Last week, Allentown, Pa. based point-of-sale (POS) maker Harbortouch disclosed that a breach involving “a small number” of its restaurant and bar customers were impacted by malicious software that allowed thieves to siphon customer card data from affected merchants. KrebsOnSecurity has recently heard from a major U.S. card issuer that says the company is radically downplaying the scope of the breach, and that the compromise appears to have impacted more than 4,200 Harbortouch customers nationwide.
 In the weeks leading up to the Harbortouch disclosure, many sources in the financial industry speculated that there was possibly a breach at a credit card processing company. This suspicion usually arises whenever banks start feeling a great deal of card fraud pain that they can’t easily trace back to one specific merchant (for more on why POS vendor breaches are difficult to pin down, check out this post.
In the weeks leading up to the Harbortouch disclosure, many sources in the financial industry speculated that there was possibly a breach at a credit card processing company. This suspicion usually arises whenever banks start feeling a great deal of card fraud pain that they can’t easily trace back to one specific merchant (for more on why POS vendor breaches are difficult to pin down, check out this post.
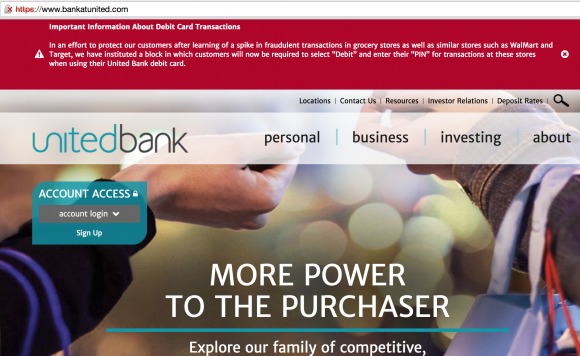
Some banks were so anxious about the unexplained fraud spikes as stolen cards were used to buy goods at big box stores that they instituted dramatic changes to the way they processed debit card transactions. Glastonbury, Ct. based United Bank recently included a red-backgrounded notice conspicuously at the top of their home page stating: “In an effort to protect our customers after learning of a spike in fraudulent transactions in grocery stores as well as similar stores such as WalMart and Target, we have instituted a block in which customers will now be required to select ‘Debit’ and enter their ‘PIN’ for transactions at these stores when using their United Bank debit card.”
In a statement released last week to KrebsOnSecurity, Harbortouch said it has “identified and contained an incident that affected a small percentage of our merchants.”
“The incident involved the installation of malware on certain point of sale (POS) systems,” Harbortouch said in a written statement. “The advanced malware was designed to avoid detection by the antivirus program running on the POS System. Within hours of detecting the incident, Harbortouch identified and removed the malware from affected systems. We have engaged Mandiant, a leading forensic investigator, to assist in our ongoing investigation.”
The company said the incident did not affect Harbortouch’s own network, nor was it the result of any vulnerability in the PA-DSS validated POS software.
“Harbortouch does not directly process or store cardholder data,” the company explained. “It is important to note that only a small percentage of our merchants were affected and over a relatively short period of time. We are working with the appropriate parties to notify the card issuing banks that were potentially impacted. Those banks can then conduct heightened monitoring of transactions to detect and prevent unauthorized charges. We are also coordinating our efforts with law enforcement to assist them in their investigation.”
However, according to sources at a top 10 card-issuing bank here in the United States that shared voluminous fraud data with this author on condition of anonymity, the breach extends to at least 4,200 stores that run Harbortouch’s point-of-sale software.
Reached for comment about this claim, Harbortouch reiterated that the malware incident impacted a small percentage of its merchants.
“It was nowhere near all of our customers, that is simply a false statement” said Nate Hirshberg, marketing director at Harbortouch, declining to answer questions about how many locations the company serves. “This malware incident impacted individual merchant locations, not Harbortouch. Harbortouch is not a processing platform, not a gateway and we do not store any cardholder data. This is not an ongoing incident and the malware was eliminated rapidly upon detection.”
One thing is for sure: POS providers — and their myriad customers — have a massive target on their backs, and there are almost certainly many other POS companies that are dealing with similar problems. Stay tuned for further updates.




Isn’t this actually more dangerous?
If you use your card as a debit card and key in your PIN to a malware infested POS, doesn’t the bad guy now get to drain your bank account via an ATM? Instead of him just buying stuff?
It depends on the bank and the amount you have in your account(s),
My bank, actually a S&L, has a $1000 daily withdrawal limit.
Also, I restricted ATM withdrawal to my checking account, with no “overdraft” coverage from my other accounts.
I believe that the PIN is encrypted at the PED in such a way that the merchant doesn’t even see it – I think it’s like end to end encryption basically. Anyone confirm? There are downsides to fraud on debit card side when it occurs, but specifically regarding losing your PIN, I don’t think it’s putting it at risk.
BUT – Any use of a Debit card puts you the consumer at risk of disruption if the number is lifted and used for fraud. It comes right out of your bank account and could disrupt payment of bills etc. Never use debit in anything other than an ATM, credit cards have better protection and if there is fraud you don’t have to worry while the bank and merchant figure it out, its not your problem, other thank checking your statement and reporting charges that aren’t yours.
It is true that debit PIN entry has been subject to a form of end-to-end encryption for a long time now… at least a decade if my memory serves.
Each debit PIN entered in the US is encrypted with a unique key per transaction. The decryption happens at the merchant’s processing bank and then the decrypted PIN is processed from that point to the cardholder’s issuing bank.
United Bank’s approach to shut down signature-based transactions on their debit cards is the correct one to take, in my opinion but it IS a radical solution. That alone would tell me that the breach is significant.
The ridiculous thing here is that the company seems to be saying (once again) – it wasn’t a flaw in our SOFTWARE – when the issue is that it was that the malware installed on the PC is able to do memory scraping.
These POS vendors that cater to small businesses really do have a large target on their backs. It is difficult for them to get small businesses to recognize the need to update equipment and security standards.
I’m not forgiving their handling of this if Brian’s reports are correct. They help NO ONE but the criminals by minimizing the scope in their public statements.
The problem is that a PIN is only 4 digits and each digit from range 0-9. Now, I understand it is encrypted and not hashed, so one cannot just brute force it without the key. But how secure is that key?
It’s line of defense is a strong and most importantly unknown key. So is it unique per card, unique per bank or unique per transaction? In the latter case how is the key generated and exchanged.
If I have to enter my debit PIN on an online transaction, I probably use a different card. (I wouldn’t use a debit card online anyway, but for the sake or argument.)
In order to brute force you need a way to know when you’ve guessed correctly.
If you submit 10^4 transactions to the bank, you better believe the card will get blocked after 5 or 6.
If they’re using symmetric encryption or properly-salted asymmetric encryption then an offline bruteforce needs to search a space much much larger than 10^4.
The real weakness here would be hacking the PED itself. Surely these things have firmware. Or can be man-in-the-middled.
That’s why I wrote “you cannot brute force it WITHOUT the key”. It is encrypted, not a hash. Also there is online and offline brute force. One doe snot always need to actually try a key to brute force it.
Hence my ask, how the key generation is. Is it unique or not? Unique per transaction, unique per bank, per card, per POS? Etc.
And if unique how is the key generated and exchanged.
Because the data is very short and very predictable, having weaknesses or non-uniqueness in keys allows for offline (!) attempts in getting the PIN decrypted.
The key is unique per terminal. It’ a Triple DES key and it’s not just a simple encryption of the PIN, it also involves the card number so that two cards with the same PIN will get different encrypted PIN values (called a PIN block). Google “ISO-0 PIN Block” and read the wikipedia entry.
I’m pretty sure they key is per terminal. I know it is per ATM and I think POS devices run the same way.
Thanks, that makes me feel safer 🙂
After reading into it, the key BTW is indeed per terminal, and depends typically on the cryptocraphic chip.
So in that case it looks all pretty safe indeed assuming the encryption takes place before it enters the main POS operating software (where it can be scraped). In the Target hack e.g. it did not, but I believe in many other POS it does.
EEVBlog got his hand on a PED and promptly tore it down, I can’t say how good or bad it is, but still an interesting thing to see how the hardware is secured:
https://www.youtube.com/watch?v=tCgtTPwlDSo
Today’s PED are tamper proof, meaning any sudden jolt/shake/etc. will wipe the encryption key from the PED. If the retailer has their systems setup you can no longer use that PED for debit as there would be no way to encrypt the PIN.
Current encryption standard for PEDs are DUKPUT TDES, though there are a few exceptions to this, mainly Automated Fueling Dispensers (AFD). Unless the AFD has been upgraded in the last few years it is most likely using DUKPUT SDES.
And anyone else notice the red and crossed out https for the bank’s website? Good for them trying to protect customers, but they really should fix that certificate error…
“If I have to enter my debit PIN on an online transaction, I probably use a different card. (I wouldn’t use a debit card online anyway, but for the sake or argument.)”
The story is talking about brick and mortar transactions…
Your PIN might be only 4 digits, doesn’t mean everyone’s is. Mine is 7 digits.
No, not in malware breaches. The PIN number is NEVER exposed to the retailer. The PIN is encrypted on the card, and the retailer’s device reads the encrypted PIN, and sends it to the bank still encrypted, and only the bank can decrypt the PIN number. The only time PINs get compromised is when skimmers are used and they are using an alternate method like a camera to capture the PIN number.
That said, you do lose all of the fraud benefits of the Visa / MC brand on the card when you use debit, and fraud resolution falls to bank policy, and in most cases, banks will not void a PIN transaction, because the PIN is essentially authenticating it as a valid transaction.
All that said, PINs ARE vulnerable. You should NEVER stick with a standard 4 digit PIN. It is fairly trivial for the hackers to crack 4 digit PINs if they capture enough of them, as they can compare “1234” to the encrypted version, say “adje” and anytime they see a PIN that is “adje” in encrypted format, they know it is 1234. (That is a VERY oversimplified explanation, but serves the point) Just always use a 6 digit or greater PIN, that is NOT a birthday or other info you can find easily online.
Also, as Brian has covered before, if your bank supports resetting your PIN by phone, especially using an automated system, they frequently will call in after finding your SSN, DOB, address, etc and try to reset it to something they then know. You should always request your bank to put a “lock” on your account that requires your PIN to ONLY be reset in a branch, or by being mailed to you.
> The PIN is encrypted on the card,
No it isn’t. The key-buttons aren’t on the card.
I think you mean encrypted on the “PIN Entry Device” (PED). But that can be hacked.
We issue VISA debit cards and VISA credit cards. The debit cards carry the same VISA protections as the credit cards, per VISA rules.
What does that mean in practice, Lynn? When a customer has their debit card stolen and their account gets cleaned out, you’ll probably put the money back. But what about when the customer also has hundreds of dollars of bounced check fees and other dings from third parties associated with not having sufficient funds to cover checks written? Do you also reimburse the customer that cost?
In response to Farkidoodle Doo, yes, but probably not significantly. If the POS is already infected, they’ve already got the entire magnetic stripe, and many places don’t require a PIN, especially for online transactions. My response has been to carry more cash, and minimize the use of my cards, especially at establishments where the employee walks away with your card. (Between my wife and I, we have had three cards skimmed, or otherwise had the whole magnetic stripe data stolen, and our bank blocked “card present” transactions, then replaced the cards.)
If the card is attached to your main bank account, yes, you run that risk.
However, for some years I keep the accounts that have cards attached separate from the main account (and never keep more than $100 on a card).
This way, even if that card is compromised, the damage is minimal.
And yes, it is a hassle to keep transferring small amounts to your debit card account, but it minimizes the risk.
I will be using cash at all small businesses and for all small transactions from now on. I just had to get a new credit card number due to $600 in unauthorized charges, which my bank covered. I used to use cash for everything but then my bank convinced me to get a cash back card.
Maybe they should allow cash discounts, put the cash back credit cards on a level playing field with regular cash.
Interference with the free market usually does Not work out all that well.
I don’t understand this mentality at all. What are you out of if you credit card number gets stolen? Nothing. What are you out if you lose the cash or get mugged? All of it.
With credit cards, the banks carry practically all the risk. Let them.
Also you’ll have to get to the ATM frequently which is also a risk. See Brian’s articles on ATM skimming …
I only use credit cards, and no debit or cash, exactly because of the risks.
Ridiculous. The last time I was robbed was 45 years ago, it is not something I have to think about. I don’t go to places that are risky. I go to a teller, get a few thousand in cash out and leave most of it at home, easy as pie.
I will still use a credit card at large retailers, for buying groceries, gas. But I will not be using a credit card for small purchases and at small retailers. The fewer people who have my number, the less chance I will have to go through the hassle of changing credit card numbers. And I will not be helping the thieves of the world get rich.
The situation is out of control and no one is going to magically fix it for us. Each person has to decide for themselves what they are going to do.
Being as anonymous as possible and lowering ones electronic footprint are probably a good ideas for everyone.
In my case, I make very few small transactions and very rarely buy at small retailers. It is no burden at all for me to pay cash for those and by doing that I will probably lower the number of retailers that have my credit card number by 1/3 or more.
Well, it is a hassle to have to get a new card and get it configured with all of the vendors that do automatic payment.
And then there is the question of identity theft. I don’t know the extent to which this is a legitimate concern for people who have had their credit card numbers stolen, but if it does, it can be a huge hassle to unwind.
And once place where I get gas gives me 5 cents/gallon off if I pay with cash.
QE & ZIRP is interfering with the ‘free market’ ie reducing the price of money to nothing. I’ve gone off-topic.
I use cash at merchants I visit infrequently, or wherever the amount spent is small (less than about $15). Credit cards at those where I visit repeatedly.
Cuts down on the chanches of encountering an infected system.
The only time a credit card of mine was compromised when, violating my rule, I used the card at Michaels for a $7 purchase (all my purchases at that store are below $15).
Edit:
Chanches should be chances
Since POS terminals are dedicated-purpose systems that should rarely have a need for new features to be added…
WHY ON EARTH are they not rapidly deploying binary whitelisting on these? I.e. nothing not on this approved list of md5 sums will run, or at least not without a UAC prompt or equivalent, and software images are loaded into read-only parts of their address spaces.
Same defense can be applied to anything that has a fixed purpose, rather than being a truly general-purpose computer for which whitelisting would be a straitjacket. Half the stuff the US Cyber Command is horrified about would be rendered safe: power grid control systems, process control at key industries (whitelisting there would have saved the Iranians some headaches when Stuxnet came calling), and so forth.
Of course, that last item probably shows why: whitelisting has not been encouraged, or even been actively discouraged, for reasons of so-called “national security”: the NSA’s ludicrous “we have to make it insecure to secure it” philosophy. What would have been the effect of broadly pushing the adoption of whitelisting? A lot fewer of these breaches and power grid folks able to sleep soundly at night, while MAYBE Iran gets the bomb. Which they then don’t dare use, since if they did, Tehran becomes a glowing crater within the following 20 minutes.
^ THIS, THIS, AND THIS!!!!!!!!!!!!!!
We actually just had our PCI Pentest completed last week by a VERY GOOD security company, and by properly segmenting our PCI network and requiring 2 factor authentication to access it, they were unable to break in, even after gaining domain admin access. Once I placed the tester inside the PCI network, it STILL didnt matter, because we have whitelisting on all registers and store servers. The result was he in no way could get card data, as the control servers for the whitelisting is also protected by 2FA. It is a PAIN to administer, but works like a charm. Not even obscurificated, custom powershell exploits could be run against the registers because of whitelisting.
But the answer as to why, is security team resources, and money. Most of these retailers dont have full security teams to administer such a PITA application to manage. And if you are midsized, you likely cant easily get the money to license every register / server with whitelisting. We only were able to extend it to our registers because our AV vendor added whitelisting to a new release, so we incurred no new content.
I also dont understand why applications that reset the machine to a base config at reboot arent used more (other than the cost / security resource issue). POS’s dont change frequently, and dont need persistent storage. Programs like deepfreeze / goback / etc are GREAT for this purpose, if malware does get in, it goes away with a reboot, and you schedule your POS’s to reboot nightly, or even better, you configure your POS app to force a reboot after an employee signs off (break, shift close, store close, etc) in the same way the computers at kinkos that customers use do.
I also have a hard time understanding how POS systems in general get hacked.
I mean, in gereal a system gets hacked (if one rules out physical access) in just three ways
1) system goes to internet resource that is compromised. E.g. your webbrowser. Should not apply to POS as it only needs to contact fixed and secure servers.
2) users downloads malware and installs it. E.g. fishing email. Should not apply to POS for obvious reasons.
3) system has open ports in the firewall to which the hacker can get into.
Since POS system typically have ports open for maintenance, I guess it is (3). Also some of Krebs articles suggests this is a common way of getting into POS systems.
But if I’m missing something I would love to be educated.
The reason I ask, is that it seems not awfull hard to lock a POS down and its main weakness is the software that allows remote access.
Don’t get me wrong, all those other things are very good as well, as they contain a breach, but I’m mostly puzzled on how they get infected in the first place.
What I have found is the POS system runs on the same network as all other devices the company owns. Look at Target for proof of this. Why is the POS system on the same network as a freezer? I would place good odds that on the fact the hackers gained access to a workstation first and then through exploration found the POS system just sitting there ready to be used.
> WHY ON EARTH are they not rapidly deploying binary whitelisting on these?
Because the hackers will simply add their malware to the whitelist after hacking the device.
Duh.
> Half the stuff the US Cyber Command is horrified about would be rendered safe: power grid control systems, process control at key industries (whitelisting there would have saved the Iranians some headaches when Stuxnet came calling), and so forth.
But then they wouldn’t have a justification for their gargantuan budget.
Whitelisting? I will ask again: “Why is this system on the public Internet in the first place?”. I don’t know the details, but I am sure there are myriad ways to prevent the bad guys’ access to the system at all, from VPN to private circuits to modem access only to firewalls, etc., etc.
the mag-stripe card business is effectively “pwned”. the best idea is to use cash.
i use a debit card online,- but,- as noted above: no over-draft protection / no line-of-credit. I put only the money i need to spend on the card and then spend it.
if they insist on automatic debits they get a gift card.
Something new, at least for me.
Was at Walmart last evening and the buyer credit card PIN Pad terminal was now asking me for the back of the credit card security code (this was for a credit card purchase). It was quite disconcerting – cause I don’t like putting that in the hands of our often compromised lowest bidder security retailers POS POS systems.
I can see the verification angle on this – but it also puts the verification code into the POS system when that is compromised.
Apparently Walmart has been upping their game:
http://thehill.com/policy/cybersecurity/240643-walmart-continually-tests-networks-post-target-breach
http://www.eweek.com/security/what-walmart-learned-from-the-target-data-breach.html
The Walmart Grocery by me has Ingenico terminals that look like they came from the first PCI-PED certifications. They have to have no more than 8MB of memory each. The best part of checking out is waiting for the transaction to be approved.
Application whitelisting is great, but remember you have to really secure that system or they just use it against you. If they discover whitelisting, they’ll likely white list whatever they need. At the point they’re into your CC systems you’ve probably been owned all over your environment, it’s a speed bump.
Add Eataly NYC to the list:
http://www.eataly.com/SecurityIncident
Whoops there goes another rubber tree plant!
This was informative. Btw, Binfer is a useful software for sending 100’s of pictures with a simple drag and drop. This is also a great photo sharing tool.
Nice comment spam there.
There’s no excuse for any merchant having those POS systems in the same segment as the rest of the network. The argument that it’s too expensive is hogwash. Yup, here comes the shameless plugs. I build firewalls using a small piece of hardware and Red Hat Fedora for pennies on the dollar versus the over-complicated vendor stuff. The whitelist can go right in the ruleset and the firewall can log and drop any traffic outside the whitelist. Simple and clean. All open source. Writeup right here:
http://www.infrasupport.com/security/firewalls/
And for those who still think security is somebody else’s problem, spend $15 and read this book:
http://www.bullseyebreach.com
– Grerg Scott
Thanks for your comment, Greg. What I have not seen asked or answered in any of the reporting concerning data breaches is “Why is this data on the public Internet in the first place?”. I don’t know the details, but I am sure there are myriad ways to prevent the bad guys’ access to the data at all, from VPN to private circuits to firewalls, etc., etc.
If the answer is “convenience”, then the data stewards need to look at the price of making it easy.
My gut tells me that most of the data does not need to be as “available” as it is and that the cost of isolating would be a fraction of the cost due to breaches.
Regards,
Thanks Stephen – Your gut is dead-bang right on. And it’s not even difficult or expensive to properly isolate those POS systems.
There’s no reason for all these breaches to continue to happen. I wonder how to get the attention of the POS vendors and their customers and show them how to make themselves safer?
Yeah, that’s self-serving, but let’s do something about this problem instead of wringing our hands about it.
– Greg
If you have an account at United Bank they are now forcing you to be at risk for card fraud by forcing you to do the transaction as a debit instead of credit. Find another bank or better yet a credit union. Don’t use a debit card for anything. If they won’t let you process as credit, there is no real benefit, just risk, all on you.
Although Harbortouch is basically saying “not my fault” “we don’t store or process payment card data”, there’s no indication of how this happened with all these merchants using Harbortouch. Was it due to the remote access they use log into these merchant’s site? Come on. There has to be a way all these merchants were hit and the commonality being Harbortouch. It’s ok to say we’re doing these things to be compliant (not storing data, etc.) but there is probably something else being done by Harbortouch that allowed their clients to be compromised.
Maybe I overlooked it in the article, but what is “PA-DSS validated POS softwdare”? (Asking about the “PA-DSS” bit, but “softwdare” is a typo.
PA-DSS = Payment Application Data Security Standard. It’s another standard document from the PCI consortium equivalent to PCI DSS, but for application packages rather than systems and networks.
Thanks for posting this rticle
interesting article they wrote about this very thing…
http://www.harbortouch.com/blog/protect-your-data/
Nice article Brian, please follow up when Harbortouch- et al, gets past the denial stage and offers more information.
You can always tell when marketing makes a statement. Would be nice to have the engineering comments.
I used to work for these people and the breach is split between the system owners and the company. the users tended to want the pos to be an free desktop pc and would hack the system so they could freely browse the web and disable the av to speed up the system or install random software that was never vetted for pci compliance. unfortunately the company tended to be cheap with securing the systems the entire deployed pos inventory is manually maintained and there is not enough staff to do normal tech support and do overnight security and software updates. remember most pos systems are running some form of windows xp embedded the few still getting updates are pos ready 2009 systems. the downside is windows xp has an very primitive compared to vista and 7’s uac. there unlikely to9 respond in the realistic point of view they have an high turnover of technical staff and the owner is having the management also running the two air fleets he owns.
Hmmm. Some misunderstanding by readers and misinformation by companies. First, this is the risk that POS companies put people at when they make card processing proprietary to their own processor. Second, Harbortouch POS does not necessarily store card data, that much is true, but the only company that you can process cards on a Harbortouch system through is HARBORTOUCH MERCHANT SERVICES. So what are they saying, “we didn’t leak your card data, that was our other division”? And if that is true, does that mean that the breach was not necessarily limited to POS customers and could also negatively impact Harbortouch clients that process on traditional terminals. Also, is there anything to the post warning customers. The bank posting is United Bank. The former name of Harbortouch was United Bank Card…. Seems a little fishy to me.
Hmmm. Some misunderstanding by readers and misinformation by companies. First, this is the risk that POS companies put people at when they make card processing proprietary to their own processor. Second, Harbortouch POS does not necessarily store card data, that much is true, but the only company that you can process cards on a Harbortouch system through is HARBORTOUCH MERCHANT SERVICES. So what are they saying, “we didn’t leak your card data, that was our other division”? And if that is true, does that mean that the breach was not necessarily limited to POS customers and could also negatively impact Harbortouch clients that process on traditional terminals. Also, is there anything to the post warning customers. The bank posting is United Bank. The former name of Harbortouch was United Bank Card…. Seems a little fishy to me.