I had just finished opening an account at the local bank late last week when I happened to catch a glimpse of the bank manager’s computer screen: He had about 20 Web browser windows open, and it was hard to ignore the fact that he was using Internet Explorer 6 to surf the Web. ![]()
For more than a second I paused, and considered asking for my deposit back.
“Whoa,” I said. “Are you really still using IE6?”
“Yeah,” the guy grinned sheepishly, shaking his head. “We’re supposed to get new computers soon, but I dunno, that’s been a long time coming.”
“Wow. That’s nuts,” I said. “You’ve heard about this latest attack on IE, right?”
I might as well have asked him about the airspeed velocity of an African Swallow. Dude just shook his head, and so did I.
Well, you can’t really blame the poor guy for not knowing. Just hours before, Microsoft Chief Executive Steve Ballmer looked a bit like a deer in headlights when, standing in front of the White House in a planned CNBC interview on how the Obama administration is looking to use technology to streamline its operations, he was suddenly asked about a report just released from McAfee effectively blaming a slew of recent cyber break-ins at Google, Adobe and more than 30 top other Silicon Valley firms on a previously unknown flaw in IE.
“Cyber attacks and occasional vulnerabilities are a way of life,” Ballmer said. “If the issue is with us, we’ll work through it with all of the important parties. We have a whole team of people that responds very real time to any report that it may have something to do with our software, which we don’t know yet.”
Microsoft has of course since acknowledged that a critical, unpatched security flaw indeed exists and is being exploited in targeted attacks. The software giant says it has only observed the now-public exploit code working against IE6, and that IE users should upgrade to the latest version IE8, which Microsoft says is much better insulated from the current batch of exploits.
Redmond typically releases software updates on the second Tuesday of each month (a.k.a. “Patch Tuesday), but the company said in this case customers may not have to wait until Feb. 9 for a patch for this security hole. Microsoft is eager to assure everyone that the attacks observed so far are only successful against IE6, and that in any event they have not been widespread.
Meanwhile, researchers continue to test that claim. Researcher Dino Dai Zovi Tweeted Monday that he had modified the existing exploit so that it worked on IE7, with the caveat that on Microsoft Vista systems it would only allow an attacker read access to the victim’s files (as opposed to full privileges to delete or modify system files).
In a sign that we may very soon start to see a number of hacked and malicious Web sites leveraging this flaw to install unwanted software, security firm Websense warned that it had spotted a Web site that was exploiting the IE vulnerability.
Microsoft’s assurances have not been enough for some. The governments of France and Germany have urged people to stop using Internet Explorer (Update, 1:16 p.m: The Australian government just issued a similar warning). For its part, the U.S. government is expected to issue a demarche to the Chinese government, looking for an explanation of the attacks against Google and others, which experts have described as a sophisticated and targeted attempts to steal trade industry secrets, as well as information about Chinese dissident groups.
At least one top Chinese computer security firm is urging consumers there not to wait for Microsoft’s patch, but to instead install an unofficial, stop gap fix (rough, Google translation). No doubt, if the wait drags on for an update from Microsoft, we will see the same offers from U.S. security firms and experts.
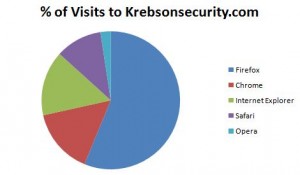
There are, of course, alternatives to IE. But then again, I’m preaching to the choir. Most of my readers already use another browser, according to the latest visitor stats for krebsonsecurity.com, compliments of Google Analytics. Here’s how my visitors break down:
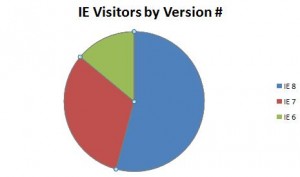
Looks like krebsonsecurity.com does have some IE6 users (and at least one IE5! user). Nearly 14 percent of the visitors browsing this site with IE are using IE6: Here’s the visitor breakdown by IE version:
If you do want to keep browsing with IE (or, work at an organization like my bank which apparently doesn’t have much choice in the matter), Microsoft has some tips here on ways to leverage additional protections both in Windows and in newer IE versions.




That graph clearly indicates that my use of W3M (lynx-like terminal browser) isn’t exactly normal…
Then again, the chance of a security flaw being exploited in it is quite a lot lower.
I don’t know whether to laugh or cry at this one!
IE6 I think still has roughly 20% of the worlds market share amongst actively used browsers. IE8 has right around the same 20% mark.
Most very funny. I especially liked the comment about calculating the speed of an African swallow. One does hope that your good sense will reach a wider audience.
(Also, another Geezer)
Laughing, crying and not surprised. A friend and sometimes client, who uses another ‘expert’ for network admin and support, has a small firm (law and taxes). That ‘expert’ as a matter of company policy has them refuse to install Microsoft updates and patches. Forget Adobe’s reader and flash player updates; not even on the horizon. Yes, my friend’s network got hit late last month. Who did they call to clean it up? Their ‘expert.’
For years I have tried to persuade him to install those updates and use Firefox. His network remains without security updates and patches–but he now uses Adobe Reader 9.3 and Firefox.
Sometimes it’s not that easy.
I work for an auto manufacturer, and the primary software for automotive dealers is from the giant “ADP”….
Their applications run on Internet Explorer, and ONLY Internet Explorer. If you try to run on anything else you get a “Browser Not Supported” error.
To add insult to injury, when we run credit checks (through ADP) across the internet, ADP “REQUIRES” Java Virtual Machine (JVM) 1.4.2_07, for those of you that don’t know has major security issues.
ADP’s response to me on the JAVA issue (almost a year ago) was that we shouldn’t be surfing the Internet. They are not responsible if we go to a bad site.
In any Enterprise environment you are going to use “Specialized” software, and the problem is that software sometimes requires “OLDER” versions of the supporting applications (IE, java, reader, etc). While there will be a few that say “Vote With Your Dollars” and don’t use it, once you buy a package that costs one million dollars (over the term of a 5 year lease). You can’t just not use it.
Other issues, like ADP payroll. It’s a legacy application, that REQUIRES Administrator rights to run. So I give that user “Local” Admin privileges and pray/hope they don’t somehow get to a bad site.
Enterprise environments are not as easy as a standalone computer or home network, making legacy software work in the enterprise is a full time job today with today’s internet environment.
If you think Auto industry has issues with outdated software, go check the Energy industry. Oh yeah, that means nuke plants and transmission lines operators. Think about telnet, tftp, forbidden MS patches and all the rest.
While granting the basic idea that corporate and legacy apps confound the security landscape, I must also add: (1) My employer’s network (small, admittedly, ~200 users, some remote) encourages (not yet requires) Firefox use and IE8 when that is used.
(2) An IE-tab add-on for Firefox has run for me all the IE-required web sites/apps I can find EXCEPT for some (and only some) Microsoft pages–updates. Yes, we keep (as I do at home) IE for those specific instances.
(3) Many (most?) legacy apps that “require administrative rights” for users, including some apps that we use, actually only require users’ full control of specific program-used folders. These less-than-full-admin-rights actually required may not be documented or apparent, it is true. So, it can be an enormous (and maybe too much of a) job for an IT manager to sort those out and implement the corresponding policies. We have had vendor assistance in doing just that, however. (No, not ADP; can’t help there.)
Yep N3 I see that same scenario today
on the matter of the opening example – i too have seen banks using out-of-date browsers, it seems a number of the tools they use are web-apps. that said, the terminals these web-apps are being used from don’t have access to the outside world – they can’t browse to a malicious or otherwise compromised site and so patching or updating the browser becomes rather irrelevant.
obviously i don’t know if this was also true in brian’s example, but it’s something to keep in mind – not every instance of out-of-date software makes for a vulnerable system. the broader operating environment is also an important consideration in determining whether the system as a whole is vulnerable.
Kurt,
I have to disagree with you. All unpatched software IS vulnerable to the threats the patch would correct.
Threats can be kept at bay by not allowing access to public network, but the system will still be vulnerable. All that it takes to compromise it is to let the threat have access to the vulnerable asset.
3G USB dongles anyone?
not that i’m trying to pull a fast one with semantics or anything, but i said the *system* wasn’t vulnerable, not the software. a system that can’t connect to the outside world is, for all intents and purposes not vulnerable to browser exploits because the browsable pages are effectively whitelisted.
If you live or work in California, watch out! IE6 is THE supported browser in use in many California government organizations… I just spent several days “fixing” an application to run correctly with IE6.
I agree with the poster above; enterprise environments are sometimes glacially slow to switch – I still support Windows 3.1 systems in factory environments!
All the more reason for these groups to spear phish use targeted attacks on enterprise environments (Govt and Private) that they wish to pilfer confidential/classified information.
I also use IE 6 at work. I have no choice as our corporate infrastructure has problems with both Firefox and newer versions of IE. I keep hearing they will be moving to newer versions in the near future. But, I only use IE 6 for my internal corporate sites.
For personal stuff, I only use my work computer for gmail and news, and for that I use firefox. For most everything else I use my home computer running XP with the latest versions of everything.
For banking and stocks, I use an old laptop running the Ubuntu version of Linux with almost nothing else enabled. I use that laptop for nothing else.
So yes, your reporting has changed the way I use the web.
While it won’t help with zero-day exploits and unpatched problems, the browser security test at http://bcheck.scanit.be/bcheck/ is a great way to make sure that your IE or Firefox browser is up to date.
The Australian government has also warned its people not to use IE.
http://www.abc.net.au/news/stories/2010/01/19/2795684.htm
My company won’t let me update IE6. They recommend we use FF, but people have to remember…
Thanks, Dano. Just added a link to that story in the blog post.
I’m not sure why they advise against IE. There’s no good reason for that. There are likely as many problems with Firefox, Safari, or Chrome. There’s no real way to say there isn’t. However, IE8 on Windows 7/Vista is an extremely difficult piece of software to break.
Additionally, there have been reports in the Metasploit lists of difficulty having the exploit work successfully. I don’t keep a VM with IE6 so I haven’t tested it myself. I know some corporations are forced to remain with IE6 but I believe that’s more at issue than a new bug surfacing.
Wow. I think Demosthenes had an easier time of it.
brian, of the IE slice, would you be able to see how many are using Ie 6, 7 ,and 8?
Unfortunately, no.
Brian,
When you are in Analytics, under browsers, then click on Internet Explorer, it will then give you a breakdown on versions, here are IE stats from my sites:
Version 8.0 49.80%
Version 7.0 32.24%
Version 6.0 17.96%
For the record, here is the browser breakdown from my sites:
Internet Explorer 44.71%
Firefox 43.80%
Chrome 4.20%
Safari 3.47%
Opera 2.37%
Mozilla 1.09%
12345 0.18%
Camino 0.18%
Ah yes. You are right. I just added the IE breakdown to the post above. Thanks, Scott.
The average cruising airspeed velocity of an unladen European swallow is roughly 11 meters per second or 24 miles an hour. We’re not sure about the African swallow yet. There are namely nearly 50 varieties of African swallow. But the following link has a rough calculation yielding approximately the same results.
http://bit.ly/89MmzA [monkeyrivertown.com]
So it goes to show: if you’re not on Windows then answers to questions such as the above are not all that remote.
interesting posts about VUPEN having reliable code bypassing DEP and IE8.
Brian,
Could you please spend a little time on the status of browser benchmarks? For the life of me, I cannot understand who gives a d@mn if Safari is faster than Chrome.
What matters is compatibility with web apps and programming. There are web standards and even a test site I have forgotten that shows how well any given browser displays the page written according to the standards. None of them are 100%, but I think that adherence to standards, security and a light memory footprint should be three criteria to judge browsers.
Of course that doesn’t help when a dumbF vendor writes their app using ActiveX.
StatCounter’s figures for worldwide browser market share (http://preview.tinyurl.com/yblgv77 ) show both IE8 and IE7 presently at about 20 % each, with IE6 at 16 %. Firefox 3.5 leads the pack at about 24 %, while Chrome 3.0 enjoys a market share of about 5 %. It’s instructive to compare the figures above with the corresponding figures for the Chinese mainland (http://preview.tinyurl.com/yfko5ja ), where IE6 still enjoys a market share of nearly 60 % (!), IE7 and IE8 15 % and 12 %, respectively, while Maxthon 2.0 at 6 % has about twice the market share of Firefox at 3 %. In this context, it’s not quite as surprising to learn that employees at the Google offices in China were using IE6 ; in that country it’s obviously vital to know how one’s site renders in that ancient browser….
Henri
Microsoft is sending out an out-of-band update on this 0-day IE threat tomorrow.
Dan, I think Msft said it would talk tomorrow about when it would issue an update, not that it would issue an update tomorrow. My guess is we won’t see a patch for the IE flaw until Friday at the earliest, but probably more like sometime next week. Just a guess, though.
Brian, the patch did come out the evening of the 21st. Our servers and desktops had it waiting for them this a.m.
It has been my experience over the past 20+ years of working in IT, and 15+ in Information Security, that trying to get organizations to change their stance on installation of new patches and software is a punishment befitting Sisyphus.
We, (the knowledgeable security practitioners) continually watch the front lines, warning of the encroaching enemies, and then are thrown to the lions, when the defenses become overrun. This continual failing battle has to change.
Organizations need to stand up and be accountable for their lack of action, and when their lack of action causes data breaches, they need to be punished, not their security staff who are fighting the growing hoards of enemies.
Lastly, the security industry needs to stop sitting on it’s laurels. We haven’t had any significant technology or software since the inception of the 3rd generation firewall to protect organizations and individuals.
I have personally thought of a career change, leaving Information Security behind, and moving on to something completely out of the Information Technology space. The lack of action and accountability of the software/hardware manufacturers, businesses, and government, have made me personally disgusted with the current state of Information Security.
That’s my 2¢, YMMV.
I am also frustrated by inaction by the industry in general. There are too many people who are willing to try and pass the buck by insisting that the problem is one of “educating users”, which I believe to be a band-aid at best.
At the highest levels, the standards committees seem to discuss ad-infinitum all sorts of possibilities, but they seem to have little incentive to actually come up with anything useful in a timely fashion. And then you have pushback from people and governments who don’t want to change anything for whatever reason.
Part of the problem is that users have come to expect that the internet have all kinds of flashing lights (flash animations, javascript) and a lot of this is in places where it isn’t strictly needed. Even pdf files are overused really – in most cases the file just holds text and figures that could be rendered with html just as well (but it wouldn’t be quite so pretty). And every cool ‘feature’ that gets added on introduces the potential for all sorts of additional vulnerabilities.
I have given considerable thought to various potential ‘solutions’ – the problem is that there are multiple things that you need to be on guard against, so there isn’t really a single thing that one can do to completely protect yourself (other than throw away your computer and go live in the woods – an option that sounds more and more appealing as time goes on).
The one that concerns me the most are the phishing attacks. These are harder to protect against in that the user is tricked into doing something that they ought not do.
In part the problem may boil down to an overreliance on using a username/password for authentication. Partly because every damned website you go to these days wants you to register, and people have gobs and gobs of passwords to keep track of. This leads people to reuse the same password for multiple websites, which is really something they ought never do. But it also means that if someone else ever gets a hold of your username/password they can log in and do whatever they want. I keep hoping for some sort of physical object that one could use in lieu of username/password that would need to be used to authenticate, and which could be secured when not in use. I don’t know if such a thing really exists however..
Sure password strength is crucial, but not at all a panacea. Gartner says that in the next 3 years web exploits will completely overthrow OTP. Tell me, what the heck should I do with my 500 RSA tokens?
I wish I had a good answer.
But as has pointed out in the past, if the computer is infected with malware, then things like tokens and smartcards don’t help you very much.
With technology would make it possible to prevent the private key from being transmitted to the bad guys, and to prevent an account from being emptied when the device is unplugged (so I suppose there is still some amount of value in these things), but the whole point of having the thing is so you can use it from time to time.
So it still comes down to preventing malware infections in the first place, because if you can’t do that, then nothing else matters.
Could today’s lack of security (in all OSs) be a result of Microsoft’s monopoly? The NYT says this: “It’s a classic market failure — the market hasn’t delivered security,” quoting James A. Lewis.
People do not select their OS and applications based on security, but because of vendor lock-in. Fix vendor lock-in and you’ll fix security because organizations will then be free to select the most secure OS and applications.
What is IE 6? 🙂
Yawn…
This whole IE has a security bug/it’s the end of the world/let’s run around with our hair on fire/better use another browser thing seems a bit overdone to me. So there’s a critical flaw that probably needs an out of band patch. It happens. It’s not the first time and it won’t be the last.
Computer security is NOT about one thing. Rather it’s about layers of defense or what is called defense in depth. Using it the last 14+ years, I’ve never been compromised. And that’s with using IE and Windows the entire time. Guess it’s just been dumb luck.
@xAdmin,
I agree 100%.
In the enterprise, where you need internet access to do your job (for 100’s of users), the ONLY thing you can do to protect yourself is to stay current with updates & patches, use a layered defense, and of course read Brian’s blog, and ISC daily (smile)
@Brian, MSRC just announced they will be releasing MS10-002 on January 21, 2010 ~10:00am PST (UTC-8). They also added comments about some PoC exploits bypassing DEP.
To cite McAfee Security Insights Blog:
“Still, so far the attacks we’ve seen using this vector have been focused on Internet Explorer 6.”
One of the targets was Google and I don’t think a lot of people at Google are using Internet Explorer 6 (most probably nobody uses IE6 at Google).
I would not be surprised to hear that the attackers have used other vulnerabilities (already know or not) in other web browser most probably in one of Google’s offerings (Chrome and Firefox).
The main problem with IE is that it gets much more media attention and that exploits are made public much faster then exploits, otherwise there is not much difference to other programs securitywise.
As far as whether anyone at Google uses IE, as was pointed out in other posts, it’s not always up to a company what browser it uses. If Google wants to pay its employees, it will have to deal with whatever browser requirements its banks/payroll companies may impose, for instance … at least until they introduce GooglePayroll and gBank and do it themselves. 😉
Like any other company of this size if Google wants to pay their customers they will send SWIFT/EDIFACT/whatever messages to their bank and they will handle the payments.
The messages will be generated by an accounting software like SAP, Siebel, JD Edwards, home grown, …
The only time a browser might be needed is when accessing the accouting software and I don’t think this will require IE6.
K951, check my posting above, which provides statistics – and their source ! – on browser market share in China and you will understand why it’s not unreasonable to conclude that employees of Google in China may in fact have been using IE6 – presumably to check how pages and tools render on what remains far and away the most popular browser in China….
Henri
It’s unreasonable to conclude that anyone at Google is using IE6 as default browser (that opens when clicking links in emails) on a regular basis.
I don’t think that a lot of Google Intranet apps is still compatible with IE6, which is so far behind in terms of web standards support…
It’s not just a case of IE being targeted because of market share. It’s just poorly designed for a world where people are responsible for the actions other people take when using their computers.
If you have to interact with a site like ADP that requires you to use IE and no other browser, you’re required to trust ADP’s site isn’t hacked. If I visit some trusted site with Firefox/Noscript and decide to permanently allow javascript, I’m taking a similar risk.
But with Firefox/Noscript, I can right-click and see which domains are being blocked, and I can easily change the security level for some or all of them. With Internet Explorer, I have to gather a list of those domains by trial and error, then manually add them to my “Trusted Sites” list.
In real life, you can never find all of the domains you need to add, and you can never get these sites to work unless you set your global security level to low. That would be less scary on my own computer, as I know I’ll never use IE if I can avoid it anyway. But one of my employees who wants to find a client phone number may look for a phone-directory website through a search engine and end up clicking on an ad for some rogue software site. How hard is it for IE to include a function that displays domains that are being blocked by security settings and allows you to individually add them to your “trusted zone” list on the fly? The fact that every time Windows computers get updates from Microsoft the default browser is changed back to IE adds insult to injury.
As far as an IE5 user who reads this blog … knowing this crew, it could be someone with UserAgentSwitcher and a sense of humor.
BTW, this small (21 employees) bank uses mainly IE8. I use Chrome and Firefox for some browsing.
One of your earlier posters was correct about IE being the supported version for some required applications. Ours is no less than the Federal Reserve Bank. Their system is paranoidedly tight, and they support IE8, but they only support IE.
I work as IT for a small savings and loan as IT administrator. I switched all our employees to Firefox as a default web browser at least 2 years ago. There are still applications that require an IE certificate that some users have to use, but they are very aware of why we require them to use an alternative browser.
We monitor our website activity as well and still find approximately 60% of our customers accessing our site with some form of IE. We do everything we can to try to educate them. Why? Because its in our best interest as well. The financial institutions are responsible for the fraud if it happens to one of our customers. Something needs to happen to change that and put more emphasis on making the end-user more responsible for his/her own actions IMHO.
I appalled by the poor advice given by Security pundits by yourself. By telling people to move away from IE to something like firefox is seriously jeopardizes their security on news OSes like Vista and Win7. Firefox does not support a Protected Mode and without that feature, firefox is FAR WORSER than IE.
Why are people like you even allowed to post on the Web.
Even if there is an exploit on IE7/8 on Vista/Win7 , protected mode will block i.t
I am appalled at how difficult you find it to leave a coherent insult.
Seriously, though — why does urging people to use another browser make them *more* vulnerable than using IE? In addition to using another browser like Firefox, I always urge people to use safety plugins like noscript — which by the way IE doesn’t have.
Finally, you should know that while Microsoft said its data execution prevention technology would block these attacks on IE8, researchers were able to show that was not always the case.