Most Internet users are familiar with the concept of updating software that resides on their computers. But this past week has seen alerts about an unusual number of vulnerabilities and attacks against some important and ubiquitous hardware devices, from consumer-grade Internet routers, data storage and home automation products to enterprise-class security solutions.
 Last week, the SANS Internet Storm Center began publishing data about an ongoing attack from self-propagating malware that infects some home and small-office wireless routers from Linksys. The firewall built into routers can be a useful and hearty first line of protection against online attacks, because its job is to filter out incoming traffic that the user behind the firewall did not initiate. But things get dicier when users enable remote administration capability on these powerful devices, which is where this malware comes in.
Last week, the SANS Internet Storm Center began publishing data about an ongoing attack from self-propagating malware that infects some home and small-office wireless routers from Linksys. The firewall built into routers can be a useful and hearty first line of protection against online attacks, because its job is to filter out incoming traffic that the user behind the firewall did not initiate. But things get dicier when users enable remote administration capability on these powerful devices, which is where this malware comes in.
The worm — dubbed “The Moon” — bypasses the username and password prompt on affected devices. According to Ars Technica’s Dan Goodin, The Moon has infected close to 1,000 Linksys E1000, E1200 and E2400 routers, although the actual number of hijacked devices worldwide could be higher and is likely to climb. In response, Linksys said the worm affects only those devices that have the Remote Management Access feature enabled, and that Linksys ships these products with that feature turned off by default. The Ars Technica story includes more information about how to tell whether your router may be impacted. Linksys says it’s working on an official fix for the problem, and in the meantime users can block this attack by disabling the router’s remote management feature.
Similarly, it appears that some ASUS routers — and any storage devices attached to them — may be exposed to anyone online without the need of login credentials if users have taken advantage of remote access features built into the routers, according to this Ars piece from Feb. 17. The danger in this case is with Asus router models including RT-AC66R, RT-AC66U, RT-N66R, RT-N66U, RT-AC56U, RT-N56R, RT-N56U, RT-N14U, RT-N16, and RT-N16R. Enabling any of the (by-default disabled) “AiCloud” options on the devices — such as “Cloud Disk” and “Smart Access” — opens up a potentially messy can of worms. More details on this vulnerability are available at this SecurityFocus writeup.
ASUS reportedly released firmware updates last week to address these bugs. Affected users can find the latest firmware updates and instructions for updating their devices by entering the model name/number of the device here. Alternatively, consider dumping the stock router firmware in favor of something more flexible, less buggy amd most likely more secure (see this section at the end of this post for more details).
YOUR LIGHTSWITCH DOES WHAT?
Outfitting a home or office with home automation tools that let you control and remotely monitor electronics can quickly turn into a fun and addictive (if expensive) hobby. But things get somewhat more interesting when the whole setup is completely exposed to anyone on the Internet. That’s basically what experts at IOActive found is the case with Belkin‘s WeMo family of home automation devices.
According to research released today, multiple vulnerabilities in these WeMo Home Automation tools give malicious hackers the ability to remotely control the devices over the Internet, perform malicious firmware updates, and access an internal home network. From IOActive’s advisory (PDF):
The Belkin WeMo firmware images that are used to update the devices are signed with public key encryption to protect against unauthorised modifications. However, the signing key and password are leaked on the firmware that is already installed on the devices. This allows attackers to use the same signing key and password to sign their own malicious firmware and bypass security checks during the firmware update process.
Additionally, Belkin WeMo devices do not validate Secure Socket Layer (SSL) certificates preventing them from validating communications with Belkin’s cloud service including the firmware update RSS feed. This allows attackers to use any SSL certificate to impersonate Belkin’s cloud services and push malicious firmware updates and capture credentials at the same time. Due to the cloud integration, the firmware update is pushed to the victim’s home regardless of which paired device receives the update notification or its physical location.
The Internet communication infrastructure used to communicate Belkin WeMo devices is based on an abused protocol that was designed for use by Voice over Internet Protocol (VoIP) services to bypass firewall or NAT restrictions. It does this in a way that compromises all WeMo devices security by creating a virtual WeMo darknet where all WeMo devices can be connected to directly; and, with some limited guessing of a ‘secret number’, controlled even without the firmware update attack.
There does not appear to be anyone or anything attacking these vulnerabilities — yet. But from where I sit, the scariest part of these flaws is Belkin’s apparent silence and inaction in response to IOActive’s research. Indeed, according to a related advisory released today by Carnegie Mellon University’s Software Engineering Institute, Belkin has not responded with any type of solution or workaround for the identified flaws, even though it was first notified about them back in October 2013. So be forewarned: Belkin’s WeMo products may allow you to control your home electronics from afar, but you may not be the only one in control of them.
Update, 10:24 p.m. ET: Belkin has responded with a statement saying that it was in contact with the security researchers prior to the publication of the advisory, and, as of February 18, had already issued fixes for each of the noted potential vulnerabilities via in-app notifications and updates. Belkin notes that users with the most recent firmware release (version 3949) are not at risk for malicious firmware attacks or remote control or monitoring of WeMo devices from unauthorized devices. Belkin urges such users to download the latest app from the App Store (version 1.4.1) or Google Play Store (version 1.2.1) and then upgrade the firmware version through the app.
Original story:
NETWORK ATTACKED STORAGE
As evidenced by the above-mentioned ASUS and Linksys vulnerabilities, an increasing number of Internet users are taking advantage of the remote access features of routers and network-attached storage (NAS) devices to remotely access their files, photos and music. But poking a hole in your network to accommodate remote access to NAS systems can endanger your internal network and data if and when new vulnerabilities are discovered in these devices.
One popular vendor of NAS devices — Synology — recently alerted users to a security update that fixes a vulnerability for which there has been a public exploit since December that allows attackers to remotely compromise the machines. A number of Synology users recently have been complaining that the CPUs on their devices were consistently maxing out at 100 percent usage. One user said he traced the problem back to software that intruders had left behind on his Synology RackStation device which turned his entire network storage array into a giant apparatus for mining Bitcoins.
According to an advisory that Synology emailed Monday to registered users, among the many not-to-subtle signs of a compromised NAS include:
- An automatically created shared folder with the name “startup”, or a non-Synology folder appearing under the path of “/root/PWNED”
- Files with meaningless names exist under the path of “/usr/syno/synoman”
- Non-Synology script files, such as “S99p.sh”, appear under the path of “/usr/syno/etc/rc.d”
Synology urges customers with hardware exhibiting the above-mentioned behavior to follow the instructions here and re-install the disk station management software on the devices, being sure to upgrade to the latest version. For users who haven’t encountered problems yet, Synology recommends updating to the latest version, using the device’s built-in update mechanism.
SYMANTEC ENDPOINT INFECTION?
Although not strictly hardware-related, other recent vulnerability discoveries also to be filed under the “Hey, I thought this stuff was supposed to protect my network!” department is new research on several serious security holes in Symantec Endpoint Protection Manager — a host-based intrusion protection system and anti-malware product designed to be used by businesses in search of a centrally-managed solution.
In an advisory issued today, Austrian security firm SEC Consult warned that the flaws would allow attackers “to completely compromise the Endpoint Protection Manager server, as they can gain access at the system and database level. Furthermore attackers can manage all endpoints and possibly deploy attacker-controlled code on endpoints.”
Symantec has released updates to address the vulnerabilities, and probably none too soon: According to the SANS Internet Storm Center, over the past few weeks attackers have been massively scanning the Internet for Symantec Endpoint Protection Management system. SANS’s Johannes B. Ullrich says that activity points to “someone building a target list of vulnerable systems.”
ROUTER FIRMWARE ADVICE, CONT’D
Continuing the discussion from above about alternatives to the stock firmware that ships with most wired/wireless routers, most stock router firmware is fairly clunky and barebones, or else includes undocumented “features” or limitations.
Here’s a relatively minor but extremely frustrating example, and one that I discovered on my own just this past weekend: I helped someone set up a powerful ASUS RT-N66U wireless router, and as part of the setup made sure to change the default router credentials (admin/admin) to something more complex. I tend to use passphrases instead of passwords, so my password was fairly long. However, ASUS’s stock firmware didn’t tell me that it had truncated the password at 16 characters, so that when I went to log in to the device later it would not let me in with the password I thought I’d chosen. Only by working backwards on the 25-character passphrase I’d chosen — eliminating one letter at a time and re-trying the username and password — did I discover that the login page would give an “unauthorized” response if I entered anything more than that the first 16 characters of the password.
Normally when it comes to upgrading router firmware, I tend to steer people away from the manufacturer’s firmware toward alternative, open source alternatives, such as DD-WRT or Tomato. I have long relied on DD-WRT because it with comes with all the bells, whistles and options you could ever want in a router firmware, but it generally keeps those features turned off by default unless you switch them on.
Whether you decide to upgrade the stock firmware to a newer version by the manufacturer, or turn to a third party firmware maker, please take the time to read the documentation before doing anything. Updating an Internet router can be tricky, and doing so demands careful attention; an errant click or failure to follow closely the installation/updating instructions can turn a router into an oversized paperweight in no time.
Update, Feb. 19, 8:10 a.m. ET: Fixed date in Synology exploit timeline.





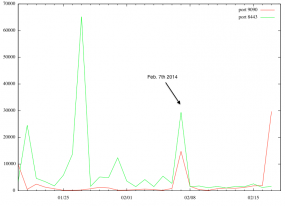

Also on the same theme, reports of hacks of consumer routers from TP-Link, ZTE, D-Link & Airlive running certain firmware revisions.
Once compromised, the routers are configured to point to rogue DNS servers and when users try to access their online bank through the router, they are diverted to a malicious site which swipes their creds.
Story here
http://www.computerworlduk.com/news/security/3501092/cybercriminals-compromise-home-routers-to-attack-online-banking-users/
Here’s a fun one: in certain firmware versions released a few months back for APC Symmetra UPSes, the newer, Schneider-branded firmware won’t allow login with any password / passphrase containing a space. The older, APC-branded firmware did not have a problem with this. Presumably whatever input sanitization they may have implemented views it as an illegal character and truncates the password at the space.
Where this is a big issue is in environments where RADIUS is in use to authenticate admin users on the UPSes. Effectively, there are three problems: firstly, this weakens passphrase-based security (arguably making it a no-go on these devices); secondly, admin users are now locked out until a password with no spaces has been set; finally, if fallback to local authentication wasn’t enabled on the UPS (and one hopes that if it was, it wasn’t with the default login) it’s now time to reboot the management card for a password reset from console.
It amazes me that with the prevalence of embedded systems and their criticality in supporting our ability to not only interact with these systems administratively, but also for them to perform their intended functions, manufacturers are still taking as lax of an approach to their development and upkeep as they are.
APC smart (ha) PDUs have, in my opinion, the slowest web server. When you enable SSL it becomes almost unusable. Along with their pkcs5 certificates, which I still have not figured out how to integrate into a MS or openssl CA (any hints on this would be very welcome)
Timely article, yesterday we received a call from a prospect that was hit with a malware infection. We haven’t been able to determine the point of entry yet but the malware went into the Asus router (default admin credentials of course) and changed the DNS to point to: 216.172.56.39
We’re assuming that someone opened an email attachment that had a payload and was able to access the router from inside their network but I’ll have to go back and see if it’s one of the models mentioned.
The only problem with DD-WRT/TomatoUSB/etc is lack of regular updates, almost would be better with a cheapo server running PFSense
The primary problem with that notion is that the vast majority of these devices are deployed to situations where proficiency in, e.g., installing or administering pfsense or similar firewalls cannot be counted on.
Many of these devices are essentially giveaways from ISPs to customers–customers who are likely to describe themselves as ‘computer illiterate’ and who are not only not going to check their firmware but are not going to understand why they should have to check their firmware in the first place.
Complicating the issue by giving them another “internet box” to turn off and back on again when their connection is having an issue is not going to help them out at all.
A better solution would be for ISPs to handle updates on leased equipment for consumer connections–though that has significant potential to be done very wrong.
Yes, but those folks most likely won’t have enabled remote administration.
Themselves, perhaps not, but a well-meaning IT-person-in-law may have done so–or they may have engaged in attempted learning.
Regardless, even if this particular exploit requires that remote sharing be enabled, what’s to say the next one will?
In Infosec, you always have to anticipate the next problem; fighting the ‘last war’ is a great way to get your boxes thoroughly compromised.
Actually Tomato is under extremely active development, with updates released every couple months, sometimes with multiple releases within a month.
The problem is that the original author (Zarate) stopped working on his projects some time ago, so someone else (Fedor) branched it to TomatoUSB to add support for newer routers and with new features (like a USB port), only to have the economic downturn force him to stop working on it, so others have branched TomatoUSB in turn and continued along their own branches. Added features have included migrating Tomato to newer versions of busybox, dnsmasq, (closed-source) Broadcom wireless drivers, and many other components that make up Tomato.
linksysinfo’s forums are the go-to spot if you want to keep abreast on what’s happening in the world of Tomato.
Personally I started out with DD-WRT but needed a higher performance firmware for my ancient WRT-54GL (which, at the time, wasn’t ancient).
Following along with @SeymourB comments, the DD-WRT firmware is being updated, as they just released an update today! (Feb. 19th, 2014)
ftp://ftp.dd-wrt.com/betas/2014/
A huge congrats!!!!
Investigative Journalist Brian Krebs Receives M3AAWG Mary Litynski Award for Protecting Online Community; Krebs Urges More Industry Cooperation Against Abuse
Would using OpenDNS on SOHO routers thwart this malware on a very basic level?
If someone owns your router (because you exposed it to the internet for file access or remote admin) it should be a simple matter for them to change the DNS settings away from OpenDNS (208.67.222.222 / 208.67.220.220) or Google DNS.
While on the subject of OpenDNS, is there anything better or is that still pretty much the go-to?
(I was thinking of switching to it myself)
“Normally when it comes to upgrading router firmware, I tend to steer people away from the manufacturer’s firmware toward alternative, open source alternatives, such as DD-WRT or Tomato.”
Yeah, especially when most routers have a sort update lifespan of a few years. Sadly though the open source firmwares out at the moment only cover a handful of devices.
I went to Symantec FileConnect…I don’t think they’ve put up new/accurate files…I downloaded everything and the versions.txt file and various dates were all October 2013!!!!!
I complained loudly to Symantec.
They’re up for 12.1.4a. I just downloaded them.
Great reporting, Brian, as always.
Have Asus RT-N56U router.
The firmware update for the security issue (dated Jan. 24) is only Beta.
I also see from the details of previous firmware updates that at least a couple of those updates announced : “Fixed AiCloud vulnerability related bugs”
The light bulb should go on (unless you happen to have one of those WeMo home automation products, in which case a hacker may have turned the light bulb off) for most. Whilst the convenience of being able to access or control items on your home network is appealing, it really pays to ensure you have technology such as VPN and 2 factor authentication as layers of defines prior to allowing remote access. These security technologies may be beyond the scope of a typical user at home who has cobbled together their existing network, but it will need to become the norm in the future if we want the flexibility of accessing our home networks from anywhere.
@ The Security Artist. Absolutely agree, i would never expose to outside world any of my home gadgets (NAS, security camera, autmation gadgets) without a VPN. But I have a question, if you exclude from 2 factor authentication a security certificate which you can generate yourself and go looking for a physical token, what options reasonably priced are there for a home user slightly more proficient than average ? I cannot image I can call Vasco or RSA and ask them to sell me 3 or 4 tokens and the management solution for my home VPN at a price I could afford.
would be great if you or Brian or other readers could suggest solutions I could look into. An app for iOS or Android is not quite acceptable because of the possibility of the phone to be hacked and the certificate stolen, but a solution with 10 one time passwords that I could print out and keep the card in my wallet (revoke them if the wallet gets stolen) would be, especially if it can be implemented with Open software. Even better if a company sells physical tokens targeting home users (or there is a freeware solution to load old, left over Vasco tokens with my own keys)
Check out duo security. Brian had an add running for them about a week ago. For home use it appears to be free. It has plugins that will work with openvpn and serveral other vpn tunnels. You download an app to your phone which sends you a push notification when someone tries to log in. All you have to do is click accept or deny.
Thanks Travis,
They look promising, I’m going to try them, the solution seems similar with PhoneFactor, now owned by Microsoft, but PF doesn’t have a free option.
@george, for a low cost solution, I also recommend using openvpn and duo security as @Travis suggested.
Brian, talk about an ironic typo: “NETWORK ATTACKED STORAGE”, or did you do that on purpose?
It’s ironic, yes, but not a typo.
Another thing that crossed my mind as far as modems/routers security and the like: What about those damn Vonage boxes? https://www.vonage.com/how-vonage-works-adapters
For the advanced user, check out the Sophos UTM for home use, which is FREE. (Used to be called Astaro UTM). I used to run IPCop but was not happy with the limitations, even with plugins. I have been running this UTM for over 7 years now and I love it.
With a home user license you get almost everything a full paid subscription would give you, and the things it does not give you, you do not need.
You should really check out pfSense if you’re still sipping the Sophos UTM cool-aid ;P
I think most people who use computers, particularly at home for personal use, don’t understand the ramifications and what they’re open to anytime they cruise the Internet or install software. People trust there’s not a problem with the software they are installing because it doesn’t happen to them. Most people haven’t been educated to the extent you and many of the experts on your site have been. Plug and play is the mindset most people are in when they install the latest device or software. They go to WalMart or Best Buy, put down their hardearned money and take the product home to use. Almost never do they perform the upfront research to educate themselves about what they’ve just bought and allowed into their homes.
Brian, you do a great service alerting us about these issues, and I thank you as I’m sure many others do.
from wemo
Our 2012 fuzz-test on NAS devices revealed hundreds of critical bugs in all NAS devices. Apparently nothing has happened since?
http://www.codenomicon.com/labs/results/nas.shtml
RE: Belkin WeMo
http://youtu.be/mqp8_ROAIJY
Internet success
😀
Obviously not layperson friendly, but I’m using a Raspberry Pi as my firewall/router/DHCP server which allows me to use my ASUS RT-N66U as a simple access point. This also simplifies the process of replacing the access point when it inevitably dies.
Ultimately, I would like to put the access point on its own network, but I need to string some more CAT 6 around the house before that can happen.
… that’s why every wifi router has a reset button in case wrong settings are selected and turns the router useless. Ask any teenager how to bypass parental controls and they’ll just state that there’s a reset button… been there with mine! LOL
During the flashing process of the ROM with a custom ROM as Tomato, if something goes wrong, you don’t have anything to reset anymore… and as Krebs says: “it turns a router into an oversized paperweight”
Thats when you set static Ip’s to each and every device. Enabling a static IP on every box will halt communications on the entire network and you should immediately know something is amok.
Sure this works on a average home or small SOHO. You can lock down most routers to a limited amount of IP’s. If the kid’s don’t have Admin rights, they can’t change the Ip’s. If they do have admin rights and do change an IP on a very limited scope, then IP conflicts should occur and the same thing applies – something went amok.
My kids knew better. I told them if they screwed with the router at all unless instructed to do so, their computer would be the last one to be configured, if at all.
I am not a big fan of wireless. I don’t know if I ever will be. With all the solid state devices out there, and now the rash of devices that may have chips that look for wifi hot spots to spew spam, I am not one to answer the door and see the State Police or Feds standing there telling me my vacuum cleaner may be cleaning the floor, but its spewing dirty emails across the internet.
Interesting that no Apple hardware is mentioned here.
Apple is not part of the Digital Living Network Alliance (DLNA).
Some of the above products could be DLNA certified. Maybe, there is a common problem that originates from DLNA compliance.
I’m running DLNA from Plex Server using Airport Extreme.
Nice article Brian… as always!
As a couple others pointed out… pfSense works wonderfully, coupled with OpenVPN and SNORT (Suricata being worked for integration currently), this is a great piece of software. Behind my pfSense box I use to run DD-WRT on my TP-Link 1043ND… but I’ve recently turned to OpenWRT as it’s a recent release and it looks like DD-WRT is dead or development has slowed.
Brian wrote: “Belkin urges such users to download the latest app from the App Store..”
Does the above imply that users can download non-Apple devce firmware from the Apple Store? If so, are directions included?
Thanks.
Nice article, made me lough when i got the FRITZ!Box vulnearabilitys in mind. FRITZ!Box is a Router by AVM pretty popular here in Germany, the german IT-News site heise.de wrote some articles about attacks on these routers with the rmote acces aktivated around 6th of february. They had a few more articles about it, telling people to turn off this feature till the patch, and the patches they rolled out. Now they wrote that the routers are also vulnearable without the remote acces turned on. May this be in connection with the other routervulnearabilitys?
Get the articles on http://www.heise.de/security (all in German)
Ditch the stock firmware… if you really know what you’re doing. I have an Asus router, that allegedly would act also as a print server for my USB HP laserjet.
“Oh, sorry, not that printer” (which it didn’t say on the box).
So I went to DD-WRT. This took about two months, including bricking the router two or three times. Then I found someone’s web page, that said a) IGNORE the router database (the first thing you’re told to use on the home page). Then, I found that there are no formal releases. And then, having joined the forum, found people talking about their “favorite” builds, something I’ve never heard in over 30 years in the industry.
I *finally* found one that worked, but have no idea if I’ll ever be able to upgrade, in case of newfound threats, without breaking it.
mark, sr. sysadmin, Linux/Unix (so, yes, I really do know what I’m doing)
Brian, I am really grateful for your willingness to help others not be hacker victims and I know that this has sometimes come at a personal cost to yourself. Thank you for continuing on with your website.
I always follow your advice, use difficult passwords; keep firmware and software up-to-date; utilize software that helps me do this [Hippo]; but this info on the routers is very confusing to me as. I am using the Linksys W54G and have been meaning to install my new one, NetGear N600 but now I am not so sure I should. I tried once before but couldn’t get it to work.
I read all the comments and understood maybe 10% of what was being said so I know my limitations. Are there companies out there who assist people in setting up new equipment so it is done right?
Thanks again.
A quote from the Sec-Consult writeup of the Symantec vulnerability that you linked to:
“This vulnerability can be used to exfiltrate database content (eg. usernames and password hashes) as well. All usernames and password hashes are stored within the database as MD5 hash without salt”
MD5 Hashed passwords without salt?!? From a security company!??! From a cryptographic standpoint, that’s essentially plaintext. Completely unacceptable from anyone who even pretends to know or care about security.
Brian – great analysis. On the ASUS topic, thus far the “check for update” function built into the GUI will not work because the server-side table of current firmware versions has not been updated since October — see http://dnlongen.blogspot.com/2014/02/breaking-down-asus-router-bug.html for an explanation. Those with an ASUS router running stock firmware must manually download the binary and then import it into the router.
Brian, what would we do without you?
My question: is there any way to check a router for malware with the help of a standard AV program, Norton 360 in my case? Or is there any other way to check/scan a router?
Sorry if my question sounds stupid.
Thanks, we owe you.
http://www.howtogeek.com/168896/10-useful-windows-commands-you-should-know/
The last one ……netstat -an – List Network Connections and Ports may help you……also … ‘netstat -ano’ which shows process numbers as well. Makes it easier to pull up task manager (or more preferably Process Explorer) and find out what exact process is using or listening for connections.
Linksys has been using their own Linux distribution since the late 90’s and Cisco IOS software has been based on the Linux kernel for at least the last 10 years (firmware updates I’ve downloaded). Newer Netgear firmware is WRT, with a “user friendly” user interface.. Microsoft, Android, Blackberry (QNX?), etc have App Stores. Android is Linux kernel based, and both Android and Windows phones can be a hotspot; i.e. include router function, and the popularity of Android would suggest its use for routers. Just goes to show that if a company works hard they can make Linux insecure.
More ASUS fun https://sintonen.fi/advisories/asus-router-auth-bypass.txt