
For nearly a dozen years, residents of South Carolina have been kept in the dark by state and federal investigators over who was responsible for hacking into the state’s revenue department in 2012 and stealing tax and bank account information for 3.6 million people. The answer may no longer be a mystery: KrebsOnSecurity found compelling clues suggesting the intrusion was carried out by the same Russian hacking crew that stole of millions of payment card records from big box retailers like Home Depot and Target in the years that followed.
Questions about who stole tax and financial data on roughly three quarters of all South Carolina residents came to the fore last week at the confirmation hearing of Mark Keel, who was appointed in 2011 by Gov. Nikki Haley to head the state’s law enforcement division. If approved, this would be Keel’s third six-year term in that role.
The Associated Press reports that Keel was careful not to release many details about the breach at his hearing, telling lawmakers he knows who did it but that he wasn’t ready to name anyone.
“I think the fact that we didn’t come up with a whole lot of people’s information that got breached is a testament to the work that people have done on this case,” Keel asserted.
A ten-year retrospective published in 2022 by The Post and Courier in Columbia, S.C. said investigators determined the breach began on Aug. 13, 2012, after a state IT contractor clicked a malicious link in an email. State officials said they found out about the hack from federal law enforcement on October 10, 2012.
KrebsOnSecurity examined posts across dozens of cybercrime forums around that time, and found only one instance of someone selling large volumes of tax data in the year surrounding the breach date.
On Oct. 7, 2012 — three days before South Carolina officials say they first learned of the intrusion — a notorious cybercriminal who goes by the handle “Rescator” advertised the sale of “a database of the tax department of one of the states.”
“Bank account information, SSN and all other information,” Rescator’s sales thread on the Russian-language crime forum Embargo read. “If you purchase the entire database, I will give you access to it.”
A week later, Rescator posted a similar offer on the exclusive Russian forum Mazafaka, saying he was selling information from a U.S. state tax database, without naming the state. Rescator said the data exposed included Social Security Number (SSN), employer, name, address, phone, taxable income, tax refund amount, and bank account number.
“There is a lot of information, I am ready to sell the entire database, with access to the database, and in parts,” Rescator told Mazafaka members. “There is also information on corporate taxpayers.”
On Oct. 26, 2012, the state announced the breach publicly. State officials said they were working with investigators from the U.S. Secret Service and digital forensics experts from Mandiant, which produced an incident report (PDF) that was later published by South Carolina Dept. of Revenue. KrebsOnSecurity sought comment from the Secret Service, South Carolina prosecutors, and Mr. Keel’s office. This story will be updated if any of them respond. Update: The Secret Service declined to comment.
On Nov. 18, 2012, Rescator told fellow denizens of the forum Verified he was selling a database of 65,000 records with bank account information from several smaller, regional financial institutions. Rescator’s sales thread on Verified listed more than a dozen database fields, including account number, name, address, phone, tax ID, date of birth, employer and occupation.
Asked to provide more context about the database for sale, Rescator told forum members the database included financial records related to tax filings of a U.S. state. Rescator added that there was a second database of around 80,000 corporations that included social security numbers, names and addresses, but no financial information.
The AP says South Carolina paid $12 million to Experian for identity theft protection and credit monitoring for its residents after the breach.
“At the time, it was one of the largest breaches in U.S. history but has since been surpassed greatly by hacks to Equifax, Yahoo, Home Depot, Target and PlayStation,” the AP’s Jeffrey Collins wrote.
As it happens, Rescator’s criminal hacking crew was directly responsible for the 2013 breach at Target and the 2014 hack of Home Depot. The Target intrusion saw Rescator’s cybercrime shops selling roughly 40 million stolen payment cards, and 56 million cards from Home Depot customers.
Who is Rescator? On Dec. 14, 2023, KrebsOnSecurity published the results of a 10-year investigation into the identity of Rescator, a.k.a. Mikhail Borisovich Shefel, a 36-year-old who lives in Moscow and who recently changed his last name to Lenin.
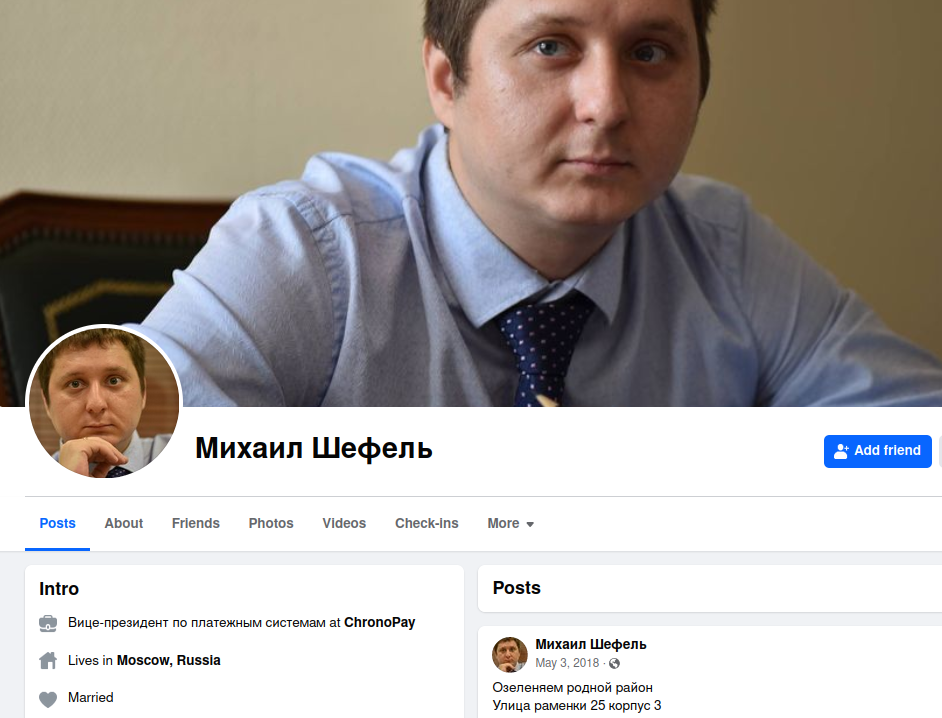
Mr. Keel’s assertion that somehow the efforts of South Carolina officials following the breach may have lessened its impact on citizens seems unlikely. The stolen tax and financial data appears to have been sold openly on cybercrime forums by one of the Russian underground’s most aggressive and successful hacking crews.
While there are no indications from reviewing forum posts that Rescator ever sold the data, his sales threads came at a time when the incidence of tax refund fraud was skyrocketing.
Tax-related identity theft occurs when someone uses a stolen identity and SSN to file a tax return in that person’s name claiming a fraudulent refund. Victims usually first learn of the crime after having their returns rejected because scammers beat them to it. Even those who are not required to file a return can be victims of refund fraud, as can those who are not actually owed a refund from the U.S. Internal Revenue Service (IRS).
According to a 2013 report from the Treasury Inspector General’s office, the IRS issued nearly $4 billion in bogus tax refunds in 2012, and more than $5.8 billion in 2013. The money largely was sent to people who stole SSNs and other information on U.S. citizens, and then filed fraudulent tax returns on those individuals claiming a large refund but at a different address.
It remains unclear why Shefel has never been officially implicated in the breaches at Target, Home Depot, or in South Carolina. It may be that Shefel has been indicted, and that those indictments remain sealed for some reason. Perhaps prosecutors were hoping Shefel would decide to leave Russia, at which point it would be easier to apprehend him if he believed no one was looking for him.
But all signs are that Shefel is deeply rooted in Russia, and has no plans to leave. In January 2024, authorities in Australia, the United States and the U.K. levied financial sanctions against 33-year-old Russian man Aleksandr Ermakov for allegedly stealing data on 10 million customers of the Australian health insurance giant Medibank.
A week after those sanctions were put in place, KrebsOnSecurity published a deep dive on Ermakov, which found that he co-ran a Moscow-based IT security consulting business along with Mikhail Shefel called Shtazi-IT.
A Google-translated version of Shtazi dot ru. Image: Archive.org.




me, I did.
the FBI would have put a stop to these shenanigans post haste! Edgar would have demanded it.
Edgar was the middle name, John. “(Hoover) became a controversial figure as evidence of his secretive abuses of power began to surface. He was found to have routinely violated both the FBI’s own policies and the very laws which the FBI was charged with enforcing, and to have collected evidence using illegal surveillance, wiretapping, and burglaries.[2][3] Hoover consequently amassed a great deal of power and was able to intimidate and threaten political figures, including high-ranking ones.” – Not who I’d have referenced for no visible reason.
In any case, if one reads this story, it appears they may have investigated semi-successfully.
But once data is in the wind you can’t get it back, nor FBI likely arrest anyone living in Russia.
Personally I think his new legal name is incomplete without at least one Vladimir in there…
The unfounded rumor is that he rocked wearing an evening gown and pearls.
Edgar Allan who?
How did they not encrypt SSN for crying out loud? At the time, Gov. Haley said that was common industry practice, even at banks. Is that still true?
> How did they not encrypt SSN
Encrypting the SSN and other sensitive information does not guarantee protection. It only adds an obstacle. If for example the original clicky state IT contractor cited above had access to SSNs via a decryption key, the attackers would still have access to everything protected by the decryption key.
There are some arguments based on the similarities between this attack and other attacks by the same group, they say it is a Russian hacker group.
And in the meantime, certain members of the US Congress are fulfilling their side job of being voting proxies for Russia with fervor. We don’t need to dox them, because y’all know who they are…
This is what I preach at my work, I hope others do too: Our data should be so well encrypted that if someone stole it, it would be useless to them.
(Otherwise there is no point in encryption)
The real question is “where did that header image come from??”
So, an IT consultant (or an employee thereof) fell for a phishing scheme, which ultimately led to the breach.
I know it is not the story told here, but I am curious–whatever happened to that IT consultant or employee? And related questions such as how in the world an IT consultant or employee (a) could fall for such a scheme (yes, I know how good they can be, and how they get more credible or persuasive over time, but …), and (b) NOT have seriously layered protection over the state’s data to severely limit whatever data was exposed?
By the way, it is questions like these that convinced me it was time to retire from IT management in health care.
As a non IT guy, I think these are good questions.
According to the Mandiant report, the IT contractor responsible for the initial intrusion no longer worked for that state agency by the time the breach was discovered.