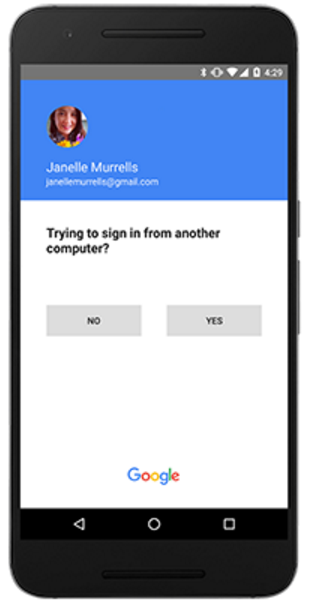
A recent ping from a reader reminded me that I’ve been meaning to blog about the security limitations of using cell phone text messages for two-factor authentication online. The reader’s daughter had received a text message claiming to be from Google, warning that her Gmail account had been locked because someone in India had tried to access her account. The young woman was advised to expect a 6-digit verification code to be sent to her and to reply to the scammer’s message with that code.
 Mark Cobb, a computer technician in Reno, Nev., said had his daughter fallen for the ruse, her Gmail account would indeed have been completely compromised, and she really would have been locked out of her account because the crooks would have changed her password straight away.
Mark Cobb, a computer technician in Reno, Nev., said had his daughter fallen for the ruse, her Gmail account would indeed have been completely compromised, and she really would have been locked out of her account because the crooks would have changed her password straight away.
Cobb’s daughter received the scam text message because she’d enabled 2-factor authentication on her Gmail account, selecting the option to have Google request that she enter a 6-digit code texted to her cell phone each time it detects a login from an unknown computer or location (in practice, the code is to be entered on the Gmail site, not sent in any kind of texted or emailed reply).
In this case, the thieves already had her password — most likely because she re-used it on some other site that got hacked. Cobb says he and his daughter believe her mobile number and password may have been exposed as part of the 2012 breach at LinkedIn.
In any case, the crooks were priming her to expect a code and to repeat it back to them because that code was the only thing standing in the way of their seizing control over her account. And they could control when Google would send the code to her phone because Google would do this as soon as they tried to log in using her username and password. Indeed, the timing aspect of this attack helps make it more believable to the target.
This is a fairly clever — if not novel — attack, and it’s one I’d wager would likely fool a decent percentage of users who have enabled text messages as a form of two-factor authentication. Certainly, text messaging is far from the strongest form of 2-factor authentication, but it is better than allowing a login with nothing more than a username and password, as this scam illustrates.
Nevertheless, text messaging codes to users isn’t the safest way to do two-factor authentication, even if some entities — like the U.S. Social Security Administration and Sony’s Playstation network — are just getting around to offering two-factor via SMS.
But don’t take my word for it. That’s according to the National Institute of Standards and Technology (NIST), which recently issued new proposed digital authentication guidelines urging organizations to favor other forms of two-factor — such as time-base one-time passwords generated by mobile apps — over text messaging. By the way, NIST is seeking feedback on these recommendations.
If anyone’s interested, Sophos’s Naked Security blog has a very readable breakdown of what’s new in the NIST guidelines. Among my favorite highlights is this broad directive: Favor the user.
“To begin with, make your password policies user friendly and put the burden on the verifier when possible,” Sophos’s Chester Wisniewski writes. “In other words, we need to stop asking users to do things that aren’t actually improving security.” Like expiring passwords and making users change them frequently, for example.
Okay, so the geeks-in-chief are saying it’s time to move away from texting as a form of 2-factor authentication. And, of course, they’re right, because text messages are a lot like email, in that it’s difficult to tell who really sent the message, and the message itself is sent in plain text — i.e. is readable by anyone who happens to be lurking in the middle.
But security experts and many technology enthusiasts have a tendency to think that everyone should see the world through the lens of security, whereas most mere mortal users just want to get on with their lives and are perfectly content to use the same password across multiple sites — regardless of how many times they’re told not to do so.
Indeed, while many more companies now offer some form of two-factor authentication than did two or three years ago — consumer adoption of this core security feature remains seriously lacking. For example, the head of security at Dropbox recently told KrebsOnSecurity that less than one percent of its user base of 500 million registered users had chosen to turn on 2-factor authentication for their accounts. And Dropbox isn’t exactly a Johnny-come-lately to the 2-factor party: It has been offering 2-factor logins for a full four years now.
I doubt Dropbox is somehow an aberration in this regard, and it seems likely that other services also suffer from single-digit two-factor adoption rates. But if more consumers haven’t enabled two-factor options, it’s probably because a) it’s still optional and b) it still demands too much caring and understanding from the user about what’s going on and how these security systems can be subverted.
Personally, I favor app-based time-based one-time password (TOTP) systems like Google Authenticator, which continuously auto-generates a unique code via a mobile-based app.
Google recently went a step further along the lines of where I’d like to see two-factor headed across the board, by debuting a new “push” authentication system that generates a prompt on the user’s mobile device that users need to tap to approve login requests. This is very similar to another push-based two-factor system I’ve long used and trusted — from Duo Security [full disclosure: Duo is an advertiser on this site].
For a comprehensive breakdown of which online services offer two-factor authentication and of what type, check out twofactorauth.org. And bear in mind that even if text-based authentication is all that’s offered, that’s still better than nothing. What’s more, it’s still probably more security than the majority of the planet has protecting their accounts.




In the context of the young woman’s scenario, Push to Accept might actually have proven to be less work for the scammer.
Research done by scientists from Brigham Young University, the University of Pittsburgh, and Google using an MRI measured a human brain’s dramatic drop in attention that results when a user is shown just two security warnings in a short period of time. The official term for this effect is called “Habituation”. What this means is if a bad actor triggers a few Push To Accept requests, in a short period of time, a user will likely not read the prompt and blindly click accept to dismiss the dialog.
This effect has been noted by David Kennedy of TrustedSec at his DefCon presentation. He discusses how, when performing Pen Tests for customer, users always tapped allow granting him access. That is to say in every Pen Test engagement where Push to Accept was deployed he was always able to gain access. To quote Mr. Kennedy “not good”.
From the scammers perspective SMS is actually the harder method as it requires social engineering where as Push just requires triggering a few login attempts to overwhelm the user.
Very good point Ryan.
Another thing, I don’t particularly like giving my mobile number out to many of these companies – as it will likely get stolen and sold at some point based on the recent past history of nearly any company on the internet.
So I only have 2FA enabled for important accounts (Google etc.) where I deem the risk is worth it. JMHO…
Sasparilla
In reality, your phone number is already out there, or will be soon. There are many databases with a disturbing amount of information available publicly. Passwords are simply not secure and 2F is a must to ensure the integrity of the accounts you use on the modern web. The pros outweigh the cons, imho.
Some things you should do in regards to your mobile phone.
1)ALWAYS lock your device (e.g. fingerprint, passcode, etc.) so someone can’t pick up your phone and start accessing your sensitive apps.
2) Register your mobile number with the FTC do not call list to avoid marketing calls https://www.donotcall.gov/
3) Call your mobile provider and put a security code on your account so changes can’t be made without your knowledge. Otherwise an intruder can just take ownership of your mobile account and accept the 2F requests.
Regards
I don’t use two-factor authentication that relies on my phone for one major reason: what happens when my phone isn’t available?
Lost, stolen, left at home – all are valid reasons why I don’t have my phone available at all times.
Instead, I use unique passwords at all important web sites and services.
In the case of Google’s 2FA, you have the option of printing out a list of single-use codes you can carry around, and which can be used if your phone is not available.
Different passwords is great, but you sure are brave to assume that if one of the sites you use gets hacked and credentials are compromised, that the site will report it in time for you to change it before the hackers use it. Maybe for most sites it doesn’t matter with different passwords, but I wouldn’t take that chance on banking, facebook, linkedin, etc. Too many breaches lately that are being reported months or years after the incident.
Not mentioned above is that Apple’s 2FA does not use SMS. Apple sends an authorization code to any one of several iOS devices (you select which one at the time you try to log in). The authorization code appears in a dialog message, direct from the operating system. It’s very quick and easy. Gives me a warm feeling every time I use it.
Apple’s 2FA does not use SMS – you’re right. But it does use SMS for the initial setup.
I’ve thought about this more than a few times to see how this – admittedly small – vulnerability can be reduced. But so far all my theories are no better – dang.
I do give credit to Apple for setting this up as well as they have.
It is worthy of note that it does NOT require a cell connection – WiFi works just fine, as I discovered recently while in Europe with WiFi+Ethernet but no cell connectivity. “It just works” and works well.
amazon allows you to use apps like google auth but uses sms 2fs as backup, how stupid is that?
It is not stupid at all. You will realize that once you lose your phone. 🙂
In case you have backup SMS, you can attach the new phone and app in minutes to your account. In case you don’t have SMS, you’ll be sending in real paperwork like coppies of your ID and more stuff to some P.O. Box in Seattle hoping they’ll activate your account.
From a purely technical point of view, I am a fan of U2F, and my Yubikey supports this. And for that matter, so does Google.
But if less than one percent of the users even turn on SMS based 2FA, I can’t see that anything better than this ever becoming widespread.
Another nice property of U2F is that if a scammer site tricks the user into clicking the button on the U2F device … nothing happens!
The U2F token is encrypted in a way that only works for the original site. Anyway, something like U2F is the future: it’s device with one button, and it does not rely on the user to be careful.
Another more insidious variant of this attack is to “prime” the victim with a message indicating that the authentication code is to confirm that a “fraudulent” login attempt is “fraudulent”.
The underlying challenge for all of us in InfoSec is that now we’ve separated authentication from authorization (and “confirm something I sent you” is clearly the latter, not the former), are we truly combining them into a meaningful access control security benefit/risk mitigation?
Authentication is not Authorization. And something I send you is not something you have.
“… now we’ve separated authentication from authorization (and “confirm something I sent you” is clearly the latter, not the former), are we truly combining them into a meaningful access control security benefit/risk mitigation?”
Not only “separated authorization from the authentication system”; but, as the “have Google request to enter a 6-digit code texted to a cell phone each time it detects a login from an unknown computer or location” method shows, it’s sending authorization to another medium (telephones) as the final way to access to the “password sytem”/authorization system from outside that system.
Before you call low adoption numbers a security disaster, be sure that the accounts going unprotected are actually important, and that the security was for the benefit of the end-user and not the service provider. Paywalls like Elsevier are an example of that.
Yes, I have a dropbox account. It’s got some old pictures in it that were long ago pasted to facebook and are in fact public.
It is one of many “infrequent use” accounts I have…I’ll bet even Mr Krebs doesn’t bother with 2FA (or possibly even a strong password) on his short-term, single-use accounts, like ones used deliberately for spam magnets.
Hi all,
Using the mobile device to either use things like Google Authenticator or 2FA assumes:
1) Safety of the device that it does not get into the wrong hand
2) The device has password/pin protection – this can be a pain in the neck in using the device
3) Using 2FA always assume continuity of mobile services and this is not always possible. Certainly a lot of travelers loath using roaming service just for that and many switch out their SIM to use local SIM. There are also many users using dual SIM devices and they switch their SIM daily. Hence one needs to switch the 2FA destination.
I have watched the 2FA movement from day one and I believe many 2FA advocates made the wrong assumption (see point 3) and that leads to a lot of problem with SSA’s demanding 2FA on sign on. It is fine for geeky people but for many ordinary users, this is too much for them.
Also 2FA is a pain in the neck for mail programs such as Thunderbird or Outlook and not everyone uses web view access.
Jack
Many 2FA options are offline. E.g. the apps do not require network to work, but also various banking dongles exist that work 100% offline. SMS and voice as 2FA obviously are not, but email is also often possible as 2FA option and if you are online, and hence accessing the service that needs 2FA, you can also use that in addition to the app or a dongle.
Note also that most email services that require 2FA, have an solution for offline clients as Outlook or Thunderbird: app passwords (special passwords only usable on that device and only for limited use) or to mark your home PC as trusted device that does not require 2FA.
2FA using text/SMS messages might actually be more secure than Google authenticator.
Google provide a single point of breach/failure while text/SMS usually involves many.
Too many services and companies rely on Google nowadays and most of the phishing campaigns are targetting this. Clever by design it might not be the best secure way to do it.
The app does not rely on Google at all. It is made by Google, but does not communicate with their servers *ever*. It is an open algorithm, that just happens to be used by Google.
But also for instance by Apple and Microsoft. Microsoft also provided an app, which does the same. And hence you can mix and match. Use Microsoft’s app to log in at Google and visa versa.
You are right about a singele point of failure. Lose the phone and you cannot access your account because you don’t have the app. But you need the app to update your account to your new phone …
With SMS you just get a new SIM and phone and your are back in business.
More points of failure usually means a larger attack surface, and thus an INCREASED risk. So that does not make SMS more secure.
Besides that Peter explained why you’re wrong about Google being a weak point.
Peter: The “Google app” is not a “single point of failure” in the way you write.
To setup one of these apps to authenticate for a particular account you get a code (usually a QR code you scan). You can simply securely backup these codes for your accounts (on a hardware encrypted USB stick or something like that).
If you lose your app for whatever reason you can just initialise another app to grant access to your accounts, at which point it’s just as easy to replace the app as a SIM is. Except you don’t have to wait for a new SIM to arrive, you can use any other device such an app runs on in the meanwhile. The site you’re logging into won’t even know you switched apps 🙂
Hey Krebs,
Keen for you to have a look at our TFA that blocks phishing like the SMS TOTP’s.
and that includes push verification?
and thats single tap? (ie fast)
I think a “Krebs” clear outline of what out there and what the real pros and cons are would be great :)!!
also re yubikey, i can’t seem to find the port on my ipad for a usb……
Using SMS for password reset / recovery is risky. Considering SS7 SMS interception attacks work. Affected are twitter, google (to some degree only), facebook, Microsoft, ebay (or course only if the phone number has been provided before for a potential recovery/reset).
Readers:
We need to remember how insecure the mobile phone infrastructure is.
The Signaling System #7 (SS7) system vulnerabilities are in the news every few months. Nothing is done about it.
It was easy for Chaos Computer Club, and 60-Minutes to hack a US Congressman.
http://arstechnica.com/security/2016/04/how-hackers-eavesdropped-on-a-us-congressman-using-only-his-phone-number/
https://www.youtube.com/watch?v=O4tUx1W3zLc
Many other references are easily found…
How about voice recognition as 2nd factor – ask person to say their name.
I haven’t seen a discussion here about SMS 2FA and the effects of unified messaging services, which some carriers are pushing themselves.
These are services that allow you to access your SMS messages across multiple devices. For example, Verizon’s Message+ app works on phones and tablets and has a desktop version as well as a web version. In addition to Verizon, there are 3rd party services that offer to consolidate your SMS messaging for access across multiple devices, including e-mail.
Once your SMS is spread across multiple devices, the security of 2FA by SMS is compromised by the least secure access point – whether that’s a tablet with no login password or your web login for your cell phone account. We’ve all read here and elsewhere how easy it is to socially engineer your way passed the customer support to get into an online account. What good is my bank’s 2FA if Verizon is the weak point?
Unified messaging services pretty much do away with the “something you have” idea of 2FA. You might “have” your physical devices (phone, tablet, desktop, etc.), but you don’t “have” your web or email account in any physical sense.
I can confirm Dropbox is not unique. I had a tech call with Apple over some minor iTunes issue or something, and the tech wanted to connect to my machine to see what I was trying to do. When he went to set up the connection, he said, “Oh, wait. That’s not going to work.” I asked why not? He said, “Well you have 2FA on, so the procedure is different and I haven’t run into it before.” I asked him how long he’d been an Apple tech. “18 months,” he said.
So, in 18 months, I was the first person he’d spoken to who was using 2FA.
BTW, the procedure wasn’t a big deal, and he was able to connect to my machine, it just involved a different step.
I just wish that sites would ALL allow the creation of a unique username. I HATE the fact that since 80-90+ percent of the sites out there want you to use an email address for the username.
REALLY? You want me to just GIVE HALF of my login information to thieves just because you are too lazy or ignorant to add one field to your database for a unique username?
Do this and a LOT of scamming would screech to a halt since they COULD NOT likely reuse the username/password combo around as much and as easily when they already know someone’s email address.
(Yes I know someone might just use the same username, but at least that would be their choice, not forced on them like it is now so often.)
>>I just wish that sites would ALL allow the creation of a unique username.<<
Many services are trying to limit how many accounts a single user can have, and this is one method they've chosen for convenience.
Mind you, many people today can create multiple email addresses, but that fact hasn't done much to change the mindset of developers.
-ASB: http://XeeMe.com/AndrewBaker
I believe that SMS based two factor authentication is something of a stopgap technology that has served its purpose and can be relegated to the pages of history in the era of smart devices. Authenticator apps provide a superior approach yet the friction they introduce in the authentication process keeps the adoption figures low.
Few friends at AppsPicket are using a fresh approach to solve the 2FA problem that uses cryptography to check both factors and remove friction for the end user.
I use 2Factor for my gmail account and the only time it really bit me was when my phone’s touchscreen was acting up and had to be repaired. Made it hard to troubleshoot since I couldn’t access email until I swapped SIMs into my backup phone. My web browser is always set to clear cache so the “remember username” never works on any website for me. Even so, I’m glad I still have it turned on.
What I wish more websites and systems would move towards is the ability to use LONGER passwords instead of complex ones, so we can use a LONG passphrase (32chars+) vs having to create a complex one each time. I think Krebs has even covered the advantages of longer passwords vs complex. I wonder what effect it really has on the back-end for the storage of long hashed passwords. Does it really use up that much more space or CPU processing?