality. If I see you door is open when you are generally at work or just left on vacation, would you like me to call you and let you know? Or should I just mind my own business. Did I do you a favor by just ignoring it?
“And if my homeowners insurance replaces everything, it doesn’t mean its a victimless crime.”
Agreed.
Well apparently most companies think everything is the “end users responsibility” which imo, is why the computer industry has been spiraling downwards for years now and is not respected. Besides android phones…. hackers, piraters, outsourcing and arrogant computer nerds, its one of this horrible industries biggest downfall. what happened to the customer is always right?
IMO companies should make things more user friendly but at the same time more secure.
Technical difficulties due to either, is the companies responsibility imo. not the user. That shows complacency and bad business.
you people act surprised about their lapse in security? really? Has TJmax even changed anything since they got millions stolen? Has any company? I understand this company services banks, but these hackers have stolen more money from department stores and other companies…..whats the diff?
I’m not saying they shouldn’t have done a hell of alot more to secure their accounts, but As you said yourself noone takes security seriously. and as I keep saying, as senator rockefeller keeps saying, neither do top American CEOs! so why are you surprised?
I just find it so disturbing you blame the home user when his pc gets hacked….and you want to crucify this company….. when they get hacked, but never the hacker? what? Its almost like most of the people on this blog think the hackers did nothing wrong. All the replies are about how America is the evilest country, and how FIS had the worst security in the world…..
Delusional just like the kid who robbed tjmax claiming he did it for the gov’t lmao.
http://votesmart.org/candidate/key-votes/53360/jay-rockefeller-iv/
Have you read the voting record of your hero?
I never said hes my hero. lol Just that hes the only senator who takes cyber security seriously. Meaning not only for national security.
whats the problem with his voting record? please explain.
People should know who they are supporting and what they are voting for instead of just believing whatever they say?
please explain….
please explain…
“I just find it so disturbing you blame the home user when his pc gets hacked….and you want to crucify this company….. when they get hacked, but never the hacker?”
No, I have been trying to point out, ad nauseum, that there is a shared responsibility. If you buy your kid a bike, you personally are responsible for making sure your kid wears a helmet.
When you operate a vehicle, you have to be licensed and operate it in safe manner or you are held liable.
When you buy a computer, we just let you on the Internet regardless of whether you have a botnet trying to grab banking passwords hosted on your system or not.
What’s the difference?
“what? Its almost like most of the people on this blog think the hackers did nothing wrong.”
Liars, lie. Cheaters, cheat. Thieves, steal. There’s a pattern here. It’s expected behavior. Please don’t confuse expected behavior with approval.
“All the replies are about how America is the evilest country,”
Don’t take everything so personally. Some people are pissed off cuz they lost money.
“and how FIS had the worst security in the world…..”
Changing default passwords and not using blank passwords and putting up a firewall are steps 0 and 1 when configuring a network. It’s like taking the “kick me” sign off your back.
Many, many other steps are required to harden a network, but if these are not taken, there’s basically no point in taking the others.
“When you buy a computer, we just let you on the Internet regardless of whether you have a botnet trying to grab banking passwords hosted on your system or not.”
Yo keep going on with this license to drive a car analogy which doesn’t relate one bit to using a computer man.
You think we should have licenses to using a computer? You think using a computer can accidentally kill someone or cause injury? what? WHAT? you can’t even accidentally rob someone with a pc man.
a botnet what? what does that have to do with a car. I need a car license because people have guns? what?
a computer is not a car. a computer is you as a person connecting to another world environment. and these are the barbarian times of the internet man.
This industry mentality, that its always the users fault has to change…..Maybe once you start getting more in tune with actual users…..you can provide better security. Instead of arrogantly thinking you know best and they are just too dumb to know better. You will never find those loopholes making you the best security man with that attitude.
“Liars, lie. Cheaters, cheat. Thieves, steal. There’s a pattern here. It’s expected behavior. Please don’t confuse expected behavior with approval.”
When people are more upset at the company that got robbed then the people that robbed them? It sounds like approval to me. 13 million? a drop in the bucket! it means absolutely nothing to those banks. and they will change nothing. have they even gotten robbed before? of course they have security….are you insane? maybe not good enough…..but apparently it does not warrant the extra cost for them. They’d rather take the breached losses. Their mentality will not change….and neither will their security much. guaranteed.
Even you guys, while demonizing FIS, actually come off as not caring. When you say nothing about the hackers that committed the robbery. SO why should they care about them?
“All the replies are about how America is the evilest country,”
I can say that too. Its nothing personal.
“Changing default passwords and not using blank passwords and putting up a firewall are steps 0 and 1 when configuring a network. It’s like taking the “kick me” sign off your back.”
and with such a huge network then, aren’t you shocked they aren’t robbed all the time? or for an actual significant sum? You act as if they had no security at all. Again, i think the problem is here they don’t see the cost for extra security, or time, worth it. It might be cheaper to take that 13 million dollar loss every 5 years. I mean you don’t even care about the hackers….why should they?
I think I understand the mentality of American CEO’s, You think you are pressuring banks and major corps to change. But all you are doing is confirming them they shouldn’t be concerned with hackers too much.
.
and its not a victimless crime. Even if it means nothing to these banks…. Because i’m sure some little guys are feeling the affects.
Is there any way to find out which financial institutions are clients of FIS? How can I find out if my bank (or credit union) is an FIS client?
Well the only issue with that is FIS has third party contracts on many things and it is hard to know. But even if your bank is completely non-fis when you use your debit card their is a good chance it will hit an fis device with them owning 2 of the largest atm networks in the world. The best thing to do if you worry about your money is just take it all out in cash and stuff it in your mattress.
This. And double this because the competitors have problems too.
Is there any evidence that JHA & Fiserv are better at security or have they just not been caught yet?
The initial problem was an unpatched linux system. combine that with company-wide routable networks and obscene lack of security and you can see how this happened.
FIS has laid off a lot of good people and outsourced a lot of talent so that management can collect their bonuses. FIS management doesn’t seem to have a clue about how to make profit the old fashioned way, so instead they cut corners and personnel, and shuffle numbers on paper in order to appear profitable. Huge acquisitions further compound the problems. It’s a top-heavy corporate structure which is completely out of touch with their employees, talent, abilities and infrastructure.
The security team often seems to have their priorities completely off target. I don’t know who runs the security group, but that’s a good place to start climbing the ladder and lopping off heads.
An unpatched Linux Machine! (LOL)
I guess upper management decided that properly securing 1000s of machines was not worth it.
The real question is how to get management to realize how freaking important security is even if its costs serious bucks?
I bet some in management believe in one of the ‘Folks Models’ of security that Rick Wash did some research about.
http://www.rickwash.com/papers/rwash-homesec-soups10-final.pdf
How to get most of America to realize this is the question. This is one thing Senator Rockefeller was always complaining about. Most American CEO’s we talking major players….dont’ take it seriously at all.
also amazing…how they weren’t robbed sooner or that they didn’t steal more like in some other cyberheists.
“It appears the extension is necessary due to the immense scale of the project, which consists of approximately 30,000 servers and operating systems, another 30,000 network devices, over 40,000 workstations, 50,000 network circuits, and 28 mainframes running 80 LPARs,” the FDIC examiners wrote.”
Good luck securing that mess! It’s physically impossible. And I mean, physically impossible.
That company will be breached no matter WHAT they do. No company of that size can be secure. No way, Jose. Fergeddaboudid.
The only thing they can try to do is up their detection and incident response so at least they can limit their losses. And I’d say good luck with that, too.
It’s consensus in infosec these days that preventing breaches just isn’t possible. The emphasis today is on detection and incident response. But for a company with this many servers, workstations and network devices, it’s going to be REALLY hard and expensive.
I think that may be a bit misleading. Hear me out. Yes, it is probably impossible to keep that many machines secure, but what really needs to be kept secure are points of ingress and egress. If you limit those and implement proper access control and DMZs then it becomes far less difficult to segment things and limit damages. One might like to think of a ship’s floodability (I like ships): ships have built into their design ‘watertight compartments’ (and a lot of them) to limit exposure to damages. One may lose part of the ship but unless one loses many parts of the ship, the boat will not necessarily sink. While this is not a perfect metaphor, my point is that proper segmentation and limiting damages will go a very long way. Hundreds of thousands of machines SHOULD be secure but they do not necessarily HAVE to be secure to keep out the outsider. The insider is a whole other story, but you can generally assume if you have a malicious insider, you will eventually have a catastrophe, if they want to breach strongly enough.
Focus on creating only a few ingress and egress points. Separate them and segment them appropriately. Implement token authentication throughout so one doesn’t have to remember a complicated password, and put that in another DMZ layer and you’ve limited the damages. Even not changing the passwords on everything but making it impossible to jump fully into the network would have gone a long way.
VLANs are nice. So are guest networks. I’ve also taken to blacklisting Zeus, etc. net blocks that have known C&C servers. Inspecting outbound traffic for dubious URLs has discovered compromised systems, even though they were fully patched and had updated AV.
Limiting ingress and egress points has gotten to be a whole lot more difficult now that smart phones have built in wireless.
If airgapped properly then phones with wifi would not even come into the matter. BYOD is always a problem but single points of entry, with very meticulous security, to the more sensitive parts of the network seem the most logical step. VLANs are great but they also have problems… eg routers.
We’ve got in house and guest wireless networks with separate firewall interfaces. And are locking down company phones with MDM.
But the personal phones with who knows what apps installed on them added to the wireless network sucks. We can’t re-architect everything all the time.
The biggest problem is keeping people from sharing credentials and bringing in personal devices. They don’t get it and upper management is not going to lop heads for this no matter how much IT preaches.
All in all, we are locked down tighter than any place I have worked without turning every device into a dumb terminal and have very few incidents. There’s a line between preaching security and alienating all the users.
MAC range white or blacklisting would probably help here, if you are willing to implement it. Granted one may spoof a MAC if one has a laptop etc and one had that level of sophistication, but with a phone, no, and best of all these generally have the same few chipsets and MAC address prefixes/ranges. Not a perfect solution, but not a hard (or expensive) one to implement. 🙂
I have explored mac white listing and black listing to get rid of smart phones. But Apple and other vendors mix mac ranges with their other products. I have looked at sticky ports on the switches, etc, but the cost/benefit gets to be unfavorable.
I am not too worried about spoofing or MIM by our end users.
More to the point, it’s a culture thing. Management and the end users have been warned.
oh so i just realized you said people can’t spoof a phone.
Cause i’ve had many hackers claim otherwise, although i don’t believe them, when i keep telling these companies that the best security is to do what google started. and ironically what alot of scam sites do now. is get your cell phone number to text activation codes to and tie to credit cards. to get rid of bots.
I don’t buy its too hard to implement. if people with fake websites are doing it. even for free games i say they should require a credit card and cell phone just for verification purposes.
and i get huge amounts of backlash like you wouldn’t believe…
I have honestly not seen that many businesses that *need* wireless, by the way. This thought that people ‘need it’ bothers me endlessly. I know people like to get their POP3/IMAP email this way, but not that many people do, and data plans are not that expensive anymore. It would probably serve a company better to offer vouchers for this if an employee needs it, on a cost basis, than it would to deal with securing a wireless network (you cannot).
“I have honestly not seen that many businesses that *need* wireless, by the way. This thought that people ‘need it’ bothers me endlessly.”
LOL. What planet are you on? Wireless is somewhere up there with food, shelter and sex where I live. How else is the average user going to identify with the hipsters in the Apple commercials. And on the practical side, many people spend way too much time in meetings.
Come give a talk here about how wireless is not needed and you will lynched by noon.
Agreed that wireless is impossible to completely harden. The good news is there are so many other tasty targets in the vicinity. Security by obscurity is not my first choice, but I will take it.
“Sorry, I think I missed a word — not that many people do NEED to POP into their mail. I would call it a ‘perk’ for 75-90% of many organizations, at least for desk-bound employees. Or you could enforce any wireless phone access to HAVE to go through a VPN.”
I won’t go into detail but we have a very mobile work force.
Sorry, I think I missed a word — not that many people do NEED to POP into their mail. I would call it a ‘perk’ for 75-90% of many organizations, at least for desk-bound employees. Or you could enforce any wireless phone access to HAVE to go through a VPN.
Like Rich said. They are going to breach you. The key now is to discover it sooner and limit the damage. Thats where the resources should be going right now. detection.
Not to pay a bunch of IT guys or security firm for the best firewall system in the world…thats only going to get breached anyways. Or for a network that is probably already breached….with that many computers? ya ok….good luck.
I do all that too. change all the passwords….mac address filters…disabling most broadcasts, especially router name….no upnp…..ip black lists…..block all outgoing…block all http…..etc……filter every single ip and allow i manually. it doesn’t matter man. it all means nothing…. I do this so at least you hackers can’t tell me i deserved to be hacked for my lapse of security. But it all means shit. Every christmas i cross my fingers when satan comes to town.
A bunch of losers working for drug dealers, mad gamers, homsexuals stalking me….who knows… Like the guy that robs your house….they probably know you.
but maybe i will at least keep out that one random dude, who doesn’t know me, from another country haha.
But you can’t foresee everything. I don’t care if you are the Albert Einstein of hackers. Especially nowadays.
You do realize that if you just don’t allow remote Wifi router access, foreigners are moot for all that shit right? It’s your PCs you should be worrying about unless you’re worried about your neighbors or someone with a cantenna timewarping from 2004. You are using WPA2 with a long hard to guess password right?
ya.
They’re not talking about home wifi. It’s a conversation about insider threats. Different animal altogether.
Just describing examples of how most of America does not care about cyber security.
In your case quit going to crap websites and gaming places and whatever other websites you’re going to that could give you malware, get a decent browser, turn off scripting, and ‘Cool out’ 😉
I’m not allowed to play games on the pc?
crap websites? You mean if i went to NBC.com after they admitted they were getting hacked and virused?
When i go to facebook whos always admitting they are getting hacked?
kind of scary when microsoft and apple headquarters are getting hacked nowadays…and can’t even figure out what the hackers did to their network….
oh you mean pornos probably lol? Well i only go to sites ok’d by WOT, trafficlight and bit defender.(not that means much) But I think nowadays i’m more likely to get viruses elsewhere believe it or not. lmao.
the latest virus I had detected was from battlelog.net. EA denies it but its the truth.
Cool out? $##@! you for killing the pc gaming industry.
and yes i forgot i also do use adblock and noscript…
“oh you mean pornos probably lol?”
From a security standpoint, you are much safer on mainstream porn sites than your average church site. Believe it or not, studies have been done confirming this.
Who do you think pioneered streaming, secure payments and many of the services we take for granted? And who do you think has a bigger security budget?
“When i go to facebook whos always admitting they are getting hacked?”
Zuckerberg rolling back privacy using teenagers as a foil.
http://readwrite.com/2010/01/09/facebooks_zuckerberg_says_the_age_of_privacy_is_ov
“People have really gotten comfortable not only sharing more information and different kinds, but more openly and with more people. That social norm is just something that has evolved over time.
“We view it as our role in the system to constantly be innovating and be updating what our system is to reflect what the current social norms are.”
Seriously, I lined up a bunch of Zuckerberg quotes and Hitler quotes and people had a hard time telling the difference.
Two quotes from Hitler (paraphrased). You are much better off telling a big lie, repeated over and over, than a small lie. When personal liberties are smashed, the public won’t be fighting you, they will be demanding it. (ala FaceBook, social media in general, Apple’s walled garden, etc)
And I have never known anyone who legitimately needed a Liberty Reserve account, although I am open to the possibility.
So if I understand you, we should lock down the network, wireless, all user devices and everything else but allow unfettered anonymous access to offshore payment processors run by two-time losers?
Looks like the Feds are actually getting better at the cyber crime game.
$200 million carder ring using LR taken down.
http://www.fbi.gov/newark/press-releases/2013/leader-in-200-million-international-stolen-data-ring-charged-in-new-jersey-as-part-of-worldwide-takedown
Citadel Botnet crimped.
http://www.informationweek.com/security/attacks/microsoft-fbi-trumpet-citadel-botnet-tak/240156171
“with very meticulous security, to the more sensitive parts of the network seem the most logical step. VLANs are great but they also have problems… eg routers.”
If you want to really get granular, you can create multiple concentric rings of security. i.e. banks have vault inside the building. Just because you let people through the front door, you don’t need to let them into the vault….or even in that section of the building.
Firewall and web filter A protect the ingress/egress points to/from the Internet. Firewall and filter B protect the ingress/egress point to the vault. If my servers are on Skype and DropBox, I have issues.
Sorry, haven’t had much time to reply lately.
I believe I had pointed out multiple (ie concentric) dmz’s as a reasonable tactic. But of course it really all depends on your business to begin with and what technologies you run.
When I said I didn’t like when people said they ‘need’ wireless, I meant the ‘quotes’. I think you got that because you returned the sarcasm 😉 but the truth is it is coddling users that gets them to be dumb and lax and open your network up to problems to begin with.
Generally any smartphone is capable of connecting through a vpn to pop mail. I think there was a good and valid reason a lot of corps held out for a long time (and some still do) on getting away from Blackberries. Until people stop having the tech version of ‘unsafe sex’ (ie mingling their personal stuff with their work stuff)… yeah that won’t happen as long as you allow personal devices the same powers in a network as private devices. I remember when a lot of places were demanding no built-in cameras in smartphones. The amount of access people are given to eg create a hotspot *WITHIN THEIR COMPANY* to connect to it from outside now is absurd. Life was simpler when you could just check for people being ‘naughty’ by hooking up a modem to their pbx line (which really was, hard to believe, for the most part only about a decade, decade and a half ago).
I think eventually the business world will need to cut down on things as industrial espionage becomes more and more of a concern.
Why aren’t you just REQUIRING users to provide the IT dept with their phones for configuration with the work network the way things (used to be? still are?) done with laptops and vpn’s? Or at least requiring them to provide you with authorized mac addresses, and then limiting port access?
People are so spoiled. 😉
Sorry that email was so scattered by the way. I don’t even think I said what I meant to say. “Private” devices should have read “corporate” devices, to start with, and I never finished my thought on industrial espionage: At some point companies may require you to turn in your phone at a desk and pick up a work-only version, maybe, that only connects to the intranet. For all I know some already do. I know it is not uncommon in certain defense circles to not allow external devices into certain areas (physical) or parts of a network AT ALL. This is not a terrible model.
“Sorry, haven’t had much time to reply lately.”
No worries.
“I believe I had pointed out multiple (ie concentric) dmz’s as a reasonable tactic. But of course it really all depends on your business to begin with and what technologies you run.”
For us, that would be like transporting French Fries in an armored car. If our “IP” was “liberated”, it would just cause the world to fall asleep.
“When I said I didn’t like when people said they ‘need’ wireless, I meant the ‘quotes’. I think you got that because you returned the sarcasm 😉 but the truth is it is coddling users that gets them to be dumb and lax and open your network up to problems to begin with.”
Agreed, but I would rather them be “dumb” in predicable manner. If I crack down too much, 10 of the ladies here will parade into HR and claim I made inappropriate sexual comments and tried to feel them up. A fair fight is for suckers.
That means I “do them a favor” by letting some sites live while killing all peer-to-peer traffic, certain protocols, etc. I can monitor the “some sites” and mirror the traffic if I need to dig.
“Generally any smartphone is capable of connecting through a vpn to pop mail. I think there was a good and valid reason a lot of corps held out for a long time (and some still do) on getting away from Blackberries. Until people stop having the tech version of ‘unsafe sex’ (ie mingling their personal stuff with their work stuff)… yeah that won’t happen as long as you allow personal devices the same powers in a network as private devices. I remember when a lot of places were demanding no built-in cameras in smartphones. The amount of access people are given to eg create a hotspot *WITHIN THEIR COMPANY* to connect to it from outside now is absurd. Life was simpler when you could just check for people being ‘naughty’ by hooking up a modem to their pbx line (which really was, hard to believe, for the most part only about a decade, decade and a half ago).”
Agreed. But personal cell phones are not seen as a threat here. And, in many cases, personal cell phones are just reimbursed as a business expense as the company does not provide all the phones. With the carriers defaulting wireless Internet connections to a local WAP (keeps the load on the carrier network if it senses local wireless), users naturally type in their network credentials.
“I think eventually the business world will need to cut down on things as industrial espionage becomes more and more of a concern.”
I know people who work at places where no non-company devices are allowed at all. They turn off all the switch ports unless the proper forms are signed off, use sticky ports, use mac address white lists, etc. But if I had the choice between a stale French fry and our data, I would take the stale French fry.
“Why aren’t you just REQUIRING users to provide the IT dept with their phones for configuration with the work network the way things (used to be? still are?) done with laptops and vpn’s? Or at least requiring them to provide you with authorized mac addresses, and then limiting port access?”
Because it would be pissing people off to no end and over-engineering the by multiple degrees. I don’t work for FIS. We need to keep things reasonable on the continuum of security vs. usability.
“People are so spoiled. ;)”
True.
you said it man.
Thats what Rich said voksalna in not so many words.
Might even be what FIS already does. Can you imagine constantly changing passwords on all of those? haha thats what i was thinking originally too. insane.
I said I wasn’t going to reply to you again and I won’t get into philosophy but it’s not as hard as you think. You should read up more on propagation and even maybe LDAP.
Philosophy? what? Don’t know where your going with that one.
but like most hackers… you think it can’t be true if its too simple. You think your superior and smarter the more big words you use. People get hacked cause they don’t know what they are doing which means they deserve to……etc.. come down off that cloud man.
FIS already does what you said. and Rich already said what you said…. and I thought I liked to listen to myself type….
These hackers just robbed people. They don’t even care about their own families…. They make the world more evil…..paypal should ban russia. lol
Oh, you’ve been in FIS’s networks? You work for FIS?
Why didn’t you just say so!
have you? why haven’t you said so?
I think its safer to assume they do have some security and mitigate the damage done already.
Its not like we hear about them getting robbed all the time. And this was not the largest cyberheist by far.
But its a good thing Brian reports on these things so that hopefully more American CEOs will realize this is a reality and not a sci fi movie.
Are you suggesting that all large institutions are inherently unsafe? While I’d agree that there’s more likely to be some minor compromises at large institutions, I don’t think failures of this order are preordained at Citi, or BoA, or the US government.
That’s quite possible actually. In any case we wouldn’t even know, large institutions are not in the habit of disclosing such things especially if they can hurt its reputation.
It also make sense in that the larger the institution the more likely security compromises go undetected and lets not forget users who may themselves be the most dangerous threat to any system not matter how secure.
Of course there are well known ways to take care of such things, IDS?IPS systems, 802.1x etc.. But when you are dealing with 10s of thousands of computers that you are trying to retrofit better security you will always face some serious problems not to mention financial limitations.
In the case of FIS its obvious that the attackers were already in system before they launched the attack and no one was able to know that they were.
YES.
The us gov’t in the past few years has finally started taking cyber security very seriously.
And one thing is for sure. We owe alot to Brian for reporting on these news stories. These are just the ones we hear about. Shit we might never hear about any of these stories. This is something mainstream media still doesn’t even take seriously man!
You think those banks don’t get robbed too? We prolly just don’t hear about it. Americans attitude towards cyber security on the whole has to change.
Even when homeland security was warning Americans to install java. Noone heard about that on the news man. If it was…it was like a 10 second sound byte or something lol.
Senator Rockefeller has been pointing out for the past few years. American CEO’s do not take security serious.
and just to add. I think Rockefeller is one of the only senators in congress to even take cyber security seriously, not just for national security….but for home users and businesses. I’ve seen the guy get really upset over this. Its a shame and hes leaving office lmao.
i meant *uninstall java. (even though voksalna says the viruses and coders are less sophisticated nowadays…./laff)
http://www.esreality.com/post/2303108/cooloutac-exposed-lol/
I guess I can understand you a bit better now.
You’ve clearly been put through the wringer on a lot of places. It must be terribly difficult to struggle under this sort of weight.
1 out of 3 Americans have. thats my point.
I’ve never gotten credit stolen, an account stolen, or any identities taken.
But ya….I have been maliciously hacked many times. Usually by pc gamers. Once by shadow crew. Last christmas i got pounded and those hackers are still stalking me….
and as far as just the malicious viruses…..this happens to way more then 1 out of 3 americans buddy. whether they know it or not.
but when it does happen to you, severe enough to take notice……its a sick feeling like when your house gets robbed. something you never forget for the rest of your life.
dude i’m still lol’n about “you seem to like saying you reap what you sow”
which i never said on this blog. I already know your a stalking hacker dude because the only time I ever said anything like that was an old country blues song i played on guitar and posted online. hahah.
hey i’m used to internet stalkers…stalk on. my facebook is public have a go at it.
imo e-sports should be a billion dollar industry feeding families. But the only people left on pc gaming are hackers. Society does not respect you. You can sit here and say America this America that. But noone in society can trust a hacker dude. Its no exaggeration. and yes i get flack for saying so. that site was started for the first sponsored e-sport and first mutliplayer fps game quake. But its dead and forgotten. kids nowadays never heard of that game. They only know games on consoles nowadays….and who can blame them. Who wants to play online with a bunch of foreigners and hackers who are not very friendly….
Piraters and hackers killed the pc gaming industry….and the pc industry in general is dying. I’m not afraid to talk about this taboo subject and I’m not afraid to blame the hackers for it. not the companies.
even as the whole computer industry in general has been plummeting people are still in denial.
which is why i can’t understand any surprise over FIS, when most major corporations don’t take cyber security serious yet.
http://krebsonsecurity.com/2013/06/fdic-2011-fis-breach-worse-than-reported/comment-page-1/#comment-185922 onward.
I did not ‘stalk’ you. That was actually one of the first English proverbs I learned and it’s pretty much what you were saying to me over and over again ever since I was posting on the LR threads, in different words. That I deserve bla bla bla. Note that I did not say YOU deserved bla bla bla. Hell, man, you were not even hacked by Russians to begin with.
I am sorry you do not feel as though you have a community to feel at home in. Taking time for introspection helps. Generally so much pent up energy wanting to get out means an outlet is needed. Stepping back and examining one’s way of reassessing the world and everyone in it including oneself and the reasons behind one’s beliefs (even if you decide not to change them!) will often make people less want to lash out at you on forums.
I still wish you the best. 🙂
I believe you…really I do…. /sarcasm.
community? I know most of the people in my community. What I am trying to explain to you, just like this blog. Most online communities are full of hacking foreigners… and its ruining the industries.
I believe once in christmas of 04 or 05. when my pc got fried on christmas day. it was an american that hired a russian. that i was talking to on aim to inquire about a friend of mine who got locked up in boston caught with 70 credit cards. i noticed as soon as talking to this dude….my pc was acting funny, I almost moved with him to Cali to start a mortgage brokerage. Then i had second thoughts…tk god i didn’t. I would of had to hunt that kid down.
anyways…. shit hit the fan for two weeks… or perhaps it was just the russian he was buying the credit cards off of on his own initative. The kid did tell me he found out the russian was hacking him before he went to jail in boston.
funny side story. I never took a credit card from him. Cause i always felt like he was gonna set me up. You can never trust a hacker….they are delusional.
but i did take him to an underground hip hop show, and we drank on that card all night long. He made his name a famous underground rappers name on the id and credit card…had me cracking up. The cops didn’t know who he was for a month haha. cause he was still using the same id in boston.
Anyways, I notice as soon i started talking to his associate on aim and making plans to go to cali and start a mtg company. I noticed my computer acting funny. for two weeks it just kept getting worse as i was frantically fixing windows to try and back up my data because it started crashing alot. Then on Christmas day BOOM it died. mobo and vid card fried. i replaced them both for 60 bucks.
maybe the kid never went to jail. maybe they just decided to fuck with my computer for kicks….who knows. maybe it wasn’t the russian. but thats who most of these americans hire man. chinese and russians. they get the equipment from china and the numbers from russia. his associate hired the russian to hack him….so i figured he hacked me too….either way pretty fkd up.
theres just one of my computer stories for you man. but one of the wickedest. fried on christmas day. haha.
a christmas present i will never forget
oh ya i lost one hdd totally, threw it out and kept the other virused one too…. fk it. lol
my uncle has gotten his credit card stolen, my grandpops. a boss of mine his identity stolen. but those are prolly by all diff people and nothing to do with me.
A LiveCD or USB is your friend. Run it off an old, obsolete laptop after unplugging the rest of your network, if you plan on pissing off the Internet.
http://en.wikipedia.org/wiki/Live_CD
‘to inquire about a friend of mine who got locked up in boston caught with 70 credit cards.’
‘funny side story. I never took a credit card from him. Cause i always felt like he was gonna set me up.’
‘and we drank on that card all night long. He made his name a famous underground rappers name on the id and credit card…had me cracking up. The cops didn’t know who he was for a month haha. cause he was still using the same id in boston.’
SO it’s funny when YOU steal. I see.
Rockefeller is part of the problem. “InfoSec” to him is whether or not he gets a copy of the data.
Cloud Computing is for Airheads and Communists.
I agree. It can be done. However, the company’s primary motivations are cost efficiency and information sharing for operational efficiency. These are inversely proportional to information security in most cases.
The best they can do is control ingress/egress points like the other guy said, built input cleaning/inspecting front-ends to the business apps, automate their security-relevant configuration across the network, implement monitoring, implement recovery mechanisms, control endpoints, etc.
However, even if they DID provide enough protections to the network, insiders could easily cause problems by slipping through the gaps in security as the networks or procedures are modified. There’s simply too much complexity here to secure it without greatly upping the cost and reducing operational flexibility. Which they won’t do.
Just thought of a simple solution but realized they it may not be feasible. What about disabling html links that appear in emails? (To prevent phishing)
I know it probably doesn’t have anything to do with the FIS breach but would it be effective and how would it work, so many things require html links in emails but its also one of the most abused features of emails after attachments.
Any ideas?
Is there a way to ‘trust’ certain email contacts so that you could still click links within them?
you know thats a good point. and i can’t find an option for this in windows live mail.
You’re getting warmer. You’re basically stumbling onto the idea of mail guards. Far back as Orange Book days, there were high assurance mail guards that could be installed between classified and untrustworthy networks to prevent various email issues. One is below.
http://www.smat.us/crypto/docs/mailguard.pdf
The system ran on the Orange Book A1-class LOCK platform. That made it nearly impenetrable at the system level. From there, it had functionality to restrict email by sender/recipient, attachment type, confidentiality levels and whether a digital signature was present. Modern guards often have more performance and functionality, but less assurance (eg using Linux or whatnot). You could very easily implement the feature you mentioned, along with content scanning, in a robust guard to stop such email attacks. Then, you’d force all email (internal and external) through that guard by making the mail clients only talk to the guard. I’d make it two guards in a failover/load-balancing configuration to prevent single-point of failure. This architecture has other benefits in that logging, human inspection and various compliance requirements can be added in later.
More on guards
https://en.wikipedia.org/wiki/Guard_(information_security)#Functionality
Of course, there can be disadvantages. Aside from less flexibility, one major issue with this architecture is that there can be delays if a flood of email comes in or if email gets stuck in the filters awaiting human review. The users might try to work around the security using other mechanisms. That’s why I recommend applying the same principles to offer instant messaging, managed file transfer and other services essential to getting work done. This way, if it’s urgent, the users will still have secure/audited mechanisms to use rather than rely on unprotected mechanisms to do their work.
@voksalna I never used a stolen credit card . Even at times when dozens of people around me were tossing them at me, and I never ratted anyone out.
I accepted drinks at a social gathering from a known criminal. That’s the only thing i’m guilty of.
the only thing i ever stole in my life….was an mp3 or bootleg movie. Thats a whole other debate. I don’t make money off them……and they are such horrible qualities. Its still worth it to go see a 3d movie nowadays if its a good flick. But its another industry taking hits, not because of bootleggers (even the asian people in my city are going out of business) because people just don’t have the money anymore, and there’s so much on cable and on demand. (i might go to movies this weekend though)
@dirtybird yes i just made a bunch of cd’s for me and my family last night. I read Brians article. I’m gonna go with tails. not sure if banks need flash though. I downloaded a couple distros. i’ll try them all out.
Tails is based on Tor. Banks and a lot of other commerce sites do not like Tor — and those sorts of things are wholly unsuited for Tor to begin with. What is more, they often do not like Tor so much that trying to use it will likely get your account blocked or prevent the transaction from going through. And you would not want to trust your banking credentials going through Tor. I could continue but there is no point. You do not want to use Tails for this or anything like this.
You may want to look at Mageia. It’s user-friendly and not trashed up like Ubuntu is. If you are not afraid of ‘less pretty’, find a live distro running hardened kernel (last I checked there were 1-2 out there, try looking for hardened Gentoo) and a semi-friendly interface (most people are most comfortable with KDE or Gnome, especially for liveboots; Gnome is probably a better choice from a security standpoint). You’ll probably want to get a portable binary copy of firefox and a copy of the noscript plugin so you can easily add it each time you boot. It would be dumb to keep this sort of thing persistent even though in general Linux is less likely to be clientsided.
apparently most of them don’t boot up quick or at all on the older xp machines anyways. tails didn’t work. I tried the airforce one thinking it was light…it didn’t work either, even on my newer machine.
puppy linux works. I might just stick with that. it boots super fast and is user friendly and has a recent release. .
they all seem to use firefox which is cool, my preferred browser.
by persistent do u mean saving settings to the hdd?
Yes, the whole point of a LiveCD is you don’t save anything to the HDD.
If you have specific, manual settings you need to configure, you will have to set them each time you boot up. Unless you replace the default file on the LiveCD with one you customize.
ya well…I was trying to make it easier for my parents…so i saved some settings on the hdd so it boots faster and they don’t have to set network settings and firewall everytime. But they still boot up with the disc.
I didn’t even use any encryption….is that terrible? lol
if its not quick and painless they are not gonna bother…and i can forget about trying to get anybody else to do it.
I mean its a great idea though.
I figure its still better then using windows still isn’t it? or should i not bother? theres no way they are going to set firewall and setup network everytime with the puppy linux which is one of the few that works on their machine.
man linux is crazy. no wonder you guys always think its the users fault. cause this o/s is not too user friendly!!…hahaha
I bet thats why mainstream media doesn’t report on crimes like this…..the gov’t or corporations don’t want the public freaking out… like sometimes when i go to fix a persons computer and they think I’m hustling them cause they have no idea what I’m talking about lol.
Well i’m glad Brian does cause maybe we need to wake up and realize we need to be more computer literate in this new age to protect ourselves as individuals and as a nation. we all should learn how to use linux 8-|
I think computer classes, like dos linux and windows should be part of primary education now for children.
Cloud computing is for airheads and communists.
Odd about dates. FIS says it was based on a report completed October, 2012.
Then the articles states: “The Executive Summary Scan reports from November 2012 show 18,747 network vulnerabilities and over 291 application vulnerabilities as past due,” the report charges.
????
The oddity of the dates is simple.
They lied the first time to save their stock price and sign up more banks to pay their expenses.
The ‘closer’ to the truth came out when it was no longer headline news that could have set FIS into a tailspin and BK.
Your bank is probably using this scammer org.
The banks would be better off hiring PC gamers to do their infosec.
QUESTION:: If you put confidential data on a hard drive, and then later sell that drive on eBay, then… who owns your data????
QUESTION: If a bank puts HIGHLY confidential data on SOMEONE ELSE’S disk drive… who owns the data????
Only an airhead couldn’t figure that one out. So, why are America banks allowed to store YOUR American data on organized crime servers in ?????
It’s called breach of fiduciary duty.
““The Executive Summary Scan reports from November 2012 show 18,747 network vulnerabilities and over 291 application vulnerabilities as past due,” the report charges.”
How are vulnerabilities counted? If they have the same patch missing from 30,000 servers, are they counting it as one vulnerability or 30,000?
If the former, yeah, they may be in really bad shape. If the latter, they are better than 99.9999999% of all corporations.
A “vulnerability” also does not equal a “risk”. A statement like “18,747 unique vulnerabilities with a CVSS rating of 4.0 or higher still exist” is a lot more meaningful.
The fact that the FDIC is asking customers to put pressure on FIS is the most telling thing in that article. It means the FDIC has no teeth and cannot take meaningful action against the FI’s they are supposed to regulate.