The high-profile Web site defacement and hacker group known as the Syrian Electronic Army (SEA) continues to deny that its own Web server was hacked, even as gigabytes of data apparently seized during the compromise leaked onto the Deep Web this weekend.

Screen shot from SEA site syrian-es.org, listing the nicknames and avatars of top SEA leaders. Image: HP Security Research
Following a string of high profile attacks that compromised the Web sites of The New York Times and The Washington Post among others, many publications have sought to discover and spotlight the identities of core SEA members. On Wednesday, this blog published information from a confidential source who said that the SEA’s Web site was hacked and completely compromised in April 2013. That post referenced just a snippet of name and password data allegedly taken from the SEA’s site, including several credential pairs that appeared tied to a Syrian Web developer who worked with the SEA.
The SEA — through its Twitter accounts — variously denounced claims of the hack as a fraud or as a propaganda stunt by U.S. intelligence agencies aimed at discrediting the hacker group.
“We can guarantee our website has never been hacked, those who claim to have hacked it should publish their evidence. Don’t hold your breath,” members of the group told Mashable in an interview published on Friday. “In any case we do not have any sensitive or personal data on a public server. We are a distributed group, most of what we have and need is on our own machines and we collaborate on IRC.”
In apparent response to that challenge, a huge collection of data purportedly directly taken from the SEA’s server in April 2013 — including all of the the leaked credentials I saw earlier — was leaked today to Deep Web sites on Tor, an anonymity network. Visiting the leak site, known as a “hidden service,” is not possible directly via the regular Internet, but instead requires the use of the Tor Browser.
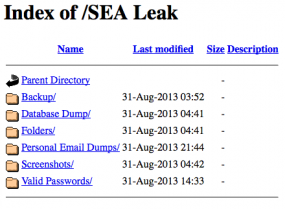
Among the leaked screen shots at the hidden Web site include numerous apparent snapshots of the SEA’s internal blog infrastructure, the Parallels virtual private server that powered for its syrian-es[dot]com Web site, as well as what are claimed to be dozens of credential pairs for various SEA member Twitter and LinkedIn accounts.
News of the archive leak to the Deep Web was first published by the French publication reflects.info (warning: some of the images published at that link may be graphic in nature). As detailed by the French site, the leak archive includes hundreds of working usernames and passwords to various Hotmail, Outlook and Gmail accounts, as well as more than six gigabytes of email messages downloaded from those accounts.
SEA LEADERS IDENTIFIED?
One of the more interesting screen shots in the leak archive is an image showing the email address listed in the “contact email” field of the back-end administration page for syrian-es[dot]com: The email listed — “hatem.deeb.hatem@gmail.com” — appears to dovetail with a name mentioned in multiple recent media reports about the identities of the alleged SEA ringleaders.
On Thursday, Vice.com published a story linking a top SEA member — who uses the screen name Th3Pr0 — to a Syrian named Hatem Deeb. Vice published a picture from a Facebook account thought to belong to Deeb, but later removed that photo, saying it had information suggesting that Deeb was in fact another Syrian native who currently resides in St. Petersburg, Russia.
 On Friday evening, NBC News unearthed a 2011 story published by a Syrian government-run newpaper al-Wenda, which identified and praised the leaders of the SEA. The al-Wenda piece specifically praised Deeb as a teenager, and as a “founding member” of the SEA. Another student, Ali Farha was later mentioned in another Syrian publication as the “manager” of the SEA website. Interestingly, Farha’s purported Facebook page indicates that he and Deeb are roughly the same age and attended the same technical school in western Syria — the University of Kalamoom.
On Friday evening, NBC News unearthed a 2011 story published by a Syrian government-run newpaper al-Wenda, which identified and praised the leaders of the SEA. The al-Wenda piece specifically praised Deeb as a teenager, and as a “founding member” of the SEA. Another student, Ali Farha was later mentioned in another Syrian publication as the “manager” of the SEA website. Interestingly, Farha’s purported Facebook page indicates that he and Deeb are roughly the same age and attended the same technical school in western Syria — the University of Kalamoom.
Also reportedly leaked are the entire contents of the SEA web site’s core server, including a file showing a history of all text commands entered by administrators of the site over several months in 2013. A review of those commands suggest that SEA administrators made frequent use of imo.im, a Web-based instant messaging program.
The history file and other documents also indicate that the SEA administrators routinely blocked specific Internet addresses from being able to load or access all or portions of their site. In addition, it shows that administrators also specifically whitelisted several Internet properties (addresses expressly allowed to access the site); among those were a number of Tor anonymizers, as well as several sites in Jordan, including the Ministry of Higher Education division of Saudi Arabian Cultural Mission in Jordan.
Declining to address the voluminous evidence of a site compromise, the SEA’s account on Twitter dismissed these latest revelations as proof of nothing.
“Publishing fake screenshots and hacking randomly pro-Syria people unfortunately don’t prove anything :)”, the group retorted.




Nice post.
inb4 mad syrians
lol they named a folder “folders”
The irony… the hackers… got hacked.
I wonder if this group are somehow employed or under some special treatment for the things they do.
The releases I’ve seen, the wordings appear to be almost press release like – not your average 19 year old with a grudge.
Just to add, I meant ‘the hackers’ with +1 sarcasm.
Readers can use onion.to to visit the hidden service if they wish to without running Tor or Tor Browser Bundle.
It’s a open web proxy to Tor hidden services (meaning one should never use it if you wish to remain anonymous like someone using Tor itself).
Where’s the link though?
strange, always thougth that these hacks are done by NSA to get people angry on Syria
I suspect, if these hackers are ever taken quite seriously, they won’t be so worried about counter-hacking as they will be about Hellfire missiles coming in their bedroom windows.
“dismissed these latest revelations as proof of nothing”
actually, they have a valid point – what is proof of anything in this virtual world? anyone can create screenshots, log files, gmail accounts etc under any name. If I post on my FB profile that “I’m the SEA” what would that prove?
ok, generating this amount of fake evidence would require a lot of time and money, but let us not forget that a war is going on and NSA has a large budget, as well as other US cyberwarfare units, not to mention Chinese, Russians, French, etc whomever has any interrest in Syria
Hehehehehe. Propaganda wars? I don’t think so. There are elita hackers out there, and some of them are truly hackers. They don’t want recognition – they do “what they think is right”.
The elite open or know of holes that haven’t been leaked or discovered yet. Some of the reasons why holes exists is due to human coding error, but Commmmon, like Brian has posted in the past, some of these holes exist for other………organizations to get in.
Some of the agencies – mainly ones who have control of their people, hire the best hackers. Why? because they want control of their actions, vice having them pounding on websites and organizations and causing chaos.
Sure there are many that are semi-defiant, and those that continue to cause issues will eventual be dealt with. If this organization was hacked, its a calling call. The world will probably never know who truly hacked these wanna-be’s, but the main focus on the hack is probably to say – your not invincible and you’d better watch your steps.
They are being watched. I’ll stop there.
Software is software….. You can use software to break software, its only a matter of time. They use the same stinking software others do. What makes you think that the software they use is any different? No one truly knows the extent of how much data is collected and by whom.
If you think passwords and whitelists are going to save anyone, its a long educational road for someone.
The official U.S. term for propaganda is ‘Public Information’ since back in 1917 and the 75,000 Four Minute Men. (And in fact most of the millions of all pro american comments at some european websites could be traced back to the same origins during Bush adminstration. – They even posted fake criticism themselves to counter with a flood of pro american comments in marginal used technical forums’ off-topic area… So everything is possible. ;-))
Can’t help but be reminded of The Onion’s poignant article http://www.theonion.com/articles/syrian-electronic-army-has-a-little-fun-before-ine,32324/ . All of this is going to make the mop-up that much easier.
hahah script kiddies owned
xa xa xa .. he is good 🙂 very well done .Long live Assad .
Сайт американского корпуса морской пехоты подвергся хакерской атаке. Пользователи интернета, пытающиеся зайти на сайт marines.com, видят страницу с надписью “союз Обамы с “Аль-Каидой”. Кроме того, хакеры призывают американских военных не выполнять приказы командования.
“Сирийская армия должна быть вашим союзником, а не врагом”, — говорится в тексте, оставленном на взломанной странице.
http:// http://www.vesti. ru/doc.html?id=1124717
Translation of above
Site of the American Marine Corps was hacked. Internet users trying to enter the site marines.com, see a page that says “Obama’s alliance with” al-Qaeda “. In addition, hackers calling the U.S. military command did not follow orders.
“The Syrian army is to be your ally, not an enemy,” – said in the text left by a compromised page.
It says, “In addition, hackers called for American troops to not follow orders.”
Thanks for the Russian translation. Appreciate having a non-Google translation that makes sense.
I can see them saying;
“I know thy pants are around thy ankles ! Just don’t look”…..
This embotchedment ritual, if you will is a fine example of children playing with… stuff that they have no idea what they are doing. All they can do is rant, whine and show ignorance, until a lawyer is required and they are standing in front of some judge.
Looks like they try to save Face since OPUSA turned into FLOPUSA.
They can say all they want; do what they think is right. But one thing is certain, they will NEVER be an elite hacking group Like Anon or Lulz. Stinking script kiddie pests, at best.
A couple of things here don’t pass the smell test:
1. Who in their right mind would collect all this info and store it anywhere? And then store it on a computer connected to the net? How would they even get it all? If I were part of this group and the admin demanded my email, twitter, and fb usernames and pws, I would tell him to go pound sand.
2. Who in their right mind would lead a high profile hacker group then use an email of the form real-last-name.real-first-name.real-first-name.high-profile-email.com? And then put it on a computer such as the one listed in point 1?
The answers to all these questions is no one. This just doesn’t make sense. Is it possible their server got hacked? Sure, but this “evidence” doesn’t pass muster.
What you expect from yellow press ?! They print any BS story as long as they can get away with it .
Money talks .
First and foremost, hackers believe themselves to be invincible. They’ll put whatever data they want to put wherever they want to put it because nobody will ever catch them.
Second, there’s an inverse correlation between actual talent and swagger, in that the people who have scads of talent keep very low profiles, while the ones with very little talent make as big a splash as possible. And inexperience leads to foolish mistakes.
While I agree it seems ridiculous that they would log their personal passes on the server, and am personally on the fence as to whether this is legit, it’s NOT uncommon for a crew to share logins or (more typically) api access to their accounts for a multitude of reasons.
Most common would be the sense that they’re somehow mitigating risk by involving more users. Nonetheless, if the hammer were to drop, it would do so on the poor bastard(s) whom logged in bare by accident at one point or another.
What am I saying… I mean, everyone doing these things is SOOO cautious and likely transparently proxies ALL traffic and would NEVER log in without massive levels of obfuscation. Right?
Just like Assad’s comments re Sarin: “it must have been the terrorists…” “We never used any chemical weapons.”
“We weren’t hacked. It’as all fake. ”
Must have gone through same propaganda training.
Its good to know that Baghdad Bob has found work again.