Earlier this month, beauty products chain Sally Beauty acknowledged that a hacker break-in compromised fewer than 25,000 customer credit and debit cards. My previous reporting indicated that the true size of the breach was at least ten times larger. The analysis published in this post suggests that the Sally Beauty breach may have impacted virtually all 2,600+ Sally Beauty locations nationwide.
Sally Beauty has declined to speculate on how many stores or total cards may have been exposed by the breach, saying in a statement last week that so far its analysis indicates fewer than 25,000 cards were compromised. But that number seems very conservative when viewed through the prism of data from the cybercriminal shop primarily responsible for selling cards stolen from Sally Beauty customers. Indeed, it suggests that the perpetrators managed to hoover up cards used at nearly all Sally Beauty stores.
The research technique used to arrive at this conclusion was the same method that allowed this reporter and others to conclude that the Target hackers had succeeded at installing card-stealing malware on cash registers at nearly all 1,800 Target locations in the United States.
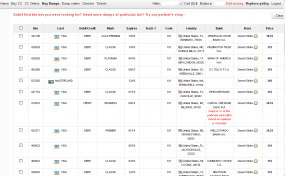
The first indications of a breach at Target came when millions of cards recently used at the big box retailer started showing up for sale on a crime shop called Rescator[dot]so. This site introduced an innovation that to my knowledge hadn’t been seen before across dozens of similar crime shops in the underground: It indexed stolen cards primarily by the city, state and ZIP code of the Target stores from which each card had been stolen.
This feature was partly what allowed Rescator to sell his cards at much higher prices than other fraud shops, because the ZIP code feature allowed crooks to buy cards from the store that were stolen from Target stores near them (this feature also strongly suggested that Rescator had specific and exclusive knowledge about the breach, a conclusion that has been supported by previous investigations on this blog into the malware used at Target and the Internet history of Rescator himself).
To put the ZIP code innovation in context, the Target break-in came to light just a week before Christmas, and many banks were at least initially reluctant to reissue cards thought to be compromised in the breach because they feared a backlash from consumers who were busy doing last minute Christmas shopping and traveling for the holidays. Rather, many banks in the interim chose to put in place “geo blocks” that would automatically flag for fraud any in-store transactions that were outside the customer’s normal geographic purchasing area. The beauty of Rescator’s ZIP code indexing was that customers could buy only cards that were used at Target stores near them, thereby making it far more likely that Rescator’s customers could make purchases with the stolen cards without setting off geo-blocking limits set by the banks.
To test this theory, researchers compiled a list of the known ZIP codes of Target stores, and then scraped Rescator’s site for a list of the ZIP codes represented in the cards for sale. Although there are more than 43,000 ZIP codes in the United States, slightly fewer than 1,800 unique ZIPs were referenced in the Target cards for sale on Rescator’s shop — roughly equal to the number of Target locations across America.
Sally Beauty declined to provide a list of its various store ZIP codes, but with the assistance of several researchers — none of whom wished to be thanked or cited in this story — I was able to conduct the same analysis with the new batch of cards on Rescator’s site that initially tipped me off to the Sally Beauty breach. The result? There are nearly the exact same number of U.S. ZIP codes represented in the batch of cards for sale on Rescator’s shop as there are unique U.S. ZIP codes of Sally Beauty stores (~2,600).
More importantly, there was a 99.99 percent overlap in the ZIP codes. That strongly suggests that virtually all Sally Beauty stores were compromised by this breach.
And here we come full circle to an explanation of why there is almost no chance that the number of breached cards is limited to fewer than 25,000. Let’s assume for the moment that Sally Beauty managed to detect and eradicate the threat that led to this payment card breach within the first 24 hours. That would essentially mean that only 10 transactions total were compromised from each store that day before the company managed to stop the theft. It’s possible, but unlikely.
What is more likely is that this batch of 282,000 cards (dubbed “Desert Strike” by Rescator) will be the first of several pushed out to Rescator’s shops in the coming weeks. Time will tell.
I asked Sally Beauty to comment on my findings. They declined again to offer any more detail on the breach, issuing the following statement:
“As experience has shown in prior data security incidents at other companies, it is difficult to ascertain with certainty the scope of a data security incident prior to the completion of a comprehensive forensic investigation. As a result, we will not speculate as to the scope or nature of the data security incident. Please check sallybeautyholdings.com for updates.”
The zip code analysis is available in this .csv spreadsheet.




Re: a comment on present instability of InfoSec and big data
My sense is that security and information handling are going to remain unstable for quite some time as they don’t appear to be in a Nash Equilibrium, and there doesn’t appear to be a common agreement on what the stable state might be.
I see quite a few “cookie policies”, and “information policies” popping up on websites now, as if in reaction to , or to be proactive to changes in a variety of information related areas, such as technology parity (the blackhats improved capabilities rival that of the whitehats), privacy concerns (government and corporate), growing public awareness (of the danger of information sharing), and corporate awareness (data as a legal liability).
The credit monitoring as damage control, the new ‘privacy policies’, the ‘cookie and information gathering policies’ being more prevalent all strike me as knee-jerk reactions looking at legal liability and not addressing the fundamental unstable position of gambling with other people’s data.
And folks going to ad-blockers, TOR, disconnect.me, and generally incognito seem similarly short term and temporary conditions. Folks are running from danger A to danger B, but it’s clear they are going to run from danger B as well (eg. keeping cash at home).
And the InfoSec folks, implementing their various schemes; same boat, different paddle. It’s clear we can’t collect everything forever without certainty of loss, so we know that we must move from collecting as much as we can and leveraging the data.
If we are indeed out of Nash Equilibrium, we should see an increase in the pace of various ‘moves’ as the players attempt to position themselves ‘ahead of the game’.
It does make one wonder where a potential equilibrium may be though. If we could get a common vision on what that might be, then at least folks could try to get there rather than this fairly ugly process we seem to be in now.
To the folks who are incensed that Sally’s allowed this to happen: Yes, they are doing a terrible job of communicating in the wake of the breach. And yes, they may have been careless at security in some way to allow it to happen, though we don’t yet have information on exactly how it occurred.
But don’t be quick to condemn. Do you think that Sally’s allowed someone from a computer address in Russia to log directly into their servers? All those eastern European criminals rely on people in the US to allow their home and business PCs to become infected with malicious software through careless browsing and out-of-date antivirus software. They can then control those infected PC’s and use them as “proxies” to hopscotch from their own computers to businesses like Sally’s while hiding their real location.
If Americans consumers were as concerned about breaches of their own computers as they are about those of Target and Sally’s Beauty, there would be a lot fewer open proxies available to the criminals.
Oh, and yes, when your computer is infected, the criminals can grab all your personal data, photos, etc., without you having to go to the inconvenience of making a credit card purchase, and they might even be able to get some photos through your web cam. If you’re upset about a stolen credit card — that consumer protection laws cover — and not about your own infected computer, you’re not grasping what’s going on here.
Actually, my firewall and IPS logs would beg to differ. Most of the attempts to log in remotely come from places like eastern Europe and China. Very few attempts (comparatively) originate from PCs inside the US.
Looks like the lawsuits have begun at least with Target:
“The class action led by Trustmark National Bank and Green Bank, say the retailer (Target) should not have allowed an outside contractor the access to its network that brought about the breach, and that it violated federal and state laws in storing the credit card data on its network.”
(taken from this link http://www.theregister.co.uk/2014/03/26/banks_lob_sueball_at_trustwave_target/ )
I agree with AlphaCentauri, people outside of circles like this just don’t seem to care a lot. They don’t “get” that they’re part of the cycle in ways that they can control. If cyber crooks were force-feeding porn instead of data-stealing malware, it would be in the news 24/7.
Target made a big splash because of its size and because it was like being told that Mom and Pop had been mugged. It was shocking. But it is hard to blame retailers for trying to do damage control (hard, but not impossible), because they are in business to make money. It is never going to be in their short-term best interest to ‘fess up, and short term is just too often where they are focused.
So, who’s going to protect Mom and Pop? The new consumer protection agency? The FTC, Justice department? FBI? Interpol? Then, they’re all going to have to get a lot busier. You can’t blame consumers from failing to protect themselves against something that they really don’t understand and that they are getting so little information about.
All this shows my that the BP model of public relations is still the norm (what, me worry?). CYA until the lawsuits are over.
The consumer is just prey every which way.