In March 2013 I wrote about Perkele, a crimeware kit designed to create malware for Android phones that can help defeat multi-factor authentication used by many banks. In this post, we’ll take a closer look at this threat, examining the malware as it is presented to the would-be victim as well as several back-end networks set up by cybercrooks who have been using mobile bots to fleece banks and their customers.
Perkele is sold for $1,000, and it’s made to interact with a wide variety of malware already resident on a victim’s PC. When a victim visits his bank’s Web site, the Trojan (be it Zeus or Citadel or whatever) injects malicious code into the victim’s browser, prompting the user to enter his mobile information, including phone number and OS type.
That information is relayed back to the attacker’s control server, which injects more code into the victim’s browser prompting him to scan a QR code with his mobile device to install an additional security mechanism.
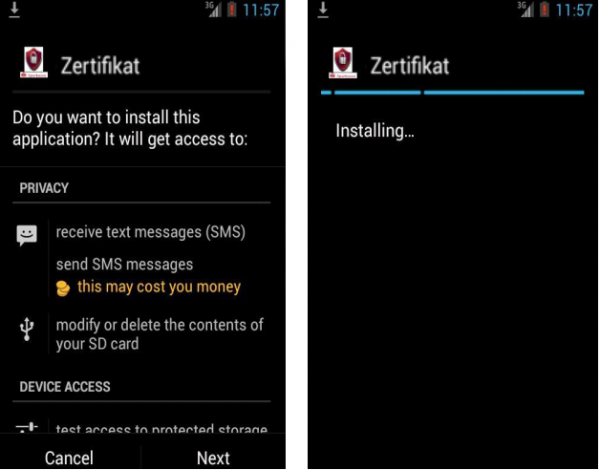
Once the victim scans the QR code, the Perkele malware is downloaded and installed, allowing the attackers to intercept incoming SMS messages sent to that phone. At that point, the malware on the victim’s PC automatically initiates a financial transaction from the victim’s account.
When the bank sends an SMS with a one-time code, Perkele intercepts that code and sends it to the attacker’s control server. Then the malicious script on the victim’s PC receives the code and completes the unauthorized transaction.
Web site security firm Versafe located a server that was being used to host malicious scripts tied to at least one Perkele operation. The company produced this report (PDF), which delves a bit deeper into the behavior and network activity generated by the crimeware kit.
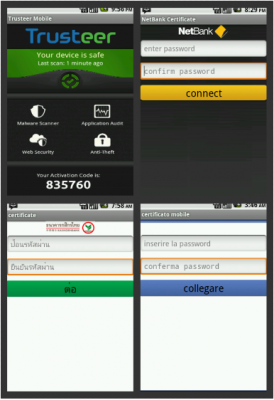
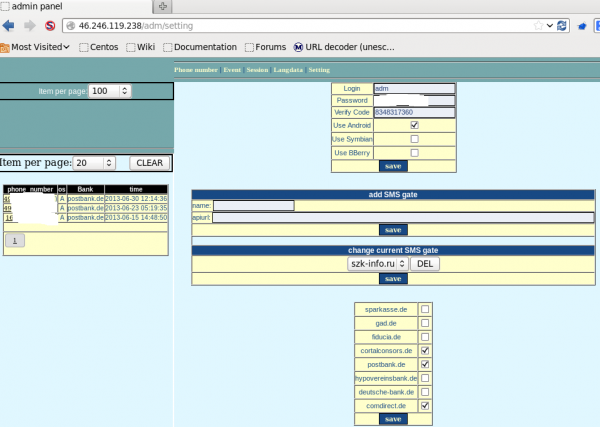
Versafe’s report includes several screenshots of the Perkele application as offered to would-be victims. The malware is presented as a security certificate; it’s named “zertificate” because the victim in this case banked at a German financial institution.
A few weeks ago, I encountered the back end system for what appears to be a Perkele distribution, or perhaps some other mobile malware bot; I should note that disguising an Android banking Trojan as a security certificate is not a ruse that’s limited to Perkele: The Pincert SMS malware also employs this trick, according to F-Secure.
Anyhow, I scarcely had time to examine this particular mobile bot control panel before it was either taken down by German authorities or was moved elsewhere by the fraudsters. But it, too, was intercepting one-time codes from German banking victims using an Android malware component similarly disguised as a “zertificate.”
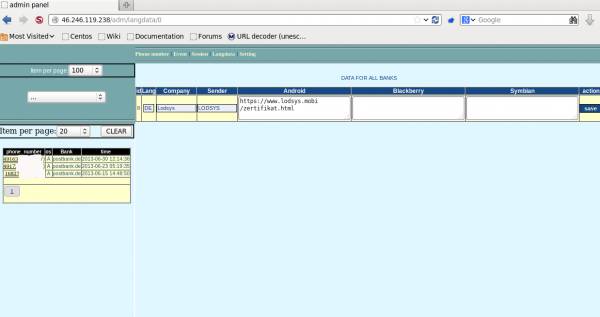
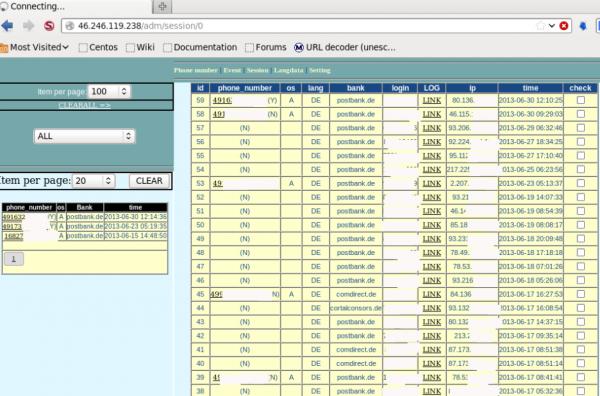
Apparently, it was fairly successful, stealing one-time codes from online banking customers of several German financial institutions, including Postbank and Comdirect.
In the screen grab below, we can see the main administrative page of this panel, which controls which banks should be targeted and from where the fraudulent text messages should be sent.
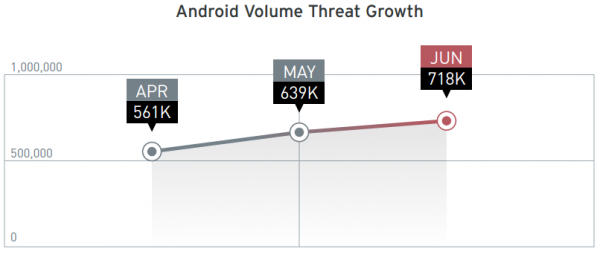
There seems to be a great deal of interest in the cybercrime underground for developing or procuring tools to trojanize Android devices. According to a recent report from security firm Trend Micro, the number of malicious and high-risk Android apps steadily increased in the first six months of 2013. According to Trend, the number of malicious and high-risk apps took three years to reach 350,000, a number that has already doubled in just the first half of 2013.
Fortunately, a modicum of common sense and impulse control can keep most Android users out of trouble. Take a moment to read and comprehend an app’s permissions before you install it. Also, consider downloading and installing apps only from Google’s Play store, which scans all apps for malware. Also there are numerous free and paid anti-malware applications available for Android.




He he he, perkele is Finish for devil or satan…. quite fitting 🙂
That toy Perekel is somewhat like 200-300 lines code app. Krebs is such a lame that can’t even differ two absolutely non-related Android bots. The picture of a Trusteer-like app is NOT Perekle.
And that public admin-panel screenshots of that Toy – that’s all Krebs got.. haha dats so funny. Would you like me to pass you the source code of Perekle? Incuding java code files and all the admin files?
That is NOT a closer look. That is a DUMB look.
Someone’s always gonna be 1 step ahead.. Or I’d even say like 5-10 steps, cuz as I see u’re so far away from “the Truth” at the moment.
All this is like a Saturday Night Life with Krebs show..
+1 .
Thank you Brian.
Yes, they’re always ahead but we love the bits of info and insight and all the trouble you’ve gone to in order to get the data, cheers.
“Fortunately, a modicum of common sense and impulse control can keep most Android users out of trouble.”
Unfortunately, many Android Users do not understand that the OS is the Wild Wild West of the mobile marketplace. Too many users assume they are safe and that their mobile provider, Google, or their bank is protecting all of their stuff for them.
That seems to me like the user’s responsibility. People don’t have to know how something works to know how to practice using a device properly. Most people have no idea how their automobile works, but they drive every day and they know enough that they do not put sugar in their gas tanks to make it ‘go’. If people are going to trust important things to a device they should have the forethought and wisdom to check and see if they can trust it, looking for known problems — and 5 minutes with Google can do that, so it is not so that it is an esoteric thing. People do not want to know widely known risks. They want to complain, however, when they do trust thousands, hundreds of thousands of dollars to a device they paid a few hundreds of dollars for and did not even have the forethought to question ‘should I really be doing my banking on this? I should find out before I keep my financial information here and also want to use whatever else on this same device’.
Honestly, even with CyanogenMod, smartphones are pretty junky. A ton of stuff I’ve come across in the Google Play store, if not already bordering on adware, reminds me of PC junkware from 2004 or earlier. And if the growth of malware is growing so fast on Android then I wouldn’t even kid myself with an AV.
I did read things on SELinux and Android 4.3, maybe that will help if everyone doesn’t end up disabling it.
Appreciate that point of view. And so, if one wants to keep his mobile data secure my advice is to get a good n old kind of Nokia 3310 for banking codes etc.
+1.
Interesting stuff. Good read for sure! Thanks Brian
Thank you for the nice blog… regard Mina
old news as always .
i Agree
There are no Germans behind Perkele.
certificate in German is written Zertifikat .
Perkele is controlled from another Middle European Country.
While I agree with your last sentence, I think Brian made mistake when transcribing ‘zertifikat’, see his screenshot: http://krebsonsecurity.com/wp-content/uploads/2013/08/zert-0a.png
lulz shit soft
coder ripper go banned on maza
soon you go write about the blackshades rat or the various sexual fetishes of malcoders?
I think he may just be running out of interesting big bad guys to write about. 🙁
The topic is still “security” nonetheless. I don’t see any issues with the above article. If anything it was very informative.
“Ethical Criminal”?
All criminals think they’ve got oh-so-good reasons for doing damage or harm to others.
I’ve worked at a prison and there was hardly a ‘guilty’ inmate in the entire place!
But everyone must leave this life, eventually, and that’s where “the rubber meets the road!” Excuses only work up to that point…..
Thanks for the heads up, Brian, as always.
Regarding DDoS attacks, can it become so that mr. Krebs take a look into regular political DDoS in Russia? Every elections are accompanied with heavy attacks against the opposition media outlets. Seems like the same foul party is at play every time. Can it be worth investigating?
Hi Georgi,
I actually did look at this issue a while back:
http://krebsonsecurity.com/2011/12/twitter-bots-drown-out-anti-kremlin-tweets/