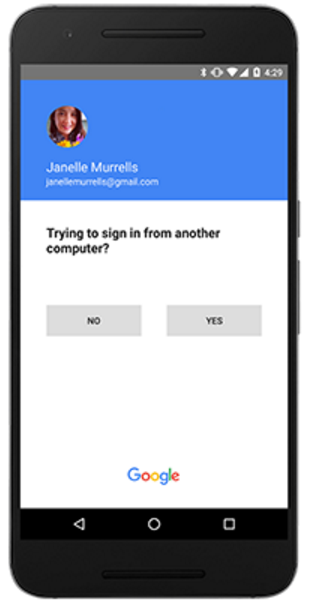
A recent ping from a reader reminded me that I’ve been meaning to blog about the security limitations of using cell phone text messages for two-factor authentication online. The reader’s daughter had received a text message claiming to be from Google, warning that her Gmail account had been locked because someone in India had tried to access her account. The young woman was advised to expect a 6-digit verification code to be sent to her and to reply to the scammer’s message with that code.
 Mark Cobb, a computer technician in Reno, Nev., said had his daughter fallen for the ruse, her Gmail account would indeed have been completely compromised, and she really would have been locked out of her account because the crooks would have changed her password straight away.
Mark Cobb, a computer technician in Reno, Nev., said had his daughter fallen for the ruse, her Gmail account would indeed have been completely compromised, and she really would have been locked out of her account because the crooks would have changed her password straight away.
Cobb’s daughter received the scam text message because she’d enabled 2-factor authentication on her Gmail account, selecting the option to have Google request that she enter a 6-digit code texted to her cell phone each time it detects a login from an unknown computer or location (in practice, the code is to be entered on the Gmail site, not sent in any kind of texted or emailed reply).
In this case, the thieves already had her password — most likely because she re-used it on some other site that got hacked. Cobb says he and his daughter believe her mobile number and password may have been exposed as part of the 2012 breach at LinkedIn.
In any case, the crooks were priming her to expect a code and to repeat it back to them because that code was the only thing standing in the way of their seizing control over her account. And they could control when Google would send the code to her phone because Google would do this as soon as they tried to log in using her username and password. Indeed, the timing aspect of this attack helps make it more believable to the target.
This is a fairly clever — if not novel — attack, and it’s one I’d wager would likely fool a decent percentage of users who have enabled text messages as a form of two-factor authentication. Certainly, text messaging is far from the strongest form of 2-factor authentication, but it is better than allowing a login with nothing more than a username and password, as this scam illustrates.
Nevertheless, text messaging codes to users isn’t the safest way to do two-factor authentication, even if some entities — like the U.S. Social Security Administration and Sony’s Playstation network — are just getting around to offering two-factor via SMS.
But don’t take my word for it. That’s according to the National Institute of Standards and Technology (NIST), which recently issued new proposed digital authentication guidelines urging organizations to favor other forms of two-factor — such as time-base one-time passwords generated by mobile apps — over text messaging. By the way, NIST is seeking feedback on these recommendations.
If anyone’s interested, Sophos’s Naked Security blog has a very readable breakdown of what’s new in the NIST guidelines. Among my favorite highlights is this broad directive: Favor the user.
“To begin with, make your password policies user friendly and put the burden on the verifier when possible,” Sophos’s Chester Wisniewski writes. “In other words, we need to stop asking users to do things that aren’t actually improving security.” Like expiring passwords and making users change them frequently, for example.
Okay, so the geeks-in-chief are saying it’s time to move away from texting as a form of 2-factor authentication. And, of course, they’re right, because text messages are a lot like email, in that it’s difficult to tell who really sent the message, and the message itself is sent in plain text — i.e. is readable by anyone who happens to be lurking in the middle.
But security experts and many technology enthusiasts have a tendency to think that everyone should see the world through the lens of security, whereas most mere mortal users just want to get on with their lives and are perfectly content to use the same password across multiple sites — regardless of how many times they’re told not to do so.
Indeed, while many more companies now offer some form of two-factor authentication than did two or three years ago — consumer adoption of this core security feature remains seriously lacking. For example, the head of security at Dropbox recently told KrebsOnSecurity that less than one percent of its user base of 500 million registered users had chosen to turn on 2-factor authentication for their accounts. And Dropbox isn’t exactly a Johnny-come-lately to the 2-factor party: It has been offering 2-factor logins for a full four years now.
I doubt Dropbox is somehow an aberration in this regard, and it seems likely that other services also suffer from single-digit two-factor adoption rates. But if more consumers haven’t enabled two-factor options, it’s probably because a) it’s still optional and b) it still demands too much caring and understanding from the user about what’s going on and how these security systems can be subverted.
Personally, I favor app-based time-based one-time password (TOTP) systems like Google Authenticator, which continuously auto-generates a unique code via a mobile-based app.
Google recently went a step further along the lines of where I’d like to see two-factor headed across the board, by debuting a new “push” authentication system that generates a prompt on the user’s mobile device that users need to tap to approve login requests. This is very similar to another push-based two-factor system I’ve long used and trusted — from Duo Security [full disclosure: Duo is an advertiser on this site].
For a comprehensive breakdown of which online services offer two-factor authentication and of what type, check out twofactorauth.org. And bear in mind that even if text-based authentication is all that’s offered, that’s still better than nothing. What’s more, it’s still probably more security than the majority of the planet has protecting their accounts.




I’ve been saying this all along. Luckily most sites allow to pick among text message and time-based two-factor authentication. (I always pick the latter.)
Unfortunately, some important sites like PayPal still DON’T. Brian, have you seen how archaic their TWA login system is?
PayPal does have available two-factor authentication. (I’ve been using it for a couple of years.) It uses Symantec’s VIP Access mobile app. However, it is challenging to figure out how to configure your PayPal account to use this, and PayPal doesn’t seem to make any effort to help you set it up, or even help you know it’s there. The best instructions I’ve seen are here: http://www.asecurelife.com/paypal-two-factor-authentication/
Thanks for the link.
I’ve now set up 2FA with both PayPal and eBay.
Glad I saw the new comment from Steve H. because I was going to say the same thing. Also of note, is eBay uses the same Symantec VIP Access 2FA system. Thanks for the good article, Mr. Krebs.
Brian, SSA has had text 2FA for like 2 or even 3 years now. I know because I set this up for my mom and sis who live stateside. I was a bit frustrated that because I live overseas, the Bellaire-centric 10-digit format wouldn’t accept an overseas phone number format (thus disenfranchising all USA expats from better security.)
Bellaire = Bellcore.
Ps I was equally disappointed when SSA (temporarily) required 2FA for all accounts but failed to consider the expats again. (Regardless, they are still head and shoulders above the rolling abortion that is the IRS’ Get Transcript set-up.)
Also failed to consider us old folks living on social security who can’t afford / don’t need a cellphone.
Hi Robert, you can use a Google Voice phone number to receive your two-factor authentication overseas, but then that phone number and email address can potentially be compromised.
Still, I like Google Voice because I can use that number for doing business and not have to give out my real cellphone number.
If 1% of Dropbox have 2FA, then presume Gmail has 10%, and maybe 20% in the US (due to identity theft concerns), and over 100 million LinkedIn passwords were exposed – Then their are potentially lots of Gmail accounts WITHOUT 2FA to be taken over – Are you sure this intended victim was not specifically targeted?
In order for the threat actor to know that 2 factor authentication was enabled they would have had to have tried logging in one time. That initial log in would have triggered a verification code to the daughter’s phone. Perhaps it’s worth mentioning that if you receive a notification that seems suspicious – i.e. a verification code that you didn’t trigger – change your password immediately.
Hey Brian,
It was great knowing about you . I have written some of your articles and it looks awesome. I also write a lot about security but more from secure design and engineering perspective rather than investigative or a particular tools.
I am more interested in developing a conceptual framework for securing I0T applications, some of the interesting insights could be grading of computing resources, threat modeling, threat metrics, risk indexes , secure software engineering practices and son on. If you are interested on collaborate on more technical aspects, please feel free to reach me out.
Best,
Ravi
“…2-factor authentication, but it is better than allowing a login with nothing more than a username and password…”
I’m in the 99%. I understand one meaning of the 2-factor authentication and choose not to use it. Reason: I don’t need an additonal login slowing me down from accessing my acc0unt. Nor, do I need 3-factor, 100000000-factor, etc making my account more secure so that I can’t even use it in a timely manner, having to go through additional steps.
My second factor if my account is compromised may be: Create another account. 2-factor authentication isn’t worth my time. I use additional security suggestions that don’t involve 2-factor authentication.
Not mentioned in the article is Gmail’s “New sign-in from…” email notifications, when accessing Gmail from multiple personal devices. I find those to be another annoyance that hasn’t secured my Gmail account, in the many times I get them. Login from another personal device and I expect another Gmail “spam” notification.
I agree. The gMail spam is moronic. If a bad actor has cracked my password and is logging in, then the first thing he is going to do is delete the e-mail that is supposedly tattling on him.
I’m totally aware of the benefits, but I’m afraid of 2FA because it makes my cell phone a single point of failure for getting in to sites. Phones can be lost, dead battery, no cell connection… So many possibilities. The main reason I would want to get to (many) sites from a new device would be if my phone failed.
I don’t consider my phone number to be permanent. I’ve had multiple carriers, moved, had both CDMA/GSM phones, etc. Sometimes porting phone numbers is not so easy. My phone number has changed. I don’t see how 2FA accommodates this reality.
I’m moving as much of my authentication from TOTP to U2F.
In Germany mobile phone providers were willing to provide you with a replacement sim card in case yours got stolen without asking too many questions. Was a popular way of deviating mTan numbers to new phones, that.
And then there are those, who for whatever reason, choose not to carry a cell phone. How would they survive in any of these proposed new eco-systems?
Not having any ggle or other social media registration to take care of, but needing to use the net for banking and government interaction, I have a purposed dumb, ie not internet enabled, phone to keep at home to use only for 2FA SMS.
It’s safe from the subversion noted by Gunter K above because the SIM is a prepaid service, from a provider which will not replace a reported stolen/lost SIM number in any case.
At an average $50/year to maintain a subscription, and using a nice reliable old-school Nokia with a backup battery, it’s a much better solution than nothing when you must interact with companies online.
I’ve seen some sites offer a list of one-time-passwords (OTP) that you print and carry with you rather than using a cell phone or other device. You use one, scratch it out on the list, and move on to the next one the next time. Periodically, you have to log on from a computer to print a new list of OTP.
And when you are accessing the internet using the cellphone that receives the SMS that is the 2nd factor. Is an SMS still a 2nd factor in this case?
Also quite a few android apps request the right to receive SMS messages. Does this make them potential backdoors to the 2nd factor? Don’t know how hard it is to sniff the data that is transferred over the network, as well…
Yes Gunter K, the platform in smart phones is full o hacking holes and I wouldn’t trust one to wall off SMS clear text at all.
However, if your first factor authentication goes along encrypted channels and you run a nice tight password routine, it is, as Brian notes, better than nothing.
First, most importantly, the advice to still use strong, unique passwords, saved in a password vault, and to choose a stronger form of 2FA such as a Google Authenticator code generator, are fully correct.
Second, a bit more nuanced response to the concerns about SMS as 2FA.
The problem with SMS as 2FA are less the social engineering angle (which is what happened in the case about which Brian is reporting here), and more that SMS itself is vulnerable to attack. That is, moderately resourced hackers can redirect the SMS messages so that they do not even need to socially engineer the legitimate holder of the mobile phone number in question.
(And then there’s the relative ease with which many mobile phone providers worldwide will allow *them*selves to be socially engineered to steal someone’s mobile phone number).
If the only 2FA option available to you is SMS, USE IT. It’s enormously better than the alternative of no 2FA. If a better option is available, use that instead.
And always be on the lookout for Social Engineering attempts.
I’d be interested in the 2FA percentage among Dropbox users who actually use the site. I have not set it up because (a) I’m using a password manager and (b) I’m there so seldom that it’s not worth the bother.
Another interesting site for 2FA information is https://www.turnon2fa.com/ – with tutorials on how to turn on 2FA for various sites.
I case of social engineering like the one described by Brian there’s no 2FA solution that would protect the victim. It’s just the matter of making the tale good enough. Even those push/application-based systems won’t stand – we’ve already seen crooks telling stories like “As one of our most valuable clients you were chosen to take a part in tests of our new software. Soon you’ll receive a message you need to confirm. It’s not real – it’s just testing. Thanks for cooperation” 🙂
Those morons over at Linked In…. I was part of a gaggle that went there when it first opened. Before it became spammy and intrusive. Once I detected it was nothing more than a finger point site that tried to drum up more connections than anyone else, I requested my account be closed. After many months of trying, they “deleted” the account. Sure they did. I kept receiving their spam emails and finally blacklisted the site. I for one do not feed social media sites for marketing campaigns.
It’s simple, if you did not request the information within the day, or the day before, simply delete and ignore until you do need to use it. With the world at nearly 80% spam level, odds are its not worth the read.
The morons at LinkedIn have conflated me with 2 businesses that I haven’t been associated with for 15 years. It makes it easy to ignore the spam that gets sent – and I can even confidently send their junk to Spamcop , even the ones that begin “Moike, we spoke last week, do you have time for a 15 minute followup call this week?”
I prefer SMS over Google Authenticator because I use multiple devices, and SMS will go to all, while GA is tethered to only one device, which I might not have with me. If GA could be authorized on more than one device I would use it.
There are security apps that support time-based tokens and device sync – 1Password, Authy, Duo Mobile. Any site that says it supports Google Authenticator will work with these (and other) apps.
Device/account sync is another ease-of-use vs security trade off, but it allows me to use TOTP more frequently than SMS.
I find 1Password has the most features, Duo the easiest to use.
David Ward, you can setup GA on multiple devices, though, it’s a pain. The trick is to have all your devices handy when you setup the 2FA for a site. When the QR code is on screen scan the same code with all your devices (Or type in the number if that’s what you are doing.)
Also, you can create off-line numbers to use and store some of them on each device.
Not easy, but it does work, and save me when I replaced my cellphone.
You can use Google Authenticator on multiple devices. You need to register new sites with all the devices at the same time:
https://support.google.com/accounts/answer/1066447?hl=en
“Setting up Google Authenticator on multiple devices”
Authy works across different devices.
As noted by others, it can be a pain, but you can set up Google Authenticator on multiple devices.
I haven’t seen mention here of printing the initial scan code or long numeric code you see when first setting up Google Authenticator for a new site. This is the code on your computer screen that you must scan or enter into each Google Authenticator app on each device before the app starts generating TOTP for the particular web site.
When you have access to a secure computer and secure printer, you can print a screen capture of the code. I do this when possible and store the printout in a safe place. That printout may later be used to setup a new device with existing accounts, for example, if you lose your primary device.
The developers at FastMail do a very good rundown
on all 2FA and make the point about SMS being at
the bottom of the heap, but good as a backup for
another failing 2FA method.
While some of the hardware solution detail applies
mainly to FastMail, their list of devices would
help anyone looking for that kind of good hardened
security. U2F looks to be the thinking man’s best
solution.
https://www.fastmail.com/help/account/2fa.html
On soft token hacking : http://gsec.hitb.org/materials/sg2016/D1%20-%20Bernhard%20Mueller%20-%20Attacking%20Software%20Tokens.pdf
Aside from what BD said about people without cell phones, or what happens if it breaks or gets lost, most sites I wouldn’t give my cell phone number to in the first place for fairly unimportant activities, and at my company we aren’t issued cell phones so that would be an issue with business related accounts I setup. (I wouldn’t give my personal cell in this case either, nor would it be wise if I decided to leave or something happened to me).
Connection to cell phones as the only option is not the answer.
(attempt #2 to post this, krebs’s site ate the first one)
Agreed. There needs to be a discussion (at/involving NIST, perhaps) about two other factors here, expense and privacy.
First of all, all mobile phone based 2FA solutions increase costs to end users. Smartphones that can run apps and not just get SMS are expensive. Data plans are expensive. Text message fees are expensive. If you don’t already have one you have to go get one, which will be expensive. If you *do* but worry about single point of failure, you need to get a backup phone, and *that* will be expensive.
And then there’s the privacy issue. Every 2FA solution I’ve seen utterly destroys your privacy with respect to whatever website it is. Having to let Google or someone know your phone number is only the beginning. 2FA plays havoc with the use of online privacy tools as well. Let’s say you don’t trust Google with even your IP address. So, you use a VPN. Now Google complains about logons from a new location every time your VPN gives you a different exit point, and Google locks out your account until you do phone verification. Stupidly, Google does this even if you *didn’t* enable 2FA for that account — you can’t opt out of it anymore. So, you can’t use Google from behind a VPN without having a mobile *and* letting Google know the number, or else paying through the nose — VPNs cost, and a separate phone just for receiving Google’s SMSes and the accompanying text message charges costs on top of that.
It gets worse still. Plenty of websites may expose information that compromises your privacy to third parties. Besides the usual advertising partners and such that can include the general public.
For a specific scenario, consider this: you want to use several online fora to discuss various topics. Some perhaps are controversial. Medical, sexual, political, whatever. For this reason you want to compartmentalize, using different screen names in each forum and not exposing your IP address or any other PII in any of them. Problem is, several of the fora are on Google Groups.
Now you have a problem. Google Groups posts from the same Google account can all be tied to each other across groups, so you will need a separate Google account for each forum that you access there. And Google Groups posts that gateway to Usenet, if not all Google Groups posts, expose the poster’s IP address in the headers.
What’s the problem? Well, five years ago there wasn’t one. It was easy to create and juggle multiple Google accounts. Not anymore. First Google added security you can’t turn off to all Google accounts — including retroactively to accounts that already existed. You can’t log into them from new IP ranges without giving Google your phone number. Then they tightened it up further, a year or so ago: you can’t even log in from a *familiar* IP range if you delete all Google cookies from your machine. It will want phone verification if you do that now. AND you can’t switch to a different Google account *without* clearing cookies anymore. If you sign out, then click sign in, the username field will be pre-filled and non-editable leaving only the password field. And of course you can’t reuse a single mobile number for a whole passel of separate Google accounts, to say nothing of the fact that doing so will cause Google itself to know they all belong to the same person, and then it will leak that information in article headers.
So now if you want to participate in five fora with distinct pseudonymous identities in each, and be absolutely sure nobody in any one of them can link your posts there with your posts in any of the other four or with your real-world identity, and they’re all hosted by Google, you will need five mobile phones.
Ridiculous!
2FA solutions, in my view, need to be all of these:
1. OPTIONAL. Google making theirs semi-not-optional is a big problem. Especially when they have some monopolies. (I don’t know of anything comparable to Google Groups at any other site, for example, let alone one that interoperates with GG, so you can post to the same forums from both services, or even only the Usenet subset.)
2. ZERO COST TO THE END USER. That categorically rules out SMS, not only because not everyone already has a mobile phone but because phone companies charge for every text not only sent but *received* (which obviously is double-dipping, but of course since they have monopolies they can get away with such behavior). It also rules out apps, since even someone with a dumbphone will need to buy a multi-hundred-dollar smartphone, AND buy an app, AND pay the data charges it subsequently racks up, probably including some it uses to display ads to you.
3. PRIVACY CONSCIOUS USER FRIENDLY. That means the user should not incur significant additional costs in *time*, let alone money, if they wish to use multiple accounts at the same site, or if they wish to avoid exposing personal information to the site or its other users. It means the 2FA solution chosen *certainly* cannot be permitted to outright *preclude* multiple pseudonym use or the use of third-party privacy tools such as VPNs. Call this the “dog principle”: “On the internet, nobody knows if you’re a dog” should continue to be true for the users of your service, or it is a badly run service.
I opened the DropBox app on my phone but could not find a way to turn on 2-factor authentication anywhere.
Same here. I just wonder if it is for a paid version.
I can’t afford a smart phone with everything else right now.
I won’t use 2FA as long as it requires I give up my phone number or email address. It’s really just another attempt to complete the dossiers on the sheeple.
“Like expiring passwords and making users change them frequently, for example.”
Personally I cannot wait until my company lengthens the interval between password changes. Then I can use my work ID and password on all of my personal Internet sites that never expire. I can’t do that now because the work one expires too often.
I do not use a cell phone, so I hope the “experts” take non-users into c0nsideration when designing future 2FA (and better).
Regards,
Bryan,
When setting up and/or logging on to a site I am offered a choice of having my computer remembered or answering a security question, in addition to a two factor response when offered.
With regard to remembering the computer vs a security question do you consider one more secure than the other?
I’m aware that the question is the only option when using a different computer, but I use the same computer most of time, so which would you recommend I use for the greatest security?
Would authenticator app solve following.:
Bad guys can do social eng to telcos and get the phone # tie to new sim card.
I’ve seen Microsoft use the feature before Google. Everytime I login to 365 it would ask me allow or deny.
Just the other day, I got texted a series of Google 2FA codes (all within a minute or two) that I did not request. They ostensibly came from the same number/source as my legit Google 2FA codes (22000), but had a different format than previous codes. The legit Google 2FA codes read “G-xxxxx is your Google verification code.” The unexpected 2FA message read “Your Google verification code is xxxxx”.
I ignored it at the time, of course, as I was not logging in from a new device. That and the format difference made me suspicious. So later that day, when I had the opportunity to do so, I logged into my gmail account from a new device. The 2FA code came in the original (legit) Google format. So right then, I knew it was a scam.
Oh, and thanks for the tip on TOTP. I’ll have to check that out. I’m a bit embarrassed I don’t know more about it.
More companies need to offer the phone callback option to a landline number as a method for 2FA. Microsoft offers this for Outlook.com, but Google does not (they require that you use a mobile number for Gmail 2FA).
The fundamental flaw in the argument against using SMS as the two-factor authentication method is that opponents are only considering SMS messages sent TO the phone. Those messages, referred to as “mobile terminate” or “MT” in the industry, are inherently insecure for a variety of reasons. In addition, having to enter a code into an open field on a web page introduces the potential for man in the middle (MITM) attacks in addition to the hijacking of the inbound SMS.
FULL DISCLOSURE HERE: I am the co-founder of a company that holds a patent in mobile-ORIGINATED SMS two-factor authentication technology so this is certainly NOT an objective opinion. It is, however, based on fact.
Mobile-originated (MO) SMS authentication offers several advantages over mobile-terminated methods. It is more secure, more easily deactivated when a phone is stolen, less vulnerable when a phone is stolen because MTs appear in previews on locked screens whereas a phone must be unlocked in order to send an authentication text and several other reasons.
Moreover, as a result of the way the U.S. carriers operate “short codes” messages cannot be spoofed to appear as though they come from another number; the UDID/IMEI matching process early in the carrier SMS transmission chain prevents that.
I would be happy to inform anyone interested about the technical details, or to debate the merits of MO vs. MT SMS 2FA, either in this forum or any other, but felt compelled to bring forward the fact that only looking at the traditional form of SMS 2FA was only seeing one side of the picture.
While not in wide spread use yet, would SQRL be a valid solution to 2 factor authentication issues? https://www.grc.com/sqrl/sqrl.htm