A hacking group calling itself the Syrian Electronic Army (SEA) has been getting an unusual amount of press lately, most recently after hijacking the Web sites of The New York Times and The Washington Post, among others. But surprisingly little light has been shed on the individuals behind these headline-grabbing attacks. Beginning today, I’ll be taking a closer look at this organization, starting with one of the group’s core architects.
Earlier this year I reported that — in apparent observation of international trade sanctions against Syria — Network Solutions LLC. and its parent firm Web.com had seized hundreds of domains belonging to various Syrian entities. Among the domains caught in that action were several sites belonging to the SEA.
At the time, the SEA had a majority of its sites hosted at Internet addresses belonging to the Syrian Computer Society, an organization considered to have been a precursor to the SEA and one that was previously headed by Syrian President Bashar al-Assad. Following the Web.com domain seizures, the SEA was forced to find new homes for their domains. Soon enough, the group moved its domains syrianelectronicarmy.com and sea.sy to a host in Russia (no doubt adding further chill to already frigid US-Russia relations vis-a-vis Syria).
Sometime during that transition period, the SEA’s main Web site got hacked. As in…completely owned. According to one confidential source, the attacker(s) gained access to the virtual servers that hosted the SEA’s site and downloaded the entire user database for sea.sy and syrianelectronicarmy.com. Shockingly (or perhaps less so for many security researchers who’ve dismissed the SEA as mostly a group of tenacious but relatively unskilled hackers), many of the top members re-used the passwords they picked for their sea.sy accounts at their Hotmail, MSN and Outlook email accounts.
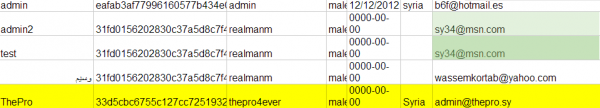
A snippet from the hacked database from syrianelectronicarmy.com. In the third column are plain-text passwords.
In nearly any dump of a Web site user database, it’s generally safe to assume that the first few users listed are founders and administrators of the site. In the hacked sea.sy database, for example, we can see that the first two usernames in the table are “admin” and “admin2.” Admin2’s email address is listed as sy34@msn.com. The last entry in the database is April 19, 2013, just a few days after Web.com began seizing domain names in its stable with the “.sy” designation.
A Google search on that email address reveals its ties to the SEA, and shows that the account was in 2010 tied to a now-abandoned hackforums.net user named “SyRiAn_34G13” (leet-speak for “Syrian Eagle”). A reverse WHOIS search at domaintools.com on the sy34@msn.com address shows that it was used in Feb. 2011 to register a site called codepassion.net.
Codepassion.net is no longer active (perhaps because it was hacked and defaced in May 2012 by other script kiddies), but thanks to the Wayback Machine at the indispensable Internet Archive, we can see the site lists as its creator a 23-year-old “virtuoso web designer” named Mohammed from Damascus, Syria. Mohammed says he is a senior front end developer at a firm in Damascus called Flex Solutions. Mohammed reveals that his last name is “Osman” when he links to his Facebook and DeviantART accounts, as well as his Gmail address (osmancode@gmail.com). That same Gmail account is also used for another account in the sea.sy database: يوزر – which Google translates to “Yoezer” “User” and used the password “963100”.
Osman’s DeviantART account — “medothelost” — says in Arabic that he is a member of the Free Syrian National Rally, a founding member of the Syrian Civil Youth Movement, and a member of the Syrian Social Nationalist Party. Another account named “medothelost” in the sea.sy database uses the email address medo_sy@hotmail.com and the password “963100.”
Looks like since working at Flex Solutions, Osman struck out on his own, and changed his identity slightly: Running another reverse WHOIS record search at domaintools.com shows that osmancode@gmail.com was used to register the site mohamadstudio.com (I guess mohamMEdstudio.com was already taken?). Anyway, Osman’s Mohamad Time Line tells readers more about this guy, who says he recently moved to Turkey. He currently lists his name as Mohamad Abd AlKarem. Around the same time that Mohammed Osman stopped tweeting at @osmancode (April 27, 2013), @mohamadabdalkarem started up. Osman/AlKarem could not be immediately reached for comment.
A short time ago, Vice.com ruined my scheming and published information on the next guy I’d planned to profile in this series — the individual listed as registered user number 4 in the database screenshot above: “ThePro.” See their story here for more on him. Thankfully, there is enough here to keep me busy for a while yet.
Update, Aug. 29, 2:23 p.m. ET: Several reporters contacted me to say they’d heard from the person at osmancode@gmail.com, who claimed he was not a member of SEA and was never contacted by me; in fact, I sent an email to this same address yesterday requesting an interview. I also never received a reply from the Twitter account tied to Mohamad Abd AlKarem). A few minutes ago, Mr. Osman replied to my email, stating that he was not part of the SEA, and furthermore if he was would he have been so careless with his information? He also said Mohamad Abd AlKarem is not him but his client. Here is his reply:
“Dear Sir
I am not a member in “Syrian Electronic Army”, and if I were, would I mention where I work, post my personal photo as declaring my political views?
Dear Sir, Would I, if being a SEA member, publish where I live and my real name, would you do that?
Actually I do believe that the most stupid man on earth wouldn’t do it, then what about someone to be considered one the best hackers?
Thus dear, you can verify that I am not a SEA member, not as well their leader, just as you have mentioned in one of your articles, depending on odd information that has – at any rate- any relation to a matter of fact.
By the way, Mr. Muhammad Abed Al-Karim is my client, and I have made reservation as any other regular common customer.”
Update, Aug. 30, 12:14 p.m.: Mashable published a story after interviewing AlKarem, which quotes AlKarem as saying he is not Osman; AlKarem told Mashable he knows Osman through the art website DeviantART, but the two have never met in real life. AlKarem told the publication that while Osman had developed some graphics for the SEA, “I don’t think he’s a member of them.” Meanwhile, Motherboard ran a piece Wednesday claiming to have identified a different member of the SEA; that publication featured a Tweet from one of SEA’s leaders “ViCt0r” who last year gave a shout out to fellow SEA members, including a Mohammed Othman.
Further supporting Osman’s statement that AlKarem is just a client are domain hosting records for mohamadstudio.com, which list Osman’s employer FlexSolutions as the technical contact. Also Osman’s personal site — osmancode[dot]com — includes a picture of him that appears different from the one on AlKarem’s site. Based on the evidence available, it seems likely that AlKarem and Osman are two different people. The image from AlKarem’s site has been removed from this story.




About: 963100:
Note that 963 is the international calling code of syria!
There is no clear meaning of the following 100 as (maybe connected to the fact that 11 is the prefix of Damascus?)
Here is a list of internal Syrian calling codes:
http://www.countrycallingcodes.com/country.php?country=Syria
Да. Не все в этой истории так просто!))) А вообще, почему бы не снять фильм на основе этой истории?
These seemingly harmless hackers must be watched with serious caution. Even visiting these sites can leave computers riddled with malware. It is not to be assumed that simply because SEA did not attack US Government databases, that it has not made attempts to. Information regarding their attack history is generally classified, but let it be known that we have not seen the last of SEA.
Aren’t these guys the least bit worried that they might find themselves on the receiving end of a ballistic missile sent by the last “super” power? They might make history is ways they didn’t anticipate.
Wow! Talk about details! Good job!
And – The password for the admin account is “admin”? What an ID10T! No wonder the DB was cracked in seconds.
I just dont understand why “hackers” are using msn/yahoo/fcbk/gmail accounts which are monitored by NSA.