Nationwide beauty products chain Sally Beauty appears to be the latest victim of a breach targeting their payment systems in stores, according to both sources in the banking industry and new raw data from underground cybercrime shops that traffic in stolen credit and debit cards.
On March 2, a fresh batch of 282,000 stolen credit and debit cards went on sale in a popular underground crime store. Three different banks contacted by KrebsOnSecurity made targeted purchases from this store, buying back cards they had previously issued to customers.
The card shop Rescator advertising a new batch of cards. 15 cards purchased by banks from this batch all were found to have been recently used at Sally Beauty stores.
The banks each then sought to determine whether all of the cards they bought had been used at the same merchant over the same time period. This test, known as “common point of purchase” or CPP, is the core means by which financial institutions determine the source of a card breach.
Each bank independently reported that all of the cards (15 in total) had been used within the last ten days at Sally Beauty locations across the United States. Denton, Texas-based Sally Beauty maintains some 2,600 stores, and the company has stores in every U.S. state.
Asked about the banks’ findings, Sally Beauty spokeswoman Karen Fugate said the company recently detected an intrusion into its network, but that neither the company’s information technology experts nor an outside forensics firm could find evidence that customer card data had been stolen from the company’s systems.
Fugate said Sally Beauty uses an intrusion detection product called Tripwire, and that a couple of weeks ago — around Feb. 24 — Tripwire detected activity. Unlike other products that try to detect intrusions based on odd or anomalous network traffic, Tripwire fires off alerts if it detects that certain key system files have been modified.
In response to the Tripwire alert, Fugate said, the company’s information technology department “shut down all external communications” and began an investigation. That included bringing in Verizon Enterprise Solutions, a company often hired to help businesses respond to cyber intrusions.
“Since [Verizon’s] involvement, which has included a deconstruction of the methods used, an examination of network traffic, all our logs and all potentially accessed servers, we found no evidence that any data got out of our stores,” Fugate said. “But our investigation continues, of course with their assistance.”
In any case, the stolen cards mapping back to Sally Beauty appear to have been pilfered quite recently, roughly matching the intrusion timeline noted by Sally Beauty: All of the banks reported fraud occurring on cards shortly after they were used at Sally Beauty, in the final week of February and early March.
The advertisement produced by the criminals who are selling these cards also holds some clues about the timing of the breach. Stolen cards fetch quite high prices when they are first put on the market, but those prices tend to fall as a greater percentage of the batch come back as declined or canceled by the issuing banks. Thus, the “valid rate” advertised by the fraudsters selling these cards acts as an indicator of the recency of the breach, because as more banks begin noticing fraud associated with a particular merchant, many will begin proactively canceling any cards used at the suspected breached merchant.
In this batch of cards apparently associated with the Sally Beauty breach, for example, the thieves are advertising the cards as “98 percent valid,” meaning that if a buyer were to purchase 100 cards from the store, he could expect that all but two would still be valid.
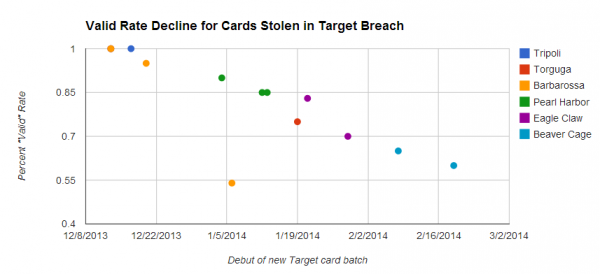
Cards stolen in the Target breach have become much cheaper as more of them come back declined or cancelled by issuing banks.
In the weeks prior to December 18 — the day that the world learned Target had been breached in a similar card compromise — the thieves running this very same card shop had been advertising several huge batches of cards at 100 percent valid. In the days following Target’s admission that malicious software planted by cyberthieves at its store cash registers had siphoned 40 million credit and debit card numbers, the “valid rates” advertised for those stolen cards began falling precipitously (along with the prices of the stolen cards themselves).
The items for sale are not cards, per se, but instead data copied from the magnetic strip on the backs of credit cards. Armed with this information, thieves can simply re-encode the data onto new plastic and then use the counterfeit cards to buy high-priced items at big box stores, goods that can be quickly resold for cash (think iPads and gift cards, for example).
Interestingly, this batch of stolen card data was put up for sale three days ago by an archipelago of fraud shops that is closely affiliated with the Target breach. In my previous sleuthing, I reported that a miscreant using the nickname Rescator (and an online card shop by the same name) was among the first — if not the first — to openly sell cards stolen in the Target breach. Further tying the Target breach to Rescator, forensic investigators also found the text string “Rescator” buried in the guts of the malware that was found on Target’s systems. According to additional reporting by this author, Rescator may be affiliated with an individual in Odessa, Ukraine.




Have they ever considered adding “Honeypot” transactions? Essentially a false transaction that is entered into the system – perhaps once a month, using a unique card number that is never used for anything else (and using different card numbers each month).
If those numbers ever turn up on the black market, it is a virtual guarantee that one would know where the leak occurred.
I’ve been thinking about doing the same thing. I think a prepaid debit card like maybe an American Express Serve card would do the job well.
Well what are the chances that it would be the card you would buy hmm? Or how long would it take for someone to use it.
I’ve always liked Tripwire. I don’t know what features are available in the current commercial Enterprise version, but way back when it had a free version it was at core a simple file integrity system: It would do checksums of files in folders you’d specify and compare that against a baseline you establish when you first build your server’s filesystem. As long as the reference checksums were kept in a trustworthy place, it was a nicely powerful way to track system modifications.
I imagine the Enterprise version has become far more powerful in what it does since the days of the freebie version. File integrity checking is now probably just a small part of what it does.
Anyway, even back then it was a nice tool. I’d love to see what the Enterprise version does nowadays.
Tripwire – as nice of a product as it is – only detects changes to a soft-processor’s hard disk or its active OS environment. My last involvement with the product (v8.3) was fairly recently and at the time I didn’t believe it to be capable of inspecting running memory or other off-the-beaten-path file-hiding areas.
Whomever modified the file system of the endpoint that triggered the alert got sloppy. A good TW-Admin will readily understand why.
True, Tripwire would only be one component of one layer of security. It definitely couldn’t stand alone, for the reasons you mentioned as well as others.
But, for what it does, it does well. Or at least the older versions I worked with did.
Tripwire has multiple products, the name is commonly affiliated with the open source product that they started with, but now includes several products including FIM, SIEM, and vulnerability management. I don’t work for them, but a quick visit to their website reflects they are not a single product. In the statement they didn’t say what products they have, but I would guess it isn’t just the open source tool.
Brian , I wish you would check on AAA roadside protection being hacked or Scotts Lawn service. My wife got a new Discover card six months ago and it has has never left our house . She has only used it to pay her annual AAA dues online and Scotts lawn service once online. I use WPA2 security and I hope that hasn’t been hacked yet ! Thanks ! Great blog! You are doing an awesome job !!
Yet another Texas-based company. Sure, it’s a BIG state, but it really seems like Texas has had more than it’s fair share of breaches. Any ideas on why that might be? Or is my tally just a wee-bit skewed?
Most likely, the reason a number of businesses are located in Texas, is that more businesses have been moving to Texas than any other state. A few reasons come to mind, but this isn’t a complete list.
No personal or corporate income tax; low cost of living; cheaper real estate; low unemployment; weak unions; good schools; friendly people; respect for the 2nd Amendment; and VERY LITTLE SNOW.
But I could be wrong.
http://tinyurl.com/nvuqnbc – The Texas Miracle that isn’t.
That article certainly was good at cherry picking stats. And long winded. I found Texans like to cut to the chase and speak their mind in much fewer words.
The writer summarized that New York and Vermont were doing better than Texas in per capita income. Well, I could argue that Texas is #1 is GDP. And the writer even had to admit that Texas has also outperformed the rest of the country in its growth of high-paying jobs.
But, like most Texans, I won’t. New York and Vermont are awesome states and we just wish you, the writer and all your friends to be happy there. (P.S. As an added incentive, U-haul rates are 40% less moving into NY than one-way hauls into Texas!)
Good luck, my friend.
Nope – you’re not wrong at all. 🙂 Dallas, Austin and Houston are in a Feb 2014 report from Forbes.com as three of the top ten fastest growing cities in the US. (http://www.forbes.com/sites/erincarlyle/2014/02/14/americas-20-fastest-growing-cities/)
Don’t forget that Texas happens to be in the middle of the country, thus making it convenient to open warehouses and distribution centers…….Cheers!
I recently moved to Texas. What I found most extraordinary was that the Texas Constitution only allows their legislature to meet for 90 days, every other year. That seems to really keep those politicians focus on high priority items since time is so short. Back in Michigan, I think our politicians sat around and dreamed up new laws and regulations because they ran out of things to do. 🙁
“That seems to really keep those politicians focus on high priority items since time is so short.”
No, it doesn’t — the usual practice in every Legislative session for as long as I can recall (and I’m a native Texan of 60+) is more typically that the really critical, must-pass legislation (budget, appropriations, etc.) doesn’t get done until the last few weeks or days (or minutes, even), while the early weeks (and months) is when the “priorities” of the Speaker and Lt. Governor are brought forth, depending upon how compliant or amenable the key committee chairperson in each chamber might be with those “priorities”. I use the quotation marks because of the highly politicized nature of that term, particularly in the past several decades.
That is an interesting point, though. In most states (including California where I live) the politicians have 24 months to screw things up compared to only 3 months in Texas.
But everything’s BIGGER in Texas, so in 3 months they can & do make BIG messes, then the electorate gets to deal with all the fall-out for another two years only to watch yet another Legislative Session fly by with no clean-up of fall-out. The legacy of the State Legislators drastically reducing funding for public education prior to the 2011-2012 school year is STILL an ongoing toxic wasteland which required suing the State just to get a small part of that funding back. Stay tuned as the Texas Tea Party attempts to dominate all in the upcoming elections and do so while blindfolded–having their heads up their a$$e$!
Most of us Texans would still prefer that instead of meeting for 90 days every two years, ‘the Lege’ would meet for two days every 90 years.
@BC…
Being in the retail IT field, I know that there are a LOT of national retailers that are based in Texas.
I don’t know why that is… whether there are business-friendly laws that make retailers want to locate there, but I think the concentration of breaches may simply be related to the concentration or retailers based in Texas.
It’s a combination of very business-friendly taxation parameters and aggressive tort-reform laws passed during the Bush (gubernatorial) administration which provide significant legal hurdles to initiation or prosecution of consumer-based litigation as well as establishing relatively low or modest maximum award limits.
Tripwire is a great tool and extremely good at what it does, but it isn’t an intrusion detection product anymore than IPtables is a firewall. If these companies want to be protected, they have to have the right tools used by the right people.
Well, technically Tripwire is change detection software, right? If set up appropriately it could function as intrusion detection. I’m glad Sally was at least using Tripwire. If Target were using Tripwire and had noticed the new binaries deposited on their systems, surely they would have been alerted more quickly. Do we know what eventually clued them in? Wasn’t it the transfer of data to outside of their company networks?
@Serena:
Tripwire is not (let me say this again: NOT) an intrusion detection mechanism.
“It only knows what it knows…and no more”.
Meaning: Critical system files or system configuration components can be monitored and verified with Tripwire’s out-of-the-box platform inspection rulesets. One would not want to monitor the entire filesystem of a Windows 2008 Server installation owing to the sheer volume of data present, and the vendor-supplied platform rules take this into account.
Aggregate the take from 500 separate machines and you have a huge amount of data to warehouse and filter. Now activate real-time file change monitoring on all those systems and watch their performance slow way down: Unacceptable to the business whose enterprise is supported by those servers. Time is money…
An application is a different story: Smaller in size that an OS deployment, ALL of its files may usually be included in monitoring – and most application fileset rules can be scoped in a manner that allows real-time checks.
Thus, Tripwire (or similar FIM products) work best in a constrained approach: Which system or application files, keys, environment variables and configuration data should an institution monitor, and which of those – if changed – would constitute a genuine warning?
As useful as they are, FIM solutions are not a security panacea: You absolutely must detect, inspect and block suspect traffic before it gets its payload onto a system.
A good attacker knows that one of the first things to do after obtaining a system-level shell on a Windows server is
net stop teagent
net stop tesvc
Then Bob’s your uncle, unless the TE Admin is paying darn close attention to his or her Console and sees an Agent go offline.
Bad actors as well as good actors know the limitations of each of these kinds of products. If you have no active IDS in your network, fooling Tripwire with an in-memory-process attack is doable – if not trivial. This may be the reason that Sally found no evidence of data theft: The malware went away with a reboot.
I think you are confusing the open source Tripwire product with the Tripwire Enterprise and logging product, which is quite a bit more robust than the Linux only FIM product most people know Tripwire for.
[The website is easy to find. I am expert witness on insurance matters with a growing interest in cyber insurance problems. I have “published” some boring blogs on this topic.]
*******************************************************
I have found no real literature about how the hacked-invasions of businesses, especially retailers, where stealing “private” data regarding individuals, make any money with that data for the cyber thieves.
(Insurance industry so-called reports say nothing about this. They only thing they say is how much dealing with a theft equals various amounts to deal with a certain incident. Those numbers are absurd when there is an incident involving, say a million people. I speculate that the insurance publications are really a concealed ad.)
So what are the moneys lost by actual individuals resulting from a “big” raid?
Obviously, there are black markets for data, but how the the purchasers in those markets really make money? (How much money is there in extortion, e.g., like the “Target Incident,” or better yet, the Nieman-Marcus attack?
Is a way to make money to collect ransoms from the institutional victims?
Did you even read Brian’s article? If you did you must have missed this paragraph:
“The items for sale are not cards, per se, but instead data copied from the magnetic strip on the backs of credit cards. Armed with this information, thieves can simply re-encode the data onto new plastic and then use the counterfeit cards to buy high-priced items at big box stores, goods that can be quickly resold for cash (think iPads and gift cards, for example).”
The insurance industry numbers you reference are the cost of measures to reassure consumers and restore lost confidence, like providing credit monitoring to assist them in finding and responding to the kind of fraud Brian described.
The costs of those frauds are actually usually borne by the merchants who sold the goods to the fraudulent cards, as a result of a chargeback mechanism that lets the issuing banks reverse the transaction and leave the accepting merchant holding the bag. I’m not sure how those costs are amortized, whether there is insurance or if they are just eaten by the retailer. No matter how that is, they’re ultimately passed along to the public at large through higher overhead.
Does that help?
Actually, the bank is usually holding the bag. There are no chargeback rights if the merchant swiped a counterfeit card in good faith.
Banks also are left with the cost of reissuing all the cards, as well as the manpower to reissue and deal with customer calls and concerns.
It’s all paper scissors rock, or musical chairs, hot potato, whatever you want to call it.
Ultimately the bank charges higher fees, reduces services, closes branches, etc… so ultimately the customer pays. And even the cost of law enforcement doesn’t come for free.. eventually it rambles around to higher inflation, higher taxes, lower services etc.
The idea that economic friction is borne on the banks, or the merchant depends on when you stop the music or what round of paper scissors rock one cares to measure.
A few will ‘win’. They collect the profit from the gambling and when the music stops they “resign”. But keep the profits from their mistakes (for example, the Target CIO resigning today). That’s the moral hazard of gambling with grandma’s data. The profit is siphoned off, the losses go to grandma and society as a whole.
The last one ‘out’ of the game is usually grandma (society as a whole) as she pays more for her annual CC fee, free checking dwindles, pays more for a product, has fewer purchasing choices, a smaller pension, etc.
I suppose the lawyers arguing about who pays also ‘win’. They collect from both all parties, so they always ‘win’. 🙂
The bottom line is that economic friction isn’t allocated to a single entity frozen in time. We all end up paying.
Sally go round the roses,
Sally go round Rescator’s roses,
…
That was a very good explanation of the economic and behavioral connections for black market credit cards.
We should continue to look at these as excellent indicators and their limiations.
One difficulty with applying economics, or game theory to these types of situations is that not all the motives are economic or to optimize; folks are not necessarily playing to ‘win’ (or even for any gain at all).
Secondly, once an indicator is known, it can be manipulated. So the various participants may give off false signals through these indicators, by intent or self-deception. For example, the market value is partly determined by how much/quickly the banks are willing to pay to buy the cards back. Market price indicators are not a very good substitute for valuation (though often the single best indicator we have).
Then there is the impact of different time periods. A credit card number that has been kept quiet for years may gain in value at some point much like an old car that’s a junker becomes an antique.
All of this points to the danger of relying too much on Efficient Market Theory. While EMT suggests that at any given time the market price will be roughly correct given known information, we also know ‘Mr Market’ is bipolar. Add to this that without knowing the various participant’s time horizons, it’s even more difficult to have a common formula for valuation. These market dislocations are certain to appear in black market credit card valuations as well.
When we look at market rates as an indicator we need to keep in mind the limitations of market quotations (EMT), never mistaking our model (market price) for reality (intrinsic value).
Nonetheless, the market price of these cards is perhaps one of the single best indicators out there.
Another American company ignoring the severity of firewall intrusion alerts then dealing with the consequences . It’s time for the big banks to switch cards over to chip and pin, otherwise this problem is going to continue on
Most of the EU uses chip & pin, right? Does the US have a higher number of intrusions proportionate to credit card transactions numbers than the EU? If so, it’s a no-brainer to switch to chip & pin.
Correlation and causation are two different things.
For example, I get up in the morning, the sun rises in the morning.. thus the sun rises because I get up in the morning??
There are good reasons to go to chip and pin, but confusing correlation with causation doesn’t make for a rational argument.
Secondly, the credit card itself becomes less important as the economy moves from brick and mortar stores towards online merchants. So while I think chip and pin is worthwhile, it’s like closing the door after most of the cows have left.
Ultimately it will take a change in mindset to handle the least amount of data, for the shortest period of time. We are nowhere near that being a popular idea (unfortunately quite the opposite).
Online merchants can use chip and pin with some type of two factor authentication to validate the purchases are being made by the right person.
That is certainly true.
The authentication is whether the cardholder is legit, and that’s only half the problem. For consumers to have confidence, it would be wise to authenticate the card processor as well.
Infosec folks focus on folks getting into their systems, and not protecting users from hackers, scams, etc. The hacks we hear about are usually from email, man in the middle etc.. and they are all enabled because consumers can’t authenticate the systems they are using. One get’s an email from their bank.. is it from them? who the heck knows.. there is no authentication. An email from an merchant? same deal.
The atm card goes in, and other than external inspection (which brian covers with skimmers very well) there isn’t much a consumer can do.. because the far end is never authenticated.
So lack of a display and keyboard on the card is the problem.. chip and pin isn’t enough.. it’s only at best authenticating the card and cardholder, not the machine and processor connection.
Making cards smarter, with chicklet kb and display would be tremendously secure (and expensive). So it just depends on what folks want to do really. However the folks who do provide that secure card system will knock it out of the park (minus their royalties on my patents for a kb and display on the card, right?)
Using proper Authentication like using a token security device like Yubikey for all bank transaction that use credit cards or the transferring of money between account holder in conjunction with Chip and Pin card technology. This certainly would stop a lot of abuse but would the American people adapt to that kind of change when doing online purchases?
Using Chip and Pin, 2FA, and security tokens in my opinion is the solution to this ongoing problem. If you adapt everyone over to this solution , then the cyber-criminals won’t be able to effectively operate and or it will make it extremely difficult to run their operations
We got into this mess because the banks want cards not present to be usable so they collect more fees.
The chip isn’t the improvement. It’s the accompanying change in protocol. We could have had the better protocol long ago, but the processors didn’t want to develop software. They have enough trouble maintaining the ancient stuff they are running now.
Everyone wants the cards usable when not present. banks, merchants and consumers. There are good economic benefits from higher velocity, and easier transactions facilitate that.
So it’s a bit unfair to put it on the banks just as it’s a unfair to assign the ‘cost’ to a single entity for fraud or breaches. We all end up paying.. even the hackers end up paying – which is funny because they don’t realize they are really hurting themselves even if they are in another country.
I do agree with you the system we have is awful. Whether present or not, it just authenticates the card/user and the user can’t authenticate the system they are using. I suspect that had the systems been designed with the mindset of protecting the consumer/grandma, it would have focused on how the consumer could verify the merchant, bank/machine more. As it stands banks send out emails with links and attachments and the consumer has no way of knowing if it’s really from who it claims to be. Or an ATM is presented for payment, and the card/consumer has no way of knowing what’s behind the plastic front.
With double authentication online bank logins (they show a token after you say who you are, but before you type your password) there is at least a try at authenticating the bank. That needs to happen not just on bank logins, but on card use, both present and not present.
That’s why keyboards and displays on the card are really what’s secure; because otherwise you really don’t know whether the machine that you putting your card in is just asking for your pin and reading the card stripe. And that is indeed expensive.
In my opinion, online/card not present is actually easier and cheaper to make more secure (but hey, what the heck do i know anyway).
One could make online ‘card not present’ literally a ‘bill pay’ with all the same authentication of logging into the bank. One could have a bank online payment secure plugin (which doesn’t exist as far as I know.. yet). Merchant writes up the bill for shopping cart.. and sends it to bank. Consumer authorizes payment of the bill. Merchant has minimum CC info (could be a bank pseudo cc id used only for the online mechanism).
I do think the card is a dinosaur for the most part. Online purchases are desired by consumers, merchants, and banks, but as you have pointed out, they expose the physical card system flaws (as well as scale up the consequences).
Authentication of the system by the consumer/card instead of just authentication OF the consumer/card would address the physical issue.
Making the card not present system use a bill pay system with unique card numbers would keep merchants from ever seeing card numbers, pins, etc. They can’t lose what they never had.
Instead of reading about a merchant online hack, we would read “10 million fake bills were submitted today.. none of which were paid, so nothing really happened, no data was compromised”.
It could be done..though I agree with you it would take a lot of effort, and folks would have to actually design to protect the consumer (oh the horror!). but hey, what the heck do I know.
You’ve basically described PayPal.
I can go to a site, add things to its shopping cart, and click check out.
The site sends me to PayPal. PayPal can request 2FA for my account. I verify PayPal using my browser’s chrome (it shows EV, USA, PayPal) and I login and confirm payment.
Payment is transferred from PayPal to the vendor. The vendor never has my credit card information (nor my bank information).
PayPal has been doing this for years.
They also offer a credit card and I think they have a new thing where you can scan a QR code to pay / buy.
I’m using PayPal more and more these days. I just hope they don’t get hit. I wonder how many attacks they have to fend off each day.
Correlation & causation aren’t the same thing, but short of asking East European malware malefactors, “Do you pick on US banks because they’re easier to penetrate?” correlation is sufficient cause to update to chip and bin.
The comparison of the idiotic ‘sun rising’ example with my argument beggars the polite language used in this forum.
The US is the largest economy. The US is a target because as the saying goes, ‘that’s where the money is’.
The US will remain the primary target even after chip and pin.
That being said, we should have had chip and pin long ago.
The problem with the argument that the US is a target because it doesn’t have chip and pin just allows folks who want to argue against chip and pin to defeat your reason… they can cite countries with lower target rates (say a few poor ones) and a per capita breach rate as low.. and no chip and pin.. and aha.. they argue that the US should not bother.. that’s the problem.. the weak argument makes a low hurdle for those wanting to stall.
We should do chip and pin because it is a bit safer, and yes, the US will still be the main target, for political, economic, and a host of reasons. That’s not about to change.
US & EU economies are roughly the same size.
http://en.wikipedia.org/wiki/List_of_countries_by_GDP_%28nominal%29
And China (depending literally on the price of rice).. but I suspect China does not have the same ‘bulls eye’ as the US.
And because the EU is a collection of countries, it’s more like comparing states, or provinces, or whatnot.
My point is that we SHOULD do chip and pin, but I reject we are a target because of lack of chip and pin. Russia and China will still target the US after we go to chip and pin. The Russian ‘miscreants’ are not likely to to start hacking russian of Chinese companies.
There is a reason Turla targetted US and EU. One could argue that it targets them because there is some correlation between the size and economic power (as you pointed out), and sure, in some secondary way that is true. Certainly if the US were the size of Bahamas, even if it had ious for credit cards ( it simply would not be a world power). One does need to be larger to be a world power, and that’s ‘where the money is’.
Anyway, we should do chip and pin. But the argument that it’s somehow the reason the US is a target is just not true. The US will continue to be a target with or without chip and pin. It’s also problematic because it set’s up “you promised the attacks would stop after we did chip and pin”. Again, if one wants to undermine the argument for chip and pin, sure, use the argument that US is a target because of lack of chip and pin. But if you really want chip and pin, it’s just not a good argument.
That’s all I’m going to say about this, as I’m sure we both have more important things to spend our time on.
regards.
Thought you said “end of week?” Dang, this is NOT a fair fight; everyone is just fish in a barrel at this point.
How do these site remain “up”? Like Rescator.la , etc. Why don’t the ISP hosting them take them down?
Cash is looking better all the time.
Oh, now, not Sally’s! It just gets worse and worse. Brian is going to have to rename this blog, The Daily Breach.
Okay, here’s the cheeky trick of the day: I went onto a website linked to my business twitter account and immediately got a pop-up flash box with a “Windows Security” label and a RED warning that it had detected 3 malware files about to be downloaded to my PC, trojans etc. Even listed the file names, with instructions to click “Clean Computer.” But I really do keep Windows Security running real time and AVG antivirus, AND Malware Bytes Pro, and none of them were sending me any warnings. So, I scanned with my real Windows Security, and sure enough, the first Windows Security warning was bogus. What nerve! I backed out real slow….!
Great info again from you Brian :).
One song that goes with the theme:
http://youtu.be/EivR78mrRFE
If the card data environment was segregated (air gapped) to point stright to the acquirer then even though these companies suffered a breach their card data would remain secure. Basic PCIDSS compliance! The technologies out there use it; it has to be cheaper than the subsequent fines and ultimately loss of your business.
PCI DSS is the band-ade for a seriously obsolete and flawed design. We are basically to make a secret of information that is embossed in plastic, and made responsible if we fail to compensate fully for the insecure system.
But you’ve hit on the heart of the matter in my view. The transaction is 3 way: cardholder, credit issuer, and merchant. The merchant system should tell the terminal how much it wants then the entire transaction should be a direct encrypted communication between the terminal on behalf of the cardholder and the processor on behalf of the card issuer. The terminal then tells the POS system it did or did not give the merchant money, and provide a voucher #.
The merchant only handles this data because this system evolved from the paper credit card tickets, which the merchant used to physically carry to the bank. It seems to me nobody thinks very clearly about the basic principles. It’s all about whatever works and is easy, like.
The Amazons, Googles, Apples, eBays and friends are going to hopefully render this entire discussion moot before long. Or maybe bitcoin, though every encryption so far has become broken and I can’t think why bitcoin’s will be an exception.
Good description, and I agree with you about minimizing the flow of information across those boundaries. We are in a time when any and all data is considered an asset, so it will require a ‘mindset reset’ to flip that around.
The consumer, in your description, still doesn’t get to authenticate the system they are using. The plastic card (even with a chip) doesn’t give any authenticated signal to the cardholder. A hacked card reader can still say “OK!” to the merchant and it can say “OK! to the cardholder.. but meanwhile the pin and card data is siphoned off… perhaps say ‘oops.. failed.. ‘ and then leave the original code to do it’s thing. Plastic cards without a display and pin pad are going to be problematic to providing authentication to the consumer/card.
I agree with you that the online merchants can do better, but it remains to be seen whether they really do better. A fake site, hacked site, and/or a DNS hack can make for large breaches over a long time. I think we need a better online payment system as well as physical card present one.
Humor: I can think of one reason bitcoin doesn’t fail from decryption: because it fails before that from someone stealing all the bitcoins. 🙂
What was the popular site used ?
Walmart seems to be in the process of such a hack problem.
Cards often are processed without signature required, even for hundreds of dollars.
Often the cashier says the security number on the back of the card must be input.
When I complied to an associate manager she was totally indifferent to it. I even mentioned I had told my bank office ( in Louisiana) and they flatly said that should not be happening, signature should always be required. The Walmart cashiers and manager couldn’t care less even when the Target breach is mentioned.
At our local Walmart entering the 3 digit code into the key pad instead of a signature has become standard policy for all tranactions.
Giving the 3 digit card on the back of the card to a MAG CARD READER is an obvious security these days !
A merchant is free to skip the signature and gives up rights to protest chargebacks. Personally, I appreciate it.
It is proper to let you enter your own security code. It should never be printed on the card. Wha the ???? It’s a PIN, fer hevens sake.
But the card companies don’t want any form of security that anybody might have trouble with, and the lowest common denominator who pays the big interest is very low indeed, comperhension-wise. So they have resisted any sort of password.
No – not the PIN. The code mentioned is the three-digit one on the back of the card, often known as CVV2
They also often demand the PIN rather than the 3 digit code in the mag reader at the local Walmart, less often the signature anymore. Rather haphazard.
It all gets collected by mag-card reader hackers I think.
The hardest thing to reproduce is the signature, and SHOULD be required.
I miss the old days when the cashier had to look at the signature.
Thank God I haven’t shopped at a Sally’s in a good while!
One question though: Why is the spokeswoman Karen Fugate so vehemently denying that customer card data has been stolen from the company’s systems when the banks of Sally’s customers have pretty much confirmed that they have?
So those numbers just happened to belong to the same people who used their cards at your store? It’s better to admit fault then deny…could end up soiling their reputation in the long run.
Hopefully the only reason she’s not confirming because their investigation isn’t yet “over”.
In all likelihood it’s to avoid the inevitable lawsuits.
Admitting guilt is one thing, but it’s the paying for damages part that companies don’t like so much.
Not to mention the loss of revenue. Sales down 5% across the chain is a really big deal and can wipe a company out. Even if it’s not their fault and even though 100% security and compliance are impossible.
We’ve got to focus back on where it starts and stop acting like it’s OK to just treat hacking like weather. These are eco-terrorists and should be dealt with as such. If a national government did it, it would be an act of war.
20 years?? Try life without parole.
This is pure conjecture on my part, so take it for what its worth…
Perhaps Sally Beauty is vehemently denying that they were hacked because they weren’t.
Farfetched, to be sure, but possible.
Here’s the “nightmare” scenario that I envision.
Suppose a smart, cool thief has actually hacked either a payment card processor (it has happened before and will likely happen again) or, heaven forbid, an acquiring bank.
If they have access at the level above the merchant, then they could be receiving traffic and data from many multiple merchants.
Rather than dumping all of the cards out at once and drawing attention to themselves, they could use the same sort of analysis (common point of purchase) on the data they are collecting and only release batches of cards from one merchant or another at a time – making it appear that specific merchants have been breached and covering their tracks.
In actuality, the level of access I am envisioning, they would not even need to do CPP analysis – simply filter their collected data by merchant ID in the auth request and only release cards from one merchantID at a time – thus making it look like a specific merchant has been breached.
Is this scenario farfetched? Yes, but not beyond the realm of feasibility.
If it was just Sally that was out there saying that they haven’t been breached, I write it off out of hand, but the fact that Sears and Michaels have both been rumored to have been hit in recent weeks with no hard evidence (as there was in the Target and Neiman Marcus cases) coming to light yet is beginning to make me wonder if something larger than individual merchant breaches is going on.
I can only imagine how much money the Target hackers walked away with. Even with prices falling they had thousands of card numbers to sell and I would imagine they got as much money as they could as quickly as they good. When information transfers instantly it’s hard to shut it down.
All this is making old fashioned credit cards more appealing. The three piece reciept, the smudges on the paper, etc. And someone actually had to destroy the copy.
Actually, I’d rather have Traveler’s Cheques.
Each check was unique, issued to you and traceable. You could get them reissued if they were lost or stolen. And they couldn’t be double-spent (and certainly not triple-spent). You showed your ID to spend them and everyone was happy.
For a while, Discover had One Time Use Credit card numbers for electronic transactions (apparently it was based on technology from Mastercard) – but it’s being discontinued this Saturday.
“Can I ‘see’ your identification.” The mean can I hold and touch your drivers license. It’s my bank, my branch, and the person asking knows me from previous visits. They put it down in front of them and start typing away. They ask about last transactions and other questions that I have answered before but they act as if they don’t know me. At some point they insist it’s because of their excellent security and procedures they must follow. A simple transaction takes far too long and in one year my DL was lost three times.
A week later I get a call from the fraud department notifying me that I may have been the victim of identity theft. Turns out that someone opened an account in my name by phone or over the internet. The bank allows them to open the account without coming in with picture ID and to sign a signature card.
Turns out that this new ac count gave the thief access to every account the my signature is on at BoA. They see every account including ones that my signature is one ” for emergency reasons ” ( elderly parents who might need me to sign a check if they are sick ) BoA defends their policies by saying they only follow federal and state laws.
I had one credit card that I never used. It was a convert from Wachovia that I didn’t ask for but got.
The devil is in the details and this true story is already 50% too long for most readers who no longer open with a greeting or sign off with closing.
So, just for the record: I found out most of the information that one would think the merchant, bank, credit card issuer, police department etc would want to know. But they do not want the information until they are ready for it. Who knows how long that may take.
If this was an episode of The Soprano’s the problem could be cleared up in short order. But that is not how ” civilized ” society works now is it?
Sorry for the typo’s; I didn’t proof read….might be a lesson in that fact for me to pay attention to.
It all brings us back to mules, though, doesn’t it? You can’t use thousands of stolen credit card numbers without having thousands of money mules or reshipping mules to facilitate the fraudulent purchases.
My credit card number was one of the ones stolen from Sally Beauty here in Vestal, NY.
I purchased my wife’s hair color at their Vestal, NY location February 24th at around 8 PM, for $36.31.
My card was obviously one of the card numbers that was sold this past week. I went to my local kwik fill to purchase a beverage and my card was declined. Suspicious why my card would be declined, I checked my bank account while in the kwik fill where I discovered 13 transactions were on my card totaling almost $9,000 at a Target in Brooklyn, NY.
I immediately called my bank to inform them of the charges and dispute them, and I’m praying and praying that I can get my money back. My wife, our 3 kids, and I were planning on buying a house this year.
This thief has completely crippled my life. My bank has a max spending limit of $10,000 per month, and I had about $1,000 in my savings. This thief using my card number has made my account hit the max spending limit for the month, so even if I do get my money back, I can’t use it, spend it, or pull it out of the bank until the end of the month. Can’t pay my rent, or any of my bills, and I have absolutely no money to use until all this mess gets fixed.
I have 3 kids and a wife to support and take care of, and this has completely ruined me.
I hold Sally Beauty completely responsible for their negligence in properly securing and protecting my sensitive information. Also, they failed to notify any of their customers in a timely manner, as they only just made a public stated on March 6th, the day before my bank account was cleaned out. If they detected the intrusion on February 25th, then why did they wait until March 6th to make a public statement? Had they made an immediate public statement, this entire incident could have been avoided and I could have called the bank and received a new card.
Sally Beauty failed it’s customers by not properly securing their sensitive information, and not informing them of the breach in a timely manner.
I sincerely hope and pray that no one else was affected, and if you made any purchases at any Sally Beauty on February 24th, call your bank right now, and get a new card. You could be next.
I would not wish this to happen to my worst enemies.
I’m an honest, hard working father and husband, I don’t drink, do drugs, or anything. I work hard, and come home to my kids. I’m the only income for my wonderful family of 5. I don’t deserve this to happen to me.
In case anyone was wondering, I called the bank first, cancelled my card and was issued a new one, also filed a police report, and contacted an attorney just in case. I suggest if you were hit too, that you do the same.
Good luck everyone.
Oh, my goodness! This is awful. This is where cybertheft meets the real world and shows what a lie it is that “only the big stores and banks” get hurt with this stuff. Crazy enough, you Mr. Wheeler are the second person that I’ve heard with this story in the past week. One of my colleagues got hit exactly the same way, to the tune of $13,000 dollars. In her case, her card was used at a luxury store that broke the transactions into 3 parts because her bank or card provider had a limit that wouldn’t take the amount all at once. How crazy is that? I consider the store(s) to be co-conspirators in cases like this. $9,000 at Target in Brooklyn? Give me a break. Good luck to you and your family, sir.
I’m very sorry to hear of your troubles, and I am certainly not trying to lay the blame on you as the victim, but your story is exactly why I do not and will not use my debit card at the point of sale for any purchase.
For me, any card directly associated with MY money (i.e. checking or savings account) is ONLY used at a bank ATM in order to deposit or withdraw funds.
I will only use a card that is directly associated with SOMEONE ELSE’S MONEY (i.e. a credit card) at retail at this point. If a thief gets my account info, it will be a hassle, but my money is not directly at risk.
I find it interesting that Sally still has not said anything to confirm a breach. I’m wondering if this may have been more localized in nature or if there is some other form of action at play that we haven’t seen before.
Why are we still in detect mode? Are people still wanting to watch criminals still information instead of blocking them? Why not block the activity immediately when TripWire detected it. Why allow it to happen in the first place? It makes no sense to just watch criminals exfil data instead of blocking them in the first place.