If you happen to stumble upon a Web site that freaks out your anti-virus program, chances are good that the page you’ve visited is part of a malicious or hacked site that has been outfitted with what’s known as an “exploit pack.” These are pre-packaged kits designed to probe the visitor’s browser for known security vulnerabilities, and then use the first one found as a vehicle to silently install malicious software.
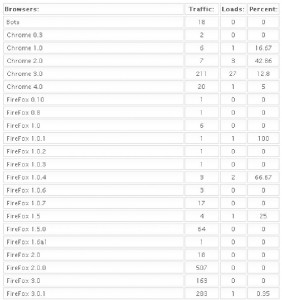
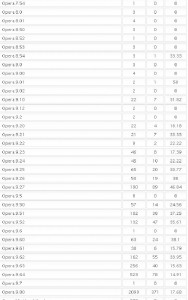
Exploit packs have been around for years, and typically are sold on shadowy underground forums. A constant feature of exploit packs is a Web administration page (pictured above), which gives the attacker real-time statistics about victims, such as which browser exploits are working best, and which browsers and browser versions are most successfully attacked.
One of the most popular at the moment is a kit called “Eleonore,” and I’m writing about it here because it highlights the importance of remaining vigilant about patching. It’s also a reminder that sometimes the older exploits are more successful than the brand new variety that garner all of the headlines from the tech press.
 The screen captures in this blog post were taken a few weeks ago from a working Eleonore installation (version 1.3.2) that was linked to several adult Web sites. As we can see from the first image, this pack tries to exploit several vulnerabilities in Adobe Reader, including one that Adobe just patched this month. The kit also attacks at least two Internet Explorer vulnerabilities, and a Java bug. In addition, the pack also attacks two rather old Firefox vulnerabilities (from 2005 and 2006). For a partial list of the exploits included in this pack, skip to the bottom of this post.
The screen captures in this blog post were taken a few weeks ago from a working Eleonore installation (version 1.3.2) that was linked to several adult Web sites. As we can see from the first image, this pack tries to exploit several vulnerabilities in Adobe Reader, including one that Adobe just patched this month. The kit also attacks at least two Internet Explorer vulnerabilities, and a Java bug. In addition, the pack also attacks two rather old Firefox vulnerabilities (from 2005 and 2006). For a partial list of the exploits included in this pack, skip to the bottom of this post.
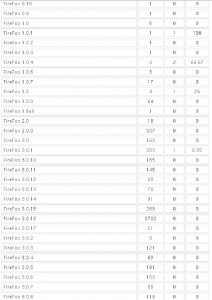
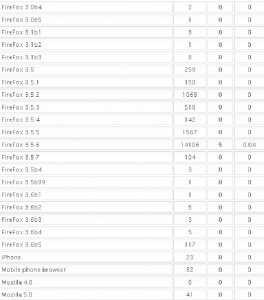
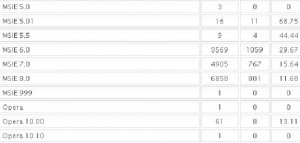
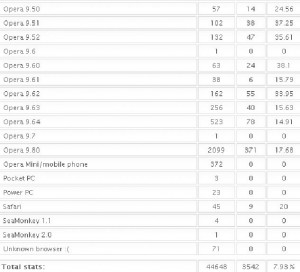
It’s important to keep in mind that some of these exploits are browser-agnostic: For example, with the PDF exploits, the vulnerability being exploited is the PDF Reader browser plug-in, not necessarily the browser itself. That probably explains the statistics in the images below, which shows a fairly high success rate against Opera, Safari, and Google Chrome users. In the screen shots below, the numbers beneath the “traffic” field indicate the number of visitors to the malicious site using that particular version of the browser, while the “loads” number corresponds to the number of visitors for that browser version that were found to be vulnerable to one or more of the vulnerabilities exploited by the Eleonore pack. The “percent” fields obviously indicate the percentage of visitors for each specific browser type that were successfully exploited (click for a larger version):
Just from observing some of these stats, it’s clear that some of the most successful exploits target vulnerabilities that were patched quite some time ago. In a few cases where I have highlighted the importance of patching Java vulnerabilities, for example, I received feedback from some readers who doubted whether anyone ever tried to attack Java flaws. As we can see from the second screenshot above, the Java exploit was the second most successful attack (behind an exploit pack that attacks at least three different Adobe Reader flaws).
More Firefox stats (again, click for a larger version)
Here are the Internet Explorer breakdowns:
…and the Opera and Safari statistics:
Vulnerabilities exploited by this Eleonore pack include:
PDF pack
PDF Brand new PDF Exploit (12/2009)
PDF collab.getIcon (4/2009)
PDF Util.Printf (11/2008)
PDF collab.collectEmailInfo (2/2008)
MS Internet Explorer Exploits
MS09-002 (Internet Explorer 7 exploit 1/2009)
MDAC – ActiveX (Internet Explorer exploit, 3/2007)
Java
Javad0 (12/2008) – Java Calendar (Java Runtime Environment (JRE) for Sun JDK and JRE 6 Update 10 and earlier; JDK and JRE 5.0 Update 16 and earlier; and SDK and JRE 1.4.2_18 and earlier)
Firefox
compareTo – exploit for a Firefox vulnerability from 2005
jno – Exploit for Firefox version 1.5.x (2006)