The previous two posts on this blog have featured stories about banks buying back credit and debit card accounts stolen in the Target hack and that ended up for sale on rescator[dot]la, a popular underground store. Today’s post looks a bit closer at open-source information on a possible real-life identity for the proprietor of that online fraud shop.
Rescator[dot]la is run by a miscreant who uses the nickname Rescator, and who is a top member of the Russian and English language crime forum Lampeduza[dot]la. He operates multiple online stores that sell stolen card data, including rescator[dot]la, kaddafi[dot]hk, octavian[dot]su and cheapdumps[dot]org. Rescator also maintains a presence on several other carding forums, most notably cpro[dot]su and vor[dot]cc.
![A private message on cpro[dot]su between Rescator and a member interested in his card shop. Notice the ad for Rescator's email flood service at the bottom.](https://krebsonsecurity.com/wp-content/uploads/2013/12/rescator-pm-cpro-600x153.png)
A private message on cpro[dot]su between Rescator and a member interested in his card shop. Notice the ad for Rescator’s email flood service at the bottom; this will become important as you read on.
![Rescator, a.k.a. "Hel" a.k.a. "Helkern" the onetime administrator of the Darklife forum, introduces himself to vor[dot]cc crime forum members.](https://krebsonsecurity.com/wp-content/uploads/2013/12/vor-1edited-600x414.png)
Rescator, a.k.a. “Hel” a.k.a. “Helkern” the onetime administrator of the Darklife forum, introduces himself to vor[dot]cc crime forum members.
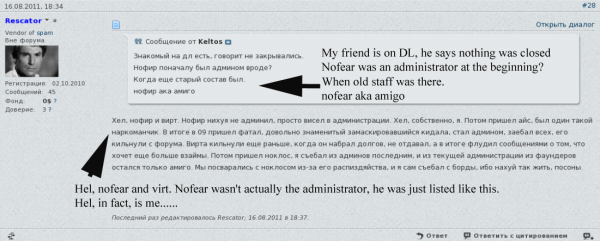
The only darklife member who matched that nickname was “Helkern,” one of darklife’s three founders. Darklife administrators were all young men who fancied themselves skilled hackers, and at one point the group hacked into the venerable and closely-guarded Russian hacking forum cih[dot]ms after guessing the password of an administrator there.
![Darklife admin "Helkern" brags to other members about hacking into cih[dot]ms, a more elite Russian hacking forum.](https://krebsonsecurity.com/wp-content/uploads/2013/12/cihhacked-600x470.png)
Darklife admin “Helkern” brags to other members about hacking into cih[dot]ms, a more elite Russian hacking forum.
And a self-portrait of Helkern:
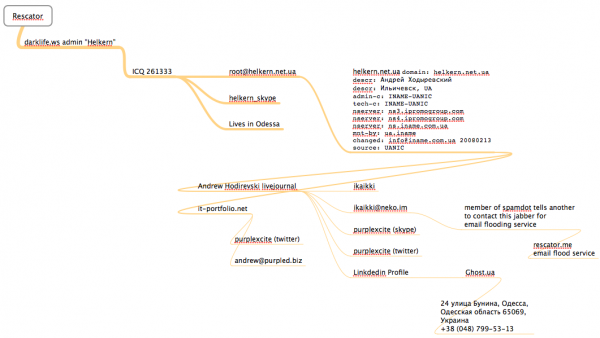
So if Helkern is Rescator, who is Helkern? If we check at some of the other Russian forums that Helkern was active in at the time that Darklife was online in 2008, we can see he was a fairly frequent contributor to the now-defunct Grabberz[dot]com; in this cached post, Helkern can be seen pasting an exploit he developed for a remote SQL injection vulnerability. In it, he claims ownership of the ICQ instant messenger address 261333.
In this introductions page from a Russian language gaming forum, a user named Helkern also was active in 2008 and claimed that same ICQ address. Helkern said his email address was root@helkern.net.ua, his Skype address was helkern_skype, and that he lived in Odessa, the third-largest city in Ukraine. Helkern — going by his shortened username “Hel,” also was a VIP member of xaker[dot]name. In this cached post we can see him again claiming the 261333 ICQ address, and pointing out to other members that his real nickname is Helkern.
A historic WHOIS lookup ordered from domaintools.com shows that helkern.net.ua was first registered in 2008 to an Andrey Hodirevski from Illichivsk, a city in the Odessa province of southwestern Ukraine.
I located a relatively recent Livejournal profile (ikaikki.livejournal.com/profile) for an Andrew Hodirevski from Odessa, Ukraine that includes several profile pictures which are remarkably similar to the photos of Helkern leaked by the cih[dot]ms guys. That profile (“ikaikki“) says Hodirevski’s email address is ikaikki@livejournal.com, that his Jabber instant message address is ikaikki@neko.im, and that his Twitter account is “purplexcite” (that Twitter has since been deleted). In almost a dozen posts on LiveJournal, Hodirevski talks about his interest in Java programming, and even includes a few pictures of himself attending an instructional class on Java.
The same anime profile image for Andrew’s LiveJournal page is also on the LinkedIn profile for an Andrew Hodirevski from Ukraine, and the two pages share the aforementioned Twitter profile (purplexcite). Andrew’s LinkedIn page also says he is the administrator and Web developer at a hosting company in Ukraine called ghost.ua.
That site is no longer online, but a cached copy of it at archive.org shows that the business is located in Odessa at this address, and the phone number +38 (048) 799-53-13. Ghost.ua lists several pricing plans for its servers, naming them after different despotic leaders, including Fidel Castro and Muammar Gaddafi (it is spelled “Kaddafi” on Ghost.ua). Recall as I mentioned at the top of this post that one of the clones of the card shop at Rescator[dot]la is kaddafi[dot]hk.
This page at it-portfolio.net lists an Andrey Hodirevski from Odessa with the same anime profile image, the “purplexcite” Twitter profile, and a Skype address by the same name. It says his professional skills include programming in Java, CakePHP and MySQL, among others. This Google groups discussion about CakePHP includes a message from an Andrey Hodirevski who uses the email address andrew@purpled.biz.
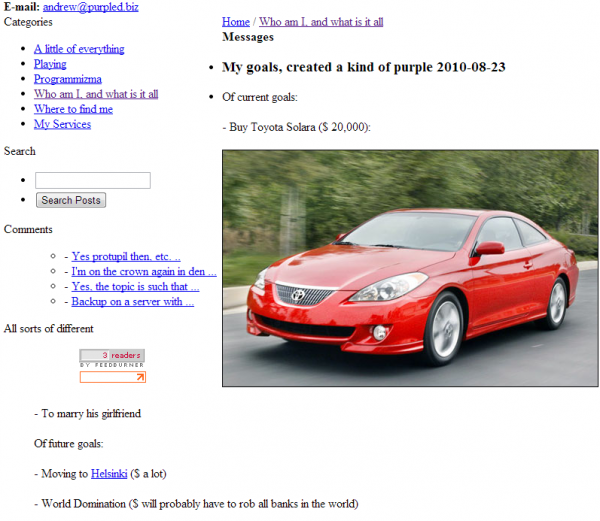
Purpled.biz is no longer online, but a cached copy of it from archive.org shows it was once Andrew’s personal site. Here we learned that Andrew’s current goals (as of 2010) were to get married to his girlfriend, buy the $20,000 Toyota Solara pictured below, move to Helsinki, and to achieve world domination. In order to accomplish the latter goal, Andrew jokes that he “will probably have to rob all the banks in the world.”
 After searching my huge personal archive of hacked cybercrime forums for Andrew’s various email and Jabber addresses, I found several private messages sent by different users on the Spamdot[dot]biz forum who recommended to other members the “ikaikki@neko.im” Jabber address as someone to contact in order to hire a service that could be used to flood someone’s Gmail inbox with tens or hundreds of thousands of junk messages. Recall that this Jabber address is the same one listed at Andrew’s LiveJournal profile.
After searching my huge personal archive of hacked cybercrime forums for Andrew’s various email and Jabber addresses, I found several private messages sent by different users on the Spamdot[dot]biz forum who recommended to other members the “ikaikki@neko.im” Jabber address as someone to contact in order to hire a service that could be used to flood someone’s Gmail inbox with tens or hundreds of thousands of junk messages. Recall that this Jabber address is the same one listed at Andrew’s LiveJournal profile.
To bring this full circle, one of the many services that Rescator sells these days is a popular email flooding service at rescator[dot]me. Turns out, Yours Truly has already been the direct target of an attack launched through Rescator’s service; I wrote about it in this July 2012 story, Cyberheist Smokescreen: Email, Phone, SMS Floods.
I have no idea if Rescator/Helkern/Andrew was involved in hacking Target, but it’s a good bet that he at least knows who was. I sought comment from various contact addresses listed above for this individual, and received a reply from someone at kaddafi[dot]me who said he knew Andrew and would relay my questions to him. Ultimately, he came back to me not with answers, but with a bribe not to run my story.(1:48:35 PM) krebs//: hi
(1:48:44 PM) krebs//: brian krebs here
(1:49:05 PM) krebs//: trying to reach rescator
(1:49:11 PM) krebs//: aka andrey
(1:51:12 PM) krebs//: don’t believe it’s really krebs?
(1:51:15 PM) krebs//: http://krebsonsecurity.com/wp-content/uploads/2013/12/kaddaficon.png
(1:53:32 PM) krebs//: 🙂
(1:53:53 PM) krebs//: tyt?
(2:00:14 PM) kaddafi.me: Hello Brian 🙂
(2:00:24 PM) kaddafi.me has not been authenticated yet. You should authenticate this buddy.
(2:00:24 PM) Unverified conversation with kaddafi.me/Muammar started. Your client is not logging this conversation.
(2:00:30 PM) kaddafi.me: ooo you’ve got OTR
(2:00:37 PM) kaddafi.me: Afraid of NSA? )
(2:01:38 PM) kaddafi.me: Why do you want to talk to Andrew?
(2:03:46 PM) krebs//: i am more afraid of others
[Image] (2:03:56 PM) The privacy status of the current conversation is now: Private
(2:04:11 PM) kaddafi.me: Yeah well you should after someone sent you drugs from silkroad.
(2:04:24 PM) krebs//: 🙂
(2:04:59 PM) krebs//: you’re right of course, it’s andrew 🙂
(2:05:17 PM) kaddafi.me: What’s all the commotion about Rescator anyways?
(2:05:20 PM) krebs//: well i have a story about him going up tomorrow
(2:05:23 PM) kaddafi.me: Did you even notice other shops are selling same shit?
(2:05:32 PM) krebs//: sure
(2:05:46 PM) krebs//: but I’m not looking at other shops right now
(2:06:05 PM) kaddafi.me: Well you should )
(2:06:10 PM) krebs//: in time 🙂
Kaddafi promised a response by 10 p.m. ET yesterday. This morning, not seeing a response, I pinged this individual again, and received the following response:
(10:08:46 AM) kaddafi.me: Hi.
(10:09:19 AM) kaddafi.me: You better contact me from another jabber that’s not associated with your name, I’ve got an offer for you.
(10:11:12 AM) krebs//: why from a different jabber?
(10:11:33 AM) kaddafi.me: Because I’ve got an offer for you. So you don’t think I’m trying to play games and fool around with logs after you read my offer.
(10:11:52 AM) krebs//: what kind of offer?
(10:12:27 AM) $10.000 not to post your article
Obviously, I did not take him up on his offer, assuming he was not just messing with me. Here is a mind map I put together (using MindNode Pro for Mac) that outlines how much of this information was derived and connected.






![The email flood service at rescator[dot]me](https://krebsonsecurity.com/wp-content/uploads/2013/12/rescator-me-news-600x360.png)

As someone who used a debit card at Target during the data breach period, I’ve been obsessively checking my bank statements for anything abnormal. I obviously haven’t seen anything yet, but I can’t help but imagine how many other shoppers like myself already think they’re in the clear because things have been quiet—when characters like this “Rescator” guy could be holding our information off to the highest bidder.
This is why this situation won’t be dying down anytime soon, even if Target wants it too. Folks might be crying fraud as late as March. Moral of the story: Always carry cash!
Why wouldnt you just have a new card issued? In most cases a new card can be issued without canceling the old card until the new one arrives, and even if you do have to go without a card for a few days you can use cash and you will be protected.
You can cancel your card now, or you can do it after there is fraud, either way, same process. Based on the carding forums it looks like he may be moving as many as 50,000 cards a day, so its only a matter of time before all the numbers are out there and fraudulent charges hit.
You don’t even have to go without a card if you have a local branch office and don’t mind a trip there (this is what I did). Whenever you are ready to cancel the current card, call the bank to have them cancel, then go to the local branch and have them create a temporary new card that is linked to your account. Your new permanent card will be mailed in a few days and you can trash the temporary card.
Exactly. The day I heard this news about this Target breach, I ran to my bank, cancelled my debit card and ordered a new numbered debit card. Writing checks for over a week has been a pain but well worth it as far as some semblance of security.
Ditto. I just got a new debit card. Including travel time to and from the local bank branch, replacing the debit card took about one hour. Totally painless.
They will sit on this information much longer than a few months. Often times fraud will not be attempted for 6-12 months (or longer) after the compromise occurred.
If it was used at Target during the time frame it is unquestionably compromised. Get a new card.
Where have you heard this? I see people getting site dump and using the cards as it downloads lol
Get a new debt card, have the bank turn the other one off, start using prepaid debit/visas for purchases. Only use debit card at bank ATMs
Ms. Katrina Lowe . . . My sentiments exactly.
(For Years I have been warning folks to use Cash when you can.)
Cash is King IMO but unfortunately society is downgrading cash and really pushing for the use of MORE plastic!!!
TR
I actually called Bank of America to request a new card…and they told me they had actually shipped one out to me already (sans my request). I guess they’re doing this automatically now? I had no idea, but great. At least they know this can still cause issues down the road.
I’m going to be way more cash-friendly in 2014, regardless.
Katrina,
It’s best that you cancel you’re debt card for a new one. When they sell credit cards over the “Black Market” a good amount get sold in bulk, so for example. They sell 100 credit card numbers for $500.00 or for bitcoins (The unregulated online currency) but they sell the same list to many different people around the world, so they keep trying to use one until it gets accepted. So the odds may not be in you’re favor. I wouldn’t stress yourself by looking at your bank statement.
Anyone else notice they took down the Lampeduza[dot]la site today?
Rescator[dot]la down too, although it has gone up and down a bunch the past few days. I tried through tor as well without being able to get there. Curious if its actually down or if the US has made an attempt to block access in some way.
Brian, I understand the primal urge to seek out more when you find clues and hints and you know more than everyone else, but don’t you at some point expect more retaliation than a bundle of drugs from silk road arriving at your doorstep? I mean, to call out criminals publicly by name seems bold and unnecessary. Aren’t there more effective ways to help in the fight against cyber crime?
I applaud you Brian! You are a fearless man; a good example. Thanks for all you do!
Get a new debt card, have the bank turn the other one off, start using prepaid debit/visas for purchases. Only use debit card at bank ATMs
I haven’t yet seen a discussion of risk if the cardholder used Target’s debit card.
Well done, Krebs 😉
Vor.cc is free registration with no acceptance process anymore.
This Andrey/Andrew should be eliminated. All criminals involved in these massive breaches should be eliminated.
But I guess the US government is too busy seizing the websites of counterfeit jersey sellers, and mp3 search sites.
As usual, great detective work and related article, Brian Krebs.
Why can’t the authorities work as accurately and timely and, as a result, permanently take down these micreants?
Not unlike a rogue TV repair service, they will merely reinvent themselves and be back in business in 48 hours or less.
Doxxing another carder… Interesting stuff bk! Looking forward to the inevitable posts about you getting swatted again…
I found this on CSO….. Its a compilation of what to do articles based on the Target breach. Some are business suggestions, some consumer suggestions.
Hope it Helps, Target shoppers……
http://www.csoonline.com/article/744888/cso-s-guide-to-the-target-data-breach-updated-12-23-?source=rss_news
My bank already called me and told me my card was one of the ones stolen, and they replaced it. I don’t know how they would know this. Maybe they saw I made a transaction at Target and decided to take preventive measures? Whatever it was, its a pain in the ass to update my card information everywhere.
There is no dirty money in Ukraine 🙂 Just money …
Why are you so popular? I saw your name on Betabot once, but that was about it. Is it because your an old timer?
Possibly because he knows the proper usage of the words your / you’re.
Sorry, I didn’t know you are a grammar nazi.
I hate grammar but that is not being a grammar nazi – you just spend too much time texting or something, lol
No hard feelings, I do spend a lot of time chatting texting.
I should’ve checked my reply before commenting, but you’re still a grammar nazi ;).
For example^…lol…i’m really….out of it.
Very good…avoid the contraction altogether!
Were eastern Europeans should get money then? In uraine people earn about 200$ month its not enought! Everyone like good life
Anyways cybercrime is old stufff its not actual anymore! Pointless to talk about this just kids having fun
How is it old? I still see phone scams, cc fraud, blackmailing, ppd, ddos attacks & other stuff every month.
QUESTION – Any word on just how the malware made it into Targets systems as of yet? I saw some articles out in the news sites saying that Target confirmed this as a malware, but I cannot find anything to say if this was a result of a spear phishing attack or a break in through a back door or some other type of attack?
Top executives lack technical understanding. They provide small budgets for IT departments.
This happens all over the place. The fact that a system looks nice in the outside may be a mess in the inside.
They are greedy when it comes to hire good developers and now we all have to pay for it.
If this world was led by IT people, it would be much more efficient
Great job Brian! I bet the kid is shitting in his pants since then 🙂
CNNMoney
Target says ‘up to 70 million’ names, email addresses, and…
The Verge - by Aaron Souppouris - 20 hours ago
The retailer says up to 70 million names, mailing addresses, phone numbers or email addresses were stolen as part of last November’s hack. … Target is extending that offer, now saying that any customer who has shopped at …
So now they are saying addresses, emails ( not uncommon) etc were accessed. Quite interesting as having delt with people that did card scams ( mostly by theft) and money laundering they always said the more they could get the better, but why was target maintaining all that information. Even the CVV.
I doubt that he has anything to do with the hack. CC numbers went on sale in Russia 2-3 weeks prior and they were 20-30x times cheaper comparing to what Andrey was charging. He is just a 2nd or 3rd-tier re-seller.
there’s a big price diff between stolen credit cards (CCs) and dumps. one you use to card stuff online, the other you can make fake plastic out of. dumps are about 10x as expensive as CCs.
@Krebs:
Incredible amount of brain power and personal time involved in this. I sincerely commend you in your work on this.