Most of us know to keep our guard up when withdrawing cash from an ATM and to look for any signs that the machine may have been tampered with. But ATM fraud experts say they continue to see criminal innovations with “insert skimmers,” wafer-thin data theft devices that fit inside the ATM’s card acceptance slot and do not alter the outward appearance of a compromised cash machine.
The insert skimmer pictured below was recently pulled from an ATM in Europe. According to a report by the European ATM Security Team (EAST), this type of device is inserted through the card reader throat and then sits inside the card reader capturing the data of cards that are subsequently inserted.
Of course, an insert skimmer alone isn’t going to capture your PIN. For that, thieves typically rely on cleverly hidden tiny cameras. Often, the spy camera is tucked inside a false panel above or directly beside the PIN pad. But as I’ve noted in stories about skimming attacks that never touch the ATM (such as vestibule door skimmers), crooks often get very creative, hiding cameras behind things like convex mirrors — or even phony fire alarms.
The image below was captured last year by a U.S.-based bank’s own ATM security camera. It shows a skimmer scammer getting ready to install a tiny camera hidden inside of a fake fire alarm.

Hidden cameras made to work in tandem with skimming devices need not be hidden on the compromised ATM itself.
Broken record alert: Consumers can foil the vast majority of skimming attacks merely by covering the PIN pad with their hand when entering their PIN: That way, even if the thieves somehow skim your card, there is less chance that they will be able to snag your PIN as well. You’d be amazed at how many people fail to take this basic precaution. Yes, there is still a chance that thieves could use a PIN-pad overlay device to capture your PIN, but in my experience these are far less common than hidden cameras (and quite a bit more costly for thieves who aren’t making their own skimmers).
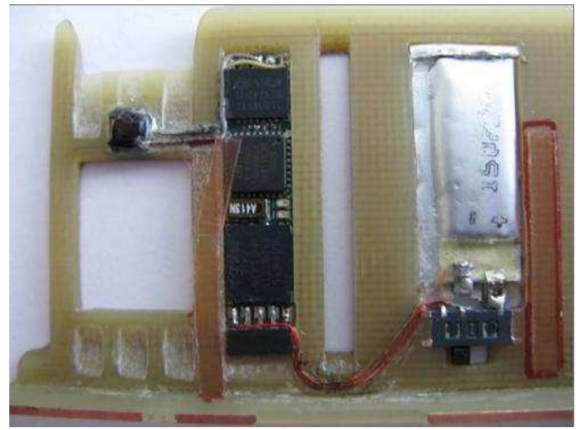
I also wanted to share an update on a relatively new form of skimming that I first wrote about in November 2014 known as “ATM wiretapping” attacks. These schemes involve a so-called “wiretapping” device that is inserted through a tiny hole cut in the cash machine’s front. The hole is covered up by a fake decal, and the thieves then use custom-made equipment to attach the device to ATM’s internal card reader.

ATM wiretapping thieves cut a hole in vertical face of the ATM to the left of the card reader facing the screen. Source: EAST.
According to EAST, six countries reported ATM wiretapping attacks. “Typically such devices have been installed through holes drilled (or melted) below or to the right of the card reader entry throat,” EAST notes. We can see the hole drilled by the thieves in the attack on the ATM pictured above, which was covered up by the phony decal shown here removed and resting to the right of the PIN pad:
Finally, EAST’s report has an update on another type of ATM attack that is alarmingly more common these days: Those in which crooks use gas or solid explosives to blow cash machines to smithereens. Banks in at least 11 countries reported attacks on ATMs involving explosive gas, according to EAST’s latest report in July.

Some ATM makers are blowing up their own cash machines to figure out how to make them more resistant to explosive attacks.
“Two countries reported significant increases in such attacks, and another country reported extensive collateral damage to buildings and nearby ATMs,” EAST’s Lachlan Gunn wrote. “Two countries also reported attacks using solid explosives. One of them reported that criminals perpetrating explosive attacks (gas and solid) are getting more violent and are employing para-military type tactics and weapons.”
Such attacks are becoming so common that some ATM makers are actually blowing up their own cash machines in test environments to see how they can be hardened with countermeasures. The image to the right shows the aftermath of one such test.
Fortunately, I’m not aware of any reports yet of paramilitary hoodlums lobbing grenades or blasting bazookas at U.S.-based ATMs…yet.
On that note, as this and other insert skimmer attacks show, it’s getting tougher to spot ATM skimming devices: It’s best to focus instead on protecting your own physical security while at the cash machine. If you visit an ATM that looks strange, tampered with, or out of place, try to find another ATM. Use only machines in public, well-lit areas, and avoid ATMs in secluded spots. Also, if you have the choice between using a free-standing ATM and one that is located inside of or attached to a bank, the latter is usually a safer bet.
Further reading:
Stealthy, Razor Thin ATM Insert Skimmers
The Rise of Thin, Mini and Insert Skimmers




Would showing a picture of the front of the ATM on the screen itself (mooted, but never seen) have stopped any of these sorts of attacks?
Yes, and some European banks have been doing that. The problem however is that it requires keeping the software (that displays the picture) and outer hardware up to date and in sync. Plus dat the same internal ATM equipment is often used with multiple ‘outsides’. In essence, increases cost and hence is often not done.
I’m sure this is not a new suggestion, but I wonder why ATMs haven’t adopted on-screen keyboards which rearrange themselves after each keystroke. This certainly raises useability issues, but would foil any attack from getting the PIN unless the camera has a very good view of the screen, which might itself be thwarted by the ATM’s own screen to prevent onlookers from observing the screen contents.
The problem with the keyboard on the screen is the ADA laws for the blind. It is hard to tell a blind person where the keys are on the touchscreen. Also I wrote a paper about detecting the XY position of the screen touches and showed that the PIN could be captured even when randomly placed on displays.
ATM keyboards are a true marvel of technology, they do all the encryption right on the keyboard and there is no way to tap into them . Try to open them and pooh goes the encryption keys and it would never receive a Des 3 key , it will have to be destroyed. With that in mind I don’t know how you can use screen as keyboard and also maintain integrity of data. Hope this explanation helped.
Brian you need to post an FAQ on what to do if you think you have encountered a skimmer. I’ve found it freaks out gas station attendants if you walk in and complain your card didn’t read and then tell them their gas pump looks like it has a skimmer installed.
I can just imagine what a bank branch manager would do if you walked in and accused them of having skimmers…
In actuality, this isn’t an infrequent occurrence.
Our tellers are required to physically check their ATM machines each morning prior to branch opening. Any alterations (or suspected alterations) are cause for immediately closing the machine down, and notify me — the CSO.
Skimming is not as prevalent at banks as it is at other less monitored and secure ATMs. Kiosks, gas stations, mom-and-pop stores, etc., get hit far more frequently since (a) the machine is usually not in constant view, and (b) most banks have procedures (and video surveillance) set up to monitor for and attempt to thwart such attempts.
Right about making the tellers or other staff check the ATMs to see if there have been attached a skimming device. But it is important, that the checks are not done with a regular cycle – the checks have to be random.
If skimming equipment has been attached then the best thing to do is to notify the police and have them set up a surveillance of the ATM. This way you have a chance of apprehending the crooks. You should only close the machine if the police are not able to set up surveillance.
If you close the machine, the crooks will most likely try to reclaim their equipment. The crook are often nearby and keeping an eye on the ATM, and they will know right away, that the machine has been closed.
Asking the teller or other staff to remove the skimming devices is not the best choice – because they can easily ruin fingerprints or DNA that can be used afterwards. Therefore ask the police to remove the equipment.
It is also important to consider the personal safety of the teller if you tell them to remove the skimming device.
So if the police is not able to help you right away you should close the ATM, but the sensible choice would often bee to let the crooks reclaim the skimming device and get away. The best thing you can do in this case is to make keen observation about the number of bad guys, the kind a car or truck that they drive etc.
Why did the you assume tellers were told to remove the skimmers? Nowhere did he say that. He just said if a skimming device was found that they ere to close the ATM.
“… immediately closing the machine down …” means disabling customer access to the services provided by the machine, and should include putting a sign over the entire machine front saying it is out of service and blocking the card insert location.
Normal for our bank also. ATM are checked every morning. Footage is reviewed for every alarm that goes off (not going to explain) I check my gas pump every time. I also don’t use ATMs, I keep enough cash. At ATM is more likely to get robbed than myself.
As I was reading this article, I was wondering how often bank tellers check ATMs for skimmers. This is reassuring to know that that is an everyday protocol. I will for be more aware when using my credit card at the gas pump, as well.
Been there, done that.
Used an ATM that I hadn’t used in several months. Looked the same, but “different” somehow. Pin pad was so stiff I was concerned that I was typing on an overlay. Concluded that the bank must have replaced the machine with a new one since I had last used it, but obviously I couldn’t be sure. Lacking anything else to go on, I completed the transaction.
After returning home, however, I got really worried. So I called the bank’s after-hours security hotline. Expected the agent would simply say: “Oh yes, we replaced that machine on such-and-such a date. No cause for alarm.”
Nope. She went into full-on, scramble the jets mode. Cancelled my card and locked my account. Asked a bunch of questions about prior transactions, and what it was about the ATM that made me suspicious. THEN she told me to call the local city police RIGHT AWAY and ask them to go check it out!
Which I did… reluctantly. The desk sergeant thought it was the funniest story he’d heard in months… until I told him that the BANK told me to do it. Then he got very official, and asked a boatload of questions, including several that seemed designed to assure him that I wasn’t trying to perpetrate a hoax on the bank… or the police.
Bottom line: I wasted a LOT of time on the phone with the bank and the police. I lost the use of my card and checking acct for over a week. And when I eventually called the bank to re-activate everything, NO ONE was willing to tell me ANYTHING about the incident.
A LOT of fuss and bother for NOTHING. Won’t try THAT again soon. In future, if I ever have any doubts, I’ll just go find another ATM. And leave the “detecting” to the bank staff!
Where was this ATM located?
In a bank-controlled separate building near the bank?
In a grocery store or a convenience store or a bar or some other non-bank business?
Or was it a stand-alone in a parking lot or near a sidewalk nowhere near a bank?
Small bank-controlled lobby (2 ATMs) with separate entrance adjacent to main bank entrance. On busy street in central part of Cambridge, MA.
Perhaps just calling the bank to replace your card as lost or stolen would be easier. Personally, I’d do just what you did, or nobody will keep up with the crooks in these cases. You should be proud that you helped gather data on such incidents. Otherwise you simply let the crooks move on to another day of ripping other people off!
What has happened to personal responsibility and a sense of public duty?
Need to remove the interface entirely and transfer the task to a smartphone.
Load bank app. Authenticate into app from trusted device. Signal to bank your location and request for funds from list of available ATMs. Send cypted key to ATM. ATM decypts with private key. Enter desired funds on smartphone. Confirm on Phone with biometric. ATM depenses money.
Keeping the interface on the ATM is a 1970’s design construct that has long outlived its value as have fuel dispensers and any kiosk design that requires you insert plastic or currency. Not an overnight, but living in a world of plastic invites innovations as these. Say goodbye to plastic! NFC has a smilar impact, but still holds some RAM scraping risk locally.
Right. And completely disenfranchise a large segment of the population of older Americans who neither HAVE a smart phone, nor WANT one, for ANY of a number of valid reasons, not the least of which is COST.
You’re right Esther. Also, let’s stop encouraging Windows XP and IE6 users from migrating to newer versions of their software. This disenfranchises a large segment of corporate and small-business America who neither HAVE software that supports newer versions of Windows, nor WANT those, for ANY of a number of valid reasons, not the least of which is COST.
Obviously, RSS is right here. Security improvements should not be delayed because of cost or “older population”. This doesn’t mean that it is not necessary to provide accessible help and guidance to all end-users that are affected by any new measures.
You clearly have not dealt with an aging parent or grandparent yet. My 85 year old mother-in-law is never going to learn to use a smartphone. Her regular cell phone is challenge enough. But she still needs to use the ATM and is perfectly capable of doing so.
It’s not the same as sticking with XP. That’s stupidity. But changes in cognitive function with age is not stupidity, it’s just reality, even for the most with-it old people.
I’d just like the ability to opt in for more security to use, say, two factor security and a feature like positive pay (basically, if I write a check, I enter it into a banking web page or write/send the check from their web page.)
This would let people who aren’t technically adept keep the systems they know and love. Unfortunately, older people are already so much more likely to be targeted for scams, and that would probably even make it worse.
Smartphones are walking surveillance devices, which is why I refuse to use one. I should not be penalized for not wanting to help criminals, peeping toms and gov’ts spy on people.
You would have to be real delusional to think your phone is secure. Even the NSA has begged us not to use them in the past when they came out with their fishbowl recommendations that noone took seriously. They are a joke. I kind of laugh at the arrogant security professionals who think “noone gets targeted” but locking down their computers like fortnox, at the same time they are walking around with smartphones lmao.
Seriously ridiculous post, advocating the lowest common denominator. Change with technology or get left behind. I know plenty of people in their 80s who have not only have smartphones, but use them for banking, facebook, and twitter. Don’t be an ageist.
Why don’t you just die early?
Yup.. there ya go.. put all that financial stuff on your hand-held computer.. why? ’cause it’s conveeeeeeeeenient…. sooooooooooo when the person drops the phone, or happens to leave it at the local watering hole, or *GASP* has it stolen, all that good info is right there available for whomever to ‘go forth and multiply’ .. has all the faceplant and twiddle info.. contacts.. oh and that ap for doing wireless transactions by putting your phone next to the reader.. not to speak to all those checks that they took a pic of and deposited (nah, no info on that)…. ahhhh technology..
Nope! Dont need to steal it or wait for some fool to leave it on the table while he dances with wife, dont even need the honest mistake of leaving it at the airport, restaurant or even in that unattended convertible sitting out on the road in front of Mom&Dads Gated Community Home!
Just get me about 18-20 feet away and Ill be done in about 40 seconds, should pretty much have access to thier entire life if correct target is selected.
Matter of Proximity and Opportunity with a small touch of talent!! 😉
O! Wait! That cant be done!!! Just ask any honor roll teen! They know everything about Phones and Tablets and even a little about computers. Definitly know everything about Security and Risk in todays digital world!
Im in the wrong buisness for sure!!!!! 🙂
If I remember right, all the major phone systems are susiptable to security hacks. No matter the OS. Even more so then the common ATM. Any back door available to the nsa, or any government agency is available to the bad guys. How would you propose that security be done? The new special bank card? The key fob, the phone? Picture, special number? Every system , I repeat every system, connected, is hackable. One thing, I remember from an old security master, is for every good guy, there’s more then one bad guy. And they are just as smart, at not getting caught.
Another thing, xp, in its day, was the fastest OS around. Even in its end it was the fastest for startup, and required the least maintance. And with several universal free security programs, was the most secure. You could make it do anything, or make it stop from doing something. The newer systems including Linux and apple? No such luck. Xp you could sign in, do what you want now. No such luck afterward. All major systems since then, will check with home, update, verify this copy, report what’s on the machine, what programs were used, is that secure? That’s not what I use a machine for, bookkeeping, photos, games, yes..but to be delayed? To take control of a machine, until it decides that I am me? And where and why I want to use it? Or that the ram I added does not make this some new machine?
jim, your tin-foil hat seems crooked. To be the most effective, it needs to be on straight.
here is one of the “people don’t get targeted”, “we are only less secure because of advancements in technology” people.
We are less secure because more exploits are public and because noone gives a crap about defensive security anymore because offensive security is more fun! And we are especially insecure when most “security professionals” are always downplaying and preaching against using any security claiming something is fud….
Like John Mcafee always says, there is probably 10s of thousands of teenage girls getting spied on in the showers with their waterproof phones everyday. Its so dam easy to get a bad app put on google playlist or the apple store, or to just spoof someone elses contact with a bad sms message, which kevin mitnick loves demonstrating to people in the audience. The latest is backdoors and spyware being implaneted in the firmwares themselves now for companies. Which as jim says is great for the bad guys too!
The NSA themselves begged us all to stop using smartphones and to demand vendors to secure them when they came out with their fishbowl recommendations almost 5 years ago.. Thats how dangerous and serious it is and why they manufacture their own phones.
And now deal with jailbroken and compromised Smartphones such as the millions of Android phones which will never be updated by their carrier.
What’s the statistics of smart phone users compared to old style phone.
I can’t imagine my mum operating such a smart phone to retrieve money.
Your proposal is not simple enough for general acceptance.
Doesn’t make sense. What if I have a smartphone with no data plan? How about when I’ll need to use an ATM overseas? Would I have to buy a 50$ international data plan for this only? I don’t have biometrics on my smartphone and don’t want it. I don’t want MY biometric info to be stored on my lousy phone.
You clearly a narrowed view of ATM security. Hey! Let’s push it one notch down stupidity: Have the bank confirm with your Facebook friends that it’s really you trying to request funds…….
I am guessing that many of the unattended ATM machines will just end up going away.
Fit the ATMs with gas sensors – if it suddenly changes out of expected threshold, you know there’s a foreign gas present, and to trigger recording and silent alarm?
… or deliberately have a spark source running regularly so that there’s no opportunity for gas to build up to dangerous levels before being ignited … it takes them some time to fill the machine with gas to required level, no?
Route unencrypted data cables through solid metal channels away from edges of the machine? The wire tapping relies on being able to fish out the wires, splice them, and then put them back. Also, perhaps, including some wires within the bundle that are present for continuity/resistance check, and shielding the cables with continuity check on the shield also.
Place multiple light sensors in areas of machine where sensitive cabling is present but light is not expected?
Maintain positive pressure in sensitive areas of the case not requiring air cooling, and if pressure rapidly changes, trigger recording + alarm?
Place optical checks and physically moving portions within the card slot that are checked inbetween card insertions to ensure that there are no obstructions within the slot, kinda “cookie cutter” style? In slot skimmer would be hole punched :), or for a non destructive method, if resistance to moving portions is found, issue is flagged for review.
Ensure there’s only flush surfaces besides actual reader itself in card reader slot – no holes, pits etc. whilst mechanical sweeps at rest?
There are lots of things you *could* do, but not without refitting all of the ATM machines that are currently out there.
And we all know that the banks don’t want to pay for refits – just look at the sheer number of them that are still running XP.
yes another way to remote control of atm diebold software
ATM machine selection is also important. Some machines are more easily hacked because of location/traffic.
I frequently use ATM machines in my travels around Asia …. I avoid all ATM machines in low traffic areas as well as those that are accessible 24 hours .. My preference are ATM’s attached to banks that are inside shopping malls as the malls are closed at night .. and being attached to a bank provides some additional benefit in the event of a card failure .. you have someone to talk to.
In Ireland we’ve seen them ripped from walls using stolen equipment (including JCB diggers) from local building sites, then they put it in a van to work on from another location
IMO this will be more likely than explosives if this attack is to happen in the states
We are already seeing these, and have been for some time, just not with in-wall machines. Where I live (Major metro area) about once a week or so you see on the news someone that drives a truck into a closed store that has a small freestanding ATM, and they load it up / yank out of the ground / etc so they can get the entire machine and then go work on it elsewhere. Seems like this could easily be foiled with on-board GPS with a backup battery, but to my knowledge that isn’t done in these smaller, cheap ATMs that you see in gas stations here.
I doubt were going to see blown up ATM’s in the US, there are too many other ways to attack ATMs here that are less likely to get you caught.
Why not make pin numbers ‘memory only’ and mandatory? Or put tape over the pin and memorize it. If you forget the pin number you can pull the tape back and make a mental note of it then cover it again before inserting.
Huh?
Skimmers are found in Michigan
http://www.abc12.com/news/headlines/Skimmer-found-inside-gas-pump-in-Mundy-Township–323774181.html
Another machine found with skimming device in it.
http://www.live5news.com/story/29960245/skimming-device-found-on-atm-at-bank-of-america-in-west-ashley
The solution is quite simple. Use CASH. Keep any excess cash in a bank or savings firm. If traveling use some form of replaceable travelers checks. Recently even in closed down Greece travelers with American Express Travelers Checks could negotiate them for actual CASH at all American Express offices in Greece.
If you are in your home territory you should have a reasonable handle on how much spendable money you will normally need in any given week, or month. Take what you need, secure any amount you feel un-comfortable carrying on your person in your office safe or residence safe spot. Use a credit card or check (cheque?) drawn on your bank for any unexpected out-of-budget purchase.
When traveling within the United States I have had no difficulty in cashing a $500 check at my hotel desk when I found I was running a little short on spendable cash.
As an aside, I am going tomorrow to a regional Fall Harvest and Swap Meet. Thousands of People will attend. Farm Vehicles, Cars, Trucks, Chickens, Sheep, Goats, cows, vegetable from A to Z will all be offered. The event flyer says: “Cash Only, no vendor will accept Checks or Credit / ATM Cards.”
With what’s going on with the hacking and ATM skimming, the use of any ATM is only for the foolish.
10 years ago I tried to use American Express Travellers Checks in Italy. No one would take them, not even banks. My web search finds AMEX offices in Italy only in airports.
Cash? Then we go back to being held up in the street.
The solution is quite simple, yes. Just like the previous poster said. Just like using “cash” is local, and is a solution, so is…..
…being part of your local environment.
And correcting it.
Every skimmer gets inserted by someone who lives next to someone else. Maybe you. Maybe they live with you.
The LE and LEO’s are failing us now, but they can help.
We each need to have a zero-tolerance for people we know who break the law in any way.
And we need to seek out any stench of law breakers we smell. My brother, my mother. Behind bars.
The LE and LEO’s need to support our local contribution by locking these bitbag lumps of lazy excrement up – so when we find them and rat them out, we know we don’t need to worry about them coming back to our houses and burning us alive.
That’s local for you.
Don’t think this is some kind of global Internet problem just because computers are involved. It’s trash local.
Any thoughts?
The more I think about this, the more I wonder why a Consumer should care at all that their financial institutions are failing them (from a financial risk standpoint) with ineffective security mechanisms to protect the assets we pay them to protect.
If they cannot handle it then they should be liable for it. Not up to the consumer to do the Bank’s job or take their losses.
The banks do pay: customers are not liable for fraud from compromised cards. And in 95% of instances if the customer covers their hand as they enter their pin, the fraudster has to resort to F2F fraud spend rather than ATM withdrawals: riskier and a longer time period to deliver the same financial output.
Or banks could start using palmsecure from Fujitsu soon?
And you want us to go to a cashless society! I’ll save my two cents!