New data gathered from the cybercrime underground suggests that the apparent credit and debit card breach at Home Depot involves nearly all of the company’s stores across the nation.
Evidence that a major U.S. retailer had been hacked and was leaking card data first surfaced Tuesday on the cybercrime store rescator[dot]cc, the shop that was principally responsible for selling cards stolen in the Target, Sally Beauty, P.F. Chang’s and Harbor Freight credit card breaches.
As with cards put up for sale in the wake of those breaches, Rescator’s shop lists each card according to the city, state and ZIP code of the store from which each card was stolen. See this story for examples of this dynamic in the case of Sally Beauty, and this piece that features the same analysis on the stolen card data from the Target breach.
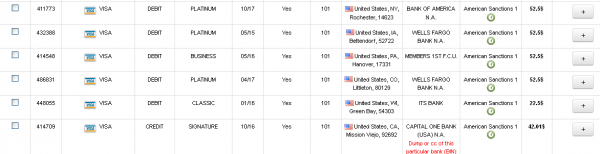
Stolen credit cards for sale on Rescator’s site index each card by the city, state and ZIP of the retail store from which each card was stolen.
The ZIP code data allows crooks who buy these cards to create counterfeit copies of the credit and debit cards, and use them to buy gift cards and high-priced merchandise from big box retail stores. This information is extremely valuable to the crooks who are purchasing the stolen cards, for one simple reason: Banks will often block in-store card transactions on purchases that occur outside of the legitimate cardholder’s geographic region (particularly in the wake of a major breach).
Thus, experienced crooks prefer to purchase cards that were stolen from stores near them, because they know that using the cards for fraudulent purchases in the same geographic area as the legitimate cardholder is less likely to trigger alerts about suspicious transactions — alerts that could render the stolen card data worthless for the thieves.
This morning, KrebsOnSecurity pulled down all of the unique ZIP codes in the card data currently for sale from the two batches of cards that at least four banks have now mapped back to previous transactions at Home Depot. KrebsOnSecurity also obtained a commercial marketing list showing the location and ZIP code of every Home Depot store across the country.
Here’s the kicker: A comparison of the ZIP code data between the unique ZIPs represented on Rescator’s site, and those of the Home Depot stores shows a staggering 99.4 percent overlap.
Home Depot has not yet said for certain whether it has in fact experienced a store-wide card breach; rather, the most that the company is saying so far is that it is investigating “unusual activity” and that it is working with law enforcement on an investigation. Here is the page that Home Depot has set up for further notices about this investigation.
I double checked the data with several sources, including with Nicholas Weaver, a researcher at the International Computer Science Institute (ICSI) and at the University California, Berkeley. Weaver said the data suggests a very strong correlation.
“A 99+ percent overlap in ZIP codes strongly suggests that this source is from Home Depot,” Weaver said.
Here is a list of all unique ZIP codes represented in more than 3,000 debit and credit cards currently for sale on Rescator’s site (Rescator limits the number of cards one can view to the first 33 pages of results, 50 cards per page). Here is a list of all unique Home Depot ZIP codes, in case anyone wants to double check my work.
In all, there were 1,822 ZIP codes represented in the card data for sale on Rescator’s site, and 1,939 unique ZIPs corresponding to Home Depot store locations (while Home Depot says it has ~2,200 stores, it is safe to assume that some ZIP codes have more than one Home Depot store). Between those two lists of ZIP codes, there are 10 ZIP codes in Rescator’s card data that do not correspond to actual Home Depot stores.
Finally, there were 127 ZIP codes for Home Depot stores that were not in the list of ZIPs represented in Rescator’s card data. However, it’s important to note that the data pulled from Rescator’s site is almost certainly a tiny fraction of the cards that his shop will put up for sale in the coming days and weeks.
What does all this mean? Well, assuming Home Depot does confirm a breach, it could give us one way to determine the likely size of this breach. The banks I spoke with in reporting this story say the data they’re looking at suggests that the breach probably started in late April or early May. To put that in perspective, the Target breach impacted just shy of 1,800 stores, lasted for approximately three weeks, and resulted in the theft of roughly 40 million debit and credit card numbers. If a breach at Home Depot is confirmed, and if this analysis is correct, this breach could be much, much bigger than Target.
How does this affect you, dear reader? It’s important for Americans to remember that you have zero fraud liability on your credit card. If the card is compromised in a data breach and fraud occurs, any fraudulent charges will be reversed. BUT, not all fraudulent charges may be detected by the bank that issued your card, so it’s important to monitor your account for any unauthorized transactions and report those bogus charges immediately.




I enjoyed reading your post. Good ideas.
Though I do not necessarily concur with the idea in totality, I regard your point of view.
Google has a dual login system for a password breach that occurred. Can’t the charge card companies do the same. Your purchase would be verified with four digit pin or name sent to your phone. To save time you call the number in advance. With out your phone no purchsse.
I doubt this would be practical. Most people would be ill prepared at the till and delays in the cellular network would cause problems.
Nice. Bravo. – http://mobile.businessweek.com/articles/2014-09-12/home-depot-didnt-encrypt-credit-card-data-former-workers-say
The security personnel in all of these stores are incompetent.
A simple hardware encrypted card reader would have prevented hackers from seeing any card data.
If there is a need for HD or Target to hold on to the CC data, they could obtain the key to decrypt the CC data and then only perform the decryption on a single server which is security hardened.
The incompetence is beyond comprehensible and these HUGE multi-billion dollar chains are clearly not handling card data with due care.
What about the overlap with other merchants of similar size? Are they substantially lower or are they about the same? Without the comparison you haven’t showed correlation yet, only coincidence.
whoah this weblog is wonderful i really like reading your posts.
Stay up the good work! You understand, lots of individuals
are looking around for this info, you can aid them greatly.