The previous two posts on this blog have featured stories about banks buying back credit and debit card accounts stolen in the Target hack and that ended up for sale on rescator[dot]la, a popular underground store. Today’s post looks a bit closer at open-source information on a possible real-life identity for the proprietor of that online fraud shop.
Rescator[dot]la is run by a miscreant who uses the nickname Rescator, and who is a top member of the Russian and English language crime forum Lampeduza[dot]la. He operates multiple online stores that sell stolen card data, including rescator[dot]la, kaddafi[dot]hk, octavian[dot]su and cheapdumps[dot]org. Rescator also maintains a presence on several other carding forums, most notably cpro[dot]su and vor[dot]cc.
![A private message on cpro[dot]su between Rescator and a member interested in his card shop. Notice the ad for Rescator's email flood service at the bottom.](https://krebsonsecurity.com/wp-content/uploads/2013/12/rescator-pm-cpro-600x153.png)
A private message on cpro[dot]su between Rescator and a member interested in his card shop. Notice the ad for Rescator’s email flood service at the bottom; this will become important as you read on.
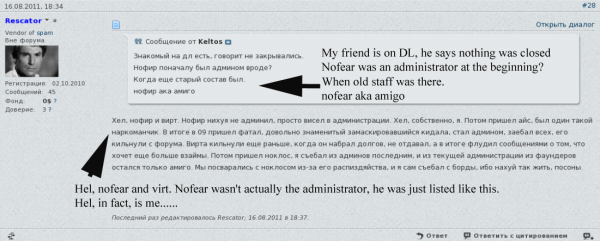
![Rescator, a.k.a. "Hel" a.k.a. "Helkern" the onetime administrator of the Darklife forum, introduces himself to vor[dot]cc crime forum members.](https://krebsonsecurity.com/wp-content/uploads/2013/12/vor-1edited-600x414.png)
Rescator, a.k.a. “Hel” a.k.a. “Helkern” the onetime administrator of the Darklife forum, introduces himself to vor[dot]cc crime forum members.
The only darklife member who matched that nickname was “Helkern,” one of darklife’s three founders. Darklife administrators were all young men who fancied themselves skilled hackers, and at one point the group hacked into the venerable and closely-guarded Russian hacking forum cih[dot]ms after guessing the password of an administrator there.
![Darklife admin "Helkern" brags to other members about hacking into cih[dot]ms, a more elite Russian hacking forum.](https://krebsonsecurity.com/wp-content/uploads/2013/12/cihhacked-600x470.png)
Darklife admin “Helkern” brags to other members about hacking into cih[dot]ms, a more elite Russian hacking forum.
And a self-portrait of Helkern:
So if Helkern is Rescator, who is Helkern? If we check at some of the other Russian forums that Helkern was active in at the time that Darklife was online in 2008, we can see he was a fairly frequent contributor to the now-defunct Grabberz[dot]com; in this cached post, Helkern can be seen pasting an exploit he developed for a remote SQL injection vulnerability. In it, he claims ownership of the ICQ instant messenger address 261333.
In this introductions page from a Russian language gaming forum, a user named Helkern also was active in 2008 and claimed that same ICQ address. Helkern said his email address was root@helkern.net.ua, his Skype address was helkern_skype, and that he lived in Odessa, the third-largest city in Ukraine. Helkern — going by his shortened username “Hel,” also was a VIP member of xaker[dot]name. In this cached post we can see him again claiming the 261333 ICQ address, and pointing out to other members that his real nickname is Helkern.
A historic WHOIS lookup ordered from domaintools.com shows that helkern.net.ua was first registered in 2008 to an Andrey Hodirevski from Illichivsk, a city in the Odessa province of southwestern Ukraine.
I located a relatively recent Livejournal profile (ikaikki.livejournal.com/profile) for an Andrew Hodirevski from Odessa, Ukraine that includes several profile pictures which are remarkably similar to the photos of Helkern leaked by the cih[dot]ms guys. That profile (“ikaikki“) says Hodirevski’s email address is ikaikki@livejournal.com, that his Jabber instant message address is ikaikki@neko.im, and that his Twitter account is “purplexcite” (that Twitter has since been deleted). In almost a dozen posts on LiveJournal, Hodirevski talks about his interest in Java programming, and even includes a few pictures of himself attending an instructional class on Java.
The same anime profile image for Andrew’s LiveJournal page is also on the LinkedIn profile for an Andrew Hodirevski from Ukraine, and the two pages share the aforementioned Twitter profile (purplexcite). Andrew’s LinkedIn page also says he is the administrator and Web developer at a hosting company in Ukraine called ghost.ua.
That site is no longer online, but a cached copy of it at archive.org shows that the business is located in Odessa at this address, and the phone number +38 (048) 799-53-13. Ghost.ua lists several pricing plans for its servers, naming them after different despotic leaders, including Fidel Castro and Muammar Gaddafi (it is spelled “Kaddafi” on Ghost.ua). Recall as I mentioned at the top of this post that one of the clones of the card shop at Rescator[dot]la is kaddafi[dot]hk.
This page at it-portfolio.net lists an Andrey Hodirevski from Odessa with the same anime profile image, the “purplexcite” Twitter profile, and a Skype address by the same name. It says his professional skills include programming in Java, CakePHP and MySQL, among others. This Google groups discussion about CakePHP includes a message from an Andrey Hodirevski who uses the email address andrew@purpled.biz.
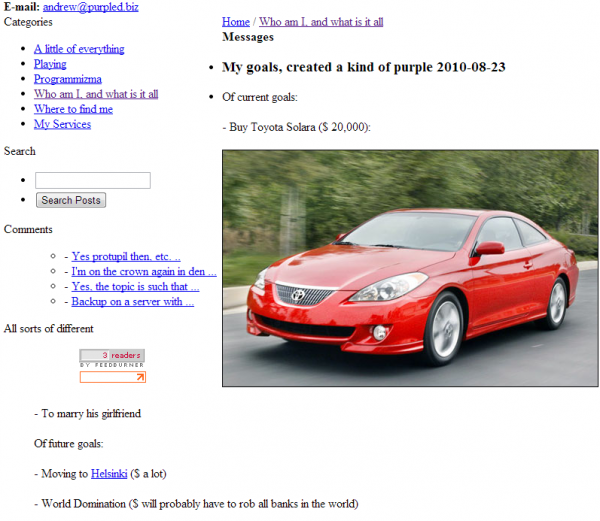
Purpled.biz is no longer online, but a cached copy of it from archive.org shows it was once Andrew’s personal site. Here we learned that Andrew’s current goals (as of 2010) were to get married to his girlfriend, buy the $20,000 Toyota Solara pictured below, move to Helsinki, and to achieve world domination. In order to accomplish the latter goal, Andrew jokes that he “will probably have to rob all the banks in the world.”
 After searching my huge personal archive of hacked cybercrime forums for Andrew’s various email and Jabber addresses, I found several private messages sent by different users on the Spamdot[dot]biz forum who recommended to other members the “ikaikki@neko.im” Jabber address as someone to contact in order to hire a service that could be used to flood someone’s Gmail inbox with tens or hundreds of thousands of junk messages. Recall that this Jabber address is the same one listed at Andrew’s LiveJournal profile.
After searching my huge personal archive of hacked cybercrime forums for Andrew’s various email and Jabber addresses, I found several private messages sent by different users on the Spamdot[dot]biz forum who recommended to other members the “ikaikki@neko.im” Jabber address as someone to contact in order to hire a service that could be used to flood someone’s Gmail inbox with tens or hundreds of thousands of junk messages. Recall that this Jabber address is the same one listed at Andrew’s LiveJournal profile.
To bring this full circle, one of the many services that Rescator sells these days is a popular email flooding service at rescator[dot]me. Turns out, Yours Truly has already been the direct target of an attack launched through Rescator’s service; I wrote about it in this July 2012 story, Cyberheist Smokescreen: Email, Phone, SMS Floods.
I have no idea if Rescator/Helkern/Andrew was involved in hacking Target, but it’s a good bet that he at least knows who was. I sought comment from various contact addresses listed above for this individual, and received a reply from someone at kaddafi[dot]me who said he knew Andrew and would relay my questions to him. Ultimately, he came back to me not with answers, but with a bribe not to run my story.(1:48:35 PM) krebs//: hi
(1:48:44 PM) krebs//: brian krebs here
(1:49:05 PM) krebs//: trying to reach rescator
(1:49:11 PM) krebs//: aka andrey
(1:51:12 PM) krebs//: don’t believe it’s really krebs?
(1:51:15 PM) krebs//: http://krebsonsecurity.com/wp-content/uploads/2013/12/kaddaficon.png
(1:53:32 PM) krebs//: 🙂
(1:53:53 PM) krebs//: tyt?
(2:00:14 PM) kaddafi.me: Hello Brian 🙂
(2:00:24 PM) kaddafi.me has not been authenticated yet. You should authenticate this buddy.
(2:00:24 PM) Unverified conversation with kaddafi.me/Muammar started. Your client is not logging this conversation.
(2:00:30 PM) kaddafi.me: ooo you’ve got OTR
(2:00:37 PM) kaddafi.me: Afraid of NSA? )
(2:01:38 PM) kaddafi.me: Why do you want to talk to Andrew?
(2:03:46 PM) krebs//: i am more afraid of others
[Image] (2:03:56 PM) The privacy status of the current conversation is now: Private
(2:04:11 PM) kaddafi.me: Yeah well you should after someone sent you drugs from silkroad.
(2:04:24 PM) krebs//: 🙂
(2:04:59 PM) krebs//: you’re right of course, it’s andrew 🙂
(2:05:17 PM) kaddafi.me: What’s all the commotion about Rescator anyways?
(2:05:20 PM) krebs//: well i have a story about him going up tomorrow
(2:05:23 PM) kaddafi.me: Did you even notice other shops are selling same shit?
(2:05:32 PM) krebs//: sure
(2:05:46 PM) krebs//: but I’m not looking at other shops right now
(2:06:05 PM) kaddafi.me: Well you should )
(2:06:10 PM) krebs//: in time 🙂
Kaddafi promised a response by 10 p.m. ET yesterday. This morning, not seeing a response, I pinged this individual again, and received the following response:
(10:08:46 AM) kaddafi.me: Hi.
(10:09:19 AM) kaddafi.me: You better contact me from another jabber that’s not associated with your name, I’ve got an offer for you.
(10:11:12 AM) krebs//: why from a different jabber?
(10:11:33 AM) kaddafi.me: Because I’ve got an offer for you. So you don’t think I’m trying to play games and fool around with logs after you read my offer.
(10:11:52 AM) krebs//: what kind of offer?
(10:12:27 AM) $10.000 not to post your article
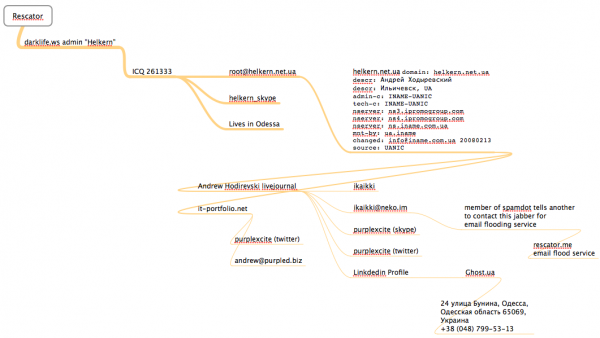
Obviously, I did not take him up on his offer, assuming he was not just messing with me. Here is a mind map I put together (using MindNode Pro for Mac) that outlines how much of this information was derived and connected.






![The email flood service at rescator[dot]me](https://krebsonsecurity.com/wp-content/uploads/2013/12/rescator-me-news-600x360.png)

Love the story..
Great job
Fascinating. Just like Cuckoo’s Egg when it first came out.
Great work as usual, Brian. You spoil us. I hope this guy, together with his buddies will be sometime apprehended, but even if he will be not, I hope he will be seriously inconvenienced by authorities in his country eager for their share. After all he was, as another commenter pointed out once under house arrest, he might be reached again by the long arm of law is he doesn’t pay his dues.
Mi concern is that those guys will get better and better at not exposing themselves, remember 1999-2000 ? At that time the botnets were more like a technological curiosity, certainly not monetized and the phishing mails I was receiving were so ridiculous and rif with grammatical errors that I thought nobody would fall for such a thing. Just little over 10 years later both of them are genuine threats….
Love it how the jeep he’s posing in has a flat front tire. And who goes for coffeemugs when one can have plastic throw-aways
Just syncs with the way the trail leads to him.
Reminds me of the process of linking persistent cheaters across different guid’s/games that cannot resist using same/similar names across all game keys (think server admin streaming to anticheat like PBBans)
Hey Brian, nice mind map. But I though you would have been using Paterva / Maltego for case investigation these days..
This is fantastic research Brian, fascinating and informative.
Top work Brian. I hope you have a Merry Christmas and a Happy New Year. I look forward to more from you in 2014.
I’ll revenge, brian.
hello helkern figured you’d comment here this is pixl8er i pinged your email.
Well done, Brian!
I like the fakt that some kid( if thats him ) manage to f@ck half of America so badly that they still dont know whats happend to them . Quality .Very Well done .
Sorry, script kiddie is just the next to last link in the food chain; the real puzzler is – whodunit? Who pilfered/installed worms/trojans malware on POS readers or terminals, card scanners AND how did they spirit the info off Target property and across national borders … now THAT was some trick.
Hawking stolen goods? Not so much …
40 million cards of a population of 313 million. Hardly half of the country and it cost the consumer nothing. In fact, with Target knocking off 10% this past week, it would seem that most of America benefited from this kiddy hack.
andy – ” with Target knocking off 10% this past week, it would seem that most of America benefited from this kiddy hack.”
Is this the modern day (contemporary version of) the “Broken Window Fallacy”? From wiki:
” The parable of the broken window was introduced by Frédéric Bastiat in his 1850 essay … to illustrate why destruction, and the money spent to recover from destruction, is actually __not__ a net-benefit to society. ”
I think the time and effort spent cancelling cards, arranging for new cards, has overall put a damper on economic activity, let alone the additional costs borne by all involved results in, of course, a net-negative. Those w/o the benefit of a proper education in economics or applied sciences even would not understand the equations involving time, the value of money and the ‘burning’ of un-recoverable resources that must also be considered in the analysis of the losses imposed in this so-called ‘hack’.
The biggest expense (or loss) is: The time ppl will spend ‘cleaning up’ this mess, time which cannot of course be recovered …
.
The irony is strong in this one….
Did you really just break out the fallacy card after you have spent days on ad hominem attacks on myself and others about our pea brains and inability to think outside the box?
Low-level ‘mechanics’ understanding the nuts and bolts of TCP/IP (down to layer 1 Phys) protocol have a place just like high-level strategic thinkers and planners do who understand application layers; Neither one is really a replacement for the other.
Hello, _Jim. I just received a message from the spirit of DaVinci, making a visit with many of his contemporaries. He said to look up “Renaissance man”. I said to him, “DaVinci, nobody calls people like you Renaissance men anymore; we call that a polymath now.”
It’s only through understanding the world around you through various subjects that you can ever have any wisdom to offer anybody about any subject. Absent wisdom, there are only facts. You seem to be short on those, as well, though I do applaud your willingness to share your opinions openly. Regardless, your talents probably are less suited to trolling and more suited to starting an Amway franchise. Do you have an MBA by any chance?
That’s a wonderful write up Brian. Loved yiur article and research as always. Keep the info flow….
Rescator has no brain….When against Brian. Well done brian!
Reuters is now reporting that encrypted PIN data has also been taken, ‘according to a senior payments executive familiar with the situation’.
http://www.reuters.com/article/2013/12/25/us-target-databreach-idUSBRE9BN0L220131225
Liberal use of quotes around “encrypted” and “compromised” in the article leave one to wonder what more we’ll find out as the investigation progresses…. A bad Christmas for Target, whether or not consumers have stayed away from their stores the past couple of days.
All of this news about thieves stealing encrypted PINs hardly changes the situation here. I would fully expect the thieves that had access to Target’s point of sale systems to have access to this information. But unless they are somehow also able to decrypt those PINs (unlikely), this is a non-story.
Heh. That was my reaction, too. Given the data we *already* knew they’d stolen, and where that put them in the card data flow, they pretty much had to have encrypted PINs.
What’s making my head hurt is trying to figure out how the thieves got the card data out. I’m not coming up with a scenario in which Target could be PCI compliant *and* still have an outbound hole big enough to drive these trucks full of data through.
Are you seriously being sincere when you keep saying ‘unlikely’?
I think he’s being sincere — he said “unlikely”, NOT “impossible”. I’ve always believed, largely due to WHICH coding scheme survived WWII without being cracked (the Code Talkers, *not* Enigma), that ANY mathematical encryption scheme can be broken with the right tools & knowhow; but while many hackers are smart (including these), I doubt there’s another Alan Turing in the hacker community.
Brian wouldn’t have said that if the encryption PCI requires on PINs was weak. Not only that, but it seems these hackers are too busy harvesting the low-hanging fruit (Visa, MC, Amex & Discover magstripes) to bother much with the stuff that takes more effort (REDcards, PINs, account numbers from checks, etc.) And they almost certainly don’t have the REDcard debit checking-account database; that would have required hacking into a corporate server.
Nonetheless, I have heard a few anecdotal claims of fraudulent transactions using REDcard debit, which suggests at least *some* PINs may have been compromised. (As I’ve posted here before REDcard debit *always* requires a PIN, unlike Visa/MC debit.) I suspect they’re the easy-to-guess kind (1111, 1234, etc.), but I wonder if Target’s PIN-encryption scheme for REDcard debit would permit a hacker operating at POS level to create fake transactions simply by injecting an encrypted PIN into the terminal? (It’s DEFINITELY a good thing I changed my REDcard debit PIN even before Target admitted there was ANY breach, much less a PIN breach!)
Where I live, Target has two big stores. Both were busy all last week leading up to Xmas. Parking lots were full. This news didn’t seem to scare too many people away.
Good job Brian, love your article.
Awesome work Brian, better than an intrigue and conspiracy Novel.
Thank you, Brian. Good job! And thank you all for reminding me to use the credit card for purchases and the debit card only for ATM’s. Merry Christmas and Happy New Year’s to all out there! 🙂
I had never come across, nor heard of your blog before. However, it came up quick on a search for info on this Target story. Wow. I may not understand the depths and dimension of the details you lay out, but I know enough to be able to discern that you sir, know your business.
I’ll be keenly following your updates. This is a big story, affecting a big company and a hell of a lot of people, and you’re right out in front of it.
How do you get the invites or logins to these forums? I’ve been wanting to do some research myself but can never get into the forum.
Thanks, nice article Brian.
The bottom line is we give the keys away. I have rules that I live by and the number one rule is that not everyone lives by my rules.
http://www.youtube.com/watch?v=FWgVdY3SfbI
Brian,
I am curious — I know you like to do these exposes, and you know my feelings about them being done before even any charges are made or people are convicted, but why do you not do these sorts of exposes on Americans or Britons? Could you do it legally? What happens if and when you are wrong? It is not like somebody from outside of the country can say ‘oh you have defamed me, I will sue’… What happens if one of these people one day realize they can just pretend to be somebody else by using their name in these places? And how can you ever make that up to somebody? Is there a possibility you could have already done this? Do you know what it is like to be investigated for a crime you did not commit, in a world where accusations live forever? Especially when it comes to cultures where disclosing the identities of people who are being investigated is prohibited?
I am trying not to judge because I am sure you have your reasons, and yes, if you find it morally correct you should probably pass this information over to a proper investigator, but how do you get to be the judge?
Wow, didn’t see this question coming 🙂 Especially from you, Voksalna.
If I had information that led back from a site selling cards stolen from Target by the truckload to a guy in the UK or the US, you bet I’d write about it. But I don’t have any indicators like that. Oddly enough, each time I follow the trail, it leads back to someone in Russia or the former Soviet Union.
You can derive several conclusions from this. One is that Brian Krebs doesn’t like Russians or people from CIS nations, and therefore takes every opportunity available to him to portray them as bad people. You’d be wrong about this, of course, because I happen to be very fond of the culture and many people from these regions.
Or you could simply conclude that a great many people involved in cybercrime happen to live in these regions. This, I think, is indisputable. Does that mean all technically-minded people in these regions are cybercriminals, or that there are no cybercriminals living in other countries, including the United States? Of course not (cue the predictable response about how I should be focused on the NSA instead of people involved in traditional financial crimes online).
Could someone spend five or six years building up a fake trail of clues and identities all with the purpose of framing someone? Of course. Is someone who only gradually gets pulled into a life of cybercrime going to think of this ahead of time when they’re in their early teens? Doubtful.
I don’t know who was responsible for hacking Target. We may never know. But given the attention this breach has received, I think we will at some point. And if past such crimes are any indication, the guys responsible live somewhere in E. Europe and/or Russia. Meanwhile, the guys who will get caught and brought to justice are the street schmoes in America and elsewhere who will buy and use these cards stolen in the breach at Target and other victims of cybercrime.
Another reason, I think, is that it’s far harder to capitalize on the stolen cards in foreign countries due to fraud controls. It’s easier to steal them and sell them to Americans, which means that more of this activity will be overseas and more of the actual card fraud itself is here.
Why work hard at stealing the data here, when you can have the instant gratification of buying stolen data and getting cash instead?
It’s all about the risk/reward. There’s a much higher risk if you’re in the states stealing the data than in buying the data and using it. There’s a much higher risk overseas of using stolen card data than in stealing it. Thus, synergy is achieved.
It is possible that Rescator said he was Hel simply to transfer attention to Hel, either to seek revenge or put pressure on competition. This entire article hangs on a single statement made pseudonymously by a high level identity thief. A statement that was knowingly made in a forum that would reasonably attract the attention of law enforcement.
This is really good work Krebs. Don’t stop. There is nothing wrong with analyzing and re-posting public data. However I would suggest that taking the time to mention the limitations of your data set and alternate possibilities would add value to these endeavors.
As someone who has been the target of malicious slander I feel the need to point out that for some people it is relatively easy to construct stories that damage others. Once you become familiar with the way people draw conclusions and observe which types of stories tend to work… It is really easy to cause a lot of damage.
Thank you. You have made my question/point far more elegantly. I think it is important that statements made by people, especially in public forums, are not taken at face value, not least of all when it comes to a world that relies on deception and in fact revels in it. I’m not sure Brian is understanding that while I find the exposes distasteful, my larger problem with these articles is that they can all too easily be built from the grain of a single (perhaps incorrect) statement. Ironically the more of these articles he writes, the far more likely these articles will be used to do precisely the opposite of what Brian thinks he is trying to do.
While I do not want to make a strong comparison to the Silk Road story, here, it seems relevant to make a point, and so I will ask — Brian, what if somebody who owned a forum had taken over a dormant account with “breadcrumbs” as you like to call them and used that to push the attention on to somebody else? Or for that matter the swatting story (see, I do read your articles, I don’t just post about complaints about you writing more about people from CIS ;)). You may not realise it but you hold the power of ruining somebody’s life in your hands and they do not have the “humorous” ability to just say “hello, police, you may be getting SWAT calls about me”. When it comes to “crime” the mere insinuation of something automatically makes somebody seem less credible (in some ways — maybe more credible in others). And of course that sort of thing could also be used to build up the reputation of an alter-ego with absolutely no threat to the actual actor. You could do this yourself, in fact (and I am not saying you did or would).
Just remember, while you believe you are studying people, you have given people quite a lot of opportunities to study you back; this goes for both sides.
I was never saying you should be more focused on the NSA as opposed to what is your “balliwick” (I am probably spelling this word wrong, but it is my personal English “word of the day” today ;)). I was merely stating that to ignore it or to ignore that it affects everything else is a common but woeful mistake. It is going on. It is real. And it affects maybe more than you realise or care to admit. The bigger error to me is that it ignores the fact that parallel construction has existed for a while, and has greatly expanded under these programs. It also encourages other countries to do the same. Maybe they have better or worse legal systems than the USA but it is undeniable that most of the surveillance technology used against countries like mine and other “lesser countries” citizens are made by the USA and Western Europe. It creates a different sort of arms race. And that arms race *directly* impacts cybercrime on many fronts.
There have been plenty of stories about credit card fraud and forums centering on Americans that you have not covered or done “exposes” on. I’ve been curious if this is because the informant and infiltration-oriented culture is so ingrained there that you are basically doing what you accuse CIS countries of doing — looking the other way just for a different master. Again, you do not owe me an explanation, but sometimes one can learn as much from who you do NOT “expose” as who you do. Some people may even consider that lack of information informative.
I wrote the bulk of my reply to the more subject-specific matter under Adrian’s reply. Please see that for the rest of my reply. Thank you.
When someone is actively pursuing illegal and illicit activities – especially those that harm innocent consumers in the USA – and most likely cannot be touched by local law enforcement … then I’d say Brian is rightfully justified in exposing that person, especially someone as arrogant as rescator. I’d like to see rescator pursued, caught, flayed, and eviscerated in public … perhaps with those who’ve been harmed by his activities given a chance to tug at the hooks in rescator’s intestines as he dies a very old man.
We either start taking our e-security seriously and personally, or risk the eventual collapse of our economic system brought on by miscreants in Eastern Europe, Russia, and China. (Read Mandiant’s report on APT-1.) I commend Brian Krebs for exposing this bent punk. (And I am the only one that noticed the swastika on the broken-down jeep?)
JCTeller – “(And I am the only one that noticed the swastika on the broken-down jeep?)”
… naw … check page one of comments – also notice the interpretation provided by others of the letters adjacent to the symbols ….
I am confused. If Rescator did not steal this data then technically whoever did steal this data would just go to somebody or somewhere else (and in fact has, judging from what I have seen). Should you dislike him and disagree with his acts? I think it’s safe to say the majority of people would agree. Should you treat him as the cause of, or even the bulk of, the problem? No. Because he is not, any more than your standard neighbourhood drug dealer. The problems are larger than this.
@voksalna: If English-speaking crooks were as sloppy as this guy, US law enforcement would quickly track them down without Brian’s help. These guys apparently feel they can operate relatively openly if they do so in Russian.
So ask Russian law enforcement why they aren’t tracking these guys down faster than a non-native speaker like Brian can.
voksalna could, no doubt, like several others explain the ‘mechanics’ involved to get the the authorities involved, but perhaps voksalna cannot explain from a high-level point of view *why* the authorities will not become involved. This would range from, 1) the authorities are receiving payola and do not want to stop a ‘good thing’ from their perspective, 2) the authorities would rather have the hackers be ‘chewing’ on the west’s assets and resources rather than those assets and resources closer to home, at which point the authorities would a) stop receiving payola and b) have to become un-lazy and prosecute the hackers.
Perhaps voksalna can now elaborate on these points.
End of communique.
Have you considered pharmacology as a viable solution to your problem?
End of communique.
Voksalna sounds like a Julian Assange wannabe. Basically a well-couched version of “anyone who steals from the big bad USA is automatically a hero.”
Actually, I think his sense of sarcasm and humor is pretty sharp.
Voksalna’s point is valid. A person is innocent until proven guilty. Brian’s evidence would not be sufficient to obtain a conviction in a trial.
But it would be sufficient to obtain a search warrant against Hodirevski’s home/office records, including electronic, paper and financial records, and including records of payment for the domain helkern.net.ua to see who has been paying for it since his name was removed from the whois in early 2011 and whether there was any prior record that the domain was sold or stolen.
If it was stolen, using root@helkern.net.ua as a contact email for illicit activity would be very stupid, because the rightful owner might regain his domain at any time.
It seems too obvious a connection for anyone to have been so careless, but if he is/was completely certain that he was not going to face legal consequences for stealing from people in the West, he may not have thought about it at the time.
AlphaCentauri ” Voksalna’s point is valid. A person is innocent until proven guilty. ”
Not to state anything about the naivety of the above statement, but, under what legal systems? For instance, in the United States legal system, can you state which CFR (Code of Federal Regulations) or that portion of the USC (US Code) that applies the above standard? What about other countries, like France, where such offenses would be governed by Code pénal, or Criminal Code?
I would not presume to know what ‘laws’ might cover this in Russia or the Ukraine.
Even setting the above aside, it is still the job of a persecutor to put together a case with all the relevant evidence that can be secured. The prosecutor in his duties makes no assumptions as to the innocence of the accused or the one charged with a crime.
http://en.wikipedia.org/wiki/Coffin_v._United_States
http://en.wikipedia.org/wiki/Presumption_of_innocence#The_fundamental_right
http://www.en.pravo.org.ua/files/Criminal%20justice/CPC.pdf (see page 10)
Of course, the reality may be different, especially in Ukraine under the current administration, but I was discussing fundamental rights.
He does do some things like this about Americans.
http://krebsonsecurity.com/2013/03/the-obscurest-epoch-is-today/
http://krebsonsecurity.com/2013/05/ddos-services-advertise-openly-take-paypal/
Amazing work ! I have been following your blog for a while now and I am always delighted by the quality and accuracy of your articles.
Thank you very much !
Hi Brian. As a fellow CISSP and ISSA member it’s a pleasure following your posts. Met you in person at a previous conference event in L.A. Enjoy the reads and learning a bit about your research progression. It takes time, persistence, patience and a little out of the box thinking with access and knowledge of research tools to work the “darkside” of the net. I too believe the Target breach will become more public than most. Definitely a breach to learn by and will hopefully move private firms to re-invent and invest into system security programs and technologies.
Thank you for sticking with it !
Wow awesome to see this story getting picked up elsewhere!!
NYT Article:
http://bits.blogs.nytimes.com/2013/12/24/who-is-selling-targets-data/?_r=0
Brian, you are one brave, dedicated soul. Thank you for all you do. Thank you again, and again.
To everyone asking about how data came out of targets network:
I worked for target up until 2013. Openly available computers (to employees) inside TSC (target/team service center) were pitifully open and often infected, with nothing more than Symantec endpoint and basic firewall protection, generally aimed at making sure hourly employees didn’t browse porn at work. The internal transaction records system, InsidePOS is installed on every computer by default. Theoretically the pos records required an employee ID/pw combo with basic managerial rights assigned to it before revealing any (somewhat redacted) transaction information; which is searchable by time, date, register #, card prefix etc.
I cannot even begin to count how many times I “coached” my fellow and often superior ranked co-workers about security best practices such as logging out prior to leaving the shared computers. Including the store “executive team lead” human resources, who seemed overly fond of leaving extremely sensitive documents open to public via and access while the “executive” assumed no one would touch the open computer where hourly employees check their pay and submit time off requests.
With even a hobbyists experience in ITSec and general computing best practice, it was trivial to secure open connections to and from the outside world. Despite being forbid I often times sent work home to be finished after usb devices were “banned”, even a basic ssh could defeat local domain fences. Not to mention practically any web based email, along with hundreds of other exchange protocols.
Based on my handful of years within local store and regional/district networks, the sheer lack of basic security awareness and physical access to intranet machines would make it trivial to get data outside store networks. A reasonably written threat combined with insider access to store networks (and appallingly unprotected winXP network shares) would easily be able to chain from register point of sale–> compromised XP machine–> attacker.
Hell the company used to have open network shares containing dumps of “guest transactions” ready made to be press to plastic. Also every team member device in the store relied on unbroadcasted Wi-Fi networks secured often times by wep or simple “target+ store number+zipcode” passwords. Adding to this the semi-recently released guest in store Wi-Fi for shopping, a scenario involving inside access seems likely.
Granted all my experience is roughly a year old, but considering all the ipcams, remote access, shared drives and user negligence there are countless holes in targets networks just waiting for a that to fit them
@tybalt –
If HALF of what you say is true, Target has an even more enormous PR disaster on its hands than just being hacked. Seems like they were actually asking for it…
Unfortunately, that sort of lax security is more the norm than the exception. The employees who use the computers are way over their heads in terms of understanding the risks. They only understand the inconveniences of good security.
And if you’re the person who points out the problems, you just become the person who gets blamed when things don’t work — because you logged off the computer that has been logged into the same username for the past six months and no one else remembers their usernames, let alone their passwords.
Target is the breach you’ve heard about. But there’s no way that stolen credit cards and identities would be for sale so cheaply on carding forums if the information weren’t pouring out of US businesses like water from a firehose.
Okay, I can see it now – in my day – the headlines said, “our kids need to learn the 3 Rs! – so now they need to learn the 3D’s!! The three dimensional shift from sitting at home wiping our behinds, to being totally world aware and sniffing packets as a side recreational habit! HA!
We are doomed!
Isn’t this the same kind of analysis that amateur CSIs on Reddit and other web sites frequently get in trouble for doing? Some photo on some site looks kind of similar to a photo on some other site, some user name is kind of similar, and so on, therefore this guy is guilty? Sure, the evidence looks promising, but I disagree with the decision to post so much detail about the alleged perpetrator, including name, photos, and contact info on a public web site.
Mr. Krebs, if you truly want to help, send the info to the proper authorities instead of causing a huge headache to someone who may not even be involved. If this person is really involved and the case is such a slam dunk, his name will be made public later anyway when he is arrested and convicted. This kind of article empowers amateur CSIs everywhere to continue with their so-called investigations that frequently end up targeting the wrong person.
Based on the user postings on the carder forums since this story went up, I’d say he nailed it.
Should ask Richard Jewell. Or those other people who got accused during the whole “crowdsource the Boston Marathon” thing, or the Amerithrax investigation that ruined more than one scientist’s life before being acquitted of doubt (or committing suicide, which surely was a happy case closed instead of proof). I could easily name off another dozen before I would even have to start looking on Google. Why not ask them how they feel about it, since hey it just seemed correct.
It was the lazy and un-principled news media who pointed to Richard Jewell. Not bloggers. His physical-link to the event, discovering the backpack filled with pipe bombs in the park did help ‘start’ the theory he was the bomber, however. The news media has also pointed fingers at a number of others for crimes, as well as regularly assigning certain ‘despised’ (in their view) political views to groups or persons who commit violent acts. It is a partly a matter of making headlines and also the deadlines to publish (the five or six O’clock news or setting up the printers for the afternoon ‘print’ edition of the NY Times for instance).
I agree with much of what you said, here (see, I am not disagreeing with you just to disagree — you realise this I hope?), but I believe you are looking at everything as though each incident occurs within its own box, and it does not. This is especially true of now. Basically we are in a time of ‘Me-First’ and I don’t mean simply narcissism. Innumerable ‘First comment!’ posts are everywhere. Now it is more like a game of ‘Telephone’ — one person starts a rumour, everybody else twists the rumour, and everybody wants to be the first person to not just know a story, but to be the one who discovered it — not just the newspapers. Deadlines now are irrelevant — the only deadline that matters now for most people is beating out everybody else so that they can feel special.
My problem with this is, and continues to be, the more people race to be first, the more people don’t give a f*ck about who they destroy along the way, or even what they stand for (and I’m not talking about terrorists here, by anybody’s definition). The only way I can make this point is to say ‘Imagine you were in the wrong place at the wrong time and people were doing this to you’. Is this applicable here? It is not my place to judge or say. But it’s not yours or Brian’s either. If these things had been written about after a (fair) court trial/etc, then it would seem less offensive to me.
I will ask again, what is the point of these stories? Is it shaming? Page hits? Being ‘first’ with a story before someone else ruins the time put into investigating it and ‘scooping’ it?
Back to Richard Jewell: What good did vilifying him in the press do? Would it have even done any good if he HAD been guilty? Isn’t there plenty of time to shame someone, if really you MUST shame somebody (note, I am not for shaming anybody, ever — if you are shaming people you need to understand that it tends to drive the wedge deeper, which is at best counterproductive — in which case, your definition of justice has nothing to do with rehabilitation and re-entry and more with destroying a life), after they’ve actually been found guilty in a court of law?
My goal in these comments is rarely to take a side — and almost always with trying to figure out whether other people even know if and why they are taking the sides that they are taking. I’ve never judged you even while we have disagreed; I have dismissed you solely when you have dismissed me and other people who are also trying to engage in an actual dialogue via ad hominem or avoidance tactics… but you’ve judged me, have you not? I have generally come here because people need to think about their opinions and why they come to conclusions; if they can explain them cogently and logically and rationally, then, even if I disagree, I have almost always accepted it instead of trying to hoist my own worldview upon them.
I am for information and understanding; I really don’t care as much about ‘being right’. In that light, I’d gladly email with you, just like I would and have emailed with other people that I have both agreed and disagreed with (albeit I am a bit behind in my emails right now). If you’d like to communicate in this way, let me know. If not I will consider this a subject we probably will not agree upon and wish you a good new year.
Well stated.
My only comment is this: Here in the US, reentry is NOT the goal for criminals, no matter how much some may say it is. Rather, here, generally the mentality is geared towards punishment, retribution, proving a point, and “an eye for an eye.”
Our system is in NO way built to rehabilitate, and is actually built to make it hard to get OUT of the system (not just out of jail / prison), keeping people in the system and making it hard to resume a normal life, for even those that have made mistakes or are trying to stay out of criminal ways.
I cant remember the study, but somewhere in Europe they have gone to prisons that are work camps, with almost vacation like facilities, work training, and a very non-prison atmosphere, and I believe the re-offender rate there was something like only 10%….compare that to the US, where almost universally the re-offender rate is between 70-80%
Good point CJD – when you think about it, that prison model you mention needs to be adopted by the US for at least 1st time offenders. I feel after that, the old way of doing things is just as well; but then I also feel jailing non-violent offenders forever is costing the taxpayer way too much, and some kind of prison reform needs to happen. In fact they need something additional that prisoners who are stuck in the system can voluntarily participate in, that uses mind control techniques. This was attempted in the late ’50s with the Concord Prison Experiment and was actually recognized by many in the science community as a true double-blind study conducted by Timothy Leary using psilocybin as the drug of choice because of its safety. Despite have record low recidivism rates, ironically the news media destroyed the credibility of the study by slanted broadcasting, and skewed “facts”, and Leary himself damaged the concept further with his later LSD fiasco. This I fear has set back prison reform here for 100 years!
I wished there was a political action group to join under this subject. Because it is one of my biggest peccadilloes with our system of governance in the US. Also, let’s face it – we don’t handle penology in any way – shape – or form like a Christian would. Then we have the audacity to claim we are a nation of Christians!
Using pharmacology is a slippery slope (and not just from a “Clockword Orange” perspective). There is actually a sizeable amount of research into use of MDMA and other phenylethamines with criminals as well (not just the harder psychedelics like LSD/etc) as a method of “treating” empathy problems. Actual experiential encounters in proper circumstances may be good but anything forced or coerced or favoured won’t end well. Stacking the deck and letting people know this will let people out will only lead to a mockery of anything real or positive. Anything more and you are suggesting inhumane emotional castration. I believe 50 or so years ago they tried this. They called it “prefrontal lobotomies”. Doing this chemically is done in all countries already via psychotropics. It has not given anybody more respect or freedom; on the contrary it has given them more negative labels. Again there are no easy solutions.
The part of the world CJD is referring to is most likely Sweden or Norway or possibly Iceland. Of all parts of the world, they seem to have the lowest recidivism rates — and the best treatment of criminals. But that does not mean it would work everywhere. Much of what happens in a prison derives from the society outside of the prison that led a person to that prison to begin with. I think most criminals would probably be far better served with no record and a period of monitoring like your country does with ankle bracelets compared to being in prisons surrounded by other prisoners.
Which brings me back to human nature: We are humans and we attempt to adjust to our surroundings. Over a long enough period we do or we perish (physically or emotionally) because it is too psychologically stressful/difficult/demanding to be part of any out-group for any significant period of time (read Goffman). Separating people from everybody but other criminals while constantly calling them prisoners and treating them like subhuman garbage will only recreate real-life versions of the Stanford Prison Experiment — and it has, repeatedly. Look no further than the pictures from Guantanamo for extreme versions of this, but smaller versions (and occasionally large versions) of it occur in almost every prison around the world.
With regards to Christianity, I think most people believe “turn the other cheek” is something to be commanded of others, not something to apply to oneself. This is part of the problem, and it all goes back, again, to self-image. These sorts of idiosyncracies are only problems when they are applied against you or somebody you care about; most people don’t even realise they are doing it otherwise. We as humans are prejudiced to confuse our opinions with facts. Hence why I always ask people to explain why they are saying things, not restate what they’re saying. Most people cannot.
Clockwork Orange and phenethylamines. Dumb mistypings.
The double-blind study was quite successful, but then that was because it was a double-blind study, the criminals knew not what the program was about, I think they just went along out of boredom. 1st hand knowledge of the plan would tend to ruin it, as you suggest; but doing nothing is not an option either, I feel. Civil rights activists would never permit it unless it was voluntary, but being tipped off to the plan undermines it, unless it is very carefully crafted, and managed. I feel penology should be a serious science that should be advanced if we are going to reduce prison populations successfully.
@JCitizen: I suspect it is very difficult if not impossible to do a real ‘double-blind’ study in any penological setting in part due to the fact that most scientists don’t also pose studies that might make criminals “worse”. Those at an average or above average intelligence, or at all canny, would be able to gauge what the scientist(s) want and respond accordingly (or not, depending on their desires). As you said, it probably relieves boredom, but relieving boredom can also be a reason to not just go along with a study but deliberately manipulate the people doing the study.
@JCitizen: Note if one treats criminality as a psychological issue, it is quite possible that a big part of the cure would be to follow a milleu-based program. This indeed is what the Nordic/etc countries adopt successfully, and what your ‘halfway houses’ fail magnificently at. But I think the larger problem is the label and the fact that (a) criminals’ names are listed in the news/etc (sometimes in spectacular fashion) there and (b) you require people to disclose they had a felony record regardless of how far back it goes. I’ve stated before I believe that if a former felon does time and does not recidivise within a certain time period, the record should be sealed. This obviously is pointless if a name is all over the news and searchable on the web, however. The more media takes over the less possible any of these adaptation methods will be because the problem is not only with the ‘criminals’ — it is with everybody else as well for only seeing them as ‘criminals’.
Very true about felony records being searchable on the web. A friend of mine is trying to get an old felony conviction expunged and was surprised to find that her actual record doesn’t even include all the crap that comes up when employers do background searches. She was charged with all kinds of crazy-ass stuff she didn’t do, as is typical to get people to plead guilty to whatever they really did do and avoid expensive jury trials, but the crazy-ass stuff has acquired a life of its own through non-government background-check services. And her case probably never got any type of coverage in the press; it’s just these “private investigator” services that storehouse pretrial information.
Those searchable records are that way because companies but court records in bulk to sell for background checks. I went through this with my father and his lawyer said basically don’t plead to something on a differed basis because even though it will come off your court record it will never go away. Those companies are NOT liable for accuracy. Most say in their user agreement that its the buyer / employers responsibility to verify the accuracy and that they should obtain at least one other background check from another source, and verify all data with the local jurisdictions. But we know they don’t. You can send a copy of your court paperwork to these companies requesting they update it, but that’s your responsibility and there are literally hundrreds of those companies to contact. It’s an unfortunate mess, especially if the data is wrong and something you weren’t charged with, or if you just made one mistake and you’re not a career criminal. Sadly, there is little you can do. Since they state it may not be accurate and that its the buyers responsibility to verify the accuracy, you have no real recourse.
Good discussion! My thanks to everyone for responding.
Yeah, getting corrections is a lost cause. I am associated with a company that needed to get a background check from Lexis Nexus on a child care employee. We were *the customer,* but they couldn’t even get our own information right. They must have transposed the digits in the zip code, because they insisted we were 2000 miles away from where we are really located and ignored our attempts to correct the information. And they’re one of the largest companies. The smaller ones have even less reason to try to maintain a reputation for accuracy.
In the meanwhile, Ars Technica just did an article on an elected law enforcement officer planting a keylogger on a federal court computer that he would have had to break into to place to keylog his wife and just so happened to also keylog all of the federal court business. His punishment was a year of probation and a $1000 fine, and the judge saying that him losing his job/career was bad enough. Correct me if I am wrong here, but should a law enforcement officer not be MORE culpable after committing a crime, just like a priest should be more culpable for molesting a child? This is betraying the public trust by someone who has SWORN to betray the public trust. I am pretty sure that nobody Brian writes about (with maybe a certain ex-carder I won’t name from Ukraine now in political office, and that was BEFORE he took office) has actually made any promises to anybody not to break a law other than what is commonly referred to as a social contract.
THIS is why I do not like or trust the American legal system… and why I have repeatedly requested more balanced reporting on things like spying. It is bad, sure, what a massive government agency can do, but the bigger problem is things like your small towns getting tanks for ‘Homeland Security’ because of ‘terrorism’ (read: stimulus and money for defense contractors) and the every day seeming mundane availability of abuseable resources that should not exist to begin with. Find me a technology that lets people snoop and I will find you millions of people who could find a way to circumvent any control — and I don’t mean hackers. There is a primal thrill to ‘snooping’ that almost everybody has experienced at least once in their lives (or wanted to). The NSA may be overreaching but it seems to be overshadowing the fact that exactly the same sort of things are going on on a different scale in *localities* as well. And you can bet they will not be nearly as airgapped — which is also where people like Brian need to come in — and why speaking up for legal parity or placing GREATER blame on ‘official abuse’ is so important. Clapper lied to Congress. 40 years ago this would have probably left your country in a violent outburst. Now he didn’t even lose his job. It is the same thing as the Sheriff story or any of these other stories: We are not holding people culpable to the degree we should.
Conversely we are demonising other people far more than we should. If you were living with several other people on the equivalent of 200 USD a month with your 80-year-old grandmother selling 10 pints of berries on a cold spring day outside of a Kiev metro station on her feet, you may see crime as the only way out as well. It isn’t always about buying a large-screen television; when it is about greed, maybe the punishments should be higher — but not as high as when an actual breach of the public trust occurs.
“by someone who has SWORN to betray the public trust” should obviously read “SWORN to uphold the public trust” or at least sworn not to betray it. 🙁
I agree that it’s outrageous that public officials in the US get a different system of justice, especially when those same officials are the ones being “tough on crime” and incarcerating other people despite little evidence of those policies benefiting society.
As far as the Kiev resident trying to help out his grandmother the street vendor — yes, I can understand why that individual might feel he has no better options. But that solution becomes the problem when it becomes so acceptable that Ukraine receives a reputation for being a haven for scammers.
One of the most important resources Ukraine has is the intelligence and educational level of its people. But what are they using that for? Where are the exports from Ukrainian pharmaceuticals and medical devices? Or from their software and hardware manufacturers? Or their fashion designers? They need some better exports other than zero-days.
That brilliant guy would be doing his grandmother a lot more good if he were able to start a legitimate company, and he’d be helping a lot of other grandmothers by hiring employees. But it’s hard to bring in legitimate money from outside the country if everyone in the West has their spam filters and websites set to block all traffic from Ukraine.
Brian – How about a follow-up post on a likely influx of fake ‘Your credit card has expired’ or ‘Your card is no longer valid’ phishing emails?
Nice work as always.
rg
I haven’t read many comments in here, but has this side been addressed?
http://www.csoonline.com/article/744905/inside-knowledge-likely-in-target-breach-experts-say?source=rss_news
It has been discussed to some degree. I think most are of the opinion that *if* there was inside cooperation that it likely came via one of their outsourced partnerships in India. I have tried to do some additional research on their outsource efforts, with a lot of conflicting information – the most solid intel I can find is that they do use at least 2 indian IT services firms to help them with projects and possibly store support.
I believe, the indian connection makes the most sense, because finding an overworked support person in india, with maybe a gambling problem, sick relative, or just a guy who moved away from his wife and children to make a better life, would be ripe for someone like an organized crime element to corrupt with the tempting of $25-50K. That said, I have ZERO evidence to back that up, it just seems one of the more likely scenarios. BUT, it just as easily could have 100 other scenarios.
As someone that works in retail doing IT Security, I dont agree that they needed some intricate insider knowledge. First, a good hacker, and this took multiple good ones, doesnt need insider knowledge. Once they infiltrate the network, one of the most common things to go after is less guarded information documenting the network, so that they can stage the next part of the attack on the victim company. And even if they did do that, there are only about 4-5 models in all of US retail for how CC transactions are processed, and they arent difficult and complex structures.
Unfortunately, I dont know that we will ever know the full story, I dont think Target is going to release that, and the news cycle will have rotated and moved on from target…..
An insider threat doesn’t have to be a participant, but their access and privs need to be. It could have been someone who uses the same creds on every site they visit. Thus, once the crooks seen a username and pw that was employed at Target, what a ripe opportunity. All a crook has to do is a little research, on any of the social websites and they have a logon and pw.
I hope it wasn’t a disgruntled employee. Those are the worst. There was a lot of data in the spreadsheets and I am surprised to see that hardly any fields required special access…. That means two things – either an elevated account was used, or Target simply did not encrypt, password protect or limit the exposure of CC data at all.
Like I said in the original Target post Brian did – paint a Target on your back and see how long it takes before someone takes their shot at you and hits the mark.
Target seems to be focused on in-store security pretty well. Now I bet they wish they had done the same in reference to the web front.
Excellent work, Brian, and I applaud your ethics.
Another great story, Brian.
Through the many stories that you’ve run, the subject of user identity seems to be a tightrope act for many of these hackers.
Whether it be using the same handle across various sites, to the same profile picture, or email address to register… they need these connections to vet themselves when they join a new community, but people like yourself also leverage these identities to trace them back to the actual individual.
It’s an interesting balancing act.