Phishers and phone fraudsters are capitalizing on public concern over a massive data breach announced this week at health insurance provider Anthem in a bid to steal financial and personal data from consumers.
The flood of phishing scams was unleashed just hours after Anthem announced publicly that a “very sophisticated cyberattack” on its systems had compromised the Social Security information and other personal details on some 80 million Americans.
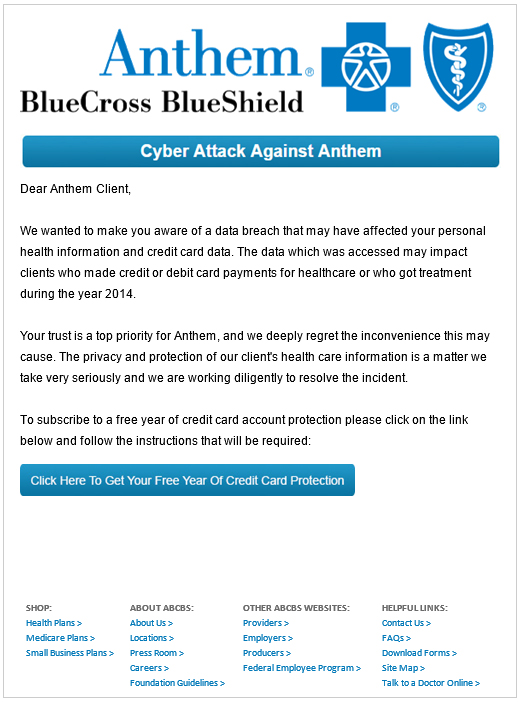
In a question on its FAQ page about whether it would be offering credit monitoring to affected customers, “Anthem said All impacted members will receive notice via mail which will advise them of the protections being offered to them as well as any next steps.” Unsurprisingly, phishers took that as an invitation to blast out variations on the scam pictured below, which spoofs Anthem and offers recipients a free year’s worth of credit monitoring services for those who click the embedded link.
According to Anthem, fraudsters also are busy perpetrating similar scams by cold-calling people via telephone. In a recording posted to its toll-free hotline for this breach (877-263-7995), Anthem said it is aware of outbound call scams targeting current and former Anthem members.
“These emails and calls are not from anthem and no notifications have been sent from anthem since the initial notification on Feb. 4, 2015,” Anthem said in a voice recording on the hotline.
It is likely that these phishing and phone scams are random and opportunistic, but there is always the possibility that the data stolen from Anthem has fallen into the hands of scam artists. According to Anthem, the information stolen includes the consumer’s name, date of birth, member ID, street address, email address, phone number and employment information. However, experts believe that the attack on Anthem was perpetrated by state-sponsored hackers from China seeking information on specific individuals for espionage purposes, although that conclusion has not been independently confirmed.
The company says it will begin sending notifications to affected consumers via snail mail in the coming weeks. In the meantime, if you’re a current or former Anthem member, be aware that these types of scams are likely to escalate in the coming days and weeks.
Update, Feb. 9, 6:15 p.m. ET: In a somewhat farcical turn of events, it appears that the image above is actually from a phishing education campaign created by a company that helps firms impress upon their employees the importance of cybersecurity. The image above, when clicked, brings users to this page, which warns visitors they’ve clicked on a link design to test awareness. That page is run by Knowbe4, whose CEO Stu Sjouwerman said in response to an inquiry that the image was likely forwarded to Anthem by a cautious employee of one of Knowbe4’s customers who received the phishing test but did not click the link. Full disclosure: Knowbe4 is an advertiser on this blog.




Jeez! It’s like throwing a pebble in a pond. Ever-growing rings of cyber-crime!
Brian – it would be nice if they defined “former” customers…former as in any customer since the beginning of time? Or only those with active plans within the last five years? Do they ever purge old records?
How am I to receive a letter if I have moved many times since I had anthem, etc.
Frustrating!
As I commented in the first post, about five years Anthem kept applicant data on a non-secure server. If someone became a customer, that data was copied to the regular, secure server and the old data was deleted. But if someone never became a customer, that data remained. And, of course, that server was breached. It was a HIPAA violation, but people who suffered identity theft only received a one year subscription to a credit monitoring service. I think you and all other former customers are in the same boat, sorry to say.
Hi there. You said that the persons previously received credit protection services. In what context? Was that some sort of proceedings? If so , where? Thank you.
Brad Clanton
It feels like all of this is now just a part of life. It’s not a case of ‘if’ you will be affected, but a case of ‘when’.
As one other witty person noted – it was just the right time for another major breach. My one year identity theft protection from Target was about to run out!
Seriously – Anthem didn’t encrypt the patient confidential information internally. Only because someone noticed data requests being made in their name was the hack discovered. No technology made the detection. JP Morgan spent $250M/year on information security. What did Anthem spend and what did they get for it?
The cost to us as individuals, as companies, as a nation, as a world are high and diverting resources from pressing needs. We need a better way.
Jonathan @nc3mobi
Encryption is not a magic sauce. Encryption is great for data in static storage or being transmitted, less good for data being used because it has to be decrypted to be used. Steve Bellovin explains better than I could: http://arstechnica.com/security/2015/02/why-even-strong-crypto-wouldnt-protect-ssns-exposed-in-anthem-breach/
At least at this point, it seems that the breach was the result of compromising one or more DBA passwords. Anthem’s DBAs would have needed the ability to see data in plain text form.
Clearly today’s controls aren’t getting the job done. The problem I see is the controls are focused on the device ex. database, server, laptop, etc. What we really care about is the data. Unfortunately, most encryption technologies inhibit use of the data by applications requiring exposure of the data in plain text creating an opportunity for theft. I don’t see this as a problem with encryption necessarily, rather with the way encryption is being used/implemented resulting in gaps and eventually exposure to a breach. To Bob’s point, encrypting data only to provide a DBA account full access to clear text is counter productive.
I disagree that today’s controls cannot get the job done. What is not getting the job done is old management types who blather on about what they did twenty years ago who prevent today’s controls from being implemented properly.
Target was the perfect example. They purchased a highly reputable system (FireEye) that warned them. And warned them. And warned them. But they never switched it into blocking mode. I can guarantee that was not an IT security decision but rather an old-time management type decision who was using their experience from two decades ago.
And no, physical age has nothing to do mindset.
What does DBA mean ?
DataBase Administrator
or
Doing Business As
The former.
Actually you can encrypt data in use. Now if you mean in motion the only course of responsible action is monitoring.
Well here’s another witty but true point, Anthem will have to cut their stock buy backs now, all the big insurers are on the S&P 500 and part of premiums help these companies buy their stock back, it’s going on all over and I think Anthem is buying back around $12 billion, so that may have to go for security now.
http://ducknetweb.blogspot.com/2014/12/insurance-carrier-stock-buy-backs.html
Breaking encryption is no longer a primary path that cybercriminals are using. Mostly, they are using exploits of various kinds to gain access to the data in human-readable format.
Since when is it safe to assume that American corporations will do what is in the best interest of the country, the economy, or the people who rely on that corporation?
As long as you’re using “When” to indicate the past because it’s probably already happened to anyone old enough to drive.
Keeping the SSN alive is all part of a plan to cause the citizenry to increasingly clamor for a secure replacement.
Once critical mass is reached, the government will release their already-written plan for a semi-secure, unique identifier that will become part of you at birth via an implant for your convenience.
https://en.wikipedia.org/wiki/Sheeple
Okay so this breach is a HIPAA violation.
so what does that say about compliance frameworks if you just are not investing resources to protect the information entrusted to these organizations.
Consequences must be expected and scaled to the violation such that its deterrent value assures true compliance.
Or we could just shrug our shoulders once more and hope that there will not be a next time…
80 million records is almost one quarter of the US population. Random calls and emails have a pretty good chance of reaching actual Anthem customers. A lot of others aren’t sure but they know they have Blue Cross Blue Shield insurance so they think they might have been impacted.
It seems like the list of US population not having their identity placed at risk might be shorter than those who have.
From experience working with these types of things I believe that encryption of the data would most likely have made little difference. Encryption only works well to protect data at rest or data in transit. Its doesn’t do a good job protecting you when you have data in is use. If data is to be used it needs to be viewed. If compromised account has business need to use the data, it would have been able to use the keys to access and view the data.
Sure the SSN could have been encrypted field but would that have kept information secure in an environment where numerous individuals and systems have the keys to decrypt it…..very unlikely. The problem is that the fields with the scariest data in it, are the ones the insurance industry often uses the most. Would be different if they rarely used these fields that only a few people needed to index on or access.
Encryption doesn’t fix everything. Its just another door that requires someone to have a key. If done right is a very strong door. Doesn’t work if everyone needs the key there fore everyone has a key or if there are weak protections on the key. Encryption of data in a database is really just another type of access control when it comes to securing data in use.
Real question will be how they implemented their access controls, data structures, and server logging and alerting, Then learning what can been done keep this from happening again and how those lessons can be leveraged across the industry. One of the largest outcomes may be a shift in what data the industry uses to index and identify unique individuals. As its easy to see how their business models are putting a huge burden on their InfoSec teams.
My credit union sends me an email whenever a valid password is used for my account (among various other alerts).
If DBA passwords are given out via spear phishing, wouldn’t this be a good idea generally?
You probably don’t get an email each time your mail client connects to your mail server telling you that you connected.
DBAs talk to databases regularly, potentially hundreds of times a day.
You could set up a trigger for rarely accessed servers, but the people who would set up those triggers *are* the DBAs. Done wrong, someone with access would disable the trigger first.
Or, they’d have the DBA’s email credentials and delete the notification.
Note: I’m not saying these things shouldn’t be done, just that they aren’t silver bullets, and typically when you’re compromised, it’s too late.
The last time I made the suggestion below, I was slammed by the Very Knowledgeable experts who read Brian’s articles. I was ignorant, didn’t understand how programming projects worked, how impossible it would be for foreign offices not to have direct access to important data, etc, etc.
Sensitive data, whether important software code or personal customer info, does not belong on a server accessible by the Internet. I don’t care how f*king inconvenient that makes it for programmers or service reps or anyone else. Access to that information should only be allowed offline. Should someone in your office in Timbuktu need something on a server in NYC, s/he should requisition it, the info be offloaded and transmitted securely with the understanding that Timbuktu will immediately convey the data to an offline device and then remove it from their online server.
Richard P. Feynman said, “It doesn’t matter how beautiful your theory is, it doesn’t matter how smart you are. If it doesn’t agree with experiment, it’s wrong.” So I submit this question. Is Anthem’s breach (BTW, 80 million is over one third of the entire US adult population), sufficiently contrary to the accepted laissez faire protocol of leaving data online to prove the protocol wrong?
In a word: yes. You’re right (IMO).
I know of one company (international in scope) which follows this policy—not naming names because someone would take it as a challenge and try for at least a DDoS attack. But all of their sensitive information is totally disconnected from the internet. Websites are served from physically separate servers with NOTHING on them but the website data. Also, customers can’t access sensitive data over the internet—they have to actually go in to a branch office or talk to an employee.
“Inconvenient”? Maybe. (I don’t think so.) But they’ve never been hacked and they never will…there’s nothing there to hack on their internet-facing computers.
If I had sensitive data personally, I would follow the same policy and have two separate computers, one of which would be permanently disconnected from the internet. But I figure there’s no point in me doing that when so many companies have all my sensitive data anyway and store it so insecurely. To quote a sci-fi novel: “Do you worry about the seventh lock on the back door when the front door is open?”
Email gets through to computers not directly accessible via the Internet. A successful phishing attempt or lucky wide-net cast will get the credentials of a users, and in this case it could have been the DBA whose username was found running the queries that tipped off Anthem.
JP Morgan’s hack was via phishing. Since this was a very professional job, and possibly a state-sponsored hack, phishing is probably the place to start looking. No need for a public facing Internet-accessible server when you can hook someone already on the inside of the network.
If you’re willing and able to employ a “no Internet” policy, you can also have a “safe email” policy. Just take your email back to what it was before we decide the email should be the gateway to … everything on the Internet. Go as far as plain text only, no attachments, if you want. A front end on a machine with access to nothing but the body of emails could render a subset of HTML as plain text – or even allow some limited but safe formatting.
The idea that your email client should have (effectively) the power of your browser is what enabled phishing. Lose some functionality and you can gain safety.
— Jerry
“The idea that your email client should have (effectively) the power of your browser is what enabled phishing. Lose some functionality and you can gain safety.”
A company can do both if they are willing to invest in keeping their employees reasonably safe and productive. We use a system that integrates the proxy server’s URL categorization, malicious code protection and sandboxing with inbound email. Every email with a link or HTML code is treated as if it were a browser request, but before an employee ever sees the email.
Since that would require spending money many small and medium (and a few large) just accept the risk.
Even simpler methods like blocking all attachments with executable code attachments like PowerShell scripts, .scr files and the like would help tremendously. It doesn’t seem to matter what the industry is. We recently got bombarded with emails from a community bank that had .zip attachments with .scr files inside. When we called them they were clueless that it had happened.
The continuing use of Social Security numbers as any kind of unique identifier defies reason. I don’t follow every data breach that occurs, but the size of this one, along with the inclusion of the number that every U.S. citizen is instructed to guard with their life, the number that ties together our financial security with a bow, is, I believe, unprecedented. This was bound to happen. I’m only surprised that it took so long.
As former Anthem customers, my wife and I have been given a wake up call to lock down our credit with the three major agencies. Given the amount of time that actually took, it would seem a lot of other people got the same call. What more we can do? In our modern age, the financial damage that can result from someone in possession of a linked name, DOB and SS#, is akin to a form of slavery. Our financial freedom, that has taken years to nourish and grow, can be wiped out in an instant.
Unfortunately, unless one wants to stuff money in their proverbial mattress and likely live a life filled with paranoia, or can exist solely on the barter system, some kind of unique identifier is absolutely necessary. It is well beyond time to scrap the Social Security number as this unique identifier.
I began this comment to make a snarky remark about the security of Bitcoin, or lack thereof (insert link to the latest Bitcoin plundering here). Unfortunately, the need for keeping our financial data and our money secure is here to stay, at least for the time being. Any humorous remarks are overshadowed with trepidation. Ask anyone who has been the victim of identity theft and hear their tales of the countless hours, days and months it took them to regain some semblance of their identity.
That we allow this to continually happen, and to a worse and worser degree, is troubling. That the U.S. banking industry took a decade longer than Europe to adopt the more secure chip and pin system is embarrassing, but the risk was all theirs to take. Will our do-nothing congress take a leadership role in moving the U.S. in the right direction? I’m not holding my breath.
” … the inclusion of the number that every U.S. citizen is instructed to guard with their life …”
For years the IRS would mail out the tax booklet to individual taxpayers with a sticker on it that could be placed on the reporting form that was mailed to the IRS for processing.
That sticker had the taxpayer’s full name, address, and Social Security Number printed on it.
In the late ’70s my college dorm had an official roster, printed by the university, that had everybody’s SSN on it. In the ’80s my cousin had her SSN printed on her checks. Yes, things were different.
I am just curious…. Why would an insurance need or keep income information and Cc info?
It is time for patients to just say no to any medical provider asks for your SSN. No dentist of optometrist or MD or hospital needs your SSN to do medical treatment. They want it because they can access some insurance information with it. Make them prove they need it. The V.A. is huge problem of this kind. The V.A uses the SSN as a universal identifier. But when I was the the USAF, and in the Army National Guard before that, I had a unique ID number which I still remember, as did all pre-Vietnam-era military members. The V.A. very recently mailed to most vets a new identifier, to be used in case the vet needs health access but isn’t in the V.A. system yet. So the V.A. can use a non-SSN number. Therefore, so can all insurance companies. Customers/patients just need to refuse to provide the SSN, and require the insurance companies to come up with a new/different number which is not tied to the financial system, to make SSN breaches far less valuable. This kind a grass-roots rebellion, together with emails and letters to Congress people (both House and Senate) and to the White House, could make the change happen. If you readers aren’t willing to do the writing and emailing, then, as Eldridge Cleaver said, you are part of the problem, and should suffer the consequences.
SSN is needed for insurance companies and medical providers primarily because of the existence of medicare and medicaid. Section 111 of Public Law 110-173. Coordination of benefit payments with other insurance providers. Insurance companies are required by law to coordinate with medicare and medicaid.In order to comply with the law they need your SSN, employer information, etc. The insurance companies aren’t trying to be evil by snarfing your info they actually need it to comply with federal law. They can be assessed fairly large penalties for not complying.
http://www.sibson.com/publications-and-resources/capital-checkup/archives/?id=1282
Can find tons of other articles about the requirements online as well. That is just the first easy one that came up that explained it pretty well.
You’re missing a critical point: You can easily get your insurance company to issue you an ID card with a number other than your SSN — you just have to ask. I’ve had one since the late 1990’s. But that doesn’t help at all in a situation like this because the insurance company will STILL have your SSN on file in their database, whence it can be stolen, along with your name and DoB, by anyone who has access to said database, whether it’s an outside hacker or a rogue employee.
I recently changed jobs and thus got a new insurance card. It does not have my SSN on it anywhere and I didn’t ask for to be that way.
My guess is that now only Medicare/Medicaid cards come with the SSN on them.
No they don’t come with SSN’s one them…lol Not in NY anyways..
Premium rates, within a company, are sometimes linked to income. A single female with children making 36K will pay less than a single person with no children making 120K
Thank you for the update .
I think this phishing example came from a commercial phishing test company:
@Jay — You’re missing a critical point: You can easily get your insurance company to issue you an ID card with a number other than your SSN — you just have to ask. I’ve had one since the late 1990’s. But that doesn’t help at all in a situation like this because the insurance company will STILL have your SSN on file in their database, whence it can be stolen, along with your name and DoB, by anyone who has access to said database, whether it’s an outside hacker or a rogue employee.
[ FWIW… Something might be amiss with the “reply” button. It’s failed for me on several occasions recently (two different posts, two different comments). After hitting “Submit” my comment seems to vanish into the aether never to be seen again. Then again, it could be Firefox or one of my add-ons… no easy way to tell. ]
Not the only one having problem with the Replys. Have posted twice on here today. Posts was there this afternoon, now poof are gone.
The crooks want to join the US epidemic of selling personal data too. Listen to the difference of the prices between the legal market and the illegal market. Hackers are smarter today and they know they can repackage and reformat data and sell it to companies who think they are buying legal data.
That being said it’s probably going on already. Like I mentioned before a few weeks ago I got a call from an offshore location soliciting me for a blood thinner clinical trial and somebody did some bad data work as they said I was on their records for taking blood thinners for a number of years now..never been prescribed and never taken any.
So again was this a legit pharma clinical trial outsoucred call center that bought some hacked data? Who knows but I can’t fix it and don’t know when it will show up again.
I’m amazed as people keep looking for some web exploitation of the data. Well think of this, they have 80 million files and most that hack for spite don’t take that much as they want let everyone know they are mad. There’s the ransomware guys that would also take more, but this to me is a bunch of hacker that want to sell data.
This why we need to index and license all data sellers, so data sold or linked carries a license number so we can look them up. Both companies and consumers have a need for this now. When the data is flawed and we can’t find where to fix it, we’re stuck as consumers. If the hackers want to play even dirtier they could scramble the data they sell so it’s pretty flawed and could hurt people. It’s not that hard to do that for those with evil intentions.
It just like counterfeit drugs that get into the real system, same thing here except even easier until enough errors might be found to determine it was stolen data. So again for 3 years I have been beating up a few members of Congress and the FTC to do this, have many blog posts on getting an indexing system in place, i.e. Licensing. Even a couple quants have chimed in on Twitter, Emanuel Derman for one who’s pretty famous retweeting me on this as well. It’s database 101 to regulate an industry, as who are they??
So along with the phishing, those affected don’t know when the hackers may swing into action. They could sit on it for months until they decide to do anything when heat blows over. Of course all these phishing notices were done by bots and if you don’t know it yet, around a quarter of the news you read anymore is written by “journobots”. That’s another story in it’s own developing with stock news feeds..anything to cheat and rig something it’s out there.
Here’s my campaign that I have been working on now for 3 years so a few months ago I put it out there to raise a little money as I’m just a sole independent with no corporate sponsors that’s been doing this on my own. We need licensing to tag on data sales and linked data that accesses our personal data. You don’t buy a house or buy stock from an entity that’s not licensed do you?
http://www.youcaring.com/other/help-preserve-our-privacy-/258776
Anymore there’s too many bad guys out there that take advantage and use technology both legally and illegally to make money. If you want to real up on how you get duped legally by companies and banks, watch the videos on the Killer Algorithms page and you’ll see what I mean on how the front end of a data base is what you see and the back end is what does the dirty work.
Be careful with all the new Fintech apps too as all the banks have labs now in the Silicon Valley, e-commerce to create apps that can mine your data on the back end to sell. Walgreens and CVS each make 1-2 billion a year selling consumer data so that gives you an idea how bit the data selling epidemic is at $180 billion a year. The licensing idea of course was not real popular with those mining data as you could well imagine, keep those consumers in the dark.
As mentioned in the article was this the list of stolen files or random. I think it’s random too as it appears to me anyway that this bunch has a longer and more sophisticated plant to sell data and make money. Like my situation, I got that off shore call about a clinical trial and that was before the breach here.
Here’s just one more item that may have some relativity today as well. Do you think Anthem might want to divert some of the funds and analytics they do with buying our credit card transaction now to security?
This is an archived post from a while back where an office of Blue Cross admitted they buy consumer credit card transactions to monitor what size clothes (and of course other data they get) their insured are buying. You can’t make this up either, and again this somewhat relates back to the data selling epidemic in the US, so where’s the ROI and is this about money or better care.
http://ducknetweb.blogspot.com/2013/03/insurance-companies-are-buying-up.html
I would say this one budget area where funds might be better spent with security right now.
Is this something Anthem has admitted to doing? Everything I can find from them says they aren’t doing it.
Blue Cross/Blue Shield companies are like franchises of a brand. There are over 30 of them. Blue Cross of North Carolina is a small regional licensee and really has nothing to do with Anthem. As independent entities and owners they tend to have very different business practices. So hearing that the licensee admitting its doing it doesn’t necessarily mean the entire industry is doing it. After that story got put out and everyone started false reporting that “blue cross” was doing it, most of the other blue cross licenses put out press releases saying they weren’t doing it was something that the owners of the North Carolina business started in 2013.
Banks, insurers and more buy your credit card data from Argus and it’s also scored so there may not be a direct buy from Blue Cross, they get it analyzed and scored from Argus. Be sure and read this as our Consumer Financial Protection Bureau also buys our credit card data from Argus too.
http://ducknetweb.blogspot.com/2014/08/argus-analytics-produces-share-of.html
There’s also E-scoring that does the same thing and skips a fine line with the law in not having to report what they sell and score about you.
http://ducknetweb.blogspot.com/2012/08/e-scoring-credit-algorithms-invisible.html
The World Privacy Forum put out an excellent report called “The Secret Scoring of America” so it’s everywhere.
You missed the point. You keep saying “Blue Cross”, which isn’t a thing. There are numerous insurance agencies which may be part of the Blue Cross Blue Shield Association but they are all independent insurance companies. Premera Blue Cross is a different entity than Anthem, which is a different entity than Blue Cross Blue Shield of North Carolina, which is a different entity than Blue Cross of Kansas, etc…etc
Mistaken attribution a companies actions to a completely different company just confuses people and spreads FUD. Which makes the situation worse at a time when a lot of people are scared for their personal information.
I think the big problem is not the use of the SSN for insurance, Medicare etc. per se, but rather it’s misuse as an authentication credential by the financial industry.
In my native home country (Germany) people are also assigned social security numbers (Sozialversicherungsnummer), but ID theft is not a major issue since there is very little a thief can do with it. In particular, it is not used for interactions with financial institutions. In order to open bank accounts, loans etc., you need to produce a government-issued photo ID. If it’s an online bank without brick&mortar branches, you can go to any post office and show your ID to verify your identity (this process is called “PostIdent”).
The other big ID theft risk in the US is related to the way the IRS handles tax refunds. This could be easily solved by giving the IRS more time to match tax returns to employer- and bank-provided information (W-2, 1099INT etc.). Of course this would require a Congress that is willing and able to actually do something useful …
I totally agree 100%! Been asking for 20+ years, why our SS# is used for everything that it’s not supposed to used for. Our wonderful congress controls everything and does nothing. When will the American people wake up- they work for us not us for them. Do your job as hired or we will fire you, plain and simple, this is what employers do!
As Dr. Cole told me during my first SANS class. “Prevention is ideal, but detection is a must”. Don’t just focus on keeping the bad guys out because you will fail sooner or later. Get a SIEM and catch them fast to minimize your loss. Anything is better than nothing. Logrhythm, Splunk, Arcsight, TripWire. Just get one and actually watch it 24/7
Joe
The SIEM market is an utter failure at solving the problems it’s marketed to solve. They are glorified log collection with deterministic “correlation”. Slap on some basic standard deviation maths and you’ve got yourself advanced security analytics! RSA had a SIEM. JP Morgan had a SIEM. Target had a SIEM. Anthem had a SIEM. All these big organizations have SIEMs. They’re great tools, but marketing as providing capabilities they simply aren’t effective at providing. A SIEM without the corresponding intrusion/breach detection capabilities/controls is NOT going to allow you to “catch them fast”.
JPMorgan is actually a wonderful case study in how to do it right. The hackers were inside their network for several weeks yet all they got was some low-value contact information. At almost any other company they could have phished some marketing person and gotten far more. Or a system administrator. Or customer service. They clearly limited in formation access to “business need to have” and not “business nice to have”.
No, I do not work for them nor do I know anyone who works for them but I do have an account with them.
I’m not sure I’d call getting compromised and having customer information stolen a case study in “doing it right”. We will agree that they fared better than others have. Regardless, I’m quite sure they have a SIEM (probably more than one) and it didn’t prevent them from being compromised
How do you know Anthem had a SIEM? I’m trying to find out if they did.
yes its true, the head of IAD for the NSA says the same thing. Assume your already breached. Prevention is almost impossible. Especially on cell phones.
Why don’t all the businesses holding personal data contribute 1 cent per customer per year (or whatever fraction of a cent is needed) into a central fund, and then any customer that wants it can have permanent credit monitoring paid for out of that fund. It doesn’t absolve the companies from the requirement to keep data safe, but saves a whole sh*tload of admin and expense if things go wrong (there but for the grace of god etc).
What is interesting to me about this is that I work for the University of California. The email we received said that Anthem had SSNs for only the staff/faculty. They did not have SSNs for students (students pay for a plan in their fees unless they opt out). So I responded to HR asking why then do they have SSNs for staff/faculty if they don’t need them for students. I’m not holding my breath for a response.
Emails stored on some third party servers can never be secure unless encrypted at source. Binfer does not store emails anywhere. It is a better way to send secure email. See http://www.binfer.com/solutions/tasks/secure-file-sharing
Brian,
The image you posted inferring the hackers have created was actually created from a phishing prevention service, Kevin Mitnick-KnowBe4:
http://blog.knowbe4.com/data-breach-at-health-insurer-anthem-80-million-records
It appears the hackers are utilizing it.
– Onnig
I just read your Feb 9 update. Please ignore my post.
– Onnig
And today we received a legitmate email from Anthem telling us about the ID protection they are providing, verfied with Anthem and our forensics team. Thus backtracking on their statement that they were going to communicate only via US Mail and sending email they warned us hackers would send. Lovely.
Hackers are spending months and months attempting to get into a particular server. Large companies like Anthem are not going to be able to fight every threat every time. Did anyone think to ask how many threats Anthem stopped this year?
Please do not jump to condemn. SSN are used for federal filing purposes. SSN are used for billing purposes. This is not going away. Anthem takes great measure to protect the identity of it’s members.
I understand that their are a lot of people scared and angry by the breach. That is a normal reaction and emotion. Please accept the offerings of the company and realize that cyber attacks are the new home invasions.
No one is 100% safe from cyber attacks. Many companies are breached every year. It is the way of the tech age.
Take your personal steps to protect yourself and monitor your own identity as well. Education and prevention is a step we can all make in fighting the war on cyber crimes.
*there
*I understand that there are …*
I’ve been following this and am just amazed by the recent news – Anthem is refusing an audit by the OIG. It’s the second time they refused, and from what I understand, it could only help them. There is a class action website set up to follow the developments. I think it is by a firm in PA – Goldman Scarlato. Really unbelievable.
When you’re in trouble, the only thing that helps you is keeping your mouth shut and stonewalling.